How Cloudflare Security does Zero Trust


Throughout Cloudflare One week, we provided playbooks on how to replace your legacy appliances with Zero Trust services. Using our own products is part of our team’s culture, and we want to share our experiences when we implemented Zero Trust.
Our journey was similar to many of our customers. Not only did we want better security solutions, but the tools we were using made our work more difficult than it needed to be. This started with just a search for an alternative to remotely connecting on a clunky VPN, but soon we were deploying Zero Trust solutions to protect our employees’ web browsing and email. Next, we are looking forward to upgrading our SaaS security with our new CASB product.
We know that getting started with Zero Trust can seem daunting, so we hope that you can learn from our own journey and see how it benefited us.
Replacing a VPN: launching Cloudflare Access
Back in 2015, all of Cloudflare’s internally-hosted applications were reached via a hardware-based VPN. On-call engineers would fire up a client on their laptop, connect to the VPN, and log on to Grafana. This process was frustrating and slow.
Many of the products we build are Continue reading
Kubectl with Cloudflare Zero Trust


Cloudflare is a heavy user of Kubernetes for engineering workloads: it's used to power the backend of our APIs, to handle batch-processing such as analytics aggregation and bot detection, and engineering tools such as our CI/CD pipelines. But between load balancers, API servers, etcd, ingresses, and pods, the surface area exposed by Kubernetes can be rather large.
In this post, we share a little bit about how our engineering team dogfoods Cloudflare Zero Trust to secure Kubernetes — and enables kubectl without proxies.
Our General Approach to Kubernetes Security
As part of our security measures, we heavily limit what can access our clusters over the network. Where a network service is exposed, we add additional protections, such as requiring Cloudflare Access authentication or Mutual TLS (or both) to access ingress resources.
These network restrictions include access to the cluster's API server. Without access to this, engineers at Cloudflare would not be able to use tools like kubectl to introspect their team's resources. While we believe Continuous Deployments and GitOps are best practices, allowing developers to use the Kubernetes API aids in troubleshooting and increasing developer velocity. Not having access would have been a deal breaker.
To satisfy our security requirements, Continue reading
Decommissioning your VDI


This blog offers Cloudflare’s perspective on how remote browser isolation can help organizations offload internal web application use cases currently secured by virtual desktop infrastructure (VDI). VDI has historically been useful to secure remote work, particularly when users relied on desktop applications. However, as web-based apps have become more popular than desktop apps, the drawbacks of VDI – high costs, unresponsive user experience, and complexity – have become harder to ignore. In response, we offer practical recommendations and a phased approach to transition away from VDI, so that organizations can lower cost and unlock productivity by improving employee experiences and simplifying administrative overhead.
Modern Virtual Desktop usage
Background on Virtual Desktop Infrastructure (VDI)
Virtual Desktop Infrastructure describes running desktop environments on virtual computers hosted in a data center. When users access resources within VDI, video streams from those virtual desktops are delivered securely to endpoint devices over a network. Today, VDI is predominantly hosted on-premise in data centers and either managed directly by organizations themselves or by third-party Desktop-as-a-Service (DaaS) providers. In spite of web application usage growing in favor of desktop applications, DaaS is growing, with Gartner® recently projecting DaaS spending to double by 2024.
Both flavors of VDI Continue reading
HTTP/3 inspection on Cloudflare Gateway


Today, we’re excited to announce upcoming support for HTTP/3 inspection through Cloudflare Gateway, our comprehensive secure web gateway. HTTP/3 currently powers 25% of the Internet and delivers a faster browsing experience, without compromising security. Until now, administrators seeking to filter and inspect HTTP/3-enabled websites or APIs needed to either compromise on performance by falling back to HTTP/2 or lose visibility by bypassing inspection. With HTTP/3 support in Cloudflare Gateway, you can have full visibility on all traffic and provide the fastest browsing experience for your users.
Why is the web moving to HTTP/3?
HTTP is one of the oldest technologies that powers the Internet. All the way back in 1996, security and performance were afterthoughts and encryption was left to the transport layer to manage. This model doesn’t scale to the performance needs of the modern Internet and has led to HTTP being upgraded to HTTP/2 and now HTTP/3.
HTTP/3 accelerates browsing activity by using QUIC, a modern transport protocol that is always encrypted by default. This delivers faster performance by reducing round-trips between the user and the web server and is more performant for users with unreliable connections. For further information about HTTP/3’s performance advantages take a look at Continue reading
Connect to private network services with Browser Isolation


If you’re working in an IT organization that has relied on virtual desktops but looking to get rid of them, we have some good news: starting today, you can connect your users to your private network via isolated remote browsers. This means you can deliver sensitive internal web applications — reducing costs without sacrificing security.
Browser Isolation with private network connectivity enables your users to securely access private web services without installing any software or agents on an endpoint device or absorbing the management and cost overhead of serving virtual desktops. What’s even better: Browser Isolation is natively integrated into Cloudflare’s Zero Trust platform, making it easy to control and monitor who can access what private services from a remote browser without sacrificing performance or security.
Deprecating virtual desktops for web apps
The presence of virtual desktops in the workplace tells an interesting story about the evolution of deploying and securing enterprise applications. Serving a full virtual desktop to end-users is an expensive decision, each user requiring a dedicated virtual machine with multiple CPU cores and gigabytes of memory to run a full operating system. This cost was offset by the benefits of streamlining desktop app distribution and the security Continue reading
Announcing Gateway + CASB
This post is also available in 简体中文, 日本語, Español.
Shadow IT and managing access to sanctioned or unsanctioned SaaS applications remain one of the biggest pain points for IT administrators in the era of the cloud.
We're excited to announce that starting today, Cloudflare’s Secure Web Gateway and our new API-driven Cloud Access Security Broker (CASB) work seamlessly together to help IT and security teams go from finding Shadow IT to fixing it in minutes.
Detect security issues within SaaS applications
Cloudflare's API-driven CASB starts by providing comprehensive visibility into SaaS applications, so you can easily prevent data leaks and compliance violations. Setup takes just a few clicks to integrate with your organization's SaaS services, like Google Workspace and Microsoft 365. From there, IT and security teams can see what applications and services their users are logging into and how company data is being shared.
So you’ve found the issues. But what happens next?
Identify and detect, but then what?
Customer feedback from the API-driven CASB beta has followed a similar theme: it was super easy to set up and detect all my security issues, but how do I fix this stuff?
Almost immediately after investigating the most Continue reading
Join The Packet Pushers For A Live Stream With Gluware June 28, 2022
We're hosting the "Real World Enterprise Automation" live stream with sponsor Gluware on June 28, 2022. Gluware is a network automation vendor that's especially good at taking your existing, multi-vendor network and adding automation to it. We'd like it if you'd register to attend this hour-or-so event in real-time via https://packetpushers.net/live. Thanks!
The post Join The Packet Pushers For A Live Stream With Gluware June 28, 2022 appeared first on Packet Pushers.
Zero-trust for cloud-native workloads – part 2: Mitigating future Log4j incidents
Zero-trust for cloud-native workloads – part 2: Mitigating future Log4j incidents
In my previous blog, I introduced the brief history of zero trust, the core pillars of a zero-trust model, and how to build a zero-trust model for cloud-native workloads. In this blog, you will learn how Calico can help mitigate vulnerabilities such as the recent zero-day Log4j vulnerability with its zero-trust workload security approach.
Zero trust: a quick refresher
The starting point for building a zero-trust model is understanding your attack and protect surface. The outcome of designing your security plan should be eliminating the attack surface completely.
Enterprises are realizing that the best approach to mitigating breaches and protecting their sensitive assets from both internal and external threats is by applying the three principles of zero trust to their security plan. These three principles are:
- Always use least-privilege access
- Always authenticate and authorize before providing access
- Always assume breach
While stakeholders are busy creating design architectures, collecting asset information, and considering tools required to achieve their zero trust goals, there are also new challenges that some decision-makers should consider. As microservices are becoming the de facto standard for application developers, it has introduced new technologies and methodologies Continue reading
Early Hints update: How Cloudflare, Google, and Shopify are working together to build a faster Internet for everyone


A few months ago, we wrote a post focused on a product we were building that could vastly improve page load performance. That product, known as Early Hints, has seen wide adoption since that original post. In early benchmarking experiments with Early Hints, we saw performance improvements that were as high as 30%.
Now, with over 100,000 customers using Early Hints on Cloudflare, we are excited to talk about how much Early Hints have improved page loads for our customers in production, how customers can get the most out of Early Hints, and provide an update on the next iteration of Early Hints we’re building.
What Are Early Hints again?
As a reminder, the browser you’re using right now to read this page needed instructions for what to render and what resources (like images, fonts, and scripts) need to be fetched from somewhere else in order to complete the loading of this (or any given) web page. When you decide you want to see a page, your browser sends a request to a server and the instructions for what to load come from the server’s response. These responses are generally composed of a multitude of resources that tell the browser Continue reading
Kubernetes Unpacked 003: Beginner Lab Environments For Learning Kubernetes
Today's Kubernetes Unpacked podcast explores entry-level lab environments for IT professionals interested in learning Kubernetes, including suggestions for simple container-based apps you can run to get familiar with Kubernetes essentials.
The post Kubernetes Unpacked 003: Beginner Lab Environments For Learning Kubernetes appeared first on Packet Pushers.
Kubernetes Unpacked 003: Beginner Lab Environments For Learning Kubernetes
Today's Kubernetes Unpacked podcast explores entry-level lab environments for IT professionals interested in learning Kubernetes, including suggestions for simple container-based apps you can run to get familiar with Kubernetes essentials.A stronger bridge to Zero Trust
We know that migration to Zero Trust architecture won’t be an overnight process for most organizations, especially those with years of traditional hardware deployments and networks stitched together through M&A. But part of why we’re so excited about Cloudflare One is that it provides a bridge to Zero Trust for companies migrating from legacy network architectures.
Today, we’re doubling down on this — announcing more enhancements to the Cloudflare One platform that make a transition from legacy architecture to the Zero Trust network of the future easier than ever: new plumbing for more Cloudflare One on-ramps, expanded support for additional IPsec parameters, and easier on-ramps from your existing SD-WAN appliances.
Any on- or off-ramp: fully composable and interoperable
When we announced our vision for Cloudflare One, we emphasized the importance of allowing customers to connect to our network however they want — with hardware devices they’ve already deployed, with any carrier they already have in place, with existing technology standards like IPsec tunnels or more Zero Trust approaches like our lightweight application connector. In hundreds of customer conversations since that launch, we’ve heard you reiterate the importance of this flexibility. You need a platform that meets you where you Continue reading
Using Cloudflare Tunnel and Access with Postgres
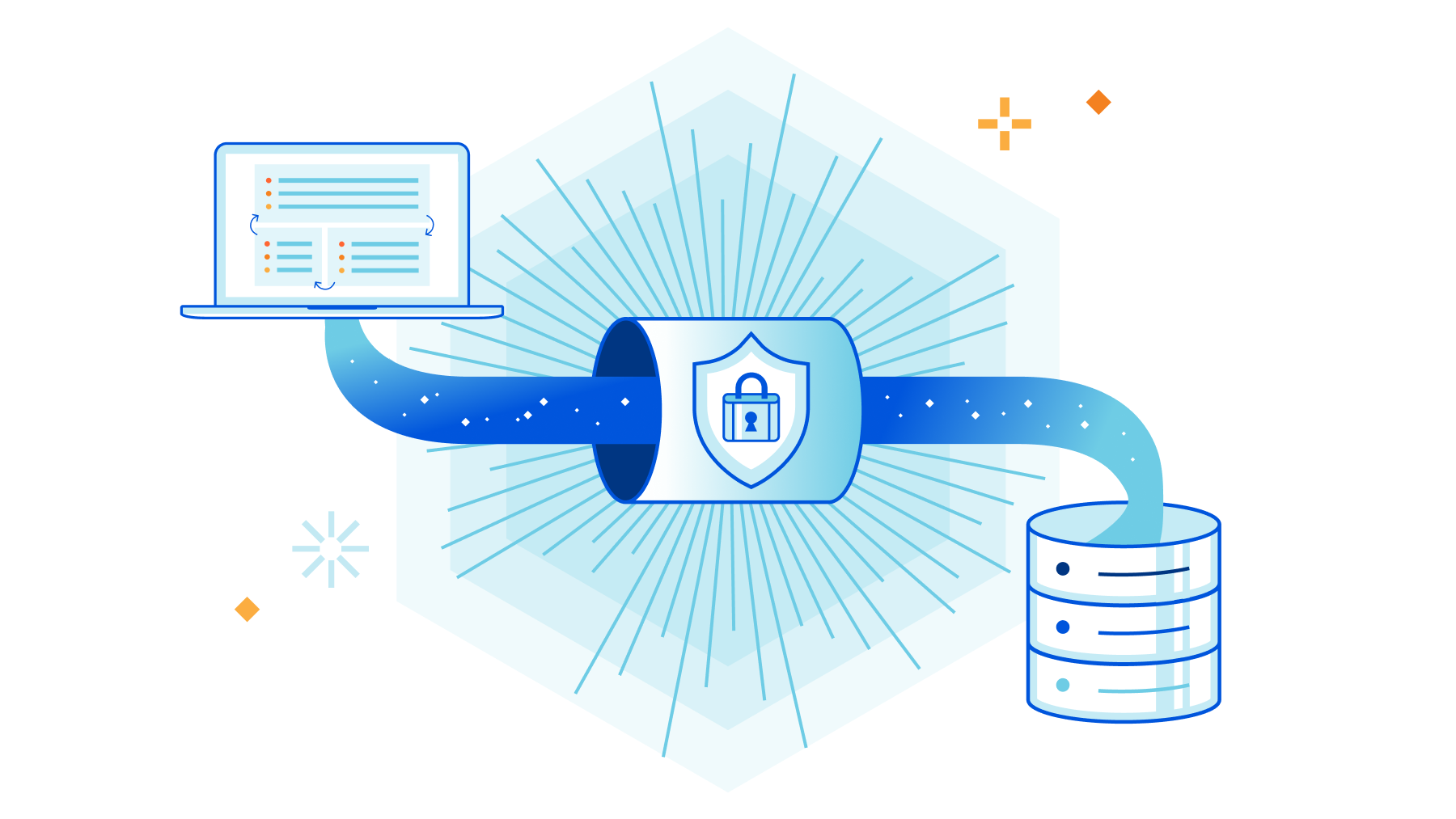
For a long time we used the traditional method of accessing internal database clusters by SSHing to a bastion host. Due to the overhead and limitations of maintaining the SSH configuration, we’ve moved to using Cloudflare Tunnels combined with Cloudflare Access to dramatically improve the user experience and onboarding times related to database access.
How we used to work
Internally we rely heavily on PostgreSQL to power many services at Cloudflare – including Stream, Images and the Cloudflare Dashboard itself. We run our Postgres clusters on our own hardware within our data centers, and they are not accessible to the public Internet, including employee laptops.
When an employee requires access to one of these databases – be it for staging environments, incident management, or supporting production services – an SSH user account is required. This SSH account has limited access on a bastion host, purely for querying databases within the data center.
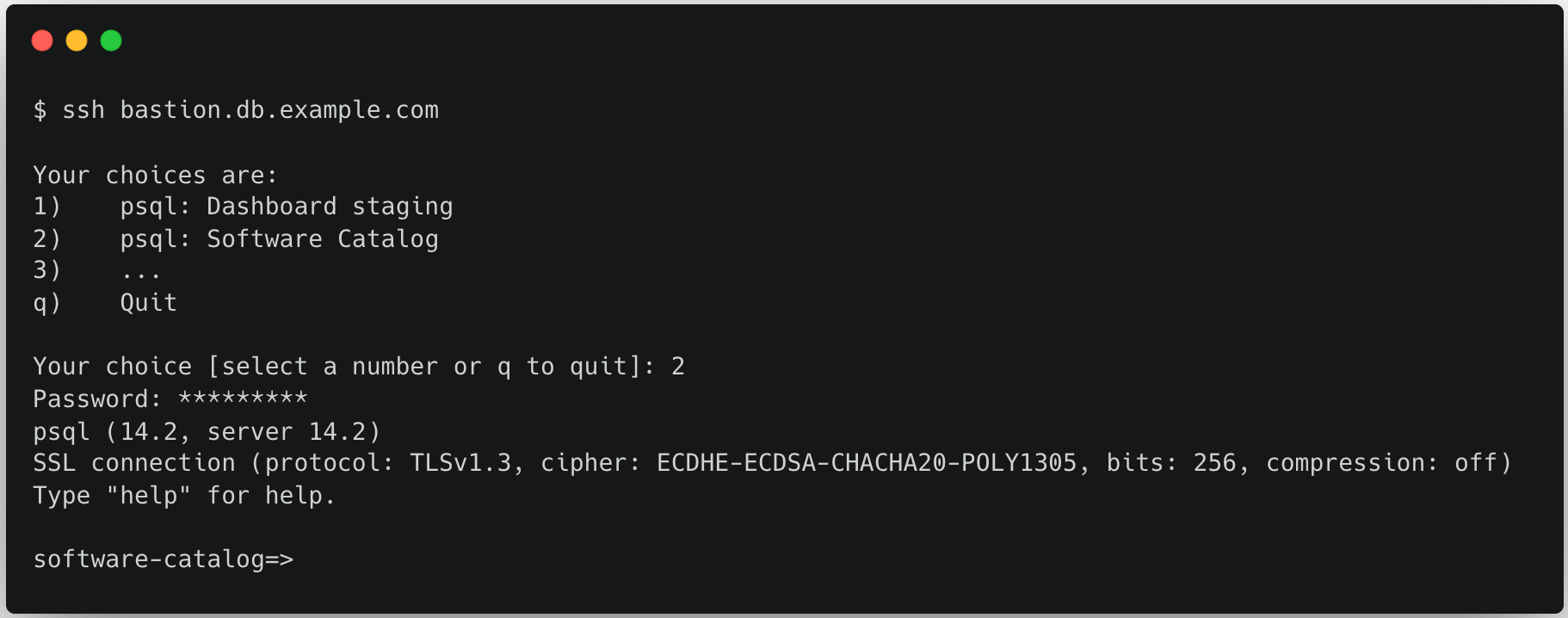
The pain we experienced
Provisioning an SSH account to these bastion hosts requires submitting a pull request to our main Infrastructure-as-Code git repository. For engineers this is a cumbersome process, and for non-engineers it is either an unnecessary learning experience, or a burden to whomever they have to Continue reading
Cloudflare integrates with Microsoft Intune to give CISOs secure control across devices, applications, and corporate networks


Today, we are very excited to announce our new integration with Microsoft Endpoint Manager (Intune). This integration combines the power of Cloudflare’s expansive network and Zero Trust suite, with Endpoint Manager. Via our existing Intune integration, joint customers can check if a device management profile such as Intune is running on the device or not and grant access accordingly.
With this expanded integration, joint customers can identify, investigate, and remediate threats faster. The integration also includes the latest information from Microsoft Graph API which provides many added, real-time device posture assessments and enables organizations to verify users' device posture before granting access to internal or external applications.
"In today’s work-from-anywhere business culture, the risk of compromise has substantially increased as employees and their devices are continuously surrounded by a hostile threat environment outside the traditional castle-and-moat model. By expanding our integration with Cloudflare, we are making it easier for joint customers to strengthen their Zero Trust security posture across all endpoints and their entire corporate network."
– Dave Randall, Sr Program Manager, Microsoft Endpoint Manager
Before we get deep into how the integration works, let’s first recap Cloudflare’s Zero Trust Services.
Cloudflare Access and Gateway
Cloudflare Access determines if Continue reading