Eurovision 2022, the Internet effect version


There’s only one song contest that is more than six decades old and not only presents many new songs (ABBA, Celine Dion, Julio Iglesias and Domenico Modugno shined there), but also has a global stage that involves 40 countries — performers represent those countries and the public votes. The 66th edition of the Eurovision Song Contest, in Turin, Italy, had two semi-finals (May 10 and 12) and a final (May 14), all of them with highlights, including Ukraine’s victory. The Internet was impacted in more than one way, from whole countries to the fan and official broadcasters sites, but also video platforms.
On our Eurovision dedicated page, it was possible to see the level of Internet traffic in the 40 participant countries, and we tweeted some highlights during the final.
#Ukraine just won the #Eurovision in Turin, #Italy
— Cloudflare Radar (@CloudflareRadar) May 14, 2022
Video platforms DNS traffic in Ukraine today, during the event, was 22% higher at 23:00 CEST compared to the previous Saturday. The @Eurovision final is being transmitted live via YouTube.
— @Cloudflare data. pic.twitter.com/juBmtDj1FP
First, some technicalities. The baseline for the values we use in the following charts Continue reading
NSX-T 3.2.1: Rolling Upgrade for NSX Management Plane
VMware NSX 3.2.1 continues to deliver enhancements for improving the VMware NSX upgrade process, including rolling upgrades that shorten upgrade maintenance windows and improved visibility into the NSX upgrade progress.
During the upgrade, the management plane will always be available, normal operation, ie, API calls, configuration changes, adding and removing Transport Nodes can be performed. If there’s an issue that occurred during the upgrade, users can roll back to the previous release without deploying a new NSX cluster and restoring the backup. The rolling upgrade feature applies to only the NSX Manager upgrade portion of the upgrade. In other words, the sequence of the NSX components upgrade remains in the following order: NSX Upgrade Coordinator upgrade, NSX Edge upgrade, Host upgrade, then the NSX Manager upgrade.
How Rolling Upgrade works
Prior to NSX 3.2.1 release, we upgrade all the manager nodes in the management cluster simultaneously. The advantage of the parallel upgrade is that it takes less time to upgrade the management plane. The tradeoff is that the management plane will not be available for a period during the upgrade process. With the rolling upgrade, the manager nodes will be upgraded sequentially. During the management upgrade Continue reading
Migrate from Cross-VC to Federation using NSX-T Migration Coordinator
NSX-T 3.2.1
With the VMware NSX-T 3.2.1 release, Migration Coordinator adds one more game changing feature: migrating from multisite NSX for vSphere deployments directly to NSX Federation. This feature builds on top of the User Defined Topology mode of migration. Folks familiar with the User Defined Topology will find the workflow similar and following the same simple model.
In this blog post, we will look at this new feature and how to leverage it. Please check out the resource links for more information on Migration Coordinator. Here, we will start with a high-level overview before digging into the details.
Migration Coordinator
Migration Coordinator is a tool that was introduced around 3 years ago, with NSX-T 2.4, to enable customers to migrate from NSX for vSphere to NSX-T. It is a free fully supported tool that is built into NSX-T. Migration Coordinator is flexible with multiple options enabling multiple ways to migrate based on customer requirements.
With the NSX-T 3.2 release, Migration Coordinator offered three primary modes for migration:
- Migrate Everything: From edges, to compute, to workloads — in an automated fashion and with a workflow that is like an in-place upgrade on existing hardware. This mode only needs enough resources to host NSX-T manager appliances and edges along Continue reading
Business Agility and Continuity with NSX Federation and Traceflow
Resilient application architectures have evolved quite significantly over the years. It is increasingly more common for Enterprises to deploy multiple data centers to support flexible workload placement and redundancy to achieve application and network high availability.
Here, we discuss key reasons to deploy multiple data centers and how NSX Federation and the recently introduced traceflow support simplify associated infrastructure strategy and implementation.
Workload Placement and Mobility
Applications and the associated infrastructure (compute, storage, networking, and security) are deployed in multiple locations to support workload mobility between these locations for use cases such as Data Center migration and Disaster Recovery testing.

Figure: Multi-Cloud Mobility
Data Center Expansion
In this scenario, IT runs out of capacity at a location (rack, building, site) and wants additional capacity at a different location for hosting new applications. Capacity can be of different types such as compute (servers), and/or storage, and/or network (bandwidth).
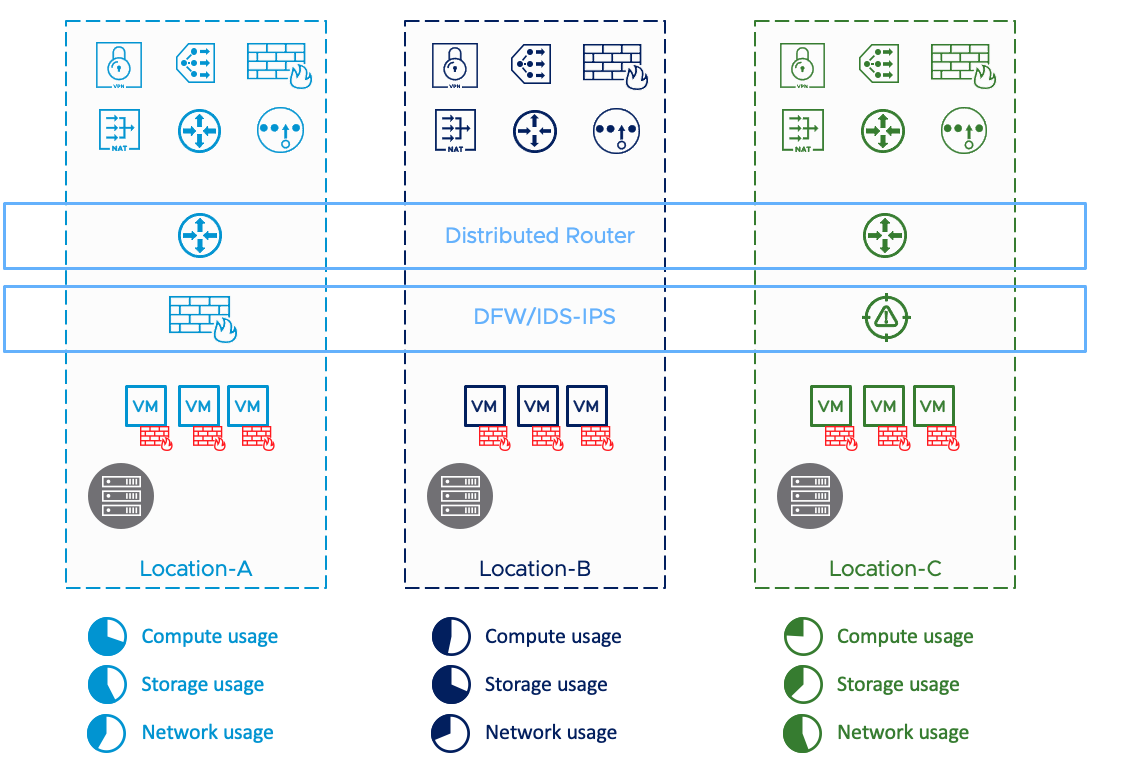
Figure: Multi-Cloud Growth
Disaster Avoidance / Disaster Recovery
This is a scenario where you lose one of your locations completely (rack, building, site) and you need to maintain the availability of your application services (compute, storage, network and security).

Figure: Multi-Location DR
Simplifying Deployment and Operations with NSX Federation
Is OpenFlow Still Kicking?
Continuing the how real is the decade-old SDN hype thread, let’s try to figure out if anyone still uses OpenFlow. OpenFlow was declared dead by the troubadour of the SDN movement in 2016, so it looks like the question is moot. However, nothing ever dies in networking (including hop-by-hop IPv6 extension headers), so here we go.
Why Would One Use OpenFlow?
Ignoring for the moment the embarrassing we solved the global load balancing with per-flow forwarding academic blunders1, OpenFlow wasn’t the worst tool for programming forwarding exceptions (ACL/PBR) into TCAM.
Is OpenFlow Still Kicking?
Continuing the how real is the decade-old SDN hype thread, let’s try to figure out if anyone still uses OpenFlow. OpenFlow was declared dead by the troubadour of the SDN movement in 2016, so it looks like the question is moot. However, nothing ever dies in networking (including hop-by-hop IPv6 extension headers), so here we go.
Why Would One Use OpenFlow?
Ignoring for the moment the embarrassing we solved the global load balancing with per-flow forwarding academic blunders1, OpenFlow wasn’t the worst tool for programming forwarding exceptions (ACL/PBR) into TCAM.
Practical OpenStack #005. How Containers help to Build OpenStack
Hello my friend,
Maintaining application in Linux may be a challenging task, especially when you have a lot of them running on a single host. One of the problems contributing to it is a dependencies management. OpenStack, in its turn, consists of a huge amount of services, which needs to run together. Containers help to solve the problem of a dependencies’ management, and, therefore, helps to setup OpenStack. In this video you will learn how that happens
Don’t Forget to Learn How to Automate All the Things
Video to the Topic
Need Help? Contract Us
If you need a trusted and experienced partner to automate your network and IT infrastructure, get in touch with us.
P.S.
If you have further questions or you need help with your networks, we are happy to assist you, just send us a message. Also don’t forget to share the article on your social media, if you like it.
BR,
Anton Karneliuk
Tech Bytes: Solving Service Networking Problems With HashiCorp’s Consul (Sponsored)
Today's sponsored Tech Bytes dives into HashiCorp's Consul product to learn how it’s evolved from its humble beginnings to become a service networking platform with features including a service mesh, service discovery, network infrastructure automation, an API gateway, and more.
The post Tech Bytes: Solving Service Networking Problems With HashiCorp’s Consul (Sponsored) appeared first on Packet Pushers.
Tech Bytes: Solving Service Networking Problems With HashiCorp’s Consul (Sponsored)
Today's sponsored Tech Bytes dives into HashiCorp's Consul product to learn how it’s evolved from its humble beginnings to become a service networking platform with features including a service mesh, service discovery, network infrastructure automation, an API gateway, and more.Day Two Cloud 147: Google Cloud Is Not Just For Devs
Today on Day Two Cloud we peel back the curtains on Google Cloud with a GCP insider to find out how Google Cloud differentiates itself, its embrace of a multi-cloud approach, and more. Our guest is Richard Seroter, Director of Outbound Product Management at Google Cloud. This is not a sponsored episode.Hedge 130: The Importance of Network Inventories
Inventories are generally hard, and hence don’t tend to be where you’d like to spend your time. The importance of having a good inventory, however, can hardly be overstated. Malcom Booden joins Tom Ammon and Russ White to talk about the importance of inventories and inventory ideas.
EVPN-VXLAN Explainer 3 – BGP UPDATE & Route Type 2
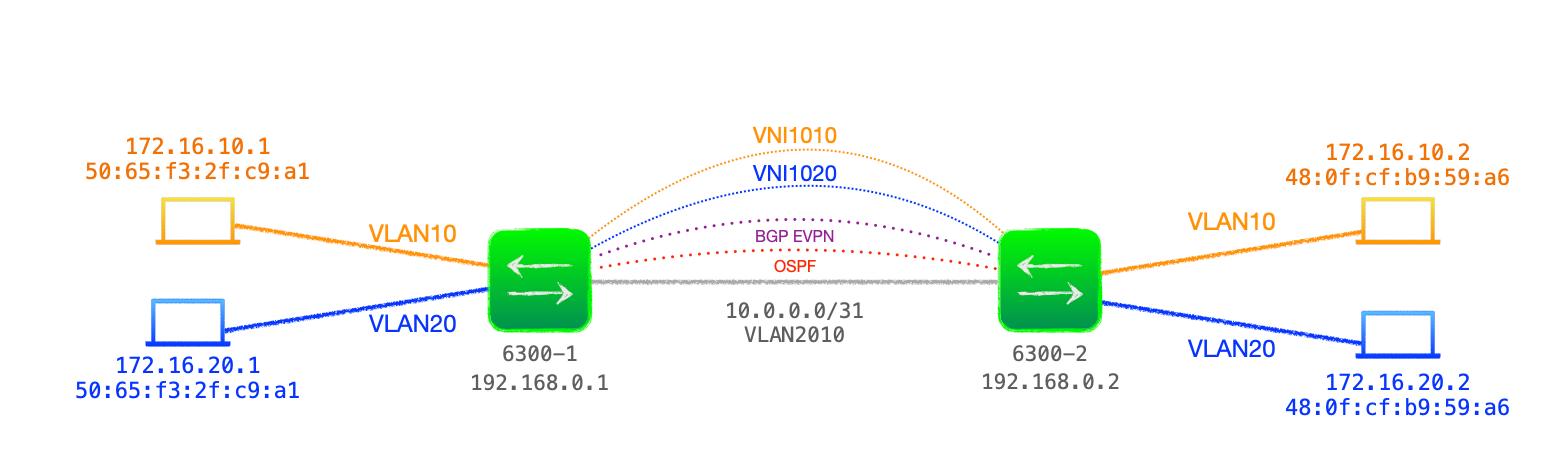
The story so far
- In post 1 we looked at VXLAN, an encapsulation type that enables L2 traffic to traverse L3 networks, the use case being virtual overlay networks to provide connectivity to VMs and containers.
- VXLAN alone uses data plane learning to build a view of the MAC addresses of the clients attached to the network. This can be suboptimal because traffic needs to hit a switch for it to learn a MAC, it is akin to basic L2 switching across the network.
- EVPN is used as a control plane for VXLAN networks, allowing peers to learn about MACs by advertising them in an extended form of BGP UPDATE.
- In post 2 we looked at the BGP EVPN session and configuration, now let's move on to advertising some routes.
Example Network - Two peers
The philosophy behind this series is start small and build. With that in mind, I'm going to start with just two EVPN peers, supporting a couple of customer VLANs.

EVPN Operations
In principle, L2VNI is very similar to the static VXLAN we saw in post 1 of this series. It consists of a Layer 2 segment that can be stretched Continue reading