Whoop Dee Doo for my SuzieQ!
or How I Gained Fabric Like Visibility on a Campus Network Without Any Upgrades Last Updated: 2022-05-05 The network automation landscape moves fast and there is always something you come across which sparks your interest, but sometimes all you can do is it make note of it and hope you have time later on to READ MORE
The post Whoop Dee Doo for my SuzieQ! appeared first on The Gratuitous Arp.
Heavy Strategy Podcast – The Great Realisation Not Great Resignation
 Heavy Strategy is about IT strategy. My co-host Johna Till-Johnson is the CEO/founder of Nemertes Research with a lot of strategy experience that combines with her technical background. The great thing is that Johna is willing to strongly debate topics. We go “head to head” and disagree to discuss. Its enjoyable and the feedback has been […]
Heavy Strategy is about IT strategy. My co-host Johna Till-Johnson is the CEO/founder of Nemertes Research with a lot of strategy experience that combines with her technical background. The great thing is that Johna is willing to strongly debate topics. We go “head to head” and disagree to discuss. Its enjoyable and the feedback has been […]
Learning BGP Module 1 Lesson 2: How BGP Builds Loop-Free Paths – Video
Russ White’s BGP series continues with a discussion of building loop-free paths with the Border Gateway Protocol (BGP). Topics include AS (Autonomous System) paths, loop prevention, why loop checks are inbound, and more on IBGP and EBGP. Russ White is a network architect, author, and instructor. You can subscribe to the Packet Pushers’ YouTube channel […]
The post Learning BGP Module 1 Lesson 2: How BGP Builds Loop-Free Paths – Video appeared first on Packet Pushers.
The deluge of digital attacks against journalists

“A free press can, of course, be good or bad, but, most certainly without freedom, the press will never be anything but bad.”
― Albert Camus

Since its founding in 1993, World Press Freedom Day has been a time to acknowledge the importance of press freedom and call attention to concerted attempts to thwart journalists’ essential work. That mission is also embedded in the foundations of our Project Galileo, which has a goal of protecting free expression online — after the war in Ukraine started, applications to the project increased by 177% in March 2022 alone.
In Uruguay today, UNESCO’s World Press Freedom Day Global Conference is underway, with a 2022 theme of “Journalism under Digital Siege.”
It is a fitting and timely theme.
While the Internet has limitless potential to make every person a publisher, bad actors — both individuals and governments — routinely deploy attacks to silence free expression. For example, Cloudflare data illustrate a trend of increased cyber attacks since the invasion of Ukraine, and journalists are frequent targets. Covering topics such as war, government corruption, and crime makes journalists vulnerable to aggression online and offline. Beyond the issue of cyber attacks, Russian authorities’ Continue reading
Wildcard proxy for everyone


Today, I have the pleasure to announce that we’re giving everyone the ability to proxy DNS wildcard records. Previously, this feature was only available to our Enterprise customers. After many of our free and pay-as-you-go users reached out, we decided that this feature should be available to everyone.
What is a wildcard DNS record?
A DNS record usually maps a domain name to one or multiple IP addresses or another resource associated with that name, so it’s a one-to-many mapping. Let’s look at an example:
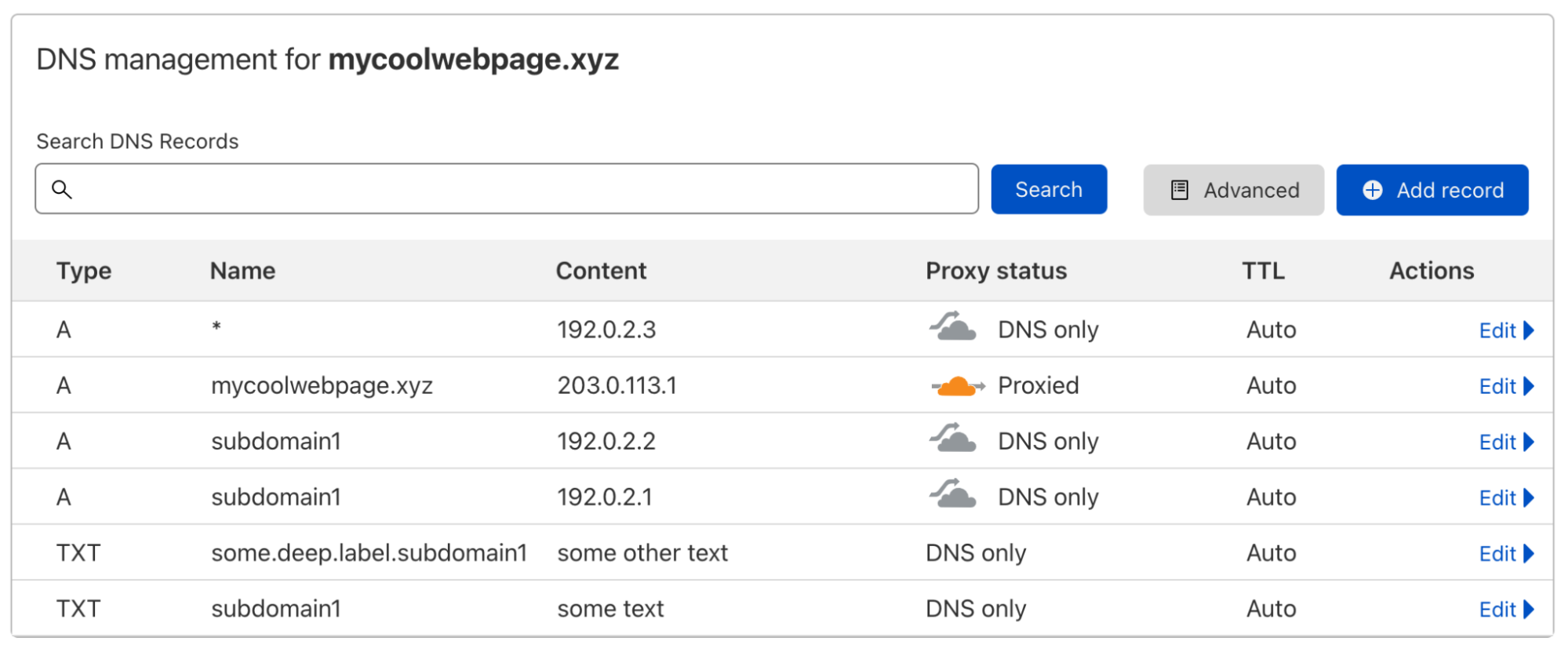
When I do a DNS lookup for the IP address of subdomain1.mycoolwebpage.xyz, I get two IP addresses back, because I have added two A records on that subdomain:
$ dig subdomain1.mycoolwebpage.xyz -t a +short
192.0.2.1
192.0.2.2
I could specify the target of all subdomains like this, with one or multiple DNS records per subdomain. But what if I have hundreds or even thousands of subdomains that I all want to point to the same resource?
This is where a wildcard DNS record comes in. By using the asterisk symbol "*" in the Name field, I can create one or multiple DNS records that are Continue reading
What Happened to FabricPath and Its Friends?
Continuing the what happened to old technologies saga, here’s another question by Enrique Vallejo:
Are FabricPath, TRILL or SPB still alive, or has everyone moved to VXLAN? Are they worth studying?
TL&DR: Barely. Yes. No.
Layer-2 Fabric craziness exploded in 2010 with vendors playing the usual misinformation games that eventually resulted in totally fragmented market full of partial- or proprietary solutions. At one point in time, some HP data center switches supported only TRILL, and other data center switches from the same company supported only SPB.
Now for individual technologies:
What Happened to FabricPath and Its Friends?
Continuing the what happened to old technologies saga, here’s another question by Enrique Vallejo:
Are FabricPath, TRILL or SPB still alive, or has everyone moved to VXLAN? Are they worth studying?
TL&DR: Barely. Yes. No.
Layer-2 Fabric craziness exploded in 2010 with vendors playing the usual misinformation games that eventually resulted in totally fragmented market full of partial- or proprietary solutions. At one point in time, some HP data center switches supported only TRILL, and other data center switches from the same company supported only SPB.
Now for individual technologies:
Learning BGP Module 1 Lesson 1: Why BGP? – Video
Russ White kicks off a ten-video series on the Border Gateway Protocol (BGP). The series is divided into two modules, with short lessons within each module. This first video covers a brief history of BGP and then gets into the purpose of BPG, reachability vs. a route, Autonomous System (AS) rules, problems that BGP solves, […]
The post Learning BGP Module 1 Lesson 1: Why BGP? – Video appeared first on Packet Pushers.
phpIPAM version 1.5 released
New version of phpipam (1.5) released.Practical Python For Networking: 7.1 Distributing Python Packages – Introduction – Video
This lesson provides an introduction to distributing Python packages. Creating packages was covered in lessons 6.1, 6.2, and 6.3. Course files are in a GitHub repository: https://github.com/ericchou1/pp_practical_lessons_1_route_alerts Additional resources: https://packaging.python.org/tutorials/packaging-projects/ https://dzone.com/articles/executable-package-pip-install Eric Chou is a network engineer with 20 years of experience, including managing networks at Amazon AWS and Microsoft Azure. He’s the founder of […]
The post Practical Python For Networking: 7.1 Distributing Python Packages – Introduction – Video appeared first on Packet Pushers.
Tech Bytes: Switching On Fortinet’s Wired, Wireless Portfolio (Sponsored)
Today on the Tech Bytes podcast, sponsored by Fortinet, we’re going to dig into Fortinet’s campus and branch switching and wireless LAN portfolio. You might think of Fortinet primarily as a firewall company, but they do much more.
The post Tech Bytes: Switching On Fortinet’s Wired, Wireless Portfolio (Sponsored) appeared first on Packet Pushers.
Tech Bytes: Switching On Fortinet’s Wired, Wireless Portfolio (Sponsored)
Today on the Tech Bytes podcast, sponsored by Fortinet, we’re going to dig into Fortinet’s campus and branch switching and wireless LAN portfolio. You might think of Fortinet primarily as a firewall company, but they do much more.Is an IP Address Protected Information?
My third article on privacy and networking is up over at Packet Pushers—