The Cloudflare network now spans 275 cities


It was just last month that we announced our network had grown to over 270 cities globally. Today, we’re announcing that with recent additions we’ve reached 275 cities. With each new city we add, we help make the Internet faster, more reliable, and more secure. In this post, we’ll talk about the cities we added, the performance increase, and look closely at our network expansion in India.
The Cities
Here are the four new cities we added in the last month: Ahmedabad, India; Chandigarh, India; Jeddah, Saudi Arabia; and Yogyakarta, Indonesia.
A closer look at India
India is home to one of the largest and most rapidly growing bases of digital consumers. Recognising this, Cloudflare has increased its footprint in India in order to optimize reachability to users within the country.
Cloudflare’s expansion in India is facilitated through interconnections with several of the largest Internet Service Providers (ISPs), mobile network providers and Internet Exchange points (IXPs). At present, we are directly connected to the major networks that account for more than 95% of the country’s broadband subscribers. We are continuously working to not only expand the interconnection capacity and locations with these networks, but also establish Continue reading
Practical Python For Networking: 6.4 – Run Package Example – Video
Now that you’ve learned how to put together a package, this lesson shows you how to call that package in a script. Course files are in a GitHub repository: https://github.com/ericchou1/pp_practical_lessons_1_route_alerts Eric Chou is a network engineer with 20 years of experience, including managing networks at Amazon AWS and Microsoft Azure. He’s the founder of Network […]
The post Practical Python For Networking: 6.4 – Run Package Example – Video appeared first on Packet Pushers.
Video: The Long Tail of AI/ML Problems
It’s time for the bad part of AI/ML in Networking: Good, Bad, and Ugly webinar. After describing the potential AI/ML wins, Javier Antich walked us through the long tail of AI/ML problems.
Video: The Long Tail of AI/ML Problems
It’s time for the bad part of AI/ML in Networking: Good, Bad, and Ugly webinar. After describing the potential AI/ML wins, Javier Antich walked us through the long tail of AI/ML problems.
Secret Management with HashiCorp Vault

Many applications these days require authentication to external systems with resources, such as users and passwords to access databases and service accounts to access cloud services, and so on. In such cases, private information, like passwords and keys, becomes necessary. It is essential to take extra care in managing such sensitive data. For example, if you write your AWS key information or password in a script for deployment and then push it to a Git repository, all users who can read it will also be able to access it, and you could be in trouble. Even if it's an internal repository, you run the risk of a potential leak.
How we were managing secrets in the service
Before we talk about Vault, let's take a look at how we've used to manage secrets.
Salt
We use SaltStack as a bare-metal configuration management tool. The core of the Salt ecosystem consists of two major components: the Salt Master and the Salt Minion. The configuration state is owned by Salt Master, and thousands of Salt Minions automatically install packages, generate configuration files, and start services to the node based on the state. The state may contain secrets, such as passwords and API Continue reading
Research Paper: One to Rule them All? A First Look at DNS over QUIC
 Research paper on DNS over QUIC suggests faster than DOT & DOH
Research paper on DNS over QUIC suggests faster than DOT & DOH
Practical Python For Networking: 6.3 – Making A Simple Package Example – Video
This lesson walks through the creation of a simple package. Course files are in a GitHub repository: https://github.com/ericchou1/pp_practical_lessons_1_route_alerts Eric Chou is a network engineer with 20 years of experience, including managing networks at Amazon AWS and Microsoft Azure. He’s the founder of Network Automation Nerds and has written the books Mastering Python Networking and Distributed […]
The post Practical Python For Networking: 6.3 – Making A Simple Package Example – Video appeared first on Packet Pushers.
Outburst: Can SONiC become the Linux of Network Operating Systems? – YouTube
 Useful business primer on why and what of SONIC
Useful business primer on why and what of SONIC
Who is Right About Edge Computing?
Edge will ultimately succeed (or fail) based on its ability to address the operational experience of those tasked with deploying and operating the its workloads.Creating MPLS/VPN Labs With netsim-tools
Two week ago I described how to create a simple VRF Lite lab with netsim-tools VRF configuration module. Adding MPLS/VPN to the mix and creating a full-blown MPLS/VPN lab is a piece of cake. In this blog post we’ll build a simple topology with two VRFs (red and blue) and two PE-routers:
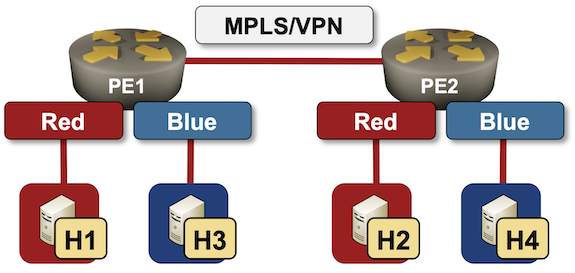
Lab topology
Creating MPLS/VPN Labs With netlab
Two week ago I described how to create a simple VRF Lite lab with netlab VRF configuration module. Adding MPLS/VPN to the mix and creating a full-blown MPLS/VPN lab is a piece of cake. In this blog post we’ll build a simple topology with two VRFs (red and blue) and two PE-routers:

Lab topology
Using LEOs and GEOs
Once you head off the main roads your Internet connectivity options are often pretty limited. However, things are improving, and in Australia you can use an Internet service based on a connection through a geostationary satellite connection or you could sign up for Starlink, a Low Earth Orbit service. Both services offer decent capacity, but there are some some other critical differences going on here. Let's look at these services using a custom test rig to put them through their paces.EVPN-VXLAN Explainer 2 – The BGP Session
In this second post I will look at Ethernet VPN (EVPN), what is it and how to configure a BGP EVPN session on Aruba devices.
Please note, this post will focus on the establishment of the BGP EVPN session between peers, and thus will not present a fully functioning EVPN network. I aim to build the configuration up in stages to enable the reader to confidently understand the different pieces of EVPN-VXLAN as a technology.
Ethernet VPN - the VPLS successor seen about campus
Reading through EVPN RFCs one gets an impression of its convoluted development, or rather, the evolving area of focus for its application.
To summarize, it started life as a service-provider focused VPLS successor, then jumped over to the control plane for virtualized data centres, now gaining a foothold in campus networks.
I put together an overview of the various RFCs here.
EVPN - what is it used for?
In the first post in this series, I explained the VXLAN forwarding process, that relies upon flood and learn.
- VXLAN is a data plane technology, concerned with the forwarding of packets and what headers to add to data.
- EVPN is a control plane technology, concerned with building a Continue reading
Protecting The Hybrid Workforce With Palo Alto Networks Secure, Flexible SASE Solution
Palo Alto Networks announces new innovations for Prisma SASE for protecting the hybrid workforce, including the general availability of Prisma SD-WAN bandwidth licensing on-demand and Okyo Garde Enterprise Edition.
The post Protecting The Hybrid Workforce With Palo Alto Networks Secure, Flexible SASE Solution appeared first on Packet Pushers.