Introduction to Pulumi for Infrastructure as Code Deployments
Introduction I’ve been itching to introduce Pulumi to you all for the longest time. I heard about Pulumi in the mid-point of 2021. At the time I was going through Microsoft AZ-700 studies and figured it would be fun to double up the learning and get my hands on Pulumi. Long story short, I really […]
The post Introduction to Pulumi for Infrastructure as Code Deployments appeared first on Packet Pushers.
Worth Reading: Career Advice I’d Give to Younger Me
You MUST read the next masterpiece coming from Ethan Banks: Career Advice I’d Give To 20, 30 and 40-Something Year Old Me. I found this bit particularly relevant:
Your life is at least half over. Stop wasting time doing things other people think is important.
If only Ethan would have told me that wisdom ten years ago.
Worth Reading: Career Advice I’d Give to Younger Me
You MUST read the next masterpiece coming from Ethan Banks: Career Advice I’d Give To 20, 30 and 40-Something Year Old Me. I found this bit particularly relevant:
Your life is at least half over. Stop wasting time doing things other people think are important.
If only Ethan would have told me that wisdom ten years ago.
VPP Configuration – Part2
About this series
I use VPP - Vector Packet Processor - extensively at IPng Networks. Earlier this year, the VPP community merged the Linux Control Plane plugin. I wrote about its deployment to both regular servers like the Supermicro routers that run on our AS8298, as well as virtual machines running in KVM/Qemu.
Now that I’ve been running VPP in production for about half a year, I can’t help but notice one specific
drawback: VPP is a programmable dataplane, and by design it does not include any configuration or
controlplane management stack. It’s meant to be integrated into a full stack by operators. For end-users,
this unfortunately means that typing on the CLI won’t persist any configuration, and if VPP is restarted,
it will not pick up where it left off. There’s one developer convenience in the form of the exec
command-line (and startup.conf!) option, which will read a file and apply the contents to the CLI line
by line. However, if any typo is made in the file, processing immediately stops. It’s meant as a convenience
for VPP developers, and is certainly not a useful configuration method for all but the simplest topologies.
Luckily, VPP comes Continue reading
Moonlander Keyboard
For the past year and a half or so, I have been using the Keycaps I didn't like they keycaps that shipped with the board (although they were fine). I swapped them out for these retro gaming style XDA profile keycaps. XDA profile keys are all the same height and shape. Key Switches I...continue reading
Heavy Networking 624: Solving Network Problems With Opmantek’s NMIS (Sponsored)
On today's sponsored Heavy Networking we speak with Opmantek, a FirstWave company. Opmantek's NMIS is a suite of network monitoring applications for managing fault, performance, configuration, compliance and automation. It supports multi-vendor, multi-tenant and multi-server solutions. We discuss the latest features and real-world use cases.
The post Heavy Networking 624: Solving Network Problems With Opmantek’s NMIS (Sponsored) appeared first on Packet Pushers.
Heavy Networking 624: Solving Network Problems With Opmantek’s NMIS (Sponsored)
On today's sponsored Heavy Networking we speak with Opmantek, a FirstWave company. Opmantek's NMIS is a suite of network monitoring applications for managing fault, performance, configuration, compliance and automation. It supports multi-vendor, multi-tenant and multi-server solutions. We discuss the latest features and real-world use cases.Fast Friday Thoughts on Leadership

I’m once more taking part in the BSA Wood Badge leadership course for my local council. I enjoy the opportunity to hone my skills when it comes to leading others and teaching them how to train their own leaders. A lot of my content around coaching, mentoring, and even imposter syndrome has come from the lessons I’ve learned during Wood Badge. It sounds crazy but I enjoy taking vacation time to staff something that looks like work because it feels amazing!
A few random thoughts from the week:
- You need a sense of urgency in everything you do. You may not know exactly what’s coming or how to adjust for what needs to be done but you need to be moving with purpose to get it done. Not only does that help you with your vision to make things happen but it encourages others to do the same.
- Team building happens when you’re not focused entirely on the goal. It doesn’t take much for your group to come together but it can only happen when they aren’t charging toward the finish line. Remember that taking a few moments here and there to reinforce the group dynamic can do a lot Continue reading
The end of the road for Cloudflare CAPTCHAs
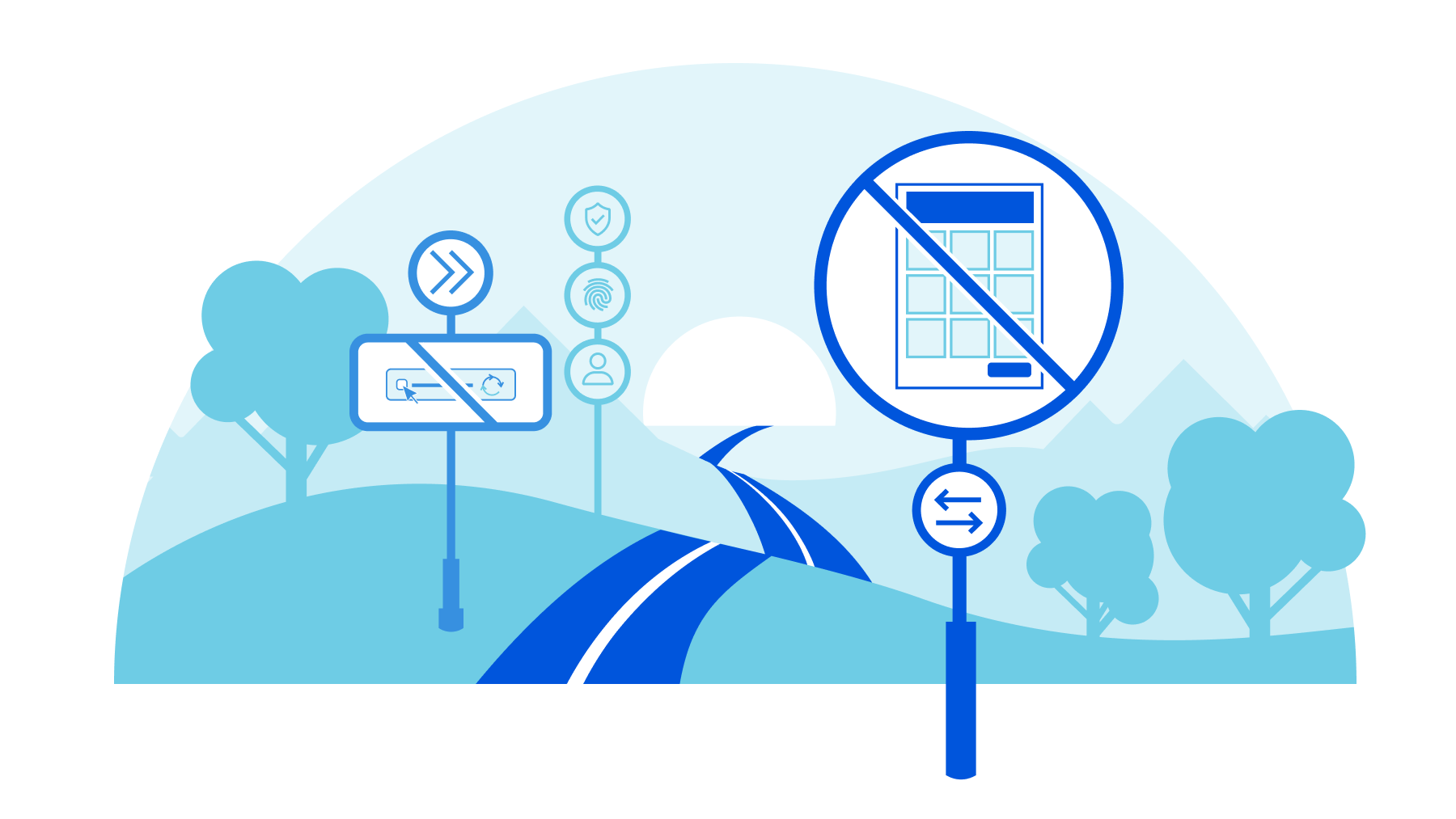
There is no point in rehashing the fact that CAPTCHA provides a terrible user experience. It's been discussed in detail before on this blog, and countless times elsewhere. One of the creators of the CAPTCHA has publicly lamented that he “unwittingly created a system that was frittering away, in ten-second increments, millions of hours of a most precious resource: human brain cycles.” We don’t like them, and you don’t like them.
So we decided we’re going to stop using CAPTCHAs. Using an iterative platform approach, we have already reduced the number of CAPTCHAs we choose to serve by 91% over the past year.
Before we talk about how we did it, and how you can help, let's first start with a simple question.
Why in the world is CAPTCHA still used anyway?
If everyone agrees CAPTCHA is so bad, if there have been calls to get rid of it for 15 years, if the creator regrets creating it, why is it still widely used?
The frustrating truth is that CAPTCHA remains an effective tool for differentiating real human users from bots despite the existence of CAPTCHA-solving services. Of course, this comes with a huge trade off in terms Continue reading
Video: Combining Data-Link- and Network Layer Addresses
The previous videos in the How Networks Really Work webinar described some interesting details of data-link layer addresses and network layer addresses. Now for the final bit: how do we map an adjacent network address into a per-interface data link layer address?
If you answered ARP (or ND if you happen to be of IPv6 persuasion) you’re absolutely right… but is that the only way? Watch the Combining Data-Link- and Network Addresses video to find out.
Video: Combining Data-Link- and Network Layer Addresses
The previous videos in the How Networks Really Work webinar described some interesting details of data-link layer addresses and network layer addresses. Now for the final bit: how do we map an adjacent network address into a per-interface data link layer address?
If you answered ARP (or ND if you happen to be of IPv6 persuasion) you’re absolutely right… but is that the only way? Watch the Combining Data-Link- and Network Addresses video to find out.
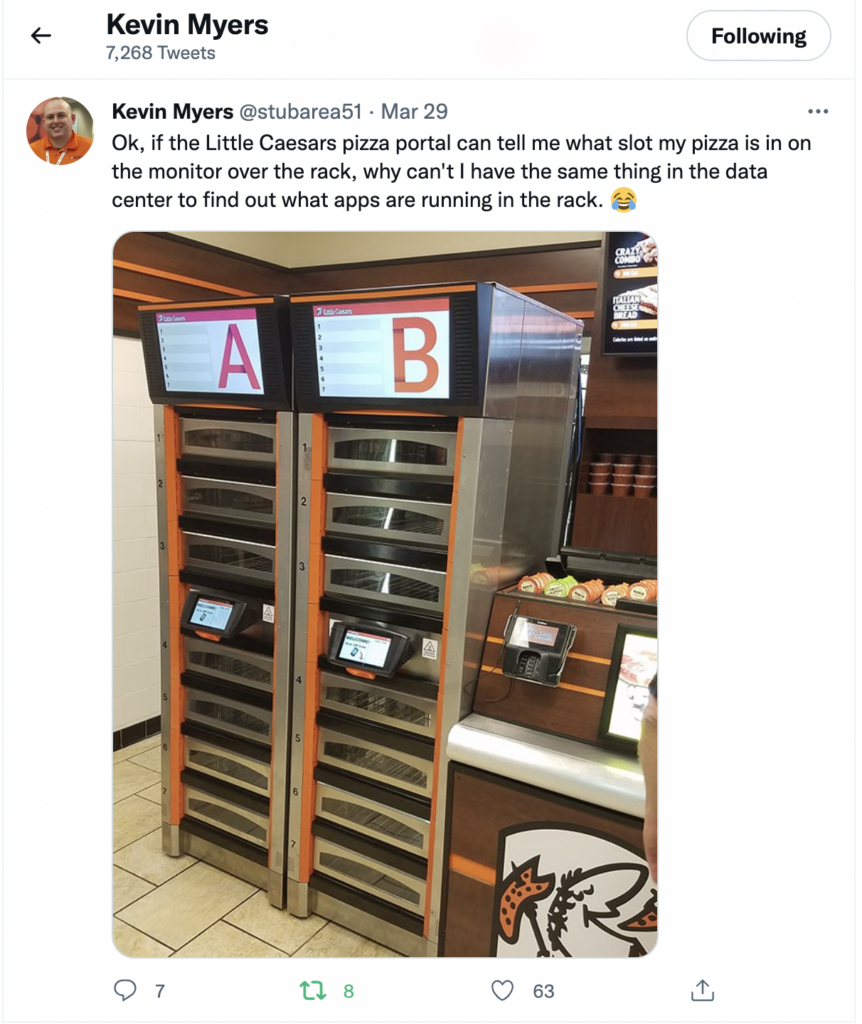
App delivery for an improved pizza experience
It’s been a while since we started work on one of our newest projects. We have been trying to solve a problem in app location. It all came from the notion that Little Caesars know where my pizza is, so why can’t the network resolve where the app is? We also thought it would be novel use of Anycast because the app can be anywhere.
So, what problems specifically have we solved using this design? Intent based gateways are a signaling mechanism allows the apps to be delivered along with the pizza. As we can see app Buffalo Wings can reach both the intent based gateway and Fried Pickles using TI-LFA, which strips the fat bits before they reach the gateway. Our unique caching solution using Tupperware, which are stacked in K8s, allows for the apps to be delivered in a bursty nexthop specific competitive manner. This has proven to keep the apps warm within the physical layer.
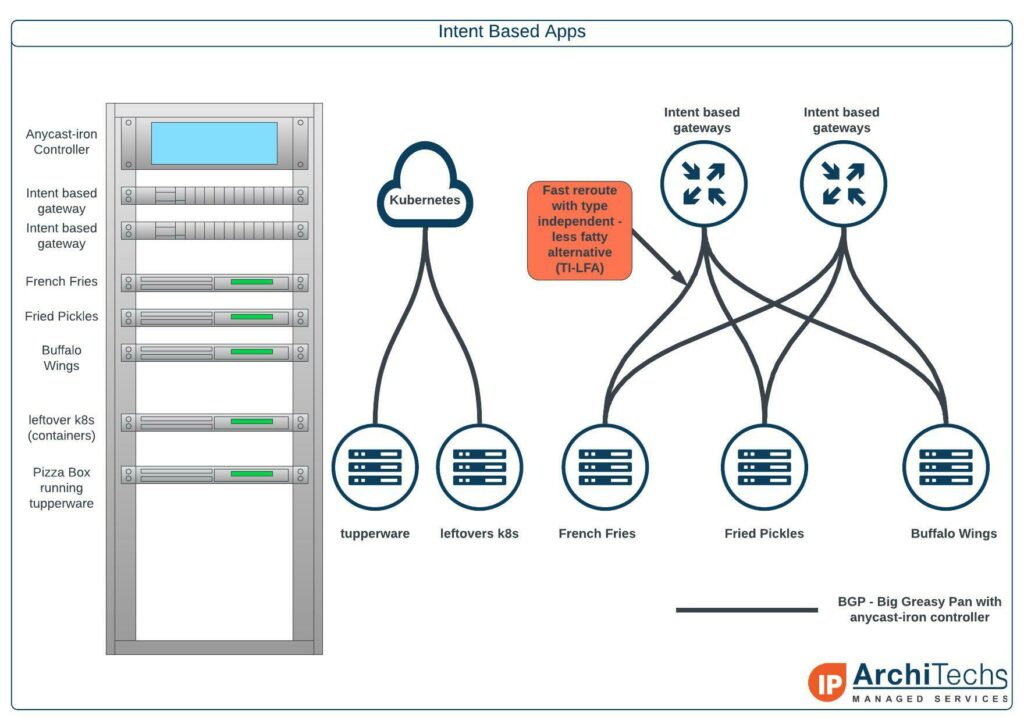
In our example, the Delivery Center Interconnect, we are doing an east to west Multi Pizza Layered Service that can drop the apps with full BTU into any of the regions. The apps are Continue reading
Infosec Useful Resources
This post is a collection of links to resources I have found useful on infosec related topics. CVE {{ link.href( path="https://www.exploit-db.com/", description="Exploit DB" ) }} - CVE compliant archive of public exploits and corresponding vulnerable software,...continue reading
Infosec Useful Resources
This post is a collection of links to resources I have found useful on infosec related topics. CVE {{ link.href( path="https://www.exploit-db.com/", description="Exploit DB" ) }} - CVE compliant archive of public exploits and corresponding vulnerable software,...continue reading
A Walk-Through Of Fortinet’s Zero Trust Network Access (ZTNA) Architecture
Fortinet’s Zero Trust Network Access (ZTNA) lets network and security teams enforce fine-grained access policies for users working remotely and in the office. It can control access to applications hosted on premises, in the public cloud, or delivered via SaaS. This post walks through the elements required to deploy ZTNA and offers advice on transitioning to a zero-trust approach.
The post A Walk-Through Of Fortinet’s Zero Trust Network Access (ZTNA) Architecture appeared first on Packet Pushers.