is CCIE still worth it in 2022? CCIE vs Network Automation or something else?
Is CCIE still worth it in 2022?
I have been seeing this discussion on social media, especially Linkedin and Twitter for some time. In this post, I will be sharing my opinions on it and hope it can help the decision of some Network Engineers who follow our blog.
As of 2022, you may realize that many Evolving Technologies getting a lot of attention and I think, most of them deserve the attention.
These are SD-WAN, SDA, Cloud Computing, Network Automation and Programmability, SDN, IOT we can say. Of course, there are many other technologies if you are dealing with Security, Wireless, Service Provider, Datacenter or many other domains of IT.
But, as a certification, if we remember the subject of this post: Is CCIE still worth it in 2022?.
CCIE is not just a technology but as a certificate, deals with many technologies and products.

And, there are many different CCIE Tracks. CCIE Enterprise is the most popular one and I will give my examples by using CCIE Enterprise Infrastructure Exam as it is the by far most popular and most well-known by the Network Engineering community.
CCIE Enterprise Infrastructure exam doesn’t only cover Continue reading
Chiplets: The First Step To Integrated Silicon Photonics For Faster Interconnects At Lower Cost
Merchant silicon applies Moore’s Law to Ethernet switching with astounding results, well documented by tech luminary Andy Bechtolsheim almost four years ago. Since then, switch chips have doubled their throughput to 25.6 Tbps, powering products with up to 64 400GbE interfaces. The problem arises when trying to transmit electrical signals off chip because the power […]
The post Chiplets: The First Step To Integrated Silicon Photonics For Faster Interconnects At Lower Cost appeared first on Packet Pushers.
6 Barriers to Moving and Managing Legacy Data to the Cloud
When moving legacy data to cloud, companies must overcome several barriers to take full advantage of the benefits a cloud architecture can offer.Cisco NCS 5500 Series Routers
Cisco already supports industry standard sFlow telemetry across a range of products and the recent IOS-XR Release 7.5.1 extends support to Cisco NCS 5500 series routers.
Note: The NCS 5500 series routers also support Cisco Netflow. Rapidly detecting large flows, sFlow vs. NetFlow/IPFIX describes why you should choose sFlow if you are interested in real-time monitoring and control applications.
flow exporter-map SF-EXP-MAP-1
version sflow v5
!
packet-length 1468
transport udp 6343
source GigabitEthernet0/0/0/1
destination 192.127.0.1
dfbit set
!
Configure the sFlow analyzer address in an exporter-map.
flow monitor-map SF-MON-MAP
record sflow
sflow options
extended-router
extended-gateway
if-counters polling-interval 300
input ifindex physical
output ifindex physical
!
exporter SF-EXP-MAP-1
!
Configure sFlow options in a monitor-map.
sampler-map SF-SAMP-MAP
random 1 out-of 20000
!
Define the sampling rate in a sampler-map.
interface GigabitEthernet0/0/0/3
flow datalinkframesection monitor-map SF-MON-MAP sampler SF-SAMP-MAP ingress
Enable sFlow on each interface for complete visibilty into network traffic.
The diagram shows the general architecture of an sFlow monitoring deployment. All the switches stream sFlow telemetry to a central sFlow analyzer Continue reading
Email Routing is now in open beta, available to everyone


I won’t beat around the bush: we’ve moved Cloudflare Email Routing from closed beta to open beta 🎉
What does this mean? It means that there’s no waitlist anymore; every zone* in every Cloudflare account has Email Routing available to them.
To get started just open one of the zones in your Cloudflare Dashboard and click on Email in the navigation pane.

Our journey so far
Back in September 2021, during Cloudflare’s Birthday Week, we introduced Email Routing as the simplest solution for creating custom email addresses for your domains without the hassle of managing multiple mailboxes.
Many of us at Cloudflare saw a need for this type of product, and we’ve been using it since before it had a UI. After Birthday Week, we started gradually opening it to Cloudflare customers that requested access through the wait list; starting with just a few users per week and gradually ramping up access as we found and fixed edge cases.
Most recently, with users wanting to set up Email Routing for more of their domains and with some of G Suite legacy users looking for an alternative to starting a subscription, we have been onboarding tens of thousands of new zones Continue reading
Mixed Feelings about BGP Route Reflector Cluster ID
Here’s another BGP Route Reflector myth:
In a redundant design, you should use Route Reflector Cluster ID to avoid loops.
TL&DR: No.
While BGP route reflectors can cause permanent forwarding loops in sufficiently broken topologies, the Cluster ID was never needed to stop a routing update propagation loop:
Mixed Feelings about BGP Route Reflector Cluster ID
Here’s another BGP Route Reflector myth:
In a redundant design, you should use Route Reflector Cluster ID to avoid loops.
TL&DR: No.
While BGP route reflectors can cause permanent forwarding loops in sufficiently broken topologies, the Cluster ID was never needed to stop a routing update propagation loop:
Making the network (even) more consumable: Salty minions for cloudlubbers ☁️
Building and integrating custom SR Linux agents — part Ⅱ

A ‘lubber’ is a “big, clumsy person”, a word more commonly used in the form of ‘landlubber’ meaning someone unfamiliar with the sea or sailing. The latter was first recorded back in 1690, combining the Middle English word ‘lubber’ (~1400) with the Germanic — or Dutch — ‘land’: “A definite portion of the earth’s surface owned by an individual or home of a nation”.
The process of combining two words to form a new one is called ‘nominal composition’ and it is used a lot in my native Dutch language. Technically this means that Dutch has exponentially more words than English for example, though we can’t be bothered to list them in dictionaries — we simply invent them as needed (against the advice of my browser’s spellchecker who argues “cloudlubber” should be written as two separate words, silly machine)
Found at the bottom of that dictionary list: Toki Pona — “simple language” — is a minimalistic constructed language consisting of only 120 words. It uses only 14 letters — a e i j k l m n o p s t u w — to form words
Insulting one’s audience from the start is generally considered bad practice, but we’re ok because I wasn’t talking Continue reading
Same, But Wildly Different: Securing Azure AD vs. AD On-Prem
Here are the most significant ways in which Azure AD security differs from that of AD on-premises, and what AD admins charged with securing both need to know.How To Pass API Query Parameters In A Curl Request
If you’re using CLI tool curl to retrieve data from a remote API, you might send forth a command like so.
curl -H "Authorization: Bearer access_token_goes_here" \ https://api.provider.com/thing/you_want/index.json
That results in a lovely JSON payload that makes you happy.
Let’s say that according to the API documentation, /thing/you_want/ accepts query parameters so that you can scope what you want to know about. Excellent! Instinctively, you try the following…
curl -H "Authorization: Bearer access_token_goes_here" \ https://api.provider.com/thing/you_want/index.json?scope=1
Rather than a scoped JSON payload that also makes you happy, you get back a message indicating that the API endpoint is displeased. Your sacrifice was deemed unworthy. Nay, YOU are unworthy. You are decidedly not happy.
What has gone wrong to anger the API gods so? You asked the wrong question of the API. More accurately, curl hasn’t formatted the request in quite the way you intuited it would.
To appease the API deities, the appropriate sacrifice comes in the form of a tweaked curl command. For example…
curl -G -H "Authorization: Bearer access_token_goes_here" \ https://api.provider.com/thing/you_want/index.json \ -d "query=scope=1"
We added a “-G” flag to make sure curl is sending a GET and not Continue reading
Tech Bytes: AppNeta Provides SASE Observability For Ops Teams (Sponsored)
Today on the Tech Bytes podcast we’re talking about how to get end-to-end observability into cloud-delivered security, including Cloud Access Security Brokers (CASBs) and SASE. Our sponsor is AppNeta.
The post Tech Bytes: AppNeta Provides SASE Observability For Ops Teams (Sponsored) appeared first on Packet Pushers.
Tech Bytes: AppNeta Provides SASE Observability For Ops Teams (Sponsored)
Today on the Tech Bytes podcast we’re talking about how to get end-to-end observability into cloud-delivered security, including Cloud Access Security Brokers (CASBs) and SASE. Our sponsor is AppNeta.Emotet Is Not Dead (Yet) – Part 2
Emotet attacks leveraging malicious macros embedded in Excel files continue, with new variants and novel tactics, techniques, and procedures (TTPs). Following our recent report, we observed new waves of Emotet campaigns abusing legitimate Windows features, such as batch scripts and the mshta utility, combined with PowerShell, to deliver Emotet payloads.
In this follow-up blog post, we first provide an overview of the delivery processes of Emotet payloads in typical attacks. Then, we examine the recent variants and reveal how techniques evolved in these attacks.
Emotet payload delivery chain
The Emotet infection chain typically starts with a spam email containing a malicious document in the attachment (see Figure 1). The attachment can be either a Word document or an Excel file with embedded VBA or Excel 4.0 (XL4) macros. To entice the user to enable macro execution in Microsoft Word or Excel, the file displays social engineering content when opened. Once macro execution has been enabled, the embedded macro is executed, leading to the delivery process of an Emotet payload.

Figure 1: A typical Emotet payload delivery chain.
As highlighted in Figure 1, there are typically two ways to deliver an Emotet payload:
- Executing macros to download the payload Continue reading
Slicing and Dicing Instant Logs: Real-time Insights on the Command Line


During Speed Week 2021 we announced a new offering for Enterprise customers, Instant Logs. Since then, the team has not slowed down and has been working on new ways to enable our customers to consume their logs and gain powerful insights into their HTTP traffic in real time.
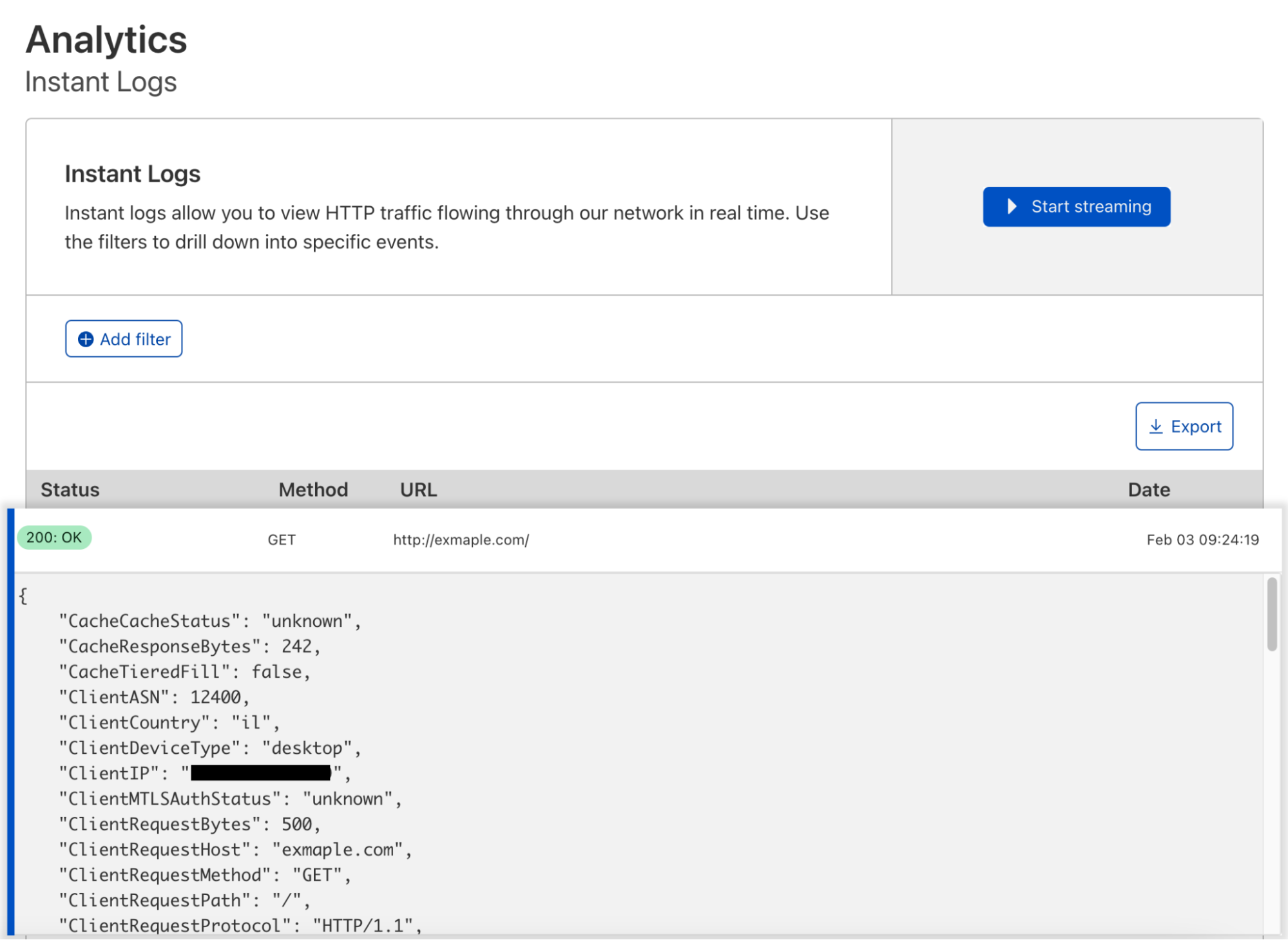
We recognize that as developers, UIs are useful but sometimes there is the need for a more powerful alternative. Today, I am going to introduce you to Instant Logs in your terminal! In order to get started we need to install a few open-source tools to help us:
- Websocat - to connect to WebSockets.
- Angle Grinder - a utility to slice-and-dice a stream of logs on the command line.
Creating an Instant Log’s Session
For enterprise zones with access to Instant Logs, you can create a new session by sending a POST request to our jobs' endpoint. You will need:
- Your Zone Tag / ID
- An Authentication Key or an API Token with at least the Zone Logs Read permission
curl -X POST 'https://api.cloudflare.com/client/v4/zones/${ZONE_ID}/logpush/edge/jobs' \
-H 'X-Auth-Key: <KEY>' \
-H 'X-Auth-Email: <EMAIL>' \
-H 'Content-Type: application/json' \
--data-raw '{
"fields": "ClientIP,ClientRequestHost,ClientRequestMethod,ClientRequestPath,EdgeEndTimestamp,EdgeResponseBytes,EdgeResponseStatus,EdgeStartTimestamp,RayID",
"sample": 1,
"filter": "",
"kind": "instant-logs"
}'
Response
The Continue reading
Network Break 368: Juniper, Cato Advance Cloud-Based Security Offerings; Citrix Gets Acquired
Take a Network Break! This week’s tech news includes new cloud-delivered security services from Juniper Networks and Cato Networks, new firewall hardware from Fortinet, prognostications on the campus switch market, Cisco teasing a private 5G service, and more.
The post Network Break 368: Juniper, Cato Advance Cloud-Based Security Offerings; Citrix Gets Acquired appeared first on Packet Pushers.
Network Break 368: Juniper, Cato Advance Cloud-Based Security Offerings; Citrix Gets Acquired
Take a Network Break! This week’s tech news includes new cloud-delivered security services from Juniper Networks and Cato Networks, new firewall hardware from Fortinet, prognostications on the campus switch market, Cisco teasing a private 5G service, and more.How to Celebrate Valentine’s Day with Your Single Friends
Valentine’s Day is just a few months away, so it’s time to think about what you’re going to do this year. It is believed that Valentine’s Day is just for people who are romantically and passionately in love. However that is not the case, you can still enjoy Valentine’s Day with your loved ones even if you are single. This article will teach you how to celebrate Valentine’s Day with your single friends, no matter where they are in their dating journey!
Have a Movie Marathon
You and your single friends can get together to watch movies. The best thing about this is you don’t even have to change out of your pajamas! Buy a big tub of popcorn, order some pizzas and cuddle up on the couch surrounded by blankets. You’ll all love this because it’s just like being in high school again!
Go To a Comedy Show
If you’re looking for something more interactive than watching movies, then check out a comedy show! It will be exciting and hilarious at once so everyone should enjoy themselves.
Valentine’s Day Charity Event
Another option is to do a charity event. You and your single friends can volunteer at an Continue reading

