Cloudflare Partner Program Now Supports SASE & Zero Trust Managed Services

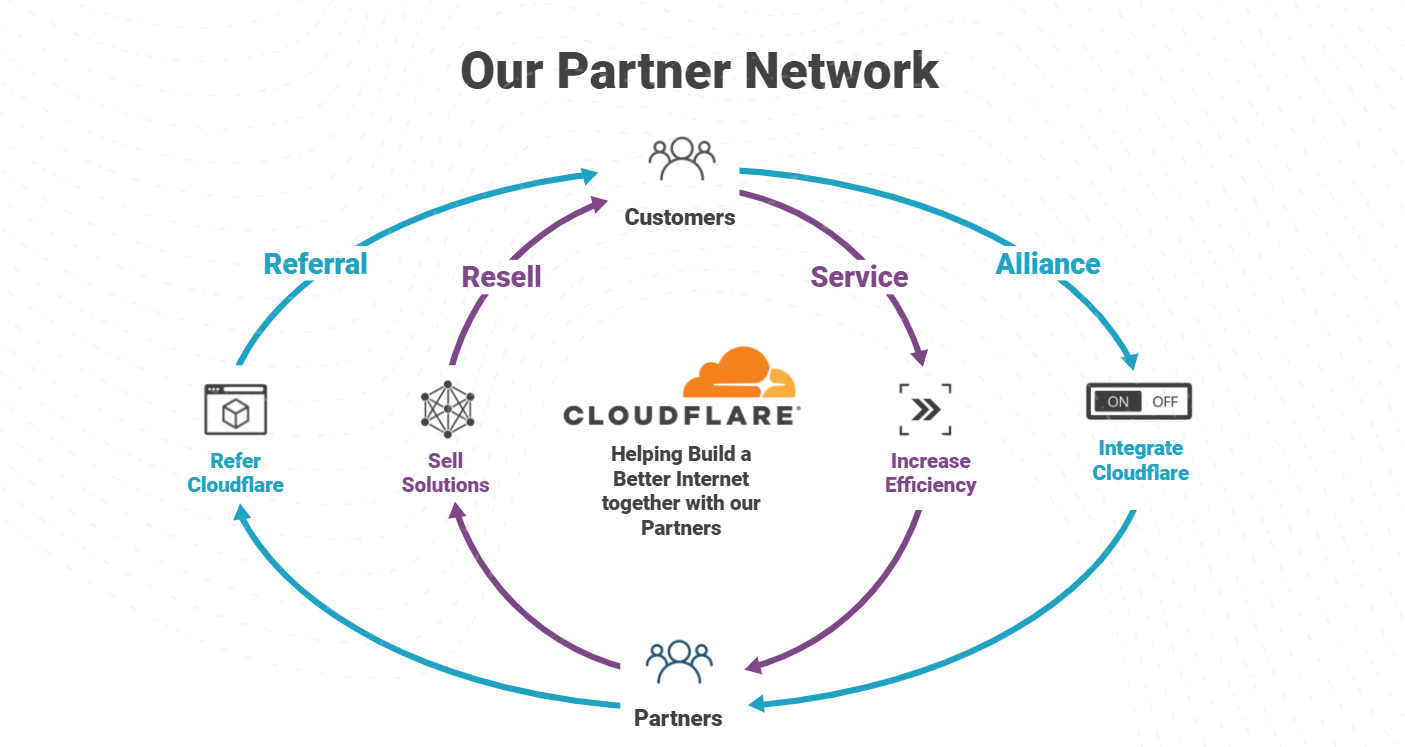
The importance of the Cloudflare Partner Network was on full display in 2021, with record level partner growth in 2021 and aiming even higher in 2022. We’ve been listening to our partners and working to constantly strengthen our ability to deliver value for businesses of all types. An area we identified we could do better, is a program to support “service partners” that want to wrap managed and professional services around Cloudflare products. Today, we are excited to announce the next evolution of the Cloudflare Channel and Alliances Partner Program to specifically enable partners that provide services around Cloudflare products with recurring revenue streams as they equip businesses of all sizes and types with Cloudflare’s leading Zero Trust and SASE solutions.
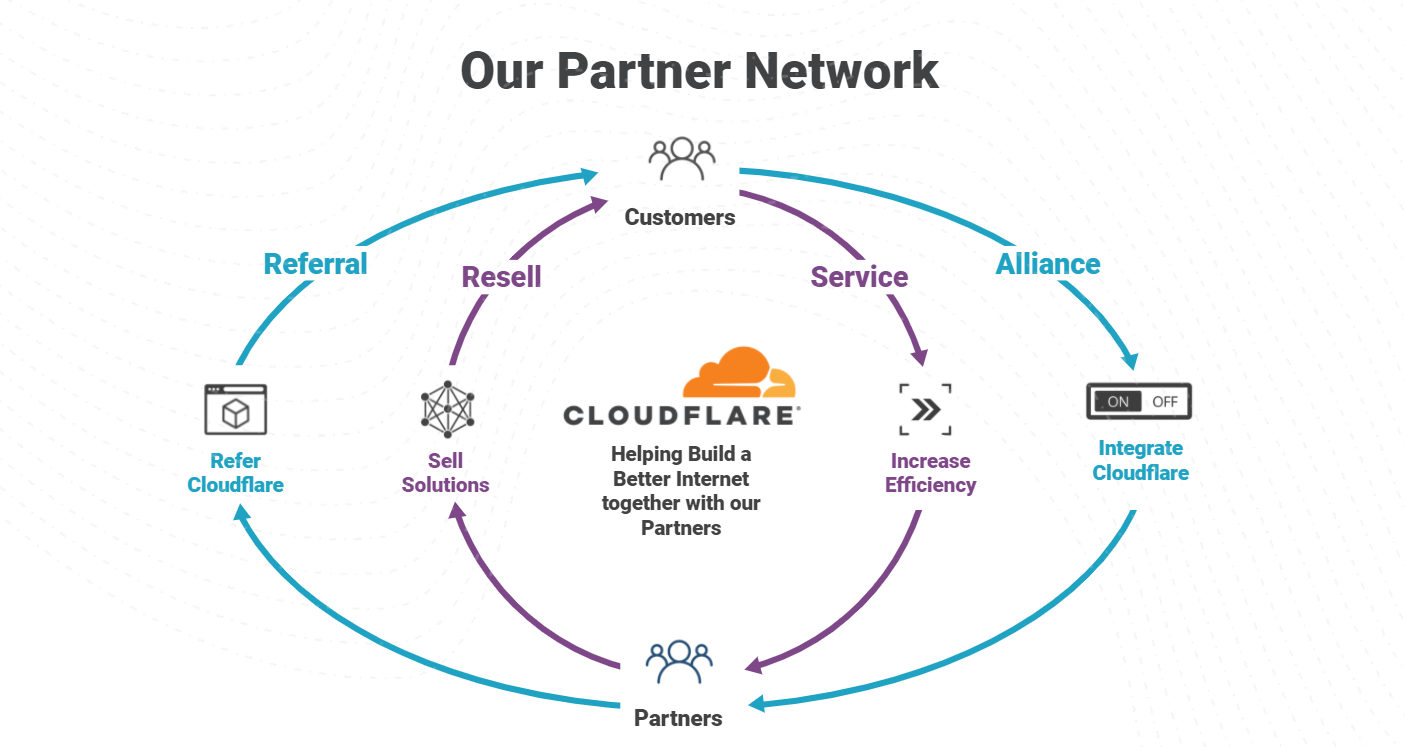
Core to enabling Services Partners are some exciting enhancements:
- New Program Paths
- New Managed Services Partner (MSP) Accreditation.
- New Support & Go-To-Market Motions
New Program Paths
We have seen a 29% increase in ransom DDoS attacks over the past year and a 175% increase just last quarter. Partners continue to be on the front lines helping mitigate and prevent disruption from these events as they extend our services. Our goal for 2022 is to arm our partners with the Continue reading
My Journey to Getting AWS Certified Advanced Networking – Specialty Certified
Last week I took and passed the AWS Certified Advanced Networking – Specialty exam on my first attempt. In this post I will describe the study materials that I used and talk about my experience of taking this test.
What type of skills does this exam test? This is a quote from AWS:
Earning AWS Certified Advanced Networking – Specialty validates expertise in designing and maintaining network architecture for the breadth of AWS services.
The key here I think is “for breadth of AWS services”. It’s not enough to only understand general networking in AWS, you need to understand how to do networking for different AWS services such as S3, WorkSpaces, Lambda, storage gateway, and so on. There is no actual prerequisite to take the exam but it definitely doesn’t hurt if you already have the Solutions Architect Associate (this was previously a prereq) as it will help you in understanding what services are available.
The following is also listed as recommendations for who should take this exam:
- Professional experience using AWS technology, AWS security best practices, AWS storage options and their underlying consistency models, and AWS networking nuances and how they relate to the integration of AWS services.
- Knowledge Continue reading
Sample Lab: SR-MPLS on Junos and SR Linux
Last week I published a link to Pete Crocker’s RSVP-TE lab, but there’s more: he created another lab using the same topology that uses SR-MPLS with IS-IS to get the job done.
Jeroen Van Bemmel did something similar for SR Linux: his lab topology has fewer devices (plus SR Linux runs in containers), so it’s easily deployable on machines without humongous amount of memory.
Sample Lab: SR-MPLS on Junos and SR Linux
Last week I published a link to Pete Crocker’s RSVP-TE lab, but there’s more: he created another lab using the same topology that uses SR-MPLS with IS-IS to get the job done.
Jeroen Van Bemmel did something similar for SR Linux: his lab topology has fewer devices (plus SR Linux runs in containers), so it’s easily deployable on machines without humongous amount of memory.
Cisco DCAUTO exam study resources

I just passed the Cisco DevNet DCAUTO (300-635) exam (Yay!). This is my 3rd Cisco exam on network automation after NPDESI in 2018 (replaced now by the DevNet program), and DevNet CORE (DEVCOR) in 2020. But this time, I documented everything I read, so I could report it here and build a Cisco DCAUTO exam study resources. By doing this, I hope to help anyone who wants to study for this certification. And, as I have already passed the DevNet CORE exam, I am now Cisco certified DevNet Professional. …
The post Cisco DCAUTO exam study resources appeared first on AboutNetworks.net.
What’s an “Address”?
Currently, there are discussions in the IETF's Internet Area on the topic of architectural evolution of the Internet and its implications for the changing role of IP addresses, and I'd like to share some of my thoughts on this topic here.Figuring Out Link Speed Using the Windows Command Prompt
Using the command line allows you to write a script or batch file to standardize troubleshooting so a user or technician can run it.Automaton 11. Data Models for NVIDIA Cumulus 5.0. Collecting Config and Operational Data via REST API with Ansible.
Hello my friend,
Right before the New Year we have posted an article, where we introduced a new approach to manage Cumulus Linux, which became available in the latest release to the date Cumulus Linux 5.0. This approach relies on REST API, which makes the automation of this platform very comfortable. Today we’ll cover how to collect the configuration and ope data with the most popular network and infrastructure automation tools these days: Ansible and Python.
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
Ansible or Python? Python or Ansible?
To be absolutely frank, there is no “or”. There is only “and” in such a question. Both Ansible and Python play crucial role in network and infrastructure automation. Both of them are widely used in various companies from small enterprise to gigantic tier-1 web companies (e.g., Google, Amazon, etc). We see different usage patterns, such as Ansible + AWX being a main toolkit, or Python + Stackstorm or Apache Airflow Continue reading
Worth Reading: The Network Does Too Much
Tom Hollingsworth published a more eloquent version of what I’ve been saying for ages:
- Complexity belongs to the end nodes;
- Network should provide end-to-end packet transport, not a fix for every stupidity someone managed to push down the stack;
- There’s nothing wrong with being a well-performing utility instead of pretending your stuff is working on unicorn farts and fairy dust.
Obviously it’s totally against the vested interest of any networking vendor out there to admit it.
Worth Reading: The Network Does Too Much
Tom Hollingsworth published a more eloquent version of what I’ve been saying for ages:
- Complexity belongs to the end nodes;
- Network should provide end-to-end packet transport, not a fix for every stupidity someone managed to push down the stack;
- There’s nothing wrong with being a well-performing utility instead of pretending your stuff is working on unicorn farts and fairy dust.
Obviously it’s totally against the vested interest of any networking vendor out there to admit it.
To eBGP or not to iBGP — that is the query (please with me ;)
To eBGP or not to iBGP — that is the query (please 🐻 with me ;)
BGP EVPN with VXLAN to the multi-tenant hosts (using SR Linux and SR OS)

There are many ways to do things, and some ways are subjectively better than others. Sometimes, things that may have been a Bad Idea™ in the past become a Not_So_Bad_After_All(maybe, provided X and not Y) option in light of new developments or concerns. To tell which one is which, we’ll just have to give it a go and see where we end up. And whatever happens — 🤞 chances are we’ll learn some things in the process regardless!
The evolution of BGP-to-the-host (how the … did we end up here?)

“Accelerating waves of change to open (2021)” paints a picture of how we can see things evolving over time. From hardware to software, from L2 to static L3 to dynamically signaled L3 with BGP to VXLAN (L2-over-L3) — it all follows a similar pattern of evolutionary change, building on technology from the past to create the future, following the path of the adjacent possible. The terminology and acronyms we humans Continue reading
Worth Exploring: Christoph Jaggi’s New Web Site
Christoph Jaggi, the author of Ethernet Encryption webinar and ethernet encryptor market overviews launched a new site in which he collected tons material he created in the past – the network security and news and articles sections are definitely worth exploring.
Worth Exploring: Christoph Jaggi’s New Web Site
Christoph Jaggi, the author of Ethernet Encryption webinar and ethernet encryptor market overviews launched a new site in which he collected tons material he created in the past – the network security and news and articles sections are definitely worth exploring.
Which CCIE is most demanded in 2022?
Which CCIE is most demanded in 2022?. Most of us, almost every Network Engineer in our IT career probably asked this question. It is important because demanded certification provides job security and having it means finding a job or changing the company easily.
Cisco CCIE has many different tracks as of 2022. After CCIE certification, the next step is CCDE. Before we continue most demanded CCIE, I would like to say that CCDE is not well known by the recruiters, so may be hard to find a job easily with it, but it is quite popular and respectful among the CCIEs. So, if someone passes CCIE Enterprise or CCIE Service Provider, they are definitely aware of CCDE and start considering that certificate.
Let’s continue our most demanded CCIE track discussion.
For many years most demanded CCIE was always CCIE Routing and Switching. As you might be aware, Cisco changed the CCIE Routing and Switching certification name to CCIE Enterprise Infrastructure, and the CCIE Enterprise syllabus has been updated as well.
We provide many CCIE tracks and among our students, CCIE Enterprise Infrastructure training is the most popular CCIE, most demanded CCIE track as well.
We recommend CCIE Continue reading
CCIE Salary – How much you can get if you pass Cisco CCIE Certification?
CCIE Salary, Cisco CCIE salary. Many people have been searching these two words on OrhanErgun.Net for some time.
Many people also have been asking me, how much they can earn monthly if they pass Cisco CCIE practical/lab exam.
For more information on CCIE course content, success stories, and registration, this is our CCIE Course.
I think the answer depends on many criteria. Since this post will be read by people all around the world, it is important to share some insights on the topic.
Before talking about dependencies, you should know some facts about the CCIE certification. Unlike CCDE, Cisco CCIE Certification is known by the recruiters very well as it has been posted as a job requirement for decades.
There are thousands of them in the world, especially Cisco CCIE Routing and Switching, the new name Cisco CCIE Enterprise Infrastructure certificate is around 50000+ people we are talking about.
At the beginning of his post, I said that CCIE salary depends on many criteria.
These are in general
- Country
- Position
- Changing the company
- Years of experience
Most probably there are other things that would affect the salary of the CCIE but these are my observations.
The country is Continue reading
Heavy Networking 615: Optimize User Experience With Palo Alto Networks’ ADEM (Sponsored)
How do you know your remote workers are having good performance--a good experience--using the applications they need to get their work done? Today we drill into Autonomous Digital Experience Management (ADEM) with sponsor Palo Alto Networks, including how ADEM works, the benefits of real-time and synthetic monitoring, how ADEM integrates with SASE, and more.
The post Heavy Networking 615: Optimize User Experience With Palo Alto Networks’ ADEM (Sponsored) appeared first on Packet Pushers.