How To Deal With Social Anxiety When Networking?
We all have social anxiety to a certain extent. However, it is entirely normal, and you shouldn’t feel alone. That is because the fear of adverse reactions from people is evolutionary.
In most cases, anxiety can prevent you from enjoying an event. Not only that, but it can prevent you from attending altogether. As a business owner or an artist, networking is essential.
Hence, if you are looking for ways to control your anxiety, you no longer have to. Here is everything you need to know on how to deal with social anxiety when networking.
Tips For Dealing With Social Anxiety When Networking
Here are the top tips that will help you overcome social anxiety while networking:
- Change In Mindset
It is no secret that mindset can have a significant impact on your life. Your perception of anxiety can help you deal with it. One way to have a positive attitude is by being mindful.
Your nerves will calm once you start to accept your social anxiety. By avoiding the things that caused it will not help you. Instead, the fear will grow gradually and have greater power over your decisions.
However, by being mindful and having self-compassion, you can Continue reading
Video: Cloud Services Hierarchy
Remember the Cloud Models, Layers and Responsibilities video by Matthias Luft? He continued his introduction of cloud services with Cloud Services Hierarchy, explained the differences between infrastructure, platform, function and software as a service, and concluded with a there’s no free lunch message.
Video: Cloud Services Hierarchy
Remember the Cloud Models, Layers and Responsibilities video by Matthias Luft? He continued his introduction of cloud services with Cloud Services Hierarchy, explained the differences between infrastructure, platform, function and software as a service, and concluded with a there’s no free lunch message.
CyberFlood: The Security Mix Tab
For those of you that use CyberFlood I want to talk about something very specific today. The “Traffic Mix” tab and the “Security Mix” tab when running a CyberFlood test. When I was playing with CyberFlood in my little “Stealthwatch... Read More ›
The post CyberFlood: The Security Mix Tab appeared first on Networking with FISH.
Broadband Outlook 2022: Chip and Component Shortages Spell Trouble for Enterprise Network Expansion
Demand for broadband service in unserved and underserved areas remains high, but what of the wild card: supply?Cloud-Native Networks Are Here To Stay: Get Certified To Succeed
The following post is by DriveNets. We thank DriveNets for being a sponsor. At service providers and network operators, demand for new and talented staff is on the rise, but with the ongoing move to software-based approaches and the cloudification of networks, the types of skills they are now seeking is changing. So in line […]
The post Cloud-Native Networks Are Here To Stay: Get Certified To Succeed appeared first on Packet Pushers.
Feedback: Cisco ACI Deep Dive
In 2021, we completed one of the longest ipSpace.net webinars: Cisco ACI Deep Dive (almost 13 hours of content1). One of the participants found it extremely useful:
I really like the technical detail of the webinar and the way it is composed. Mario also does a good job in explaining all the complexity in a clear way without oversimplifying. All the sessions help to build up an understanding on the inner workings of the ACI solution, because they deliver technical details in depth piece by piece.
I also liked his take on the value of this webinar:
I’m always amazed on how much other (offical) training vendors under deliver in their courses that cost thousands of dollars, compared to the real expert level stuff you’ve got here.
Hope you’ll like the webinar as much as he did – you can get it with Standard or Expert ipSpace.net Subscription.
Feedback: Cisco ACI Deep Dive
In 2021, we completed one of the longest ipSpace.net webinars: Cisco ACI Deep Dive (almost 13 hours of content1). One of the participants found it extremely useful:
I really like the technical detail of the webinar and the way it is composed. Mario also does a good job in explaining all the complexity in a clear way without oversimplifying. All the sessions help to build up an understanding on the inner workings of the ACI solution, because they deliver technical details in depth piece by piece.
I also liked his take on the value of this webinar:
I’m always amazed on how much other (offical) training vendors under deliver in their courses that cost thousands of dollars, compared to the real expert level stuff you’ve got here.
Hope you’ll like the webinar as much as he did – you can get it with Standard or Expert ipSpace.net Subscription.
Seven QoS Best Practices for Monitoring Cloud Traffic
NetOps teams should consider Quality of Service (QoS) best practices when using the different cloud services being adopted by enterprises today.Extending Panorama’s firewall address groups into your Kubernetes cluster using Calico NetworkSets
When deploying cloud-native applications to a hybrid and multi-cloud environment that is protected by traditional perimeter-based firewalls, such as Palo Alto Networks (PAN) Panorama, you need to work within the confines of your existing IT security architecture. For applications that communicate with external resources outside the Kubernetes cluster, a traditional firewall is typically going to be part of that communication.
A good practice is to enable enterprise security teams to leverage existing firewall platforms, processes, and architectures to protect access to Kubernetes workloads.
Calico Enterprise already extends Panorama’s firewall manager to Kubernetes. The firewall manager creates a zone-based architecture for your Kubernetes cluster, and Calico reads those firewall rules and translates them into Kubernetes security policies that control traffic between your applications.
With its 3.11 release, Calico Enterprise extends its integration with PAN firewalls to include Panorama address groups in sync with Calico NetworkSets. The new release provides granular application security for your cloud-native application and eliminates workflow complexity.
This integration helps users to:
- Eliminate complex workflows when using existing PAN firewalls with Kubernetes workloads
- Extend their Panorama firewall investment to cloud-native applications
- Provide granular application security for their cloud-native applications
Why Calico’s integration is important
Cloud-native workloads require Continue reading
Internet shut down in Kazakhstan amid unrest

In Kazakhstan, the year had barely got going when yesterday disruptions of Internet access ended up in a nationwide Internet shutdown from today, January 5, 2022 (below you’ll find an update). The disruptions and subsequent shutdown happened amid mass protests against sudden energy price rises.
Cloudflare Radar shows that the full shutdown happened after 10:30 UTC (16:30 local time). But it was preceded by restrictions to mobile Internet access yesterday.
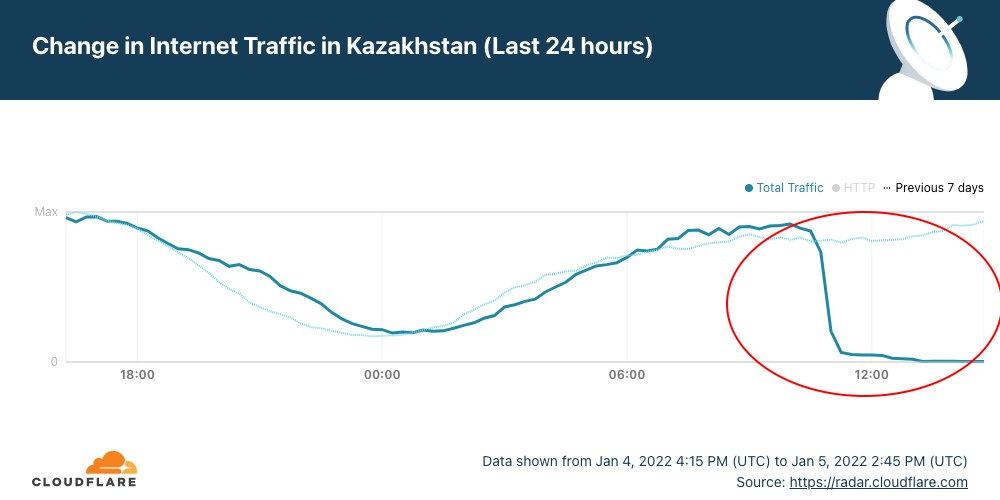
Our data confirm that Kazakhstan’s ASNs were affected after that time (around 18:30 local time). That’s particularly evident with the largest telecommunication company in the country, Kaz Telecom, as the next chart shows.
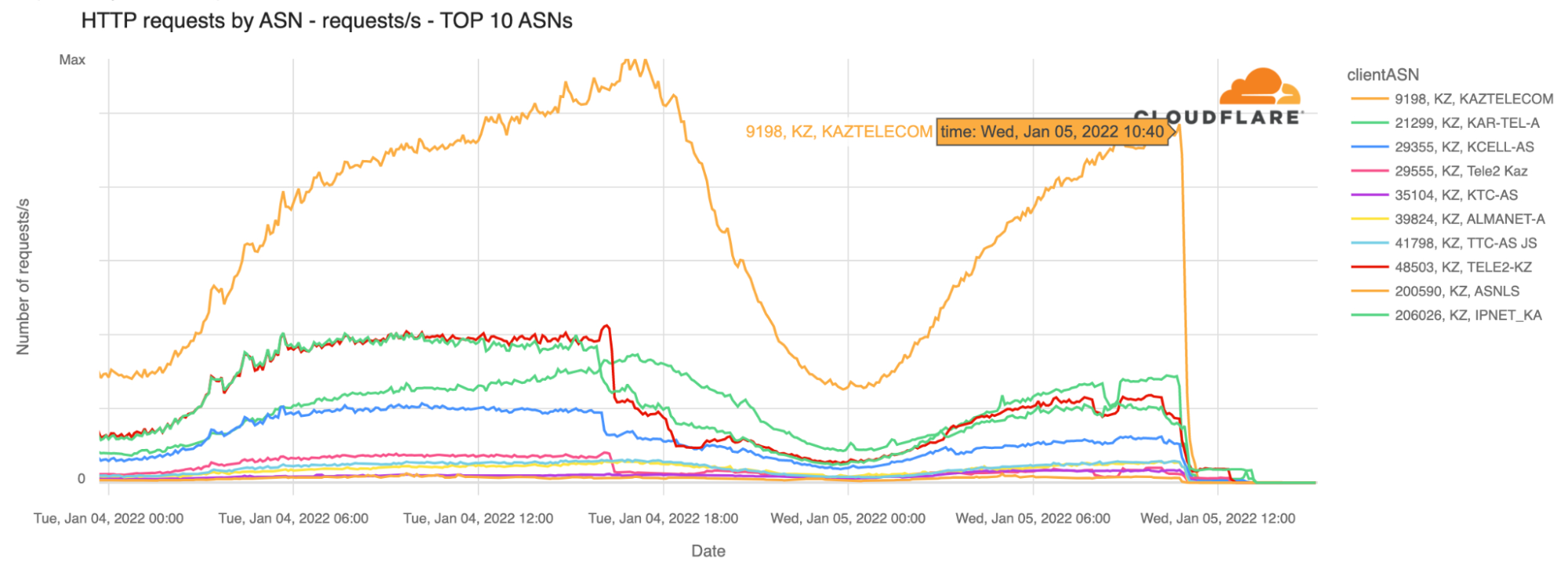
The first disruptions reported affected mobile services, and we can see that at around 14:30 UTC yesterday, January 4, 2022, there was significantly less mobile devices traffic than the day before around the same time. Kazakhstan is a country where mobile represents something like 75% of Internet traffic (shown on Radar), a usual trend in the region. So mobile disruption has a big impact on the country’s Internet, even before the shutdown that affected almost all connectivity.
When we focus on other ASNs besides Kaz Telecom such as the leading mobile Internet services Tele2 or Continue reading
Hedge 113: The PLM with Jeff Jakab
Over the last few episodes of the Hedge, we’ve been talking to folks involved in bringing network products to market. In this episode, Tom Ammon and Russ White talk to Jeff Jakab about the role of the Product Line Manager in helping bring new networking products to life. Join us to understand the roles various people play in the vendor side of the world—both so you can understand the range of roles network engineers can play at a vendor, and so you can better understand how products are designed, developed, and deployed.
How The Gambia lost access to the Internet for more than 8 hours


Internet outages are more common than most people think, and may be caused by misconfigurations, power outages, extreme weather, or infrastructure damage. Note that such outages are distinct from state-imposed shutdowns that also happen all too frequently, generally used to deal with situations of unrest, elections or even exams.
On the morning of January 4, 2022, citizens of The Gambia woke up to a country-wide Internet outage. Gamtel (the main state-owned telecommunications company of the West Africa country), announced that it happened due to "technical issues on the backup links" — we elaborate more on this below.
Cloudflare Radar shows that the outage had a significant impact on Internet traffic in the country and started after 01:00 UTC (which is the same local time), lasting until ~09:45 — a disruption of over 8 hours.

Looking at BGP (Border Gateway Protocol) updates from Gambian ASNs around the time of the outage, we see a clear spike at 01:10 UTC. These update messages are BGP signaling that the Gambian ASNs are no longer routable.
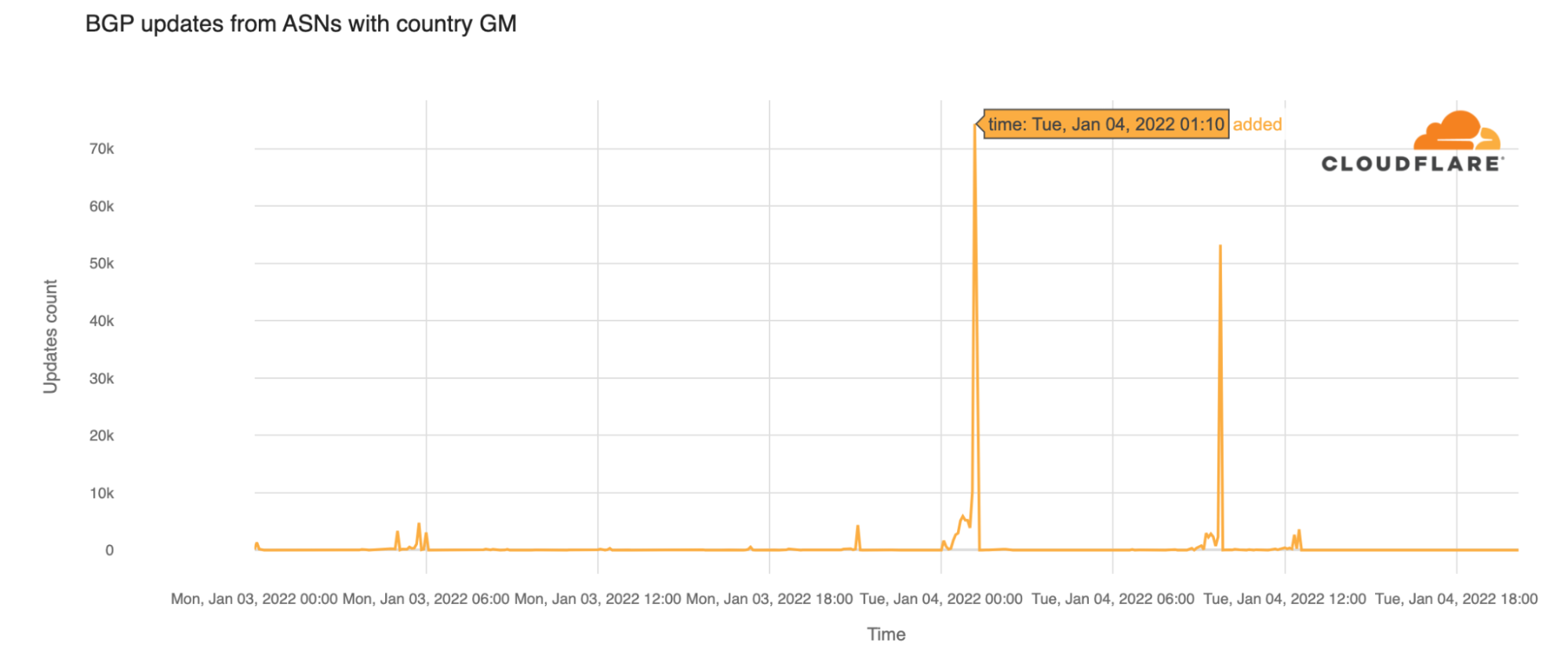
It is important to know that BGP is a mechanism to exchange routing information between autonomous systems (networks) on the Internet. The routers that make the Continue reading