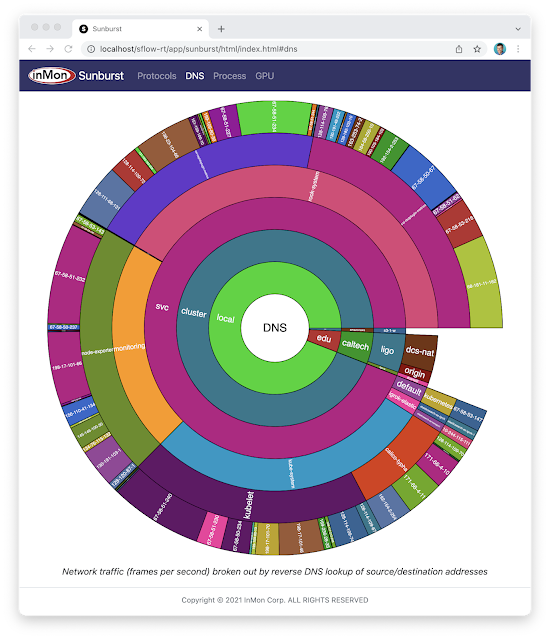
Real-time Kubernetes cluster monitoring example
The Sunburst GPU chart updates every second to show a real-time view of the share of GPU resources being consumed by namespaces operating on the Nautilus hyperconverged Kubernetes cluster. The Nautilus cluster tightly couples distributes storage, GPU, and CPU resources to share among the participating research organizations.Network Break 362: AWS Announces Private 5G Service; FTC Says No To Nvidia’s Arm Grab
Today's Network Break covers two AWS announcements including a private 5G offering and new networking service, discusses why the FTC is against Nvidia acquiring Arm Holdings, examines a new security feature in Aviatrix, and more tech news.
The post Network Break 362: AWS Announces Private 5G Service; FTC Says No To Nvidia’s Arm Grab appeared first on Packet Pushers.
Network Break 362: AWS Announces Private 5G Service; FTC Says No To Nvidia’s Arm Grab
Today's Network Break covers two AWS announcements including a private 5G offering and new networking service, discusses why the FTC is against Nvidia acquiring Arm Holdings, examines a new security feature in Aviatrix, and more tech news.Tier 1 Carriers Performance Report: November, 2021
The post Tier 1 Carriers Performance Report: November, 2021 appeared first on Noction.
Replace your hardware firewalls with Cloudflare One
Today, we’re excited to announce new capabilities to help customers make the switch from hardware firewall appliances to a true cloud-native firewall built for next-generation networks. Cloudflare One provides a secure, performant, and Zero Trust-enabled platform for administrators to apply consistent security policies across all of their users and resources. Best of all, it’s built on top of our global network, so you never need to worry about scaling, deploying, or maintaining your edge security hardware.
As part of this announcement, Cloudflare launched the Oahu program today to help customers leave legacy hardware behind; in this post we’ll break down the new capabilities that solve the problems of previous firewall generations and save IT teams time and money.
How did we get here?
In order to understand where we are today, it’ll be helpful to start with a brief history of IP firewalls.
Stateless packet filtering for private networks
The first generation of network firewalls were designed mostly to meet the security requirements of private networks, which started with the castle and moat architecture we defined as Generation 1 in our post yesterday. Firewall administrators could build policies around signals available at layers 3 and 4 of the OSI model Continue reading
How We Used eBPF to Build Programmable Packet Filtering in Magic Firewall
Cloudflare actively protects services from sophisticated attacks day after day. For users of Magic Transit, DDoS protection detects and drops attacks, while Magic Firewall allows custom packet-level rules, enabling customers to deprecate hardware firewall appliances and block malicious traffic at Cloudflare’s network. The types of attacks and sophistication of attacks continue to evolve, as recent DDoS and reflection attacks against VoIP services targeting protocols such as Session Initiation Protocol (SIP) have shown. Fighting these attacks requires pushing the limits of packet filtering beyond what traditional firewalls are capable of. We did this by taking best of class technologies and combining them in new ways to turn Magic Firewall into a blazing fast, fully programmable firewall that can stand up to even the most sophisticated of attacks.
Magical Walls of Fire
Magic Firewall is a distributed stateless packet firewall built on Linux nftables. It runs on every server, in every Cloudflare data center around the world. To provide isolation and flexibility, each customer’s nftables rules are configured within their own Linux network namespace.
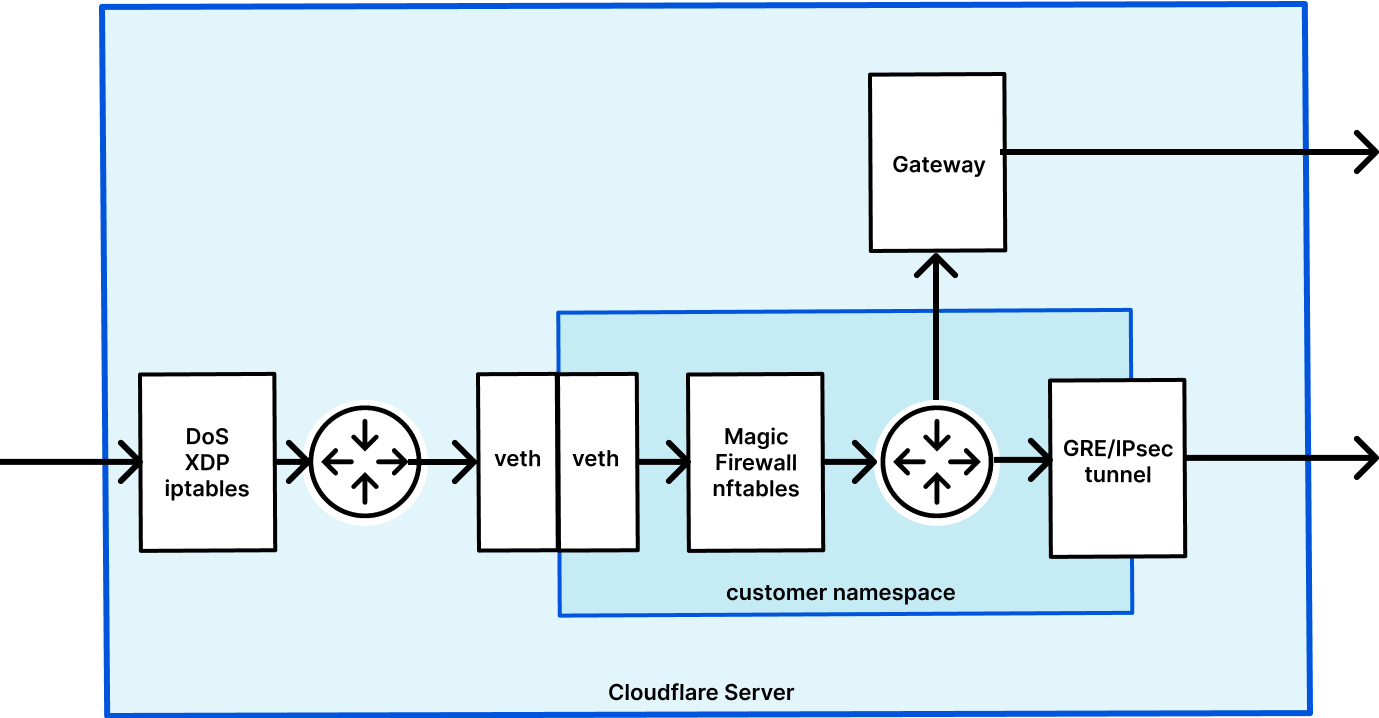
This diagram shows the life of an example packet when using Magic Transit, which has Magic Firewall built in. First, packets go into the server and DDoS Continue reading
Announcing Anycast IPsec: a new on-ramp to Cloudflare One


Today, we're excited to announce support for IPsec as an on-ramp to Cloudflare One. As a customer, you should be able to use whatever method you want to get your traffic to Cloudflare's network. We've heard from you that IPsec is your method of choice for connecting to us at the network layer, because of its near-universal vendor support and blanket layer of encryption across all traffic. So we built support for it! Read on to learn how our IPsec implementation is faster and easier to use than traditional IPsec connectivity, and how it integrates deeply with our Cloudflare One suite to provide unified security, performance, and reliability across all your traffic.
Using the Internet as your corporate network
With Cloudflare One, customers can connect any traffic source or destination — branch offices, data centers, cloud properties, user devices — to our network. Traffic is routed to the closest Cloudflare location, where security policies are applied before we send it along optimized routes to its destination — whether that’s within your private network or on the Internet. It is good practice to encrypt any traffic that’s sensitive at the application level, but for customers who are transitioning from forms of Continue reading
Cloudflare One: One Year Later


Cloudflare One helps enterprises build modern enterprise networks, operate efficiently and securely, and throw out on-premise hardware. It’s been more than a year since we announced the product suite, and we wanted to check in on how things are going.
We’re celebrating Chief Information Officers this week. Regardless of the size of their organization, they’ve had a challenging year. Overnight, their teams became responsible for years of digital transformation to prepare their networks and users to support work-from-home and to adopt new technologies. They worked with partners across security, engineering, and people teams to keep their critical infrastructure running.
Today, we want to focus on the problems that CIOs have been able to solve with Cloudflare One in the last year. Customers are using Cloudflare One at a scale we couldn’t have imagined a year ago to solve interesting problems that we didn't know existed yet. We’ll walk through some specific use cases later in the post, but first, let’s recap why we built Cloudflare One, what problems it solves, and some of the new things we’re launching this week.
What is Cloudflare One?
Cloudflare One allows companies to purchase, provision, and manage connectivity, security, and analytics tools needed Continue reading
How to connect your offices to Cloudflare using SD-WAN
Many offices will soon be re-opening and, just as two years ago when the shift to remote work brought a paradigm change for IT and networking teams, the return to office will bring its own challenges. Two years ago, Chief Information Officers faced a surprise fire drill enabling a completely remote workforce nearly overnight. As companies start to experiment with hybrid working models, IT teams are facing new problems. They are not just re-opening existing branches and potentially activating new ones to enable greater distribution of a more flexible workforce, but also ensuring users have a consistent experience regardless of where they’re connecting. All of this occurs while maintaining visibility and security across an increasingly complex and hard to maintain corporate network.
Some companies have adopted SD-WAN technology to help solve these problems. SD-WAN, or software-defined wide-area networking, is a flexible way to interconnect branches and corporate headquarters together using software as an overlay to various hardware platforms. Deploying SD-WAN can make IT and network teams’ lives simpler by consolidating management tasks and abstracting away the complexity of router configuration. SD-WAN platforms often include a central “orchestrator” that holds information about connected locations.
SD-WAN as Management Overlay for your Corporate Continue reading
PII and Selective Logging controls for Cloudflare’s Zero Trust platform


At Cloudflare, we believe that you shouldn’t have to compromise privacy for security. Last year, we launched Cloudflare Gateway — a comprehensive, Secure Web Gateway with built-in Zero Trust browsing controls for your organization. Today, we’re excited to share the latest set of privacy features available to administrators to log and audit events based on your team’s needs.
Protecting your organization
Cloudflare Gateway helps organizations replace legacy firewalls while also implementing Zero Trust controls for their users. Gateway meets you wherever your users are and allows them to connect to the Internet or even your private network running on Cloudflare. This extends your security perimeter without having to purchase or maintain any additional boxes.
Organizations also benefit from improvements to user performance beyond just removing the backhaul of traffic to an office or data center. Cloudflare’s network delivers security filters closer to the user in over 250 cities around the world. Customers start their connection by using the world’s fastest DNS resolver. Once connected, Cloudflare intelligently routes their traffic through our network with layer 4 network and layer 7 HTTP filters.
To get started, administrators deploy Cloudflare’s client (WARP) on user devices, whether those devices are macOS, Windows, iOS, Android, Continue reading
Building a BGP Anycast Lab
The Anycast Works Just Fine with MPLS/LDP blog post generated so much interest that I decided to check a few similar things, including running BGP-based anycast over a BGP-free core, and using BGP Labeled Unicast (BGP-LU).
The Big Picture
We’ll use the same physical topology we used in the OSPF+MPLS anycast example: a leaf-and-spine fabric (admittedly with a single spine) with three anycast servers advertising 10.42.42.42/32 attached to two of the leafs:
Building a BGP Anycast Lab
The Anycast Works Just Fine with MPLS/LDP blog post generated so much interest that I decided to check a few similar things, including running BGP-based anycast over a BGP-free core, and using BGP Labeled Unicast (BGP-LU).
The Big Picture
We’ll use the same physical topology we used in the OSPF+MPLS anycast example: a leaf-and-spine fabric (admittedly with a single spine) with three anycast servers advertising 10.42.42.42/32 attached to two of the leafs:
Welcome to CIO Week and the future of corporate networks


The world of a Chief Information Officer has changed — today’s corporate networks look nothing like those of even five or ten years ago — and these changes have created gaps in visibility and security, introduced high costs and operational burdens, and made networks fragile and brittle.
We’re optimistic that CIOs have a brighter future to look forward to. The Internet has evolved from a research project into integral infrastructure companies depend on, and we believe a better Internet is the path forward to solving the most challenging problems CIOs face today. Cloudflare is helping build an Internet that’s faster, more secure, more reliable, more private, and programmable, and by doing so, we’re enabling organizations to build their next-generation networks on ours.
This week, we’ll demonstrate how Cloudflare One, our Zero Trust Network-as-a-Service, is helping CIOs transform their corporate networks. We’ll also introduce new functionality that expands the scope of Cloudflare’s platform to address existing and emerging needs for CIOs. But before we jump into the week, we wanted to spend some time on our vision for the corporate network of the future. We hope this explanation will clarify language and acronyms used by vendors and analysts who have realized Continue reading
pygnmi 13. Easy and Reliable Change Validation with pyGNMI and dictdiffer by CERN
Hello my friend,
One of the import aspects of the reliable change management is to know for sure, which operational impact has the change of the network configuration. In this blogpost you will learn, how it is easy to build such a robust framework for the network management with pyGNMI, our Open Source Python library for network management with gNMI, and DeepDiff, quite cool Open Source library for a comparison of two elements.
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
Won’t Network Automation Let Me Know Which Impact Did the Change Make?
It absolutely will, if you create your automation tool in such a way. The development and implementation of network automation is always tailored to the company processes. Therefore, if you validate the status of the network before and after the change right now in a manual way, you can implement the same logic in the automated way as well. At our network automation trainings we teach you about the Continue reading
Cumulus Basics Part I – navigating the OS
This first blog on Cumulus introduces the reader to the basics of the operating system and Cumulus' NCLU.
Worth Reading: Xen on AWS Nitro NICs
If you find smart NICs interesting, you’ll like the latest blog post by James Hamilton explaining how AWS emulated Xen environment on Nitro hardware to keep old VM instances running on new hardware.
Worth Reading: Xen on AWS Nitro NICs
If you find smart NICs interesting, you’ll like the latest blog post by James Hamilton explaining how AWS emulated Xen environment on Nitro hardware to keep old VM instances running on new hardware.