IAB Workshop on Measuring Network Quality for End Users
The telephone network had a single task: make human voice conversations work well. IP networks have a more challenging objective: make all kinds of digital transactions work well. From first player shooter games, though video streaming and web transactions through to human conversations. Make 'em all work well. This topic has become one of those long-standing sagas in IETF folklore, and another chapter of the evolving story was written at a recent IAB Workshop on Measuring Network Quality for End Users. Here's my impressions of this workshop.Day Two Cloud 117: How Akamai Helped Transform IBM Cloud Console’s Architecture (Sponsored)
Today on the Day Two Cloud podcast we have a sponsored show with Akamai and a customer, IBM Cloud. When IBM rebuilt its Cloud Console from a monolithic application to microservices, the company turned to Akamai to help improve application performance while also supporting routing, failover, and availability across six global data centers. We get details from Pavel Despot, Sr. Product Marketing Manager at Akamai; and Tony Erwin, Senior Technical Staff Member/Architect at IBM.
The post Day Two Cloud 117: How Akamai Helped Transform IBM Cloud Console’s Architecture (Sponsored) appeared first on Packet Pushers.
Day Two Cloud 117: How Akamai Helped Transform IBM Cloud Console’s Architecture (Sponsored)
Today on the Day Two Cloud podcast we have a sponsored show with Akamai and a customer, IBM Cloud. When IBM rebuilt its Cloud Console from a monolithic application to microservices, the company turned to Akamai to help improve application performance while also supporting routing, failover, and availability across six global data centers. We get details from Pavel Despot, Sr. Product Marketing Manager at Akamai; and Tony Erwin, Senior Technical Staff Member/Architect at IBM.Packet Capture: What if Less Is More?
Smart packet capture (PCAP) gives analysts the ability to choose the packet evidence they collect and make it retrievable via SIEM.How Your Network Can Solve Your Digital Dilemma
In the drive to successful transformation, the underpinning computer network on which that change relies is taken for granted to just magically deliver what is needed. But that’s a strategic mistake, suggests Lars Rossen of Micro Focus, who wants the network treated as a product.Hedge 102: BGP Security with Geoff Huston
Our community has been talking about BGP security for over 20 years. While MANRS and the RPKI have made some headway in securing BGP, the process of deciding on a method to provide at least the information providers need to make more rational decisions about the validity of individual routes is still ongoing. Geoff Huston joins Alvaro, Russ, and Tom to discuss how we got here and whether we will learn from our mistakes.
Cloudflare for Offices
Cloudflare's network is one of the biggest, most connected, and fastest in the world. It extends to more than 250 cities. In those cities, we're often present in multiple data centers in order to connect to as many networks and bring our services as close to as many users as possible. We're always asking ourselves: how can we get closer to even more of the world's Internet users?
Today, we're taking a big step toward that goal.
Introducing Cloudflare for Offices. We are creating strategic partnerships that will enable us to extend Cloudflare's network into over 1,000 of the world's busiest office buildings and multi-dwelling units. These buildings span the globe, and are where millions of people work every day; now, they’re going to be microseconds away from our global network. Our first deployments will include 30 Hudson Yards, 4 Times Square, and 520 Madison in New York; Willis Tower in Chicago; John Hancock Tower in Boston; and the Embarcadero Center and Salesforce Tower in San Francisco.
And we're not done. We've built custom secure hardware and partnered with fiber providers to scale this model globally. It will bring a valuable new resource to the literal doorstep of Continue reading
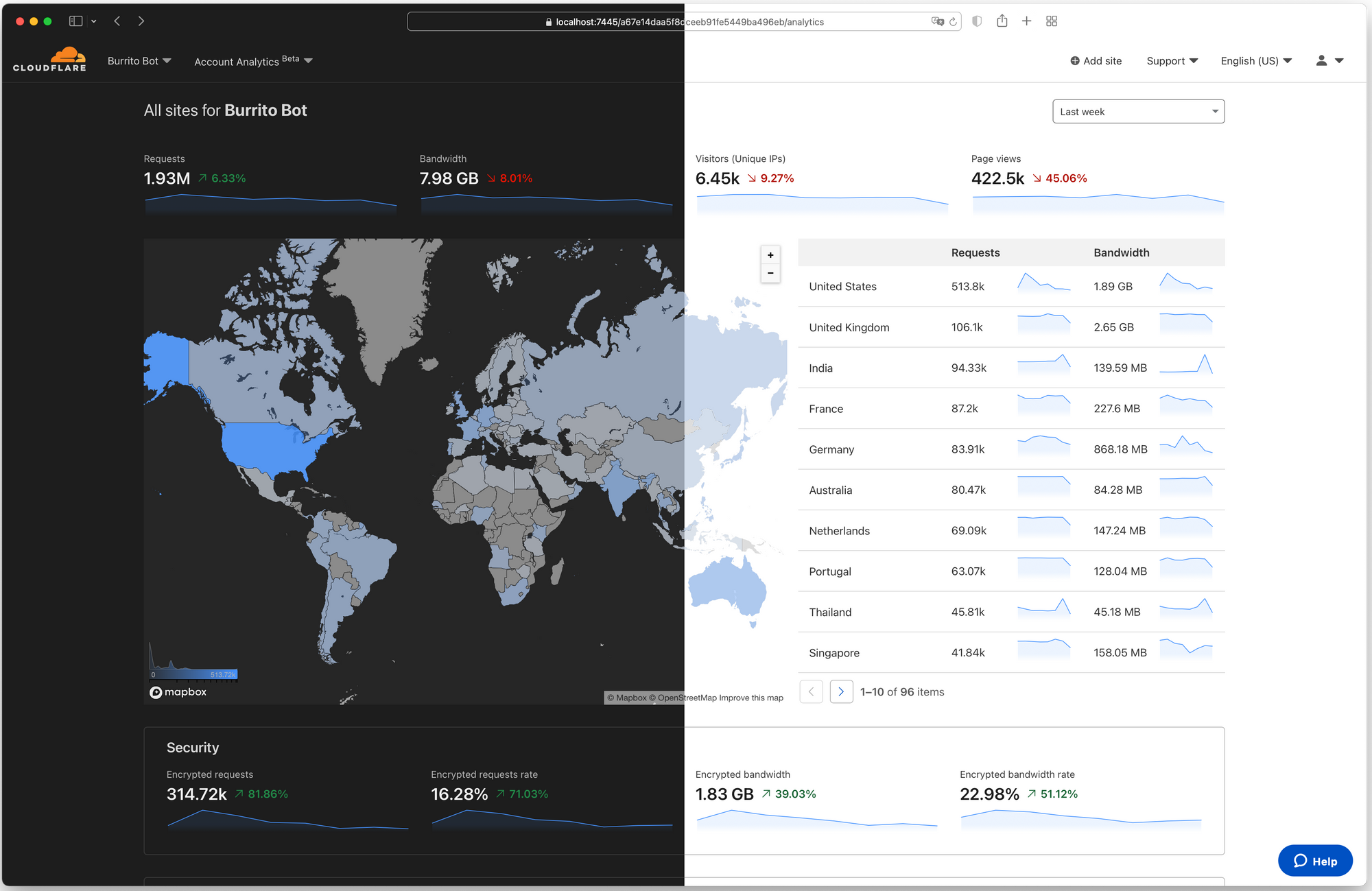
Dark Mode for the Cloudflare Dashboard


Today, dark mode is available for the Cloudflare Dashboard in beta! From your user profile, you can configure the Cloudflare Dashboard in light mode, dark mode, or match it to your system settings.
For those unfamiliar, dark mode, or light on dark color schemes, uses light text on dark backgrounds instead of the typical dark text on light (usually white) backgrounds. In low-light environments, this can help reduce eyestrain and actually reduce power consumption on OLED screens. For many though, dark mode is simply a preference supported widely by applications and devices.
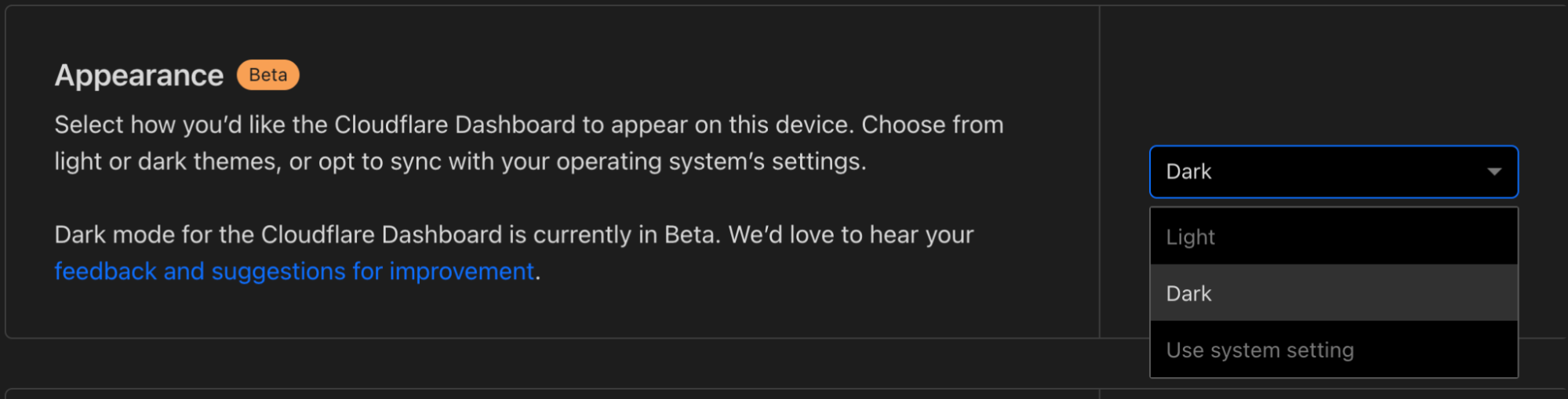
How to enable dark mode
- Log into Cloudflare.
- Go to your user profile.
- Under Appearance, select an option: Light, Dark, or Use system setting. For the time being, your choice is saved into local storage.
There are many primers and how-tos on implementing dark mode, and you can find articles talking about the general complications of implementing a dark mode including this straightforward explanation. Instead, we will talk about what enabled us to be able to implement dark mode in Continue reading
Watch Out: ISR Performance License
Bill Dagy sent me an annoying ISR gotcha. In his own words:
Since you have a large audience I thought I would throw this out here. Maybe it will help someone avoid spending 80 man hours troubleshooting network slowdowns.
Here’s the root cause of that behavior:
Cisco is now shipping routers that have some specified maximum throughput, but you have to buy a “boost license” to run them unthrottled. Maybe everyone already knew this but it sure took us by surprise.
Don’t believe it? Here’s a snapshot from Cisco 4000 Family Integrated Services Router Data Sheet:
Watch Out: ISR Performance License
Bill Dagy sent me an annoying ISR gotcha. In his own words:
Since you have a large audience I thought I would throw this out here. Maybe it will help someone avoid spending 80 man hours troubleshooting network slowdowns.
Here’s the root cause of that behavior:
Cisco is now shipping routers that have some specified maximum throughput, but you have to buy a “boost license” to run them unthrottled. Maybe everyone already knew this but it sure took us by surprise.
Don’t believe it? Here’s a snapshot from Cisco 4000 Family Integrated Services Router Data Sheet:
Keith’s Law (1)
I sometimes reference Keith’s Law in my teaching, but I don’t think I’ve ever explained it. Keith’s Law runs something like this:
Any large external step in a system’s capability is the result of many incremental changes within the system.
The reason incremental changes within a system appear as a single large step to outside observers is the smaller changes are normally hidden by abstraction. This is, in fact, the purpose of abstraction—to hide small changes inside a system from external view. Keith’s law is closely related to Clarke’s third law that “Any sufficiently advanced technology is indistinguishable from magic.” What looks like magic from the outside is really just a bunch of smaller things—each easier to understand on its own—combined into one single “thing” through abstraction.
If you’ve read this far, you’re probably thinking—what does this have to do with network engineering?
Well, several things, really.
First—the network is just an abstraction that moves packets to its users. Moving packets seems so … simple … to network users. You put data in here, and data comes out over there. All the little stuff that goes into making a network work are lost in the abstraction of the virtual Continue reading
Lightning-fast Kubernetes networking with Calico & VPP
Public cloud infrastructures and microservices are pushing the limits of resources and service delivery beyond what was imaginable until very recently. In order to keep up with the demand, network infrastructures and network technologies had to evolve as well. Software-defined networking (SDN) is the pinnacle of advancement in cloud networking; by using SDN, developers can now deliver an optimized, flexible networking experience that can adapt to the growing demands of their clients.
This article will discuss how Tigera’s new Vector Packet Processing (VPP) data plane fits into this landscape and share some benchmark details about its performance. Then it will demonstrate how to run a VPP-equipped cluster using AWS public cloud and secure it with Internet Protocol Security (IPsec).
Introduction to Vector Packet Processing
Project Calico is an open-source networking and security solution. Although it focuses on securing Kubernetes networking, Calico can also be used with OpenStack and other workloads. Calico uses a modular data plane that allows a flexible approach to networking, providing a solution for both current and future networking needs.
VPP is an easily extensible, kernel-independent, highly optimised, and blazing-fast open-source data plane project that operates between layer 2 and layer 4 of the OSI Continue reading
Simplification through Unification: One Network Across the Entire Multi-Cloud
Two major pillars of VMworld 2021 focus on enhancing productivity and consistency. More than ever, businesses are demanding consistent, secure, and reliable communication between apps and users. What Networking professionals at VMworld want to reinforce is that multi-cloud ops shouldn’t have to slow down due to poor app distribution among workspaces. The network should be durable and secure everywhere. While threats are inevitable, businesses can be prepared by learning how to converge networking, security, and threat detection within the cloud. And that’s exactly what we’re going to teach you at this year’s virtual event.
Valued customers of all different industries have chosen to allow VMware’s multi-cloud ops solutions to guide them through their digital transformation. Susan Wu, Senior Product Marketing Manager, and Aamer Aakhter, Product Manager, are two seasoned VMware leaders who will take you through how customers achieved multi-cloud excellence, and how you can say “Goodbye Compromises Everywhere. Hello Productivity Anywhere,” with this VMworld session.
While simplicity may look different depending upon an organization’s goals, there is one thing that remains constant: performance shouldn’t have to be sacrificed for safety. Your enterprise should be able to streamline the entire multi-cloud to remain agile, productive, and increasingly adaptive against any threat or operational hiccup.
IT portfolios are becoming increasingly Continue reading