netlab Network Topology Graphs
A netlab user sent me an intriguing question: “Would it be possible to get network topology graphs out of the tool?”
I did something similar a long while ago for a simple network automation project (and numerous networking engineers built really interesting stuff while attending the Building Network Automation Solutions course), so it seemed like a no-brainer. As always, things aren’t as easy as they look.
AWS Networking – Part III: VPC Verification Using AWS CLI
VPC Verification Using AWS CLI
We can verify our VPC configuration by using AWS CLI. Example 1-1 shows the output for command aws ec2 describe-vpc in JSON format. This command lists all our VPC resources with their properties. The first one is the newest VPC NVKT-VPC-01, and the second one is the default VPC which I have named DFLT-VPC. The first VPC gets ordinal zero [0], and the second VPC gets number one [1]. Note that ordinal numbers are not shown in the output. VPC properties describe the VPC-specific CIDR Block, DHCP Options, VPC Identifier, Owner Id, CIDR Block Association, and Tags.
aws ec2 describe-vpcs
{
"Vpcs": [
{
"CidrBlock": "10.10.0.0/16",
"DhcpOptionsId": "dopt-09217361",
"State": "available",
"VpcId": "vpc-04ef72cc79a73f82e",
"OwnerId": "123456654321",
"InstanceTenancy": "default",
"CidrBlockAssociationSet": [
{
"AssociationId": "vpc-cidr-assoc-0379c0e3e854f43ff",
"CidrBlock": "10.10.0.0/16",
"CidrBlockState": {
"State": "associated"
}
}
],
"IsDefault": false,
"Tags": [
{
"Key": "Name",
"Value": "NVKT-VPC-01"
}
]
},
{
"CidrBlock": "172.31.0.0/16",
"DhcpOptionsId": "dopt-09217361",
"State": "available",
AWS Networking – Part II: Create VPC – AWS Console
The first thing to do when we create a VPC is to log in to the AWS console. Then we select the AWS Region where we want to launch our VPC. We are going to use VPC Region Europe (London) eu-west-2. As the last step, we give the name to VPC and associate a CIDR block 10.10.0.0/16 to it.
Figure 1-3: Virtual Private Cloud (VPC) – Example VPC.
Project Myriagon: Cloudflare Passes 10,000 Connected Networks


During Speed Week, we’ve talked a lot about the products we’ve improved and the places we’ve expanded to. Today, we have a final exciting announcement: Cloudflare now connects with more than 10,000 other networks. Put another way, over 10,000 networks have direct on-ramps to the Cloudflare network.
This is the culmination of a special project we’ve been working on for the last few months dubbed Project Myriagon, a reference to the 10,000-sided polygon of the same name. In going about this project, we have learned a lot about the performance impact of adding more direct connections to our network — in one recent case, we saw a 90% reduction in median round-trip end-user latency.
But to really explain why this is such a big milestone, we first need to explain a bit about how the Internet works.
More roads leading to Rome
The Internet that all know and rely on is, on a basic level, an interconnected series of independently run local networks. Each network is defined as its own “autonomous system.” These networks are delineated numerically with Autonomous Systems Numbers, or ASNs. An ASN is like the Internet version of a zip code, a short number directly mapping Continue reading
How to Innovate Your Online Social Network
It is true that social media platforms have grown by leaps and bounds in the past few years. Despite the growth these platforms also face continuous criticism. It can however, not be ignored that in the coming years the social media platforms are said to improve more. These platforms are extremely unified when it comes to creating an impact. I’m the times of COVID these platforms have evolved thoroughly; people have considerably been attached, hooked more like glued to them for the entire time.
Social media platforms have not only evolved the business markets but it has also created an impact on how as a whole our society moves. It has done a great job in highlighting the evils of our society while it has also created a few negative affects which can not be ignored. Following are the few ways through which one can improve their use of these platforms to support their growth.
Do Not Rely On a Single Platform
If we talk about growth one needs to understand that the trend keeps evolving when the social media marketing started the most sought after channel for promotions was Twitter, however later on Facebook also indulged in Continue reading
Epidemic Modeling(DES)
Introduction
One of the things I have been trying to play recently with is Discrete Event Simulation(DES). I think it is a powerful tool for validating ideas. In this post, we will look at a toy epidemic model to simulate SIS/SIR models.
In Epidemic modeling, there are two classic models - SIS and SIR models. The models divide the population into different categories corresponding to different stages of the epidemic.
- Susceptible(S): Susceptible individuals can contract the disease.
- Infected(I): Infected individuals have already been contracted the disease.
- Recovered(R): Recovered individuals are recovered from the disease and can not be infected again.
SIS Model
In case of SIS, the main assumption is that an infected person can get infected again after recovering. The state transition diagram looks like:
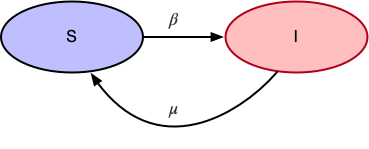
- $\beta$ is the probability of transitioning from
Susceptible(S)toInfected(I) - $\mu$ is the probability of transitioning from
Infected(I)toSusceptible(S)
SIR Model
In case of SIR, the main assumption is that an infected person can not get infected again. The state transition diagram looks like:
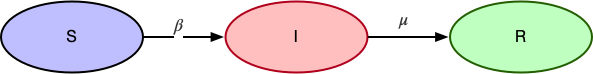
- $\beta$ is the probability of transitioning from
Susceptible(S)toInfected(I) - $\mu$ is the probability of transitioning from
Infected(I)toRecovered(R)
SIS Simulation
We will have a generic Simulation class Continue reading
Cloudflare Pages is Lightning Fast
When we announced Cloudflare Pages in April, our goal wasn’t to bring just any web development tool to the table. As a front-end developer, it’s your responsibility to bring the ideas of your marketing, product and engineering teams to life by crafting a beautifully engaging experience for every customer. With all the hard work that goes into the development process — turning mock-ups to code, getting input from your team, staging and testing changes — you want the best performance possible for your site to showcase your work and optimize your customers’ experience.
Cloudflare Pages is the most secure and most scalable Jamstack platform to build and deploy your sites on the edge. But how is Pages so fast?
It comes down to three key reasons:
- Pages is built on one of the fastest networks in the world, putting us within 50 ms of 95% of the world’s Internet-connected population. Delivering Pages from this network is the basis of our speed.
- Cloudflare helps define and implement next generation standards, like QUIC + HTTP/3 and Early Hints, that push Pages performance to the next level.
- Pages has a killer developer experience that makes it easy to build the fastest websites on Continue reading
Profiling Your Workers with Wrangler


In the year since Cloudflare’s launch of Workers Unbound, developers have unlocked the ability to run computationally intensive workloads on the Cloudflare edge network — like image processing, game logic, and other complex algorithms. With all that additional computing power comes a host of questions around performance. Our customers often ask us how they can profile or monitor their Workers to see where they spend the most CPU time, or to see whether their changes improve performance.
Here at Cloudflare, we not only want to build the fastest, most affordable, and most flexible compute platform at the edge; we also want to make the lives of our developers easier in building their applications. To do this, Cloudflare has begun to integrate with existing tools — places our developers feel comfortable and efficient in their day-to-day work. To help measure performance of our customers’ Workers, we’re beginning to integrate with the Chrome DevTools protocol. Just like you can use chrome://inspect to debug your Node backend, you can also use it to profile your Cloudflare Workers.
Introducing Chrome DevTools Integration (Beta)
We’re starting off this integration with beta support for local CPU profiling, using Wrangler. To show off how to use this Continue reading
APIs and Department Stores

This week I tweeted something from a discussion we had during Networking Field Day that summed up my feelings about the state of documentation of application programming interfaces (APIs):
I laughed a bit as I wrote it because I’ve worked in department stores like Walmart in the past and I know the reasons why they tend to move things around. Comparing that to the way that APIs are documented is an interesting exercise in how people think about things like new capabilities and notification of changes.
Branding Exercises
In case you weren’t aware, everything in your average department store is carefully planned out. The things placed in the main aisles are decided on weeks in advance due to high traffic. The items placed at the ends of the aisles, or endcaps, are placed there to highlight high margin items or things that are popular enough to be sought out by customers. The makeup of the rest of the store is determined by a lot of metrics.
There are a Continue reading
How to Simplify Your Journey to Zero Trust with NSX Workshops
At its core, Zero Trust is an operational framework that helps enterprises secure modern network environments. Zero Trust insists organizations strip away ambiguity from their security and focus on the basics: committing to a risk-based approach across end-users, networks, data, devices, and much more. If you’re ready to take the next step toward built-in, Zero Trust networking (ZTN), we can help. Learn how to successfully implement Zero Trust networking and segmentation strategies at one of our upcoming NSX Network Security Workshop Sessions on Tuesday, September 28, 2021 or on Wednesday, September 29, 2021.
During these live virtual events, Patricio Villar, Principal Network Architect and VMware Certified Expert/Network Virtualization, will cover Zero Trust foundational concepts, including:
- How to identify communication paths to segment and build policy to protect your data center
- How implementing NSX security supports ZTN framework
- How to easily implement stronger distributed security with VMware NSX
NSX Network Security Workshop topics include:
- Zero Trust Networking concepts
- Tools to implement ZTN
- Distributed Firewall
- Distributed IDS/IPS
- NSX Intelligence
- Live demos
- And much more
If you’re ready to simplify Zero Trust so you can have simply zero worries, grab your spot and register today.
See you there!
The post How to Simplify Your Journey to Zero Trust with NSX Workshops appeared first on Network and Security Virtualization.
Heavy Networking 598: The Future Of Networking – Quantum Communications With Joshua Slater
Today's Heavy Networking gets entangled in a discussion about quantum communications or quantum networking. We discuss qubits, the challenges of moving them across a network, use cases such as key distribution, and more. Our guest is Dr. Joshua Slater.
The post Heavy Networking 598: The Future Of Networking – Quantum Communications With Joshua Slater appeared first on Packet Pushers.
Heavy Networking 598: The Future Of Networking – Quantum Communications With Joshua Slater
Today's Heavy Networking gets entangled in a discussion about quantum communications or quantum networking. We discuss qubits, the challenges of moving them across a network, use cases such as key distribution, and more. Our guest is Dr. Joshua Slater.Benchmarking Edge Network Performance: Akamai, Cloudflare, Amazon CloudFront, Fastly, and Google


During Speed Week we’ve talked a lot about services that make the web faster. Argo 2.0 for better routing around bad Internet weather, Orpheus to ensure that origins are reachable from anywhere, image optimization to send just the right bits to the client, Tiered Cache to maximize cache hit rates and get the most out of Cloudflare’s new 25% bigger network, our expanded fiber backbone and more.
Those things are all great.
But it’s vital that we also measure the performance of our network and benchmark ourselves against industry players large and small to make sure we are providing the best, fastest service.
We recently ran a measurement experiment where we used Real User Measurement (RUM) data from the standard browser API to test the performance of Cloudflare and others in real-world conditions across the globe. We wanted to use third-party tests for this, but they didn’t have the granularity we wanted. We want to drill down to every single ISP in the world to make sure we optimize everywhere. We knew that in some places the answers we got wouldn’t be good, and we’d need to do work to improve our performance. But without detailed analysis across the Continue reading
Announcing Project Turpentine: an easy way to get off Varnish


When Varnish and the Varnish Configuration Language (VCL) were first introduced 15 years ago, they were an incredibly powerful combination to configure caching on servers (and your networks). It seemed a logical choice for a language to configure CDNs — caching in the cloud.
A lot has changed on the Internet since then.
In particular, caching is just one of many things that “CDNs” are expected to do: load balancing, DDoS protection, rate limiting, transformations, synthetic responses, routing and more. But above all what “CDNs” need to be is programmable, not just configurable.
Configuration went from a niche activity to a much more common — and often involved — requirement. We’ve heard from a lot of teams that want to remove critical dependencies on the one person they have who knows how to make configuration changes — because they’re the only one on the team who knows how to write in VCL.
But it’s not just about who can write VCL — it’s what VCL is increasingly being asked to do. A lot of our customers have told us that they have much greater expectations for what they expect the network to do: they don’t just want to configure Continue reading
Route Replication the Easy Way
Easy Virtual Network (EVN) was a technology Cisco came up with back in the days to make it easier to implement VRFs without the pain of running VRF lite or the complexity of running a full MPLS + BGP network. It was actually a pretty cool technology but never became mainstream. However, as part of this technology, Cisco also made it easier to replicate, or in other words leak, routes between VRFs. You don’t need the rest of EVN to do this and this simplified way of replicating routes have kind of been forgotten by the industry. I thought I would share with you the ease of replicating routes with this feature even without BGP.
We have a straight forward topology like the one below:

The USERS switch is a L2 switch and all the L3 configuration is in the CORE router. We have implemented segmentation in the network so we have a USERS VRF and then we have a SERVICES VRF for shared services such as DNS and DHCP. Because these services are in a separate VRF, we will not have reachability to them from the USERS VRF. This lab will use the following IP addresses:
User – 10. Continue reading
Interesting Concept: Time Dilation
I loved the Time Dilation blog post by Seth Godin. It explains so much, including why I won’t accept a “quick conf call to touch base and hash out ideas” from someone coming out of the blue sky – why should I be interested if they can’t invest the time to organize their thoughts and pour them into an email.
The concept of “creation-to-consumption” ratio is also interesting. Now I understand why I hate unedited opinionated chinwagging (many podcasts sadly fall into this category) or videos where someone blabbers into a camera while visibly trying to organize their thoughts.
Just FYI, these are some of the typical ratios I had to deal in the past:
Interesting Concept: Time Dilation
I loved the Time Dilation blog post by Seth Godin. It explains so much, including why I won’t accept a “quick conf call to touch base and hash out ideas” from someone coming out of the blue sky – why should I be interested if they can’t invest the time to organize their thoughts and pour them into an email.
The concept of “creation-to-consumption” ratio is also interesting. Now I understand why I hate unedited opinionated chinwagging (many podcasts sadly fall into this category) or videos where someone blabbers into a camera while visibly trying to organize their thoughts.
Just FYI, these are some of the typical ratios I had to deal in the past:

