IPv6 Buzz 079: IPv6 In The Data Center
In this week's IPv6 Buzz podcast, we explore IPv6 in the data center with guest Jeff Tantsura. Jeff is formerly head of Network Strategy with Juniper/Apstra, and now with Microsoft Azure. We explore IPv6 use cases in the data center, reasons for and challenges of assigning a /64 per host, leveraging IPv6 flow labels to improve data center fabric performance, and more.
The post IPv6 Buzz 079: IPv6 In The Data Center appeared first on Packet Pushers.
IPv6 Buzz 079: IPv6 In The Data Center
In this week's IPv6 Buzz podcast, we explore IPv6 in the data center with guest Jeff Tantsura. Jeff is formerly head of Network Strategy with Juniper/Apstra, and now with Microsoft Azure. We explore IPv6 use cases in the data center, reasons for and challenges of assigning a /64 per host, leveraging IPv6 flow labels to improve data center fabric performance, and more.Rethinking Broadband Access Options as Operators Drive 10G PON Deployments
IT managers stand to gain faster, symmetric services as fiber network spending climbs.Service Mapping with BGP Classful Transport – Kaliraj Vairavakkalai, Principal Engineer @ Juniper Networks
In this episode Kaliraj will explain to us what BGP Classful Transport (BGP-CT) is and how it works. BGP-CT is a mechanism, referred to as “service mapping”, to express association of overlay routes with underlay routes satisfying a certain SLA, using BGP. It is a framework for classifying underlay routes into transport classes, and mapping service routes to specific transport class.
The “Transport class” construct maps to a desired SLA, and can be used to realize the “Topology Slice” in 5G Network slicing architecture.
BGP-CT is still work in progress in IETF. The draft can be found here: https://datatracker.ietf.org/doc/draft-kaliraj-idr-bgp-classful-transport-planes/
The authors welcome feedback and input for the draft.

Nginx reverse proxy and Webmin
Before going into “How” you may wonder “Why” I need a reverse proxy in front of Webmin. First, and most important, is laziness. Yes, you read it right. I have in my home lab a one page html listing all http(s) resources I have in my IT lab. Instead of typing numerous URLs I just … Continue reading Nginx reverse proxy and WebminIt’s Raining Beacons: Automated Generation of Cobalt Strike Traffic
Introduction
Cobalt Strike [1] is a tool to support red teams in attack simulation exercises. To this end, Cobalt Strike provides several techniques that allow a red team to execute targeted attacks to compromise a target network, established a bridge head on a host, and then move laterally to gain additional access to computers, accounts, and, eventually, data.
While the goal of Raphael Mudge, the author of Cobalt Strike, was to provide a framework to test network defenses to support the development of effective detection mechanisms and incident response procedures, the power provided by the tools was not lost on malicious actors (see, for example, [2]).
Soon, Cobalt Strike was copied, modified, and included in the toolset used in attacks against targets of all kinds. For example, recently Cobalt Strike was used as part of both the SolarWinds supply-chain attack [3] and the ransomware attacks against Colonial Pipeline [4]. The tool is so popular that there are Telegram channels and GitHub repositories dedicated to obtaining or producing modified, pirated copies of the Cobalt Strike software [5].
Given its “dual nature” and wide adoption by both sides of the security battlefield, it is not surprising that security teams struggle to develop Continue reading
Day Two Cloud 104: Cloud Is No Escape From Your Data Center Dumpster Fire
IT and business leaders need to be more nuanced in their approach to the cloud. On today's Day Two Cloud podcast, guest Melissa Palmer discusses why cloud hype is a problem for organizations, the need to understand why you'd use cloud, what problems you're trying to solve, and why poor operational processes on prem won't magically vanish by moving to the cloud.
The post Day Two Cloud 104: Cloud Is No Escape From Your Data Center Dumpster Fire appeared first on Packet Pushers.
Day Two Cloud 104: Cloud Is No Escape From Your Data Center Dumpster Fire
IT and business leaders need to be more nuanced in their approach to the cloud. On today's Day Two Cloud podcast, guest Melissa Palmer discusses why cloud hype is a problem for organizations, the need to understand why you'd use cloud, what problems you're trying to solve, and why poor operational processes on prem won't magically vanish by moving to the cloud.Cloudflare’s Network Doubles CPU Capacity and Expands Into Ten New Cities in Four New Countries
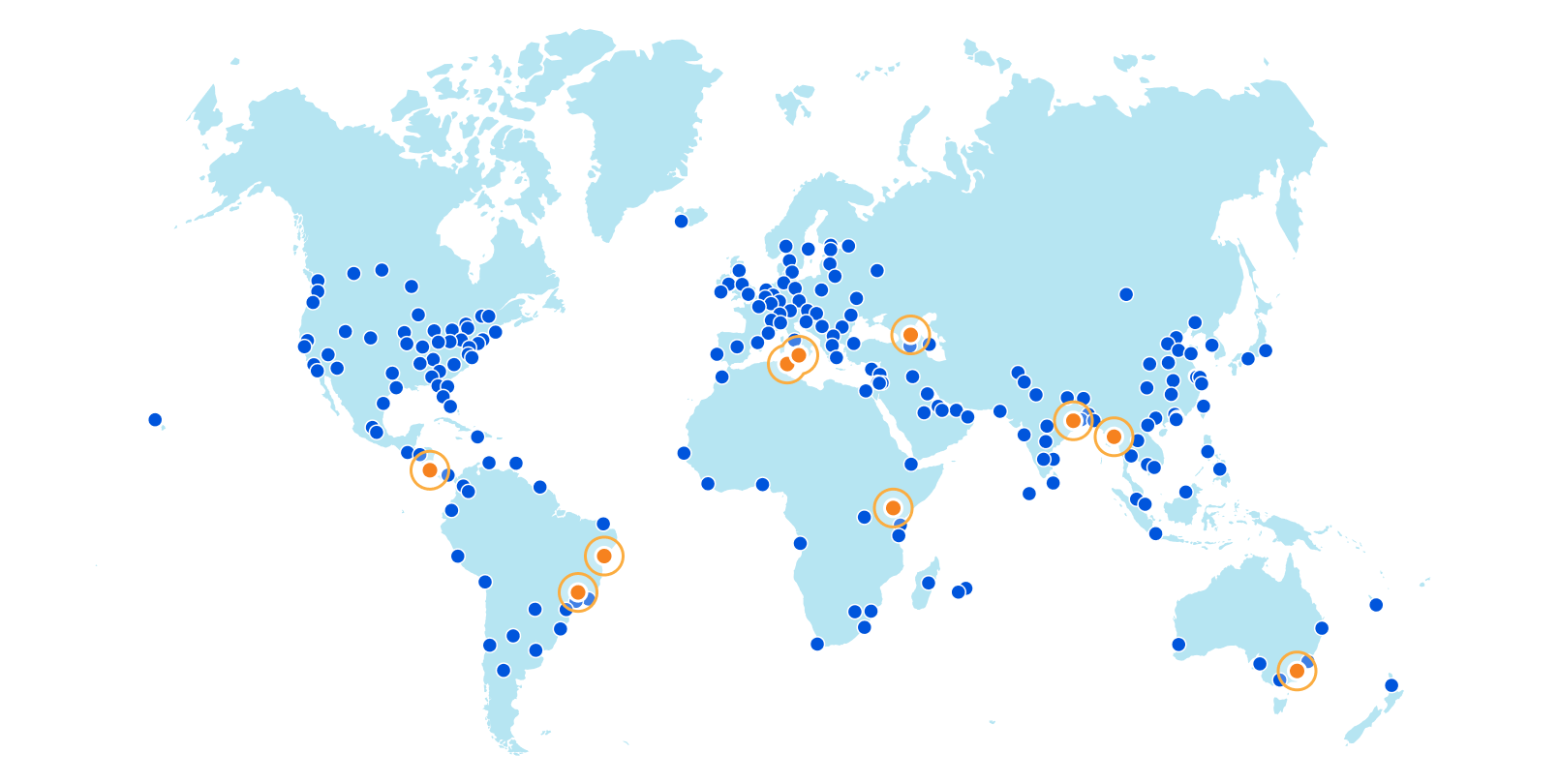
Cloudflare’s global network is always expanding, and 2021 has been no exception. Today, I’m happy to give a mid-year update: we've added ten new Cloudflare cities, with four new countries represented among them. And we've doubled our computational footprint since the start of pandemic-related lockdowns.
No matter what else we do at Cloudflare, constant expansion of our infrastructure to new places is a requirement to help build a better Internet. 2021, like 2020, has been a difficult time to be a global network — from semiconductor shortages to supply-chain disruptions — but regardless, we have continued to expand throughout the entire globe, experimenting with technologies like ARM, ASICs, and Nvidia all the way.
The Cities
Without further ado, here are the new Cloudflare cities: Tbilisi, Georgia; San José, Costa Rica; Tunis, Tunisia; Yangon, Myanmar; Nairobi, Kenya; Jashore, Bangladesh; Canberra, Australia; Palermo, Italy; and Salvador and Campinas, Brazil.
These deployments are spread across every continent except Antarctica.
We’ve solidified our presence in every country of the Caucuses with our first deployment in the country of Georgia in the capital city of Tbilisi. And on the other side of the world, we’ve Continue reading
Getting SASE? Four Guidelines for Success
The larger and more diverse your infrastructure, the more your SASE approach will need to deliver all the security you require now without limiting your options for the future.Thank You for Everything Irena, We’ll Miss You Badly
In February 2018, Irena Marčetič joined ipSpace.net to fix the (lack of) marketing. After getting that done, she quickly took over most of sales, support, logistics, content production, guest speaker coordination… If you needed anything from us in the last few years, it was probably Irena answering your requests and helping you out.
She did a fantastic job and transformed ipSpace.net from Ivan and an occasional guest speaker to a finely tuned machine producing several hours of new content every month. She organized our courses, worked with guest speakers, podcast guests and hosts, participated in every guest speaker webinar to take notes for the editing process, managed content editing, watched every single video we created before it was published to make sure the audio was of acceptable quality and all the bloopers were removed… while answering crazy emails like I need you to fill in this Excel spreadsheet with your company data because I cannot copy-paste that information from your web site myself and solving whatever challenges our customers faced.
Unfortunately, Irena decided to go back to pure marketing and is leaving ipSpace.net today. Thanks a million for all the great work – we’ll badly miss you.
Thank You for Everything Irena, We’ll Miss You Badly
In February 2018, Irena Marčetič joined ipSpace.net to fix the (lack of) marketing. After getting that done, she quickly took over most of sales, support, logistics, content production, guest speaker coordination… If you needed anything from us in the last few years, it was probably Irena answering your requests and helping you out.
She did a fantastic job and transformed ipSpace.net from Ivan and an occasional guest speaker to a finely tuned machine producing several hours of new content every month. She organized our courses, worked with guest speakers, podcast guests and hosts, participated in every guest speaker webinar to take notes for the editing process, managed content editing, watched every single video we created before it was published to make sure the audio was of acceptable quality and all the bloopers were removed… while answering crazy emails like I need you to fill in this Excel spreadsheet with your company data because I cannot copy-paste that information from your web site myself and solving whatever challenges our customers faced.
Unfortunately, Irena decided to go back to pure marketing and is leaving ipSpace.net today. Thanks a million for all the great work – we’ll badly miss you.
Full Stack Journey 055: Application Migration And Kubernetes
Are application migrations still a thing in the cloud-native world? In this episode of the Full Stack Journey podcast, host Scott Lowe is joined by Nicholas Lane, Staff Engineer on the Kubernetes platform team at Wayfair, to discuss application migrations in a Kubernetes environment.
The post Full Stack Journey 055: Application Migration And Kubernetes appeared first on Packet Pushers.
Full Stack Journey 055: Application Migration And Kubernetes
Are application migrations still a thing in the cloud-native world? In this episode of the Full Stack Journey podcast, host Scott Lowe is joined by Nicholas Lane, Staff Engineer on the Kubernetes platform team at Wayfair, to discuss application migrations in a Kubernetes environment.How Routers Really Work Live Webinar
I’m teaching a webinar on router internals through Pearson (Safari Books Online) on the 23rd of July. From the abstract—
A network device—such as a router, switch, or firewall—is often seen as a single “thing,” an abstract appliance that is purchased, deployed, managed, and removed from service as a single unit. While network devices do connect to other devices, receiving and forwarding packets and participating in a unified control plane, they are not seen as a “system” in themselves.