SD-WAN Config Is Not Mystical – Video
Michael Shepherd, CTO at Rogers-O’Brien Construction, talks through his SD-WAN experience. He points out that it wasn’t hard to configure a full-mesh architecture. That’s a stark contrast to hugging your router dearly to your chest while reciting DMVPN configuration stanzas and staring at your phone in case you need to call TAC…who you have on […]
The post SD-WAN Config Is Not Mystical – Video appeared first on Packet Pushers.
It is Easier to Move a Problem than Solve it (RFC1925, Rule 6)

Early on in my career as a network engineer, I learned the value of sharing. When I could not figure out why a particular application was not working correctly, it was always useful to blame the application. Conversely, the application owner was often quite willing to share their problems with me, as well, by blaming the network.
A more cynical way of putting this kind of sharing is the way RFC 1925, rule 6 puts is: “It is easier to move a problem around than it is to solve it.”
Of course, the general principle applies far beyond sharing problems with your co-workers. There are many applications in network and protocol design, as well. Perhaps the most widespread case deployed in networks today is the movement to “let the controller solve the problem.” Distributed routing protocols are hard? That’s okay, just implement routing entirely on a controller. Understanding how to deploy individual technologies to solve real-world problems is hard? Simple—move the problem to the controller. All that’s needed is to tell the controller what we intend to do, and the controller can figure the rest out. If you have problems solving any problem, just call it Software Defined Continue reading
Seamlessly Merging Private Mobile Networks with Corporate LANs
Enterprises may soon be able to take the technological advancements of 5G networking and seamlessly merge them with their existing corporate network.The State Of Networking With Ivan Pepelnjak
In this episode, we sit down with Ivan Pepelnjak and talk about the state of networking. We briefly talk about cloud-networking and move onto network automation discussing the pros & cons of the various solutions and frameworks in the market highlighting the importance of extensibility. Finally, we talk about Ivan’s new open source project targeted to simplify the process of standing up a new virtual lab environment.
Relevant Links
Outro Music:
Danger Storm Kevin MacLeod (incompetech.com)
Licensed under Creative Commons: By Attribution 3.0 License
http://creativecommons.org/licenses/by/3.0/
The post The State Of Networking With Ivan Pepelnjak appeared first on Network Collective.
2020 U.S. Election: Cybersecurity Analysis
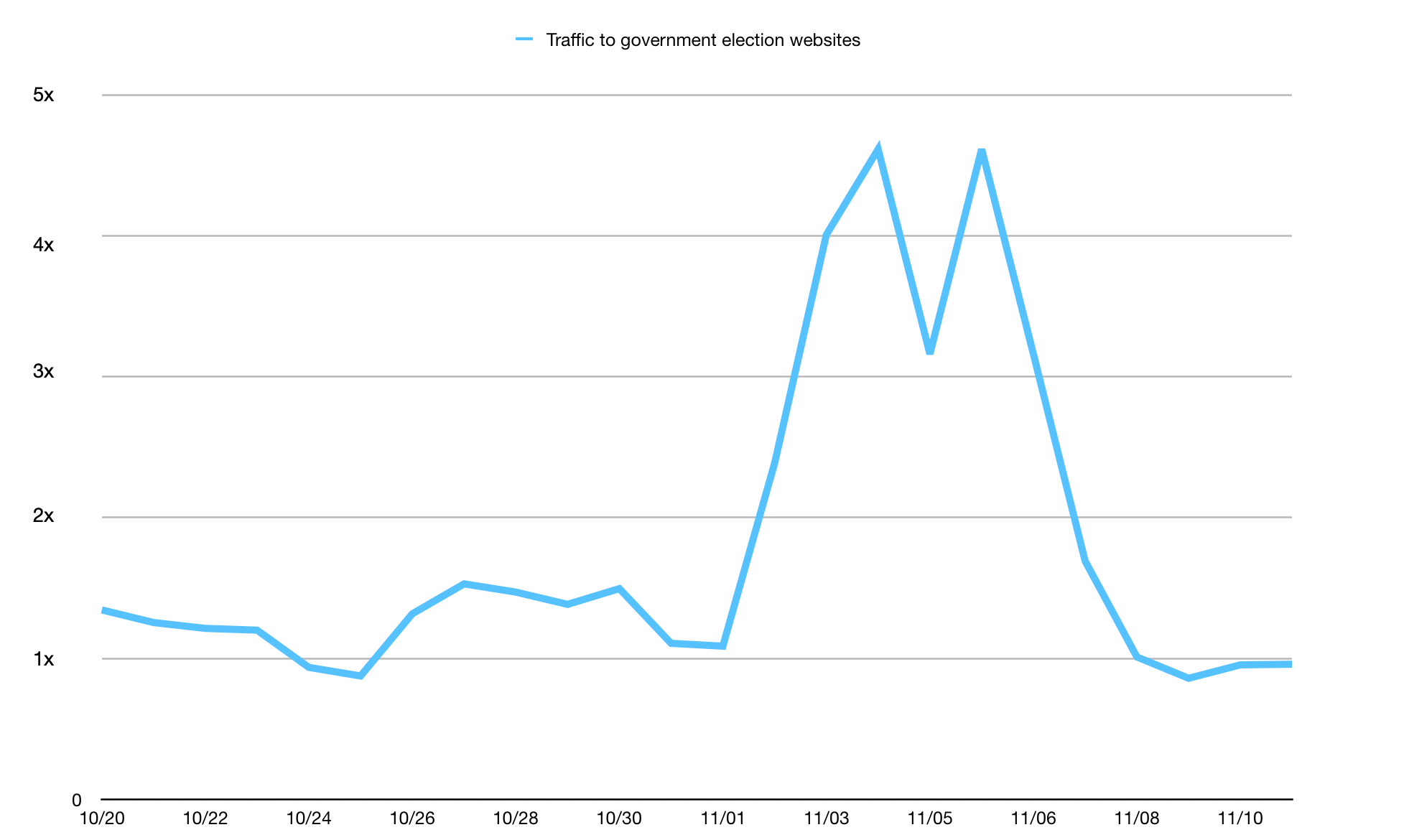
As the election season has ramped down and the new Presidential Administration begins, we think it’s important to assess whether there are lessons we can draw from our experience helping to provide cybersecurity services for those involved in the 2020 U.S. elections.
Cloudflare built the Athenian Project - our project to provide free services to state and local election websites - around the idea that access to the authoritative voting information offered by state and local governments is key to a functioning democracy and that Cloudflare could play an important role in ensuring that election-related websites are protected from cyberattacks intended to disrupt that access. Although the most significant challenges in this election cycle fell outside the realm of cybersecurity, the 2020 election certainly validated the importance of having access to definitive sources of authoritative election information.
We were pleased that the robust cybersecurity preparations we saw for the 2020 U.S. election appeared to be successful. From the Cloudflare perspective, we had the opportunity to witness firsthand the benefits of having access to free cybersecurity services provided to organizations that promote accurate voting information and election results, state and local governments conducting elections, and federal U.S candidates Continue reading
Tier 1 Carriers Performance Report: January, 2021
The post Tier 1 Carriers Performance Report: January, 2021 appeared first on Noction.
Demonstrate Small Automation Wins
Long long time ago in a country far far away when traveling was still a thing I led an interesting data center fabric design workshop. We covered tons of interesting topics, including automating network services deployments (starting with VLAN self-service for server admins).
As was often the case in my workshops, we had representatives from multiple IT teams sitting in the room, and when I started explaining how I’d automate VLAN deployments, the server administrator participating in the workshop quickly chimed in: “that’s exactly how I implemented self-service for some of our customers, it makes perfect sense to use the same approach for server port and VLAN provisioning”, and everyone else in the room agreed… apart from the networking engineer, who used a counter-argument along the lines of “we only provision a new VLAN or server port every few days, we can do it by hand” and no amount of persuasion would move him.
Demonstrate Small Automation Wins
Long long time ago in a country far far away when traveling was still a thing I led an interesting data center fabric design workshop. We covered tons of interesting topics, including automating network services deployments (starting with VLAN self-service for server admins).
As was often the case in my workshops, we had representatives from multiple IT teams sitting in the room, and when I started explaining how I’d automate VLAN deployments, the server administrator participating in the workshop quickly chimed in: “that’s exactly how I implemented self-service for some of our customers, it makes perfect sense to use the same approach for server port and VLAN provisioning”, and everyone else in the room agreed… apart from the networking engineer, who used a counter-argument along the lines of “we only provision a new VLAN or server port every few days, we can do it by hand” and no amount of persuasion would move him.
Don’t Make Parents Raise Kids in a World without Encryption

Natalie Campbell, Director of Public Advocacy at the Internet Society and a mother of two, warns against banning or weakening of encryption for the safety of children online.
Governments and law enforcement agencies are trying to ban or weaken a critical tool for keeping our children safe online. As parents, we must speak up for our kids.
Children who are fortunate enough to have Internet access are online more than ever, and many are increasingly doing learning online. But these spaces are attractive targets for criminals, and parents and schools often lack resources to guide kids on how to stay safe as they learn, socialize, and discover the world online.
Luckily, encryption has our back. Whether it’s sending a confidential message to a friend, videoconferencing with grandparents, or submitting an assignment to a teacher, platforms and services that use end-to-end encryption can help keep our children safe by keeping the line of communication private between the sender and receiver.
Despite this, some governments, law enforcement agencies, and even some child protection agencies are trying take away the strongest digital tool we have as parents to keep children safe online. The United Kingdom, Germany, the European Commission, and the Continue reading
Go Notes: Types
All about types in Golang.Tech Bytes: Get Your Arms Around Network Changes With Infoblox’s NetMRI (Sponsored)
NetMRI from Infoblox is a network management tool with a variety of capabilities including device discovery and network topology mapping, configuration monitoring, change management, and more. We dive into what this tool can do with guests Ingmar Van Glabbeek, Senior Product Manager at Infoblox; and Adam Fox, Solution Architect at Empowered Networks. Infoblox is our sponsor for this Tech Bytes podcast.Tech Bytes: Get Your Arms Around Network Changes With Infoblox’s NetMRI (Sponsored)
NetMRI from Infoblox is a network management tool with a variety of capabilities including device discovery and network topology mapping, configuration monitoring, change management, and more. We dive into what this tool can do with guests Ingmar Van Glabbeek, Senior Product Manager at Infoblox; and Adam Fox, Solution Architect at Empowered Networks. Infoblox is our sponsor for this Tech Bytes podcast.
The post Tech Bytes: Get Your Arms Around Network Changes With Infoblox’s NetMRI (Sponsored) appeared first on Packet Pushers.
Rethinking BGP on the DC Fabric (part 2)
In my last post on this topic, I laid out the purpose of this series—to start a discussion about whether BGP is the ideal underlay control plane for a DC fabric—and gave some definitions. Here, I’d like to dive into the reasons to not use BGP as a DC fabric underlay control plane—and the first of these reasons is BGP converges very slowly and requires a lot of help to converge at all.
Examples abound. I’ve seen the results of two testbeds in the last several years where a DC fabric was configured with each router (switch, if you prefer) in a separate AS, and some number of routes pushed into the network. In both cases—one large-scale, the other a more moderately scaled network on physical hardware—BGP simply failed to converge. Why? A quick look at how BGP converges might help explain these results.

Assume we are watching the 110::/64 route (attached to A, on the left side of the diagram), at P. What happens when A loses it’s connection to 110::/64? Assuming every router in this diagram is in a different AS, and the AS path length is the only factor determining the best path at every router.
Watching Continue reading
Who won Super Bowl LV? A look at Internet traffic during the game


The obvious answer is the Tampa Bay Buccaneers but the less obvious answer comes from asking “which Super Bowl advertiser got the biggest Internet bump?”. This blog aims to answer that question.
Before, during, and after the game a crack team of three people who work on Cloudflare Radar looked at real time statistics for traffic to advertisers’ websites, social media in the US, US food delivery services, and websites covering (American) football. Luckily, one of us (Kari) is (a) American and (b) a fan of football. Unluckily, one of us (Kari) is a fan of the Kansas City Chiefs.
Cloudflare Radar uses a variety of sources to provide aggregate information about Internet traffic and attack trends. In this blog post we use DNS name resolution data to estimate traffic to websites. We can’t see who visited the websites mentioned below, or what anyone did on the websites, but DNS can give us an estimate of the interest generated by the commercials. This analysis only looked at the top-level names in each domain (so example.com and www.example.com and not any other subdomains).
The Big Picture
To get the ball rolling here’s a look at traffic to Continue reading
Introducing the MANRS Ambassador Program 2021

The MANRS (Mutually Agreed Norms for Routing Security) Ambassador Program 2021 is now accepting applications. If you are an industry leader eager to improve the well-being of the Internet’s global routing system, apply now.
Ambassadors are representatives from MANRS participant organizations who show expertise and leadership in the routing security community. They are well-respected professionals committed to helping make the global routing infrastructure more robust and secure.
Ambassadors will work with MANRS Fellows, participants in an associated program that will invite applications next month. Together, they will train diverse communities on good routing practices, analyze routing incidents, research into ways to secure routing, and survey the global policy landscape.
You can read about the four Ambassadors in last year’s inaugural program, which proved highly popular. The Internet Society supports this program as part of its work to reduce common routing threats and establish norms for network operations.
You can apply to be a MANRS Ambassador in three different areas: training, research, and policy. Each Ambassador will receive a stipend of $1,500 a month. The program will start in mid-April and run for up to eight months. You can apply for more than one category but will only be selected for Continue reading