State Consistency in Distributed SDN Controller Clusters
Every now and then I get a question along the lines of “why can’t we have a distributed SDN controller (because resiliency) that would survive network partitioning?” This time, it’s not the incompetency of solution architects or programmers, but the fundamental limitations of what can be done when you want to have consistent state across a distributed system.
TL&DR: If your first thought was CAP Theorem you’re absolutely right. You can probably stop reading right now. If you have no idea what I’m talking about, maybe it’s time you get fluent in distributed systems concepts after you’re finished with this blog post and all the reference material linked in it. Don’t know where to start? I put together a list of resources I found useful.
State Consistency in Distributed SDN Controller Clusters
Every now and then I get a question along the lines of “why can’t we have a distributed SDN controller (because resiliency) that would survive network partitioning?” This time, it’s not the incompetency of solution architects or programmers, but the fundamental limitations of what can be done when you want to have consistent state across a distributed system.
TL&DR: If your first thought was CAP Theorem you’re absolutely right. You can probably stop reading right now. If you have no idea what I’m talking about, maybe it’s time you get fluent in distributed systems concepts after you’re finished with this blog post and all the reference material linked in it. Don’t know where to start? I put together a list of resources I found useful.
Practical Information Governance Starts with IT
This year, the landscape of corporate risk has become increasingly intense and complicated, making sound, practical IG more important than ever before.Meraki-CLI – Command Line Utility for the Meraki Dashboard
Meraki changed the industry years ago as one of the first platforms to use a cloud portal for all configuration; forgoing the typical local CLI/GUI administration of network appliances. One of the first things a traditional network engineer (like myself) may notice about Meraki equipment is their complete lack of a command-line interface. For the […]
The post Meraki-CLI – Command Line Utility for the Meraki Dashboard appeared first on Packet Pushers.
Jassy’s Replacement At AWS Matters
As Andy Jassy takes over the CEO role at Amazon, the question is asked, “Does it matter who takes over at AWS, the position Jassy is vacating?” The idea is that AWS is such a dominant force in public cloud, an untrained monkey could sit at the helm and AWS would continue printing billions of dollars. So who cares who replaces Jassy? Whoever the new human is, they can’t get it wrong.
That might be exactly right, but for the thought exercise, I decided to go a different direction. For purposes of this opinion article, I choose to entertain the idea that Jassy’s replacement does matter, and matters a lot.
Growing A Gargantuan Gorilla
We can all agree that AWS is the 800 pound gorilla of public cloud. However, I believe AWS will see increasing pressure from all quarters. By way of comparison, let’s consider Cisco Systems of the last ten years.
Cisco has dominated the networking space in a variety of categories for a very long time. The last decade has seen them as the target all of their competitors aim at. In that context, did it matter who replaced John Chambers when he moved on? You Continue reading
Master Class: Security in the Design of DC Fabrics
I’m teaching another master class over at Juniper on February the 10th at 12 noon PT (3PM ET):
It’s typical to think about scale, speed, oversubscription, and costs when designing a data center fabric. But what about security in a world increasingly focused on privacy, data protection, and preventing downtime caused by cyber breaches? This session will consider how data center fabric software and control plane components can impact security, including the ability to effectively manage segmentation policy, controlling failure domains, and the impact host-based routing has on fabric security.
SD-WAN Config Is Not Mystical – Video
Michael Shepherd, CTO at Rogers-O’Brien Construction, talks through his SD-WAN experience. He points out that it wasn’t hard to configure a full-mesh architecture. That’s a stark contrast to hugging your router dearly to your chest while reciting DMVPN configuration stanzas and staring at your phone in case you need to call TAC…who you have on […]
The post SD-WAN Config Is Not Mystical – Video appeared first on Packet Pushers.
It is Easier to Move a Problem than Solve it (RFC1925, Rule 6)

Early on in my career as a network engineer, I learned the value of sharing. When I could not figure out why a particular application was not working correctly, it was always useful to blame the application. Conversely, the application owner was often quite willing to share their problems with me, as well, by blaming the network.
A more cynical way of putting this kind of sharing is the way RFC 1925, rule 6 puts is: “It is easier to move a problem around than it is to solve it.”
Of course, the general principle applies far beyond sharing problems with your co-workers. There are many applications in network and protocol design, as well. Perhaps the most widespread case deployed in networks today is the movement to “let the controller solve the problem.” Distributed routing protocols are hard? That’s okay, just implement routing entirely on a controller. Understanding how to deploy individual technologies to solve real-world problems is hard? Simple—move the problem to the controller. All that’s needed is to tell the controller what we intend to do, and the controller can figure the rest out. If you have problems solving any problem, just call it Software Defined Continue reading
Seamlessly Merging Private Mobile Networks with Corporate LANs
Enterprises may soon be able to take the technological advancements of 5G networking and seamlessly merge them with their existing corporate network.The State Of Networking With Ivan Pepelnjak
In this episode, we sit down with Ivan Pepelnjak and talk about the state of networking. We briefly talk about cloud-networking and move onto network automation discussing the pros & cons of the various solutions and frameworks in the market highlighting the importance of extensibility. Finally, we talk about Ivan’s new open source project targeted to simplify the process of standing up a new virtual lab environment.
Relevant Links
Outro Music:
Danger Storm Kevin MacLeod (incompetech.com)
Licensed under Creative Commons: By Attribution 3.0 License
http://creativecommons.org/licenses/by/3.0/
The post The State Of Networking With Ivan Pepelnjak appeared first on Network Collective.
2020 U.S. Election: Cybersecurity Analysis
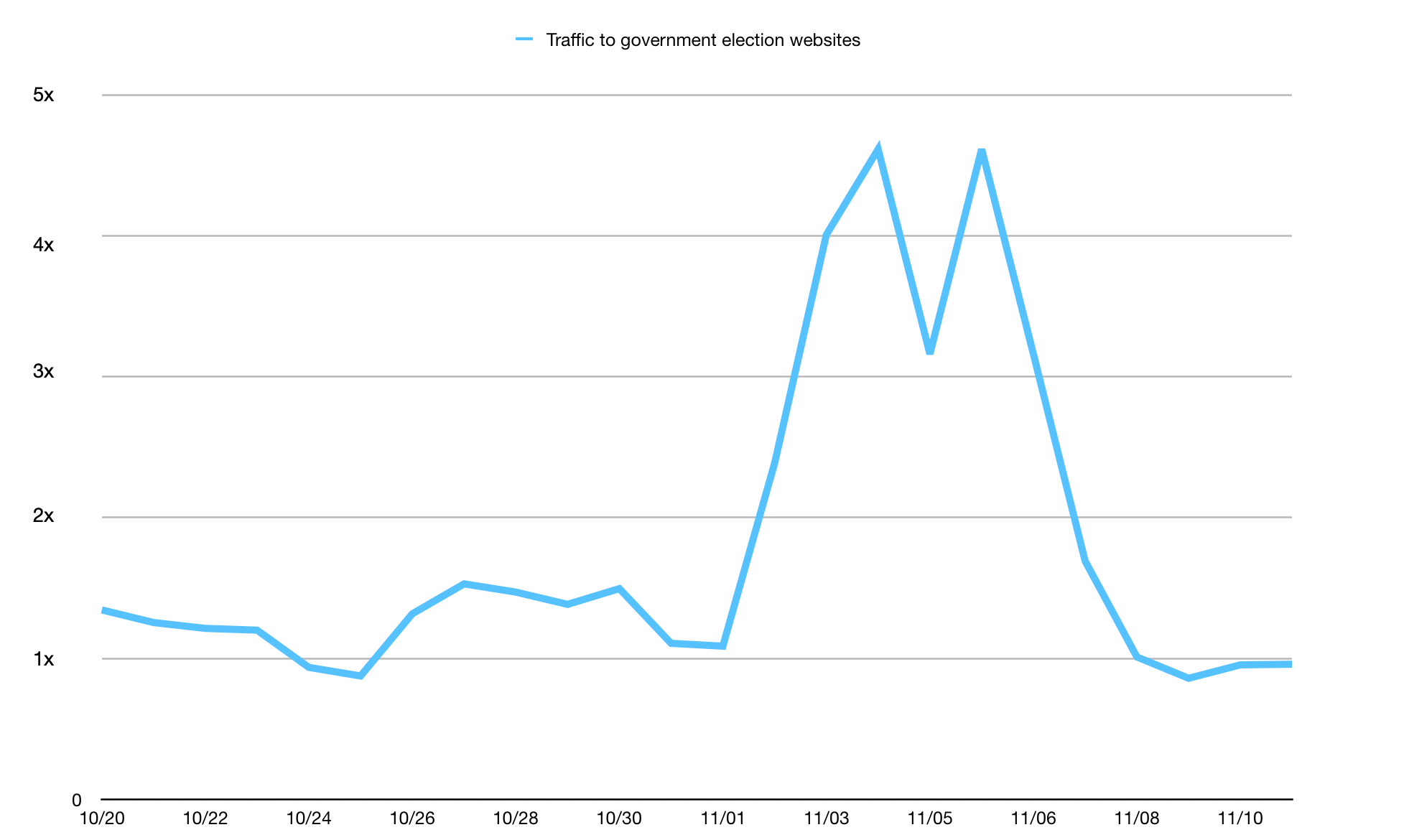
As the election season has ramped down and the new Presidential Administration begins, we think it’s important to assess whether there are lessons we can draw from our experience helping to provide cybersecurity services for those involved in the 2020 U.S. elections.
Cloudflare built the Athenian Project - our project to provide free services to state and local election websites - around the idea that access to the authoritative voting information offered by state and local governments is key to a functioning democracy and that Cloudflare could play an important role in ensuring that election-related websites are protected from cyberattacks intended to disrupt that access. Although the most significant challenges in this election cycle fell outside the realm of cybersecurity, the 2020 election certainly validated the importance of having access to definitive sources of authoritative election information.
We were pleased that the robust cybersecurity preparations we saw for the 2020 U.S. election appeared to be successful. From the Cloudflare perspective, we had the opportunity to witness firsthand the benefits of having access to free cybersecurity services provided to organizations that promote accurate voting information and election results, state and local governments conducting elections, and federal U.S candidates Continue reading
Tier 1 Carriers Performance Report: January, 2021
The post Tier 1 Carriers Performance Report: January, 2021 appeared first on Noction.