Fun Times: Another Broken Linux ALG
Dealing with protocols that embed network-layer addresses into application-layer messages (like FTP or SIP) is great fun, more so if the said protocol traverses a NAT device that has to find the IP addresses embedded in application messages while translating the addresses in IP headers. For whatever reason, the content rewriting functionality is called application-level gateway (ALG).
Even when we’re faced with a monstrosity like FTP or SIP that should have been killed with napalm a microsecond after it was created, there’s a proper way of doing things and a fast way of doing things. You could implement a protocol-level proxy that would intercept control-plane sessions… or you could implement a hack that tries to snoop TCP payload without tracking TCP session state.
Not surprisingly, the fast way of doing things usually results in a wonderful attack surface, more so if the attacker is smart enough to construct HTTP requests that look like SIP messages. Enjoy ;)
What’s Your Work From Home DR Plan?

It’s almost December and the signs are pointing to a continuation of the current state of working from home for a lot of people out there. Whether it’s a surge in cases that is causing businesses to close again or a change in the way your company looks at offices and remote work, you’re likely going to ring in the new year at your home keyboard in your pajamas with a cup of something steaming next to your desk.
We have all spent a lot of time and money investing in better conditions for ourselves at home. Perhaps it was a fancy new mesh chair or a more ergonomic keyboard. It could have been a bigger monitor with a resolution increase or a better webcam for the dozen or so Zoom meetings that have replaced the water cooler. There may even be more equipment in store, such as a better home wireless setup or even a corporate SD-WAN solution to help with network latency. However, have you considered what might happen if it all goes wrong and you need to be online?
In and Outage
Outages happen more often than we realize. That’s never been more evident than the situation Continue reading
Networking and Infrastructure News Roundup: November 27 Edition
In the news this week: New managed services for improving workflows in multi-clouds and for administering storage in and across hybrid environments.Securing Modern Applications
Modern applications are changing enterprise security. Apps today are comprised of dozens, or even hundreds, of microservices. They can be spun up and down in real time and may span multiple clouds (on–premises, private cloud, and public cloud). Traditional security stacks just aren’t suited to protecting these applications consistently.
To effectively secure modern apps, we start by identifying unique application assets across clouds—such as users, services, and data. We then continuously evaluate their risk and automatically make authorization decisions to adjust our application security and compliance posture based on asset identity—regardless of where they are or where they have moved.
Security professionals can learn how to use VMware network and security solutions to secure modern applications in the following VMworld sessions:
Security Policies for Modern Applications: An Evolution from Micro-segmentation (ISCS2240)
Enterprises are embracing cloud native transformation and modernizing traditional applications, from monolithic to microservices architectures. As applications transform and span multiple clouds (on–premises, private cloud, and public cloud), it’s essential to Continue reading
Get Off Social Media! Things to Spend Your Time on Instead
Social media can be hard to navigate especially now that there are so many platforms available at the touch of a button. Humans haven’t had enough time to evolve to social media and the vast technological innovations we’ve made. Twenty years ago, humans spent an average of 2-4 hours on their phones and the internet and now that number has grown to 10-14 hours.
This is a massive change over a very short amount of time. This, in conjunction with the effects of the coronavirus pandemic on society, has had a rather large impact on frequent users of the internet. Despite the surplus of internet websites and platforms, people are feeling more lonely and detached than ever.
If you’re struggling with these feelings and other negative feelings as a result of the echo that is social media, here are 5 things you can do instead:
Go Outside!
Depending on the lockdown rules in your state or country, you should consider going outside. It is important that you experience nature, see other human beings, and remind yourself that you are not alone in the world. You can take a walk, go on a run or just sit on your balcony and Continue reading
Heavy Networking 552: How Fortinet Enables Multi-Vendor Security Integration (Sponsored)
On today's Heavy Networking, sponsored by Fortinet, we dive into a variety of topics including a multiplicity of edges that require connectivity and security (WAN edge, LAN edge, cloud edge, remote edge, etc.), the convergence of infrastructure and security, the need for interoperability among security vendors, implementing Zero Trust Access (ZTA), and the current and future roles for machine learning and AI. Our guest is John Maddison, EVP of Products.
The post Heavy Networking 552: How Fortinet Enables Multi-Vendor Security Integration (Sponsored) appeared first on Packet Pushers.
Heavy Networking 552: How Fortinet Enables Multi-Vendor Security Integration (Sponsored)
On today's Heavy Networking, sponsored by Fortinet, we dive into a variety of topics including a multiplicity of edges that require connectivity and security (WAN edge, LAN edge, cloud edge, remote edge, etc.), the convergence of infrastructure and security, the need for interoperability among security vendors, implementing Zero Trust Access (ZTA), and the current and future roles for machine learning and AI. Our guest is John Maddison, EVP of Products.ASICs at the Edge
At Cloudflare we pride ourselves in our global network that spans more than 200 cities in over 100 countries. To handle all the traffic passing through our network, there are multiple technologies at play. So let’s have a look at one of the cornerstones that makes all of this work… ASICs. No, not the running shoes.
What's an ASIC?
ASIC stands for Application Specific Integrated Circuit. The name already says it, it's a chip with a very narrow use case, geared towards a single application. This is in stark contrast to a CPU (Central Processing Unit), or even a GPU (Graphics Processing Unit). A CPU is designed and built for general purpose computation, and does a lot of things reasonably well. A GPU is more geared towards graphics (it's in the name), but in the last 15 years, there's been a drastic shift towards GPGPU (General Purpose GPU), in which technologies such as CUDA or OpenCL allow you to use the highly parallel nature of the GPU to do general purpose computing. A good example of GPU use is video encoding, or more recently, computer vision, used in applications such as self-driving cars.
Unlike CPUs or GPUs, ASICs are built Continue reading
A Byzantine failure in the real world
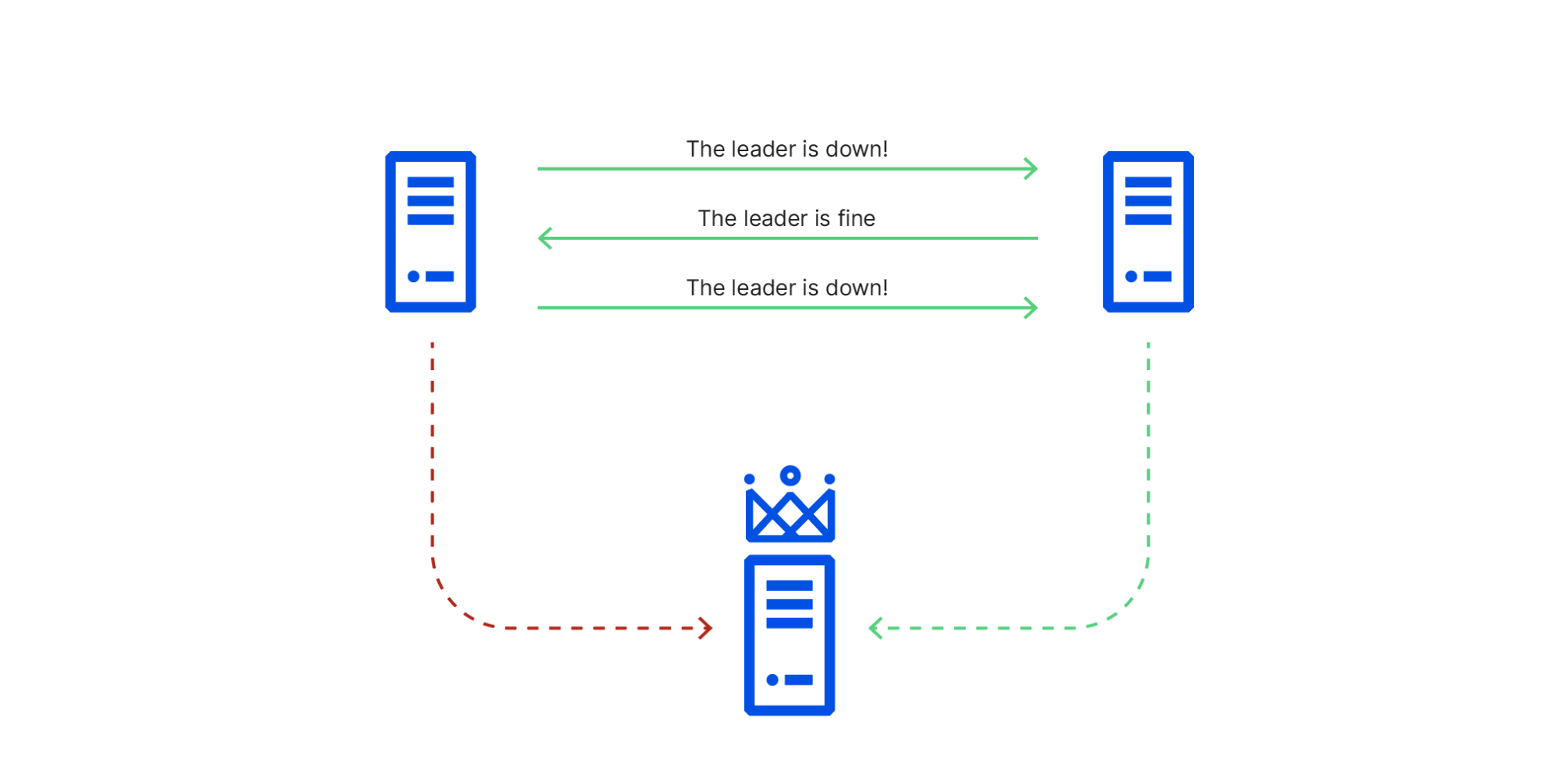
An analysis of the Cloudflare API availability incident on 2020-11-02
When we review design documents at Cloudflare, we are always on the lookout for Single Points of Failure (SPOFs). Eliminating these is a necessary step in architecting a system you can be confident in. Ironically, when you’re designing a system with built-in redundancy, you spend most of your time thinking about how well it functions when that redundancy is lost.
On November 2, 2020, Cloudflare had an incident that impacted the availability of the API and dashboard for six hours and 33 minutes. During this incident, the success rate for queries to our API periodically dipped as low as 75%, and the dashboard experience was as much as 80 times slower than normal. While Cloudflare’s edge is massively distributed across the world (and kept working without a hitch), Cloudflare’s control plane (API & dashboard) is made up of a large number of microservices that are redundant across two regions. For most services, the databases backing those microservices are only writable in one region at a time.
Each of Cloudflare’s control plane data centers has multiple racks of servers. Each of those racks has two switches that operate as a pair—both Continue reading
Reviving Old Content, Part 1
More than a decade ago I published tons of materials on a web site that eventually disappeared into digital nirvana, leaving heaps of broken links on my blog. I decided to clean up those links, and managed to save some of the vanished content from the Internet Archive:
- OSPF Flooding Filters in Hub-and-Spoke Environments
- Implicit and Explicit Null Label in MPLS networks
- Default Routes in BGP
- Filter Excessively Prepended BGP Paths
I also updated dozens of blog posts while pretending to be Indiana Jones, including:
Reviving Old Content, Part 1
More than a decade ago I published tons of materials on a web site that eventually disappeared into digital nirvana, leaving heaps of broken links on my blog. I decided to clean up those links, and managed to save some of the vanished content from the Internet Archive:
- OSPF Flooding Filters in Hub-and-Spoke Environments
- Implicit and Explicit Null Label in MPLS networks
- Default Routes in BGP
- Filter Excessively Prepended BGP Paths
I also updated dozens of blog posts while pretending to be Indiana Jones, including:
Building Black Friday e-commerce experiences with JAMstack and Cloudflare Workers
The idea of serverless is to allow developers to focus on writing code rather than operations — the hardest of which is scaling applications. A predictably great deal of traffic that flows through Cloudflare's network every year is Black Friday. As John wrote at the end of last year, Black Friday is the Internet's biggest online shopping day. In a past case study, we talked about how Cordial, a marketing automation platform, used Cloudflare Workers to reduce their API server latency and handle the busiest shopping day of the year without breaking a sweat.
The ability to handle immense scale is well-trodden territory for us on the Cloudflare blog, but scale is not always the first thing developers think about when building an application — developer experience is likely to come first. And developer experience is something Workers does just as well; through Wrangler and APIs like Workers KV, Workers is an awesome place to hack on new projects.
Over the past few weeks, I've been working on a sample open-source e-commerce app for selling software, educational products, and bundles. Inspired by Humble Bundle, it's built entirely on Workers, and it integrates powerfully with all kinds of first-class modern Continue reading
IPv6 Buzz 065: Understanding Carrier-Grade NAT (CGN) And IPv6
In this week's IPv6 Buzz episode, Ed and Tom talk discuss the impact that service provider deployment of Carrier Grade NAT (CGN) has had on the overall adoption of IPv6. Our guests are Kevin Myers and Nick Russo. Kevin and Nick have both worked with CGN and IPv6, and Nick is designing an IPv6 training course on Pluralsight.IPv6 Buzz 065: Understanding Carrier-Grade NAT (CGN) And IPv6
In this week's IPv6 Buzz episode, Ed and Tom talk discuss the impact that service provider deployment of Carrier Grade NAT (CGN) has had on the overall adoption of IPv6. Our guests are Kevin Myers and Nick Russo. Kevin and Nick have both worked with CGN and IPv6, and Nick is designing an IPv6 training course on Pluralsight.
The post IPv6 Buzz 065: Understanding Carrier-Grade NAT (CGN) And IPv6 appeared first on Packet Pushers.
Internet Society Foundation Awards over $1 Million in Digital Skills Development Grants

The Internet is for everyone – a critical lifeline that can uplift communities. But only if we go beyond Internet access and bridge the knowledge gap that continues to persist: the gap between those who have the knowledge and skills to use the Internet to empower themselves and their communities and those who don’t.
To address this divide, the Internet Society Foundation recently awarded over $1 million in digital skills development grants to eight innovative projects in Bangladesh, Colombia and Senegal. In its pilot year, the Strengthening Communities, Improving Lives and Livelihoods (SCILLS) grant programme aims to expand economic growth, improve health outcomes, and increase educational opportunities by supporting individuals and communities to more knowledgeably and skillfully use the Internet.
Learn more about these projects!

The Internet Society Foundation was established in 2019 to support the positive difference the Internet can make to people everywhere. The Foundation awards grants to Internet Society Chapters/Special Interest Groups (SIGs) as well as nonprofit organizations and individuals dedicated to providing meaningful access to an open, globally-connected, secure, and trustworthy Internet for everyone.
The post Internet Society Foundation Awards over $1 Million in Digital Skills Development Grants appeared first on Internet Society.
Tools 2. How to learn your public IP? Programatically?
Hello my friend,
Just recently we have started discussion about the tools about the performance troubleshooting in networks. One of the questions we were asked afterwards was, how to programatically get your public IP? Well, that is interesting one.
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
Can automation help with performance troubleshooting?
Yes, and that was a question we’ve started this blogpost with is about that. How can we rely the automation tools by troubleshooting? How can we get our IP to make any diagnostics? You will see some things right in this blogpost

Our network automation training has two faces: either live or self-paced. So you can choose yourself, what works better for you. On our side, we guide you from the foundation of the automation for the small networks till advanced automation use cases in big data centres, service providers, and clouds. You will lean how to structure the data using YANG modules, how to serialise it using JSON, XML, Protocol Continue reading
Over 300 Hours of Subscription Content on ipSpace.net
It’s amazing how far you can get if you keep doing something for a long-enough time. In a bit over 10 years (the initial versions of the earliest still-active webinars were created in October 2010), we accumulated over 300 hours of online content available with ipSpace.net subscription, plus another 130 hours of online course content.
Obviously I couldn’t have done that myself. Thanks a million to Irena who took over most of the day-to-day business a few years ago, dozens of authors, and thousands of subscribers who enabled us to make it all happen.
Over 300 Hours of Subscription Content on ipSpace.net
It’s amazing how far you can get if you keep doing something for a long-enough time. In a bit over 10 years (the initial versions of the earliest still-active webinars were created in October 2010), we accumulated over 300 hours of online content available with ipSpace.net subscription, plus another 130 hours of online course content.
Obviously I couldn’t have done that myself. Thanks a million to Irena who took over most of the day-to-day business a few years ago, dozens of authors, and thousands of subscribers who enabled us to make it all happen.