Tech Bytes: Fortinet’s SD-WAN Is Good Medicine For Healthcare Provider’s Video App (Sponsored)
Urgent care company PM Pediatrics relies on SD-WAN from Fortinet to provide the performance and security to support real-time voice and video applications as well as other critical apps, and to help cut bandwidth costs and streamline operations. Our guest is John Tabako, Director of IT Infrastructure for PM Pediatrics.Birthday Week on Cloudflare TV: Announcing 24 Hours of Live Discussions on the Future of the Internet
This week marks Cloudflare’s 10th birthday, and we’re excited to continue our annual tradition of launching an array of products designed to help give back to the Internet. (Check back here each morning for the latest!)
We also see this milestone as an opportunity to reflect on where the Internet was ten years ago, and where it might be headed over the next decade. So we reached out to some of the people we respect most to see if they’d be interested in joining us for a series of Fireside Chats on Cloudflare TV.
We’ve been blown away by the response, and are thrilled to announce our lineup of speakers, featuring many of the most celebrated names in tech and beyond. Among the highlights: Apple co-founder Steve Wozniak, Zoom CEO Eric Yuan, OpenTable CEO Debby Soo, Stripe co-founder and President John Collison, Former CEO & Executive Chairman, Google // Co-Founder, Schmidt Futures. Eric Schmidt, former McAfee CEO Chris Young, Magic Leap CEO and longtime Microsoft executive Peggy Johnson, former Seal Team 6 Commander Dave Cooper, Project Include CEO Ellen Pao, and so many more. All told, we have over 24 hours Continue reading
Random Thoughts

This week is very busy for me, so rather than writing a single long, post, I’m throwing together some things that have been sitting in my pile to write about for a long while.
From Dalton Sweeny:
This is precisely the way network engineering is. There is value in the kinds of knowledge that expire, such as individual product lines, etc.—but the closer you are to the configuration, the more ephemeral the knowledge is. This is one of the entire points of rule 11 is your friend. Learn the foundational things that make learning the ephemeral things Continue reading
Network Break 303: Ericsson Acquires Cradlepoint For WAN Connectivity; HPE/Silver Peak Deal Closes
Today's Network Break starts with follow-up to correct a few items, and then dives into Ericsson's Cradlepoint acquisition. On the acquisition front, HPE finalizes its Silver Peak purchase, Kentik adds synthetics to its visibility platform, Cisco bets on a live, in-person event in 2021, and more tech news.Network Break 303: Ericsson Acquires Cradlepoint For WAN Connectivity; HPE/Silver Peak Deal Closes
Today's Network Break starts with follow-up to correct a few items, and then dives into Ericsson's Cradlepoint acquisition. On the acquisition front, HPE finalizes its Silver Peak purchase, Kentik adds synthetics to its visibility platform, Cisco bets on a live, in-person event in 2021, and more tech news.
The post Network Break 303: Ericsson Acquires Cradlepoint For WAN Connectivity; HPE/Silver Peak Deal Closes appeared first on Packet Pushers.
The Week in Internet News: Lawmakers Hampered by Poor Internet Service

Too slow: Some state lawmakers in New Mexico are having trouble attending virtual committee meetings because of poor Internet service, Government Technology reports. State Rep. Micaela Lara Cadena has to share a slow connection with her children, who are attending virtual school. “The only Internet I can get comes through a phone line,” she said. “There’s no broadband, no fiber optics.”
Kicked out: Facebook and Twitter have removed several hundred fake accounts they said are linked to Russian military intelligence and other Kremlin-backed actors previously tied to interference in U.S. politics, NPR reports. The accounts were not tied to interference in the 2020 U.S. election, Facebook said, but they were linked to past attempts.
Investigating speech: In other Facebook news, the social media company is facing an investigation by a New Delhi government committee over its alleged role in religious riots earlier this year, CNN says. This is the second time in recent weeks that Facebook has been investigated for being used to spread controversial speech. Earlier, Facebook allowed a politician from India’s ruling party to remain on its platform even though his anti-Muslim posts appeared to violate rules against hate speech.
Targeting the dark web: One Continue reading
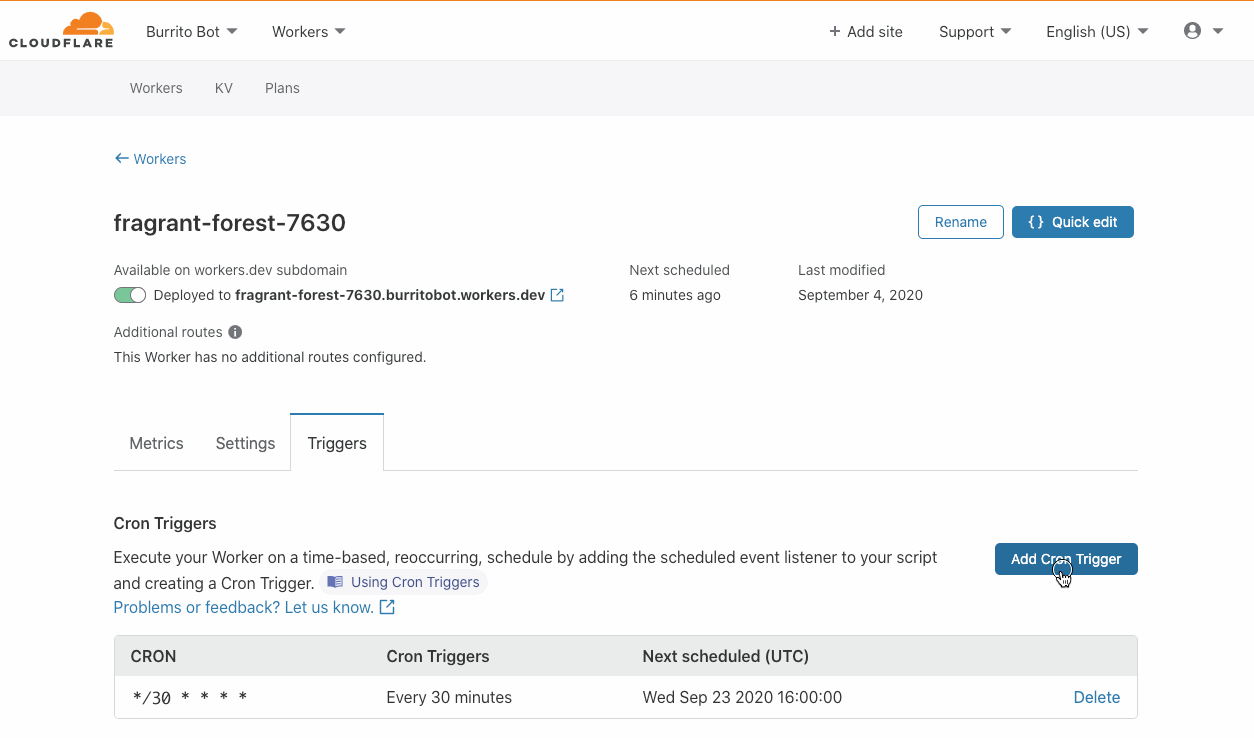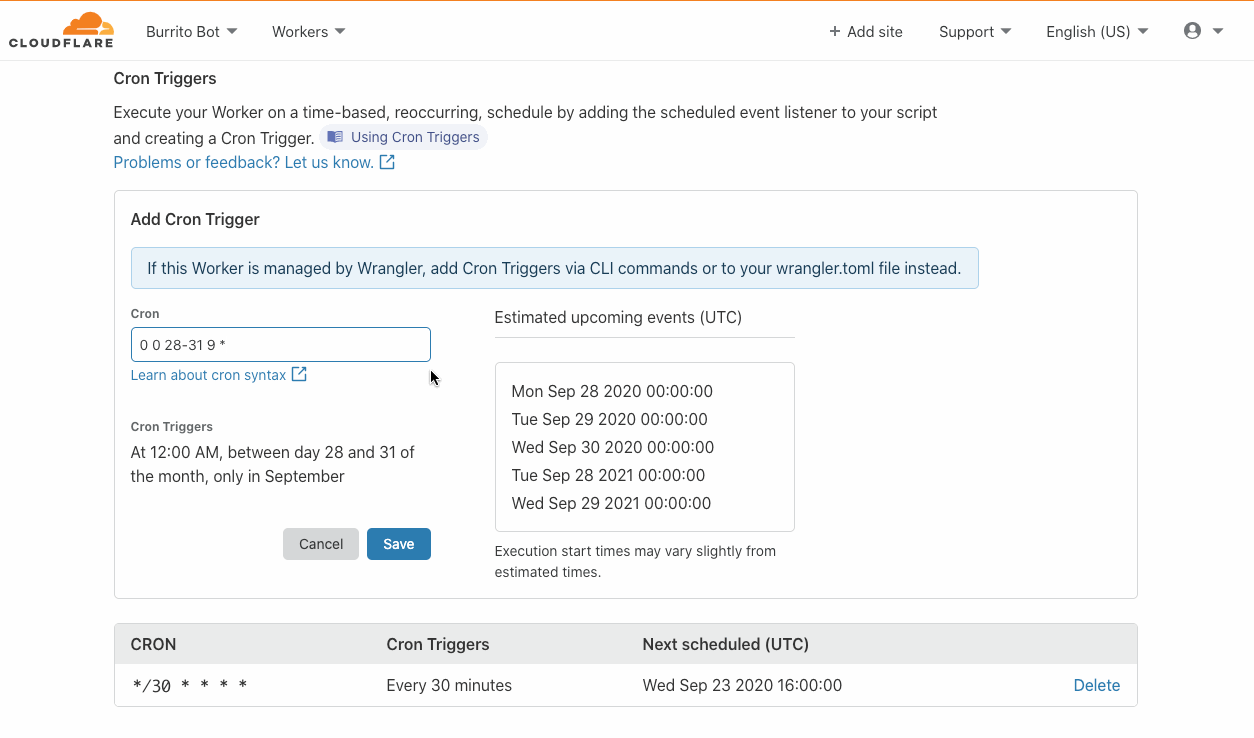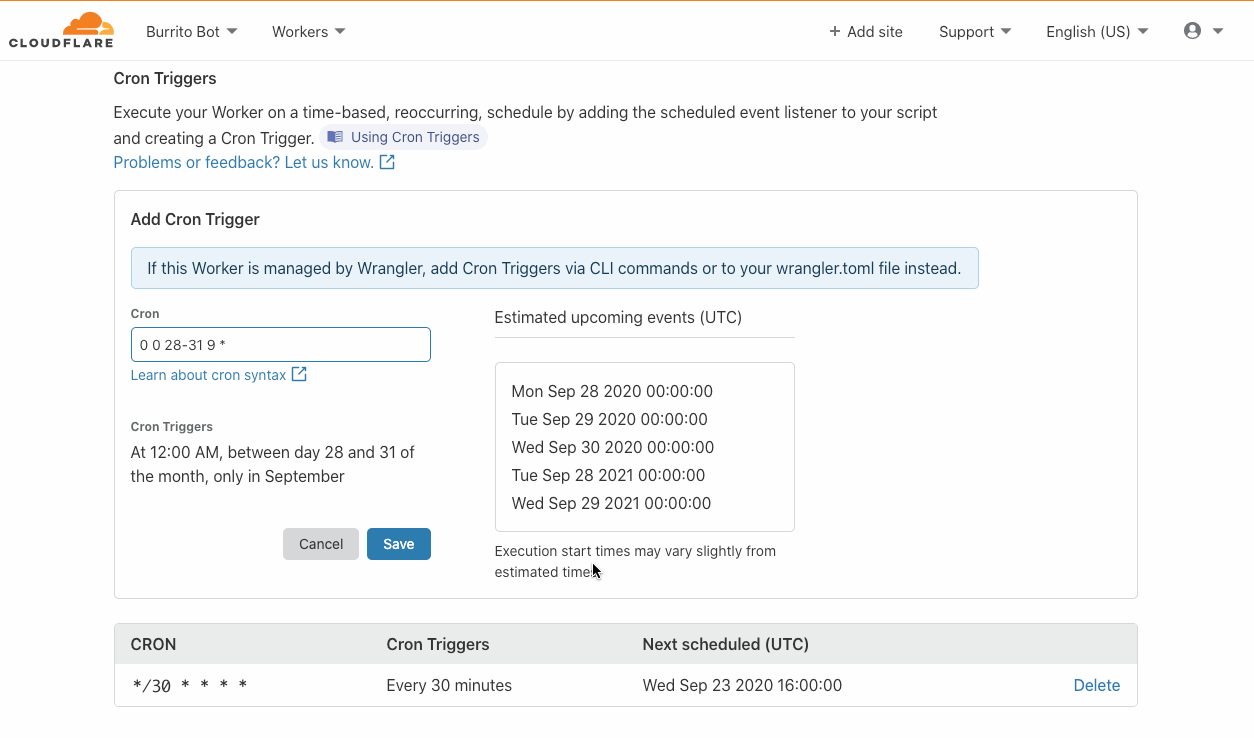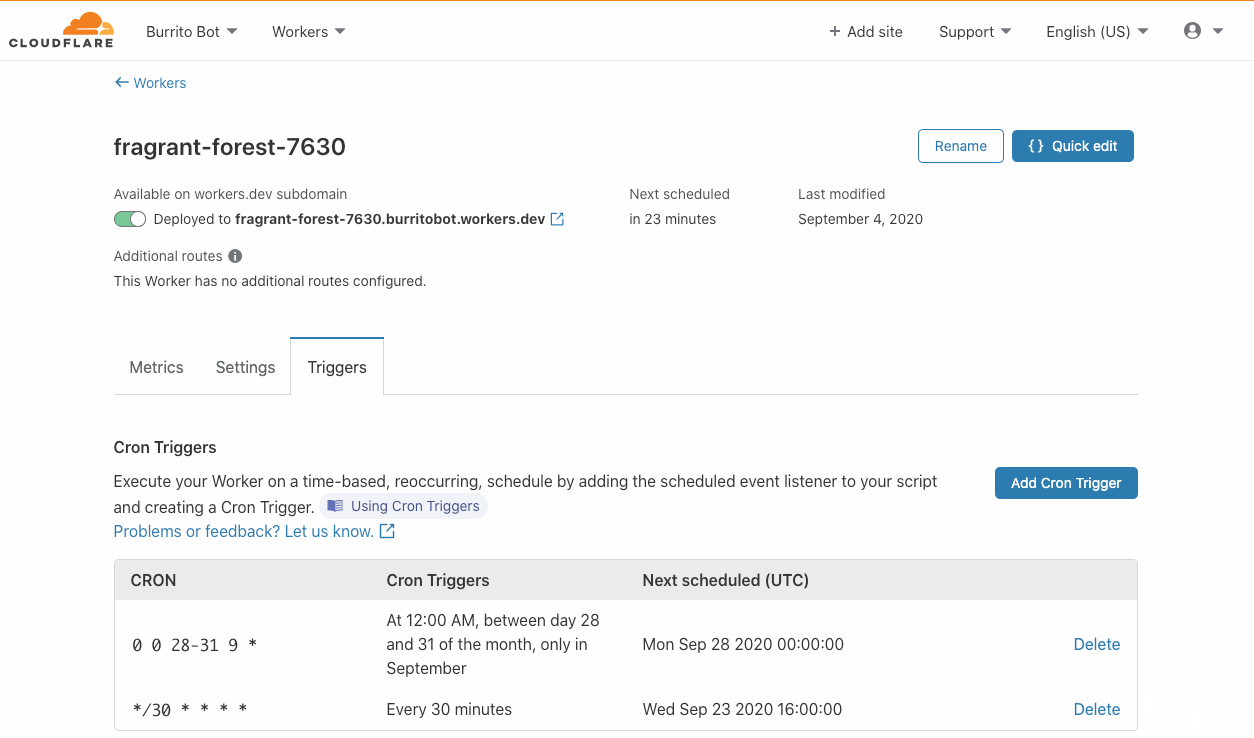
Introducing Cron Triggers for Cloudflare Workers


Today the Cloudflare Workers team is thrilled to announce the launch of Cron Triggers. Before now, Workers were triggered purely by incoming HTTP requests but starting today you’ll be able to set a scheduler to run your Worker on a timed interval. This was a highly requested feature that we know a lot of developers will find useful, and we’ve heard your feedback after Serverless Week.
We are excited to offer this feature at no additional cost, and it will be available on both the Workers free tier and the paid tier, now called Workers Bundled. Since it doesn’t matter which city a Cron Trigger routes the Worker through, we are able to maximize Cloudflare’s distributed system and send scheduled jobs to underutilized machinery. Running jobs on these quiet machines is both efficient and cost effective, and we are able to pass those cost savings down to you.
What is a Cron Trigger and how might I use such a feature?
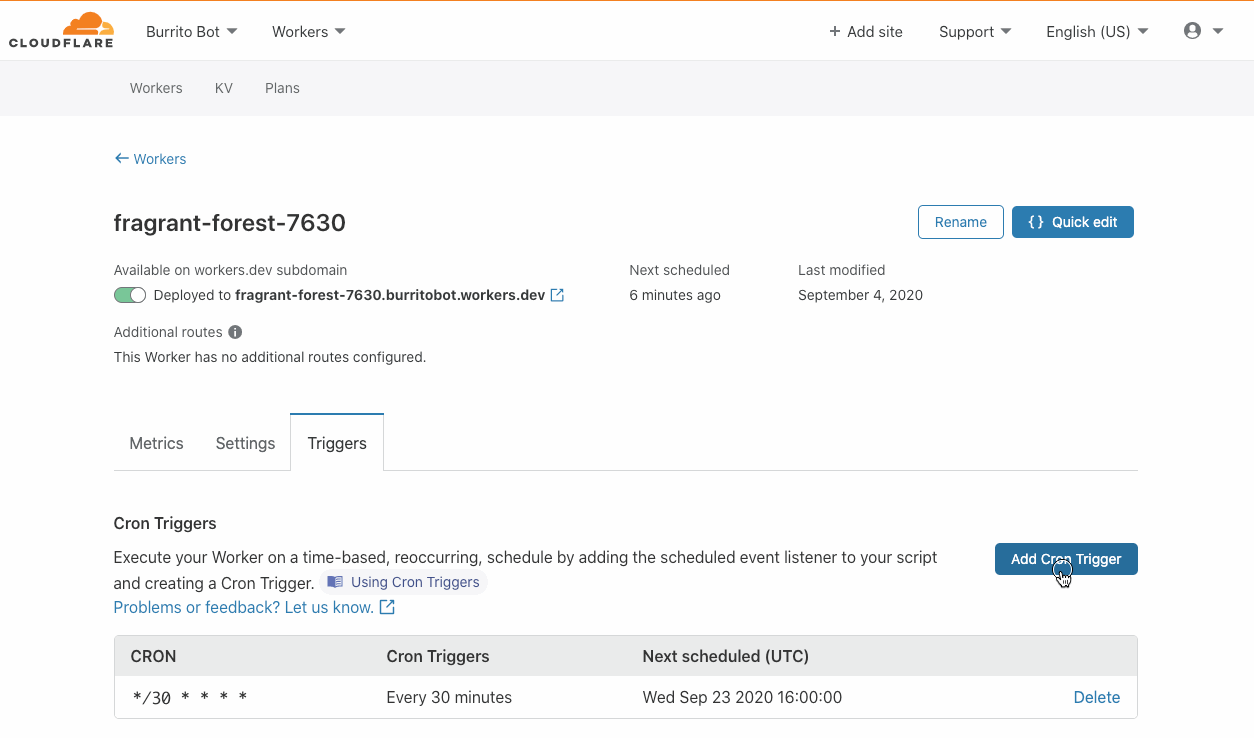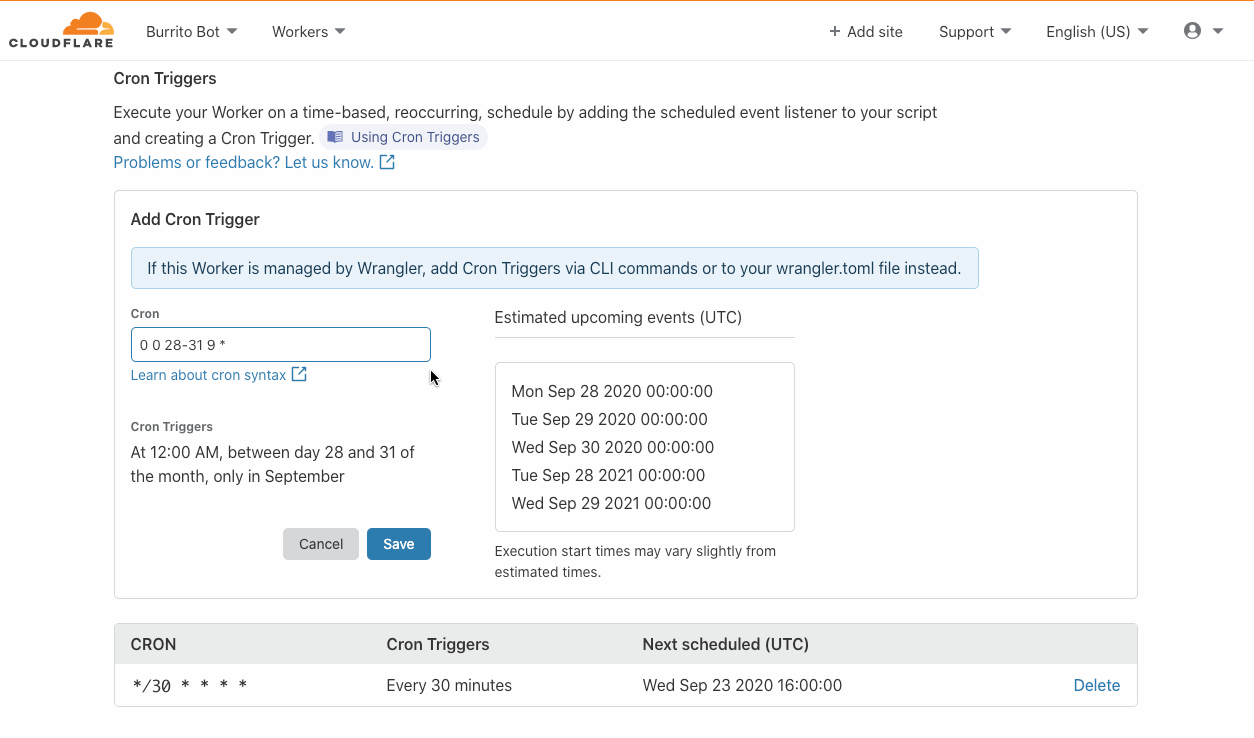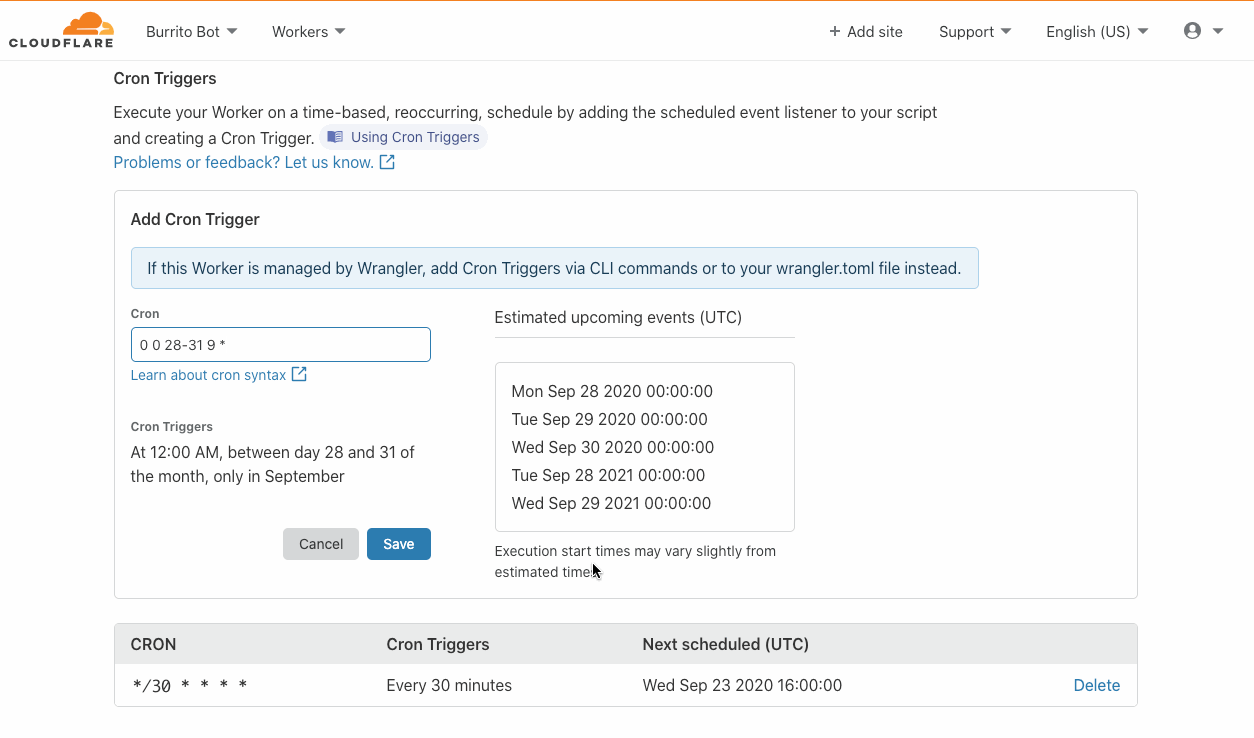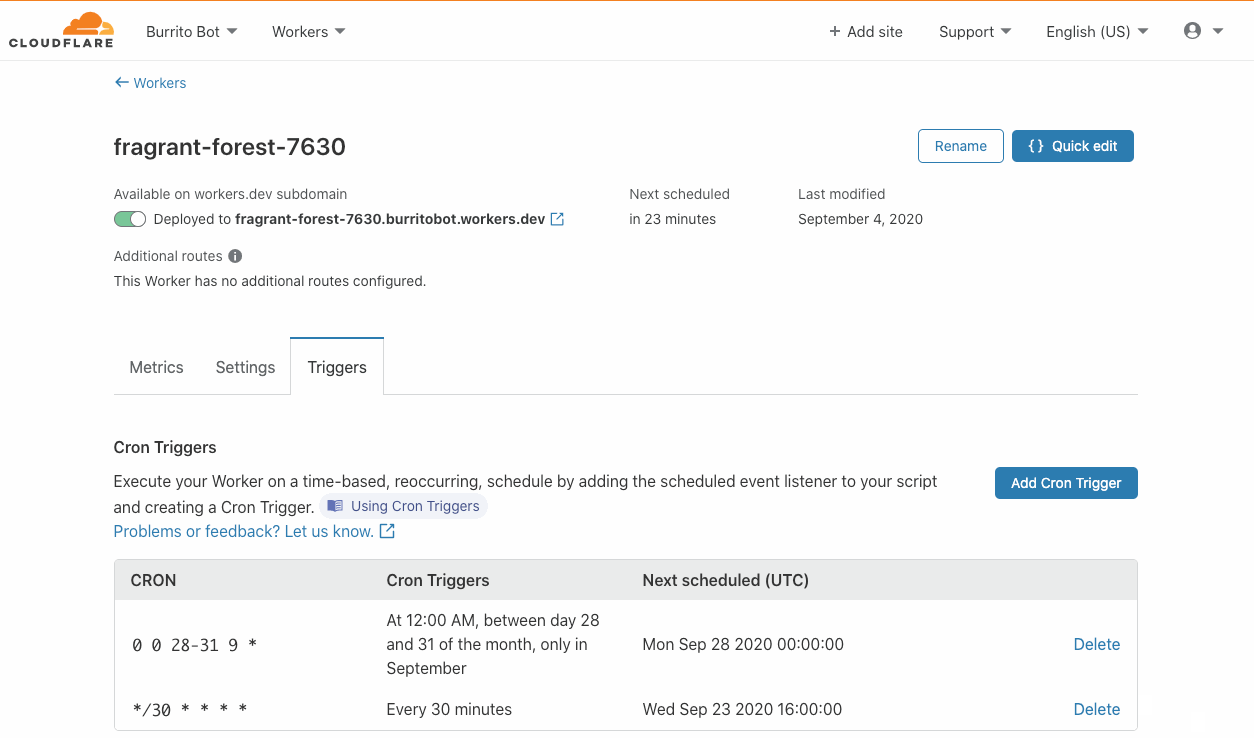
In case you’re not familiar with Unix systems, the cron pattern allows you to schedule jobs to run periodically at fixed intervals or at scheduled times. Cron Triggers in the context of Workers allow users to set time-based invocations Continue reading
Making Time for Cron Triggers: A Look Inside


Today, we are excited to launch Cron Triggers to the Cloudflare Workers serverless compute platform. We’ve heard the developer feedback, and we want to give our users the ability to run a given Worker on a scheduled basis. In case you’re not familiar with Unix systems, the cron pattern allows developers to schedule jobs to run at fixed intervals. This pattern is ideal for running any types of periodic jobs like maintenance or calling third party APIs to get up-to-date data. Cron Triggers has been a highly requested feature even inside Cloudflare and we hope that you will find this feature as useful as we have!
Where are Cron Triggers going to be run?
Cron Triggers are executed from the edge. At Cloudflare, we believe strongly in edge computing and wanted our new feature to get all of the performance and reliability benefits of running on our edge. Thus, we wrote a service in core that is responsible for distributing schedules to a new edge service through Quicksilver which will then trigger the Workers themselves.
What’s happening under the hood?
At a high level, schedules created through our API create records in our database with the information necessary to execute Continue reading
Security’s Role in Client to Cloud Networking
The Networking industry is undergoing a metamorphosis. Modern networking operations teams are challenged to cope with multiple operational models. As attackers become better and better at breaching our defenses, security analysts are increasingly at the heart of a security organization. The operators are responsible for detecting, investigating and remediating potential breaches before they progress into brand, customer, financial and IP damage. This confluence of DevOps, NetOps, SecOps, and CloudOps demands persistent operations control. How do you cope with decades of security, threat and cyber detection done in reactive silos? What happens as more workloads move to the cloud? At Arista, we value our ecosystem of security partners and networking must adapt to the new complex threats.
Security’s Role in Client to Cloud Networking
The Networking industry is undergoing a metamorphosis. Modern networking operations teams are challenged to cope with multiple operational models. As attackers become better and better at breaching our defenses, security analysts are increasingly at the heart of a security organization. The operators are responsible for detecting, investigating and remediating potential breaches before they progress into brand, customer, financial and IP damage. This confluence of DevOps, NetOps, SecOps, and CloudOps demands persistent operations control. How do you cope with decades of security, threat and cyber detection done in reactive silos? What happens as more workloads move to the cloud? At Arista, we value our ecosystem of security partners and networking must adapt to the new complex threats.
Workers Durable Objects Beta: A New Approach to Stateful Serverless
We launched Cloudflare Workers® in 2017 with a radical vision: code running at the network edge could not only improve performance, but also be easier to deploy and cheaper to run than code running in a single datacenter. That vision means Workers is about more than just edge compute -- we're rethinking how applications are built.
Using a "serverless" approach has allowed us to make deploys dead simple, and using isolate technology has allowed us to deliver serverless more cheaply and without the lengthy cold starts that hold back other providers. We added easy-to-use eventually-consistent edge storage to the platform with Workers KV.
But up until today, it hasn't been possible to manage state with strong consistency, or to coordinate in real time between multiple clients, entirely on the edge. Thus, these parts of your application still had to be hosted elsewhere.
Durable Objects provide a truly serverless approach to storage and state: consistent, low-latency, distributed, yet effortless to maintain and scale. They also provide an easy way to coordinate between clients, whether it be users in a particular chat room, editors of a particular document, or IoT devices in a particular smart home. Durable Objects are the missing piece Continue reading
Syncing RIPE, ARIN and APNIC objects with a custom Ansible module
Internet is split into five regional Internet registry: AFRINIC, ARIN, APNIC, LACNIC and RIPE. Each RIR maintains an Internet Routing Registry. An IRR allows one to publish information about the routing of Internet number resources.1 Operators use this to determine the owner of an IP address and to construct and maintain routing filters. To ensure your routes are widely accepted, it is important to keep the prefixes you announce up-to-date in an IRR.
There are two common tools to query this database: whois and
bgpq4. The first one allows you to do a query with the WHOIS
protocol:
$ whois -BrG 2a0a:e805:400::/40 […] inet6num: 2a0a:e805:400::/40 netname: FR-BLADE-CUSTOMERS-DE country: DE geoloc: 50.1109 8.6821 admin-c: BN2763-RIPE tech-c: BN2763-RIPE status: ASSIGNED mnt-by: fr-blade-1-mnt remarks: synced with cmdb created: 2020-05-19T08:04:58Z last-modified: 2020-05-19T08:04:58Z source: RIPE route6: 2a0a:e805:400::/40 descr: Blade IPv6 - AMS1 origin: AS64476 mnt-by: fr-blade-1-mnt remarks: synced with cmdb created: 2019-10-01T08:19:34Z last-modified: 2020-05-19T08:05:00Z source: RIPE
The second one allows you to build route filters using the information contained in the IRR database:
$ bgpq4 -6 -S RIPE -b AS64476 NN = [ 2a0a:e805::/40, 2a0a:e805:100::/40, 2a0a:e805:300::/40, 2a0a:e805:400::/40, 2a0a:e805:500::/40 ];
There is no module available on Ansible Galaxy Continue reading
Understanding Linux Networking
Got this interesting question from one of my readers
Based on my experience, the documentation regarding Linux networking is either elementary man pages for user-space utilities or very complicated Linux kernel source code. Does getting deep into Linux networking mean reading source code?
It all depends on how deep you plan to go:
Deploying whitebox switches. If you’re just starting you SHOULD buy a supported solution that includes hardware and a variant of Linux running on it. Your problem transformed into “configuring control-plane protocols on Linux”. Congratulations, you’ll be perfectly fine studying Cumulus Networks documentation. Apart from the secret-sauce-ASIC-blob they’re using open-source software, so whatever you learn there should be transferrable to any other Linux networking environment.
However, even though the documentation is pretty good, expect a few gotchas. As Dinesh Dutt told me:
- Unlike a traditional NOS, Linux is not a monolithic entity. There’s the kernel and there are software packages than run on top. To make installation and management easier, different folks put together Continue reading
The Secret to an Effective Multicloud Strategy Is…an Actual Strategy
The work isn’t done once a multicloud strategy is defined. It will need to keep evolving to meet, (and ideally, anticipate,) changing demands and needs.What Cyber Lessons Can the Military Teach the Private Sector?
Besides trying to avoid attack, the military focuses on resilience – the ability to limit the damage from attacks and to recover quickly afterward.A letter from Cloudflare’s founders (2020)

To our stakeholders:
Cloudflare launched on September 27, 2010 — 10 years ago today. Stopping to look back over the last 10 years is challenging in some ways because so much of who we are has changed radically. A decade ago when we launched we had a few thousand websites using us, our tiny office was above a nail salon in Palo Alto, our team could be counted on less than two hands, and our data center locations on one hand.

As the company grew, it would have been easy to stick with accelerating and protecting developers and small business websites and not see the broader picture. But, as this year has shown with crystal clarity, we all depend on the Internet for many aspects of our lives: for access to public information and services, to getting work done, for staying in touch with friends and loved ones, and, increasingly, for educating our children, ordering groceries, learning the latest dance moves, and so many other things. The Internet underpins much of what we do every day, and Cloudflare’s mission to help build a better Internet seems more Continue reading
Welcome to Birthday Week 2020

Each year we celebrate our launch on September 27, 2010 with a week of product announcements. We call this Birthday Week, but rather than receiving gifts, we give them away. This year is no different, except that it is… Cloudflare is 10 years old.
Before looking forward to the coming week, let’s take a look back at announcements from previous Birthday Weeks.
A year into Cloudflare’s life (in 2011) we launched automatic support for IPv6. This was the first of a long line of announcements that support our goal of making available to everyone the latest technologies. If you’ve been following Cloudflare’s growth you’ll know those include SPDY/HTTP/2, TLS 1.3, QUIC/HTTP/3, DoH and DoT, WebP, … At two years old we celebrated with a timeline of our first two years and the fact that we’d reached 500,000 domains using the service. A year later that number had tripled.

In 2014 we released Universal SSL and gave all our customers SSL certificates. In one go we massively increased the size of the encrypted web and made it free and simple to go from http:// to https://. Other HTTPS related features we’ve Continue reading
Duty Calls: Technologies that Didn’t: CLNS
Russ White published an interesting story explaining why we’re using IP and not CLNS to build today’s Internet.
Let’s start with a few minor details he missed that I feel obliged to point out (apologies to Russ for being too pedantic, but you know me…):
New ACI deployment? Watch out when connecting APICs to Leafs
It’s one of those articles aimed at the people with Cisco ACI experience who don’t bother with reading all the install and other guides again while going through n’th time of building and ACI fabric, like me. When it comes to Cisco ACI, you really should. There’s a small change with the physical build of the third generation of APIC server where 10G SFP interfaces from APIC towards the Leaf switches (used for fabric discovery and later for the in-band controller to fabric communication) where 4x10G card is built in the server and not like 2x10G on M2/L2 and other
The post New ACI deployment? Watch out when connecting APICs to Leafs appeared first on How Does Internet Work.

