Secondary DNS – Deep Dive
How Does Secondary DNS Work?
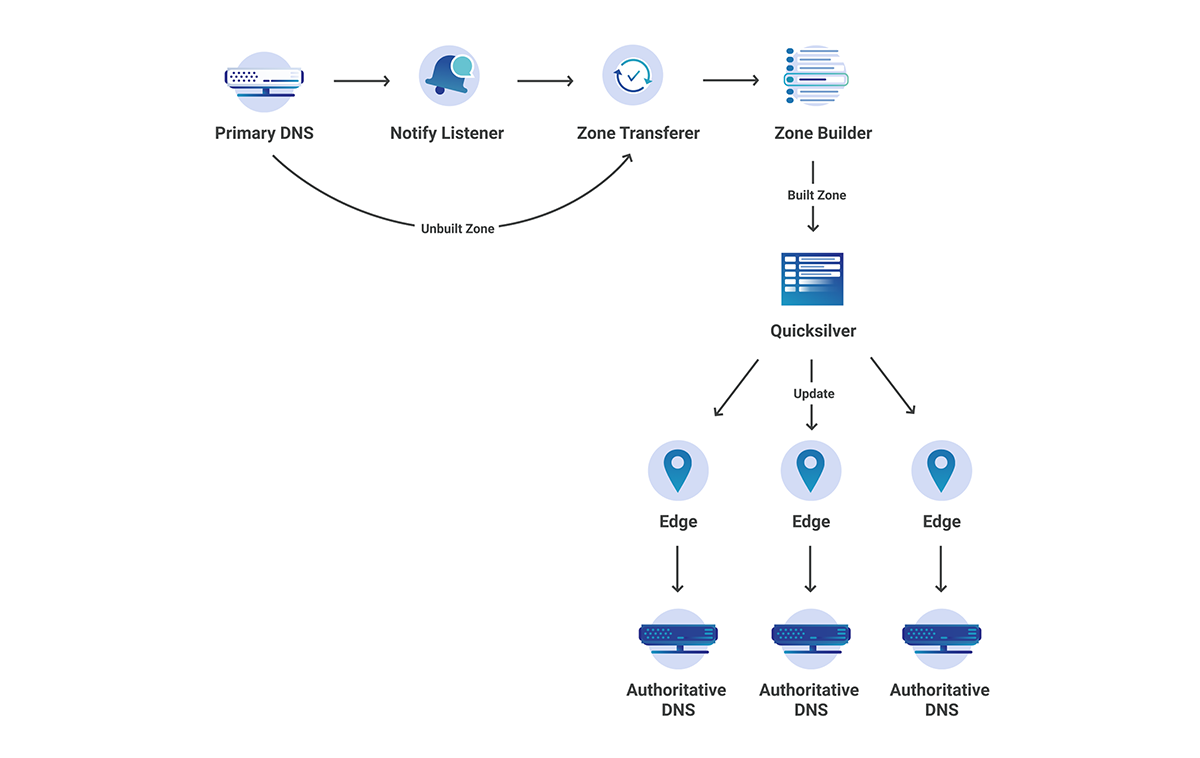
If you already understand how Secondary DNS works, please feel free to skip this section. It does not provide any Cloudflare-specific information.
Secondary DNS has many use cases across the Internet; however, traditionally, it was used as a synchronized backup for when the primary DNS server was unable to respond to queries. A more modern approach involves focusing on redundancy across many different nameservers, which in many cases broadcast the same anycasted IP address.
Secondary DNS involves the unidirectional transfer of DNS zones from the primary to the Secondary DNS server(s). One primary can have any number of Secondary DNS servers that it must communicate with in order to keep track of any zone updates. A zone update is considered a change in the contents of a zone, which ultimately leads to a Start of Authority (SOA) serial number increase. The zone’s SOA serial is one of the key elements of Secondary DNS; it is how primary and secondary servers synchronize zones. Below is an example of what an SOA record might look like during a dig query.
example.com 3600 IN SOA ashley.ns.cloudflare.com. dns.cloudflare.com.
2034097105 // Serial
10000 // Continue readingHow Docker Uses iptables to Implement Published Ports
In early September I explained the difference between exposed and published Docker container ports.
Now let’s peek behind the curtain and explore how Docker uses iptables to publish container ports, and why it runs a userland proxy process for every published port.
For even more details, explore the Docker Networking Deep Dive webinar.
Building a Multi-Cloud Network for less than $1 an Hour – Aviatrix Kickstart
This is the post I had been meaning to write for ages. How do you leverage Infrastructure as Code to build a multi-cloud network? It turns out you don’t have to write the code yourself. This is the beauty of Aviatrix Kickstart. For less than $1 an hour, I was able to build a multi-cloud … Continue reading Building a Multi-Cloud Network for less than $1 an Hour – Aviatrix KickstartWhy I’m running for the NANOG Board of Directors?
This year I decided to run for the NANOG Board of Directors and I wanted to elaborate what I would like to accomplish if elected. The election for NANOG Board of Directors will be held October 19 -21, 2020. Please mark your calendar and see my full profile at https://www.nanog.org/participate/elections-nominations/2020-board-candidates/board-candidate-tom-kacprzynski/
Being in the industry for the last sixteen years, I have been involved in operating a number of network types such as enterprise, datacenter, private backbone and CDN networks. Throughout these years I’ve gained the technical and organizational knowledge at established and lean startup businesses. My roles ranged from technical network engineering/architecture to leadership as department head of network engineering and software development teams along with network sourcing.
Since 2018, I was selected for the NANOG program committee and currently serving my second term. Additionally I serve as community organizer in creating a local Chicago/Midwest community of network operators. Since 2014 I have started the Chicago Network Operators Group, which is modeled after NANOG, as a vendor neutral organization. Producing nine successful conferences for the last six years has provided me with experience on working with vendors, navigating conference venue logistics, acquiring sponsors, curating content with the Continue reading
Tech Bytes: AppNeta And Performance Visibility Over The Last Mile (Sponsored)
Today’s Tech Bytes episode is sponsored by AppNeta, and we’re going to discuss how companies can get performance visibility for end users now that many people are working from home and connecting over last-mile networks that IT has little visibility into or control over. Our AppNeta guests are Seth Differ, Senior Manager, Solutions Consulting; and Alec Pinkham, Director of Product Marketing.Tech Bytes: AppNeta And Performance Visibility Over The Last Mile (Sponsored)
Today’s Tech Bytes episode is sponsored by AppNeta, and we’re going to discuss how companies can get performance visibility for end users now that many people are working from home and connecting over last-mile networks that IT has little visibility into or control over. Our AppNeta guests are Seth Differ, Senior Manager, Solutions Consulting; and Alec Pinkham, Director of Product Marketing.
The post Tech Bytes: AppNeta And Performance Visibility Over The Last Mile (Sponsored) appeared first on Packet Pushers.
Announcing eBPF Mode GA
A few days ago, our team released Calico v3.16. As part of that release, we have marked the eBPF dataplane as “GA”, signalling that it is now stable and ready for wider use by the community. In this blog post I want to take you through the process of moving from tech-preview to GA. If you’re not already familiar with eBPF and the benefits of the Calico eBPF dataplane, or if you want to see throughput and latency graphs compared to the standard Linux dataplane, I recommend that you read our introductory blog post. To recap, when compared with the standard Linux dataplane (based on iptables), the eBPF dataplane:
- Scales to higher throughput, using less CPU per GBit
- Natively supports Kubernetes services (without kube-proxy) in a way that:
- Reduces latency
- Preserves external client source IP addresses
- Supports DSR (Direct Server Return) for reduced latency (and CPU usage)
- Uses less CPU than kube-proxy to keep the dataplane in sync
For the tech preview release, our focus was on covering a broad set of features and proving out the performance of the new dataplane. However to meet the bar for GA, we had to:
- Address our list of known missing features
- Continue reading
Everyone Must Learn to Code
The word on the street is that everyone—especially network engineers—must learn to code. A conversation with a friend and an article passing through my RSS reader brought this to mind once again—so once more into the breach. Part of the problem here is that we seem to have a knack for asking the wrong question. When we look at network engineer skill sets, we often think about the ability to configure a protocol or set of features, and then the ability to quickly troubleshoot those protocols or features using a set of commands or techniques.
This is, in some sense, what various certifications have taught us—we have reached the expert level when we can configure a network quickly, or when we can prove we understand a product line. There is, by the way, a point of truth in this. If you claim your expertise is with a particular vendor’s gear, then it is true that you must be able to configure and troubleshoot on that vendor’s gear to be an expert. There is also a problem of how to test for networking skills without actually implementing something, and how to implement things without actually configuring them. This is a Continue reading
Network Break 301: Samsung Dials Up A 5G Contract; Broadcom Announces Fast, Power-Efficient New Jericho Chip
Network Break analyzes Samsung's multi-billion 5G contract from Verizon, a new Jericho ASIC from Broadcom, the insiders driving Zoombombing, the persistence of DDoS attacks, and more tech news.
The post Network Break 301: Samsung Dials Up A 5G Contract; Broadcom Announces Fast, Power-Efficient New Jericho Chip appeared first on Packet Pushers.
Network Break 301: Samsung Dials Up A 5G Contract; Broadcom Announces Fast, Power-Efficient New Jericho Chip
Network Break analyzes Samsung's multi-billion 5G contract from Verizon, a new Jericho ASIC from Broadcom, the insiders driving Zoombombing, the persistence of DDoS attacks, and more tech news.What Happens When The Whole World Goes Remote? Not To Worry, We Were Built For This


In March, governments all over the world issued stay-at-home orders, causing a mass migration to teleworking. Alongside many of our partners, Cloudflare launched free products and services supported by onboarding sessions to help our clients secure and accelerate their remote work environments. Over the past few months, a dedicated team of specialists met with hundreds of organizations - from tiny startups, to massive corporations - to help them extend better security and performance to a suddenly-remote workforce.
Most companies we heard from had a VPN in place, but it wasn’t set up to accommodate a full-on remote work environment. When employees began working from home, they found that the VPN was getting overloaded with requests, causing performance lags.
While many organizations had bought more VPN licenses to allow employees to connect to their tools, they found that just having licenses wasn’t enough: they needed to reduce the amount of traffic flowing through their VPN by taking select applications off of the private network.
We Were Built For This
My name is Dina and I am a Customer Success Manager (CSM) in our San Francisco office. I am responsible for ensuring the success of Cloudflare’s Enterprise customers and managing all of Continue reading
