Network Break 299: Cisco Acquires Audio Filter BabbleLabs; Apple Update Hits Facebook In The Ads
Today's Network Break shares listener follow-up, then dives into a new Cisco acquisition of an audio company; discusses how Facebook is responding to an Apple update that will hurt a part of Facebook's business; covers financial results from HPE, VMware, and Nutanix; and more tech news.Network Break 299: Cisco Acquires Audio Filter BabbleLabs; Apple Update Hits Facebook In The Ads
Today's Network Break shares listener follow-up, then dives into a new Cisco acquisition of an audio company; discusses how Facebook is responding to an Apple update that will hurt a part of Facebook's business; covers financial results from HPE, VMware, and Nutanix; and more tech news.
The post Network Break 299: Cisco Acquires Audio Filter BabbleLabs; Apple Update Hits Facebook In The Ads appeared first on Packet Pushers.
The Week in Internet News: U.S. Moves Closer to Banning Chinese Apps

Shopping for video: As U.S. President Donald Trump pushes for a ban of TikTok unless it’s sold by its Chinese owner, Walmart has joined Microsoft in a bid for the short-video sharing app, CNBC reports. TikTok is reportedly nearing an agreement to sell its U.S., Canadian, Australian, and New Zealand operations for $20 billion to $30 billion.
Boycotting an app ban: Another Chinese app that’s been targeted by Trump is WeChat, but the Chinese foreign ministry has suggested that consumers in the country could boycott Apple if the U.S. takes action against WeChat, The Straits Times says. Apple, as a large U.S. company, seems to be a convenient target for Chinese consumers.
An East/West split: As others have warned, an official with the U.K.’s National Cyber Security Centre has suggested that the Internet may split into a Western version and a Chinese-led Eastern version if Trump moves forward with a ban of Chinese apps, the Independent reports. A split could raise concerns about Western technology keeping up with the East, the official says.
Spy vs. hacker: New Zealand’s government has turned to its intelligence agency to thwart a sustained, multi-day cyberattack on the Continue reading
Century Link/Level 3 Outage is one of the biggest Internet Problem! 3.5% Drop in Global Internet Traffic
On August 30, 2020, Level 3/Century Link, AS 3356 had major Internet outage. In fact this outage effected massive amount of networks, including very well know ones such as Amazon, Microsoft, Twitter, Discord, Reddit etc.
3.5% Global Internet Traffic was dropped due to this outage and entire network converged after almost 7 hours. This is huge amount of time. When we usually discuss convergence, specifically fast convergence, ‘Seconds’ if not ‘ Milliseconds ‘ are the target values.
No one wants to have minutes level network convergence. But when there is an Outage like this, we categorize them as ‘ Catastrophic Failures’ and unfortunately network design usually doesn’t take this kind of failures into an account.
But could it be prevented?
In the first place, let’s understand that, this event, similar to many other catastrophic network events, started at a single location. (According to a CenturyLink status page, the issue originated from CenturyLink’s data center in Mississauga, a city near Ontario, Canada.)
But it spread over entire backbone of AS3356.
In fact, I remember on 2014, which we famously know as 512k incident happened because of this network (Level 3) as well and that event also caused Continue reading
Redundant Server Connectivity in Layer-3-Only Fabrics (Part 2)
In June 2020 I published the first part of Redundant Server Connectivity in Layer-3-Only Fabrics article describing the target design and application-layer requirements.
During the summer I added the details of multi-subnet server and client connectivity and a few conclusions.
Pushing to Multiple Git Remotes
I am working on a project where I need to push to both a github and bitbucket repository as the project is stored in both of these locations. I do not have the ability to sync between the two using either github or bitbuckets built in tools. This post goes through the process of ...Analysis of Today’s CenturyLink/Level(3) Outage
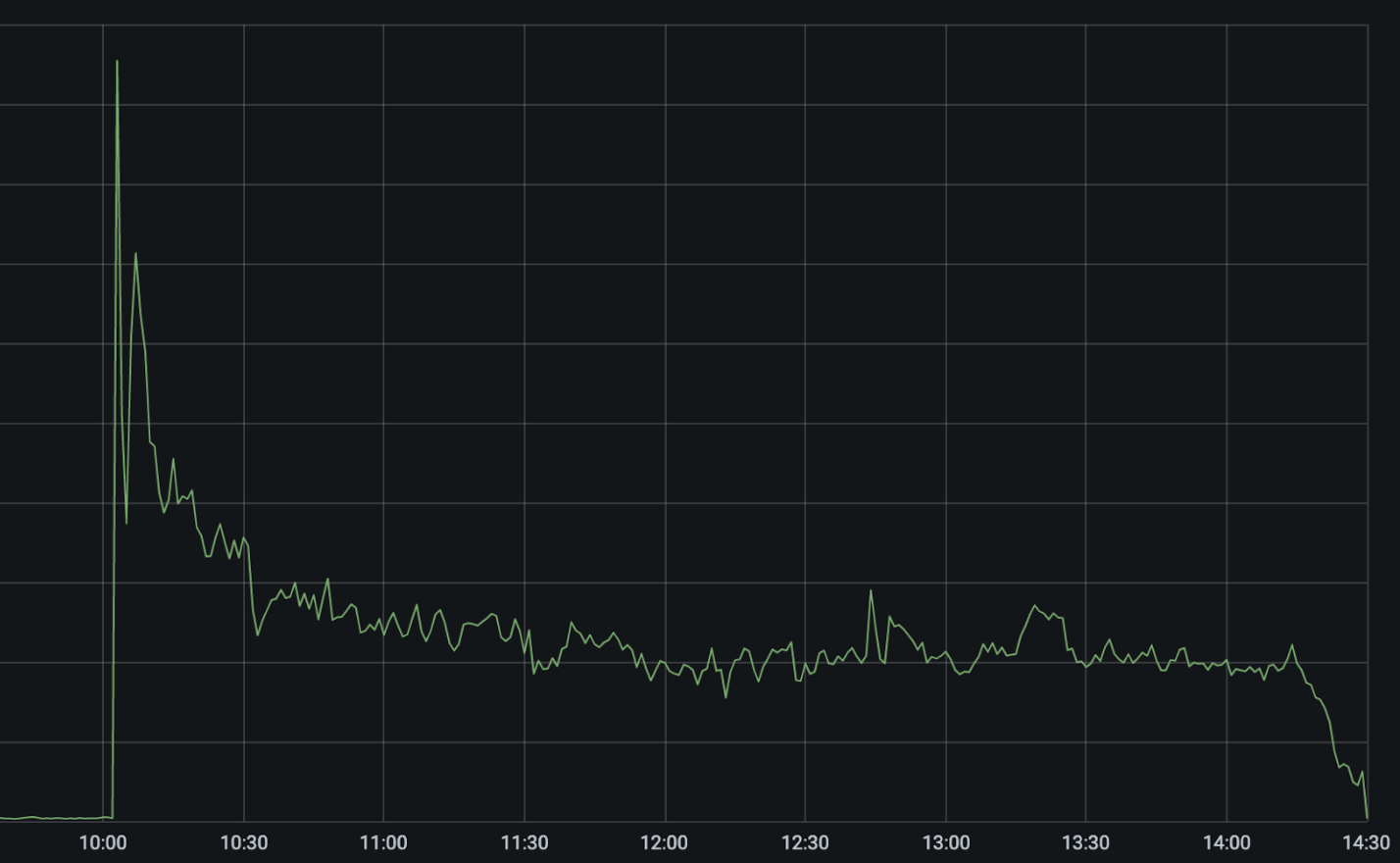
Today CenturyLink/Level(3), a major ISP and Internet bandwidth provider, experienced a significant outage that impacted some of Cloudflare’s customers as well as a significant number of other services and providers across the Internet. While we’re waiting for a post mortem from CenturyLink/Level(3), I wanted to write up the timeline of what we saw, how Cloudflare’s systems routed around the problem, why some of our customers were still impacted in spite of our mitigations, and what appears to be the likely root cause of the issue.
Increase In Errors
At 10:03 UTC our monitoring systems started to observe an increased number of errors reaching our customers’ origin servers. These show up as “522 Errors” and indicate that there is an issue connecting from Cloudflare’s network to wherever our customers’ applications are hosted.
Cloudflare is connected to CenturyLink/Level(3) among a large and diverse set of network providers. When we see an increase in errors from one network provider, our systems automatically attempt to reach customers’ applications across alternative providers. Given the number of providers we have access to, we are generally able to continue to route traffic even when one provider has an issue.
Why I Joined Aviatrix
Earlier this month I joined Aviatrix Systems as a Solutions Architect with a focus on growing the Aviatrix Certified Engineer (ACE) program. I had gone through a journey of 2 years of immersing myself in Public Cloud platforms from training sites, such as A Cloud Guru and Linux Academy. Here are some of my observations … Continue reading Why I Joined AviatrixIn South Asia an Online Training Course Equips Engineers for the Future

The Internet Society, in partnership with South Asia Network Operators Group (SANOG) recently concluded a five-week, hands-on training course for entry level network engineers and system administrators from South Asia. The online course Introduction to Network Operations, which took place from June 15 to July 19, prepared professionals to take advantage of the new opportunities the Internet is creating. The training provided practical learning about UNIX/Linux, networking, and the Domain Name System (DNS) to over 40 participants from Research Education Networks (RENs), government institutions, network operators, universities, and private institutions. SANOG subject matter experts Thilina Pathirana from Sri Lanka and Gazi Zehadul Kabir from Bangladesh moderated via Moodle, an e-learning platform.
Skills and Knowledge for Digital Transformation
The course aimed to prepare young engineers for the future. The technical skills and hands-on knowledge enable them to build expertise to advance professionally in their chosen field of network and system administration. The course also served as a common platform for South Asia community members to actively interact, exchange knowledge, and learn from one another.
For participants, the course was a great learning experience. “It was the best online course I had yet,” said Afaq Ahmed from Pakistan. For young engineers Shreekar Continue reading
Heavy Networking 537: Ansible Vs. Terraform For Network Automation
The networking community seems to have coalesced around Ansible for network device automation and Terraform for cloud. Why this divide? Are the two tools really that different? Today's Heavy Networking explores how and where you can use both these tools, with guests Ned Bellavance and Josh VanDeraa.
The post Heavy Networking 537: Ansible Vs. Terraform For Network Automation appeared first on Packet Pushers.
Heavy Networking 537: Ansible Vs. Terraform For Network Automation
The networking community seems to have coalesced around Ansible for network device automation and Terraform for cloud. Why this divide? Are the two tools really that different? Today's Heavy Networking explores how and where you can use both these tools, with guests Ned Bellavance and Josh VanDeraa.Iron Chef: Certification Edition

My friend Joshua Williams (@802DotMe) texted me today with a great quote that I wanted to share with you that made me think about certifications:
You’ve probably already thought through this extensively, and maybe even written about it, but after sitting through another 8 hour practical exam yesterday I’m more convinced than ever that expert level exams from technical companies are more analogous to a gimmicky Food Network TV show than real world application of technical acumen. They don’t care so much about my skill level as they do about what kind of meal I can prepare in 30 minutes using Tialapia, grapes, and Dr. Pepper syrup with my salt shaker taken away halfway through.
I laughed because it’s true. And then I thought about it more and realized he’s way more than right. We know for a fact that companies love to increase the level of challenge in their exams from novice to expert. It’s a way to weed out the people that aren’t committed to learning about something. However, as the questions and tasks get harder it becomes much more difficult to get a good sense of how candidates are going to perform.
Boiling Water Isn’t Continue reading
Asynchronous HTMLRewriter for Cloudflare Workers
Last year, we launched HTMLRewriter for Cloudflare Workers, which enables developers to make streaming changes to HTML on the edge. Unlike a traditional DOM parser that loads the entire HTML document into memory, we developed a streaming parser written in Rust. Today, we’re announcing support for asynchronous handlers in HTMLRewriter. Now you can perform asynchronous tasks based on the content of the HTML document: from prefetching fonts and image assets to fetching user-specific content from a CMS.
How can I use HTMLRewriter?
We designed HTMLRewriter to have a jQuery-like experience. First, you define a handler, then you assign it to a CSS selector; Workers does the rest for you. You can look at our new and improved documentation to see our supported list of selectors, which now include nth-child selectors. The example below changes the alternative text for every second image in a document.
async function editHtml(request) {
return new HTMLRewriter()
.on("img:nth-child(2)", new ElementHandler())
.transform(await fetch(request))
}
class ElementHandler {
element(e) {
e.setAttribute("alt", "A very interesting image")
}
}
Since these changes are applied using streams, we maintain a low TTFB (time to first byte) and users never know the HTML was transformed. If you’re interested in how we’re Continue reading
Video: Networks Are Not Homogenous
The last Fallacy of Distributed Computing I addressed in the introductory part of How Networks Really Work webinar was The Network Is Homogenous. No, it’s not and it never was… for more details watch this video.
Navigating the open network operating systems space
Subscribe to Kernel of Truth on iTunes, Google Play, Spotify, Cast Box and Sticher!
Click here for our previous episode.
Some of your favorites are back together on this episode of the Kernel of Truth podcast— specifically Roopa Prabhu, Brian O’Sullivan and Pete Lumbis. Things have changed a little around here since the last time the three of them were chatting together on the podcast but one thing hasn’t, how much they love to talk all things open networking. In this episode the group talks about how to navigate the open networking operating systems space. From figuring out how to choose an open network operating system, to understanding what works best for deployments, and even what resources and communities are out there for you to tap into. We have it all here for you to help you get started. All you have to do is sit back and enjoy the episode and don’t forget to also check out the links below with resources referenced in the podcast.
Guest Bios
Roopa Prabhu: Roopa is a Linux Architect at NVIDIA, formally Cumulus Networks. She and her team work on all things kernel networking and Linux system infrastructure areas. Her primary Continue reading
