A Narrow Window of Opportunity for Rural Connectivity in the U.S.

As COVID-19 continues to shine a spotlight on the vital role the Internet plays, a short window of opportunity has opened for the Federal Communications Commission (FCC) to do their part in connecting rural Indigenous communities in the United States.
The Tribal Priority Window is currently open for federally-recognized tribes, Alaska Native Villages, and Hawaiian Homelands to apply for Educational Broadband Service (EBS) spectrum, but it closes on August 3rd. Access to the EBS spectrum would enable Indigenous communities to build their own Internet networks.
The FCC set this deadline before the pandemic, but Tribal governments are now overwhelmed by handling the Coronavirus with limited resources. The FCC must give them more time to apply to the priority window. COVID-19 will not simply disappear from tribal lands in time for tribal governments to pull together applications.
The need for reliable, affordable Internet access is more pressing than ever.
Need proof? One only has to look at the fact that Indigenous communities in the US face the lowest rate of broadband access and the highest per capita rate of COVID-19 infections. The need for access to accurate information and telehealth is at an all-time high. Tribal communities are at serious risk Continue reading
IPv6 Buzz 056: What’s The Deal With NAT64?
In this week's IPv6 Buzz episode, Ed and Tom speak with Sander Steffann to get his expert take on NAT64, an important IPv6 transition technology. We also delve into his critical IPv6 efforts with the European Regional Internet Registry (RIPE).
The post IPv6 Buzz 056: What’s The Deal With NAT64? appeared first on Packet Pushers.
IPv6 Buzz 056: What’s The Deal With NAT64?
In this week's IPv6 Buzz episode, Ed and Tom speak with Sander Steffann to get his expert take on NAT64, an important IPv6 transition technology. We also delve into his critical IPv6 efforts with the European Regional Internet Registry (RIPE).Dictionary: coulrophobia

The feeling you get working with ITIL consultants
The post Dictionary: coulrophobia appeared first on EtherealMind.
Internationalizing the Cloudflare Dashboard
Cloudflare’s dashboard now supports four new languages (and multiple locales): Spanish (with country-specific locales: Chile, Ecuador, Mexico, Peru, and Spain), Brazilian Portuguese, Korean, and Traditional Chinese. Our customers are global and diverse, so in helping build a better Internet for everyone, it is imperative that we bring our products and services to customers in their native language.
Since last year Cloudflare has been hard at work internationalizing our dashboard. At the end of 2019, we launched our first language other than US English: German. At the end of March 2020, we released three additional languages: French, Japanese, and Simplified Chinese. If you want to start using the dashboard in any of these languages, you can change your language preference in the top right of the Cloudflare dashboard. The preference selected will be saved and used across all sessions.
In this blog post, I want to help those unfamiliar with internationalization and localization to better understand how it works. I also would like to tell the story of how we made internationalizing and localizing our application a standard and repeatable process along with sharing a few tips that may help you as you do the same.
Beginning the journey
The first Continue reading
Remove Whitespace from Rendered Templates in 11ty
The default behavour of 11ty is to just remove the template tags from rendered templates and leave behind white space in its place. This is probably mostly fine but for me it was causing large amounts of white space in my rendered templates and needless changes in git diffs. 11ty uses...NVM Install and Usage Ubuntu 2004
How to install and use Node version manager on Ubuntu 2004.Dictionary: internet

Its not capital I anymore
The post Dictionary: internet appeared first on EtherealMind.
The Hedge Podcast 45: When to Quit Certifications

Certifications are a perennial topic (like weeds, perhaps) in the world of network engineering. While we often ask whether you should get a certification or a degree, or whether you should get a certification at all, we don’t often ask—now that you have the certification, how long should you keep it? Do you keep recertifying “forever,” or is there a limit? Join us as Mike Bolitho, Eyvonne Sharp, Tom Ammon, and Russ White discuss when you should give up on that certification.
Meet the MANRS Ambassadors

We’ve appointed four MANRS ambassadors in the areas of training, research, and policy. We’re excited to welcome Anirban Datta, Flavio Luciani, Boris Mimeur, and Sanjeev Gupta to the program, and can’t wait to benefit from their input and expertise.
Ambassadors are representatives from current MANRS participant organizations who provide mentorship, guidance, and feedback to others in the routing security community. With their wealth of experience and knowledge – and their passion and commitment – they help make the global routing infrastructure more robust and secure.
The MANRS Ambassadors Selection Committee, consisting of six representatives from the MANRS Advisory Group, assessed the applications and appointed four exceptional individuals.
They’ll receive a monthly stipend of US$1,500 for up to six months and together they’ll train people on good routing practices, analyze routing incidents, research ways to secure routing, and survey the global policy landscape. Ambassadors will also provide mentorship to the MANRS Fellows in their respective categories to help the Fellows to fulfill their obligations.
Four Amazing Ambassadors

Anirban Datta, training ambassador
Anirban works for Fiber@Home Global Ltd in Dhaka, Bangladesh. His role is to establish international links and points of presence in different parts of the world. He’s also involved with Continue reading
Day Two Cloud 058: Using Curiosity And Mistakes To Advance Your Career
Today's Day Two Cloud gets into career advancement with guest Sam Erskine. Curiosity is key, and the mistakes you make can actually lead to new knowledge and opportunities. Sam is head of cloud engagement for a large consulting firm and has worked in a variety of IT roles. He's distilled his career experiences into a helpful five-step process, which we explore.Day Two Cloud 058: Using Curiosity And Mistakes To Advance Your Career
Today's Day Two Cloud gets into career advancement with guest Sam Erskine. Curiosity is key, and the mistakes you make can actually lead to new knowledge and opportunities. Sam is head of cloud engagement for a large consulting firm and has worked in a variety of IT roles. He's distilled his career experiences into a helpful five-step process, which we explore.
The post Day Two Cloud 058: Using Curiosity And Mistakes To Advance Your Career appeared first on Packet Pushers.
SD-WAN’s Musical Chairs, Tools, and the State of Support
A gaggle of networking geeks sits around the virtual roundtable and has a conversation on current events. Topics include the ever moving SD-WAN market landscape, our favorite (and least favorite) tools that have emerged since plunging into pandemic mode, and an honest discussion on whether or not support from our major vendors has been deteriorating or not.
 |
A considerable thank you to Unimus for sponsoring today’s episode. Unimus is a fast to deploy and easy to use Network Automation and Configuration Management solution. You can learn more about how you can start automating your network in under 15 minutes at unimus.net/nc. |
Outro Music:
Danger Storm Kevin MacLeod (incompetech.com)
Licensed under Creative Commons: By Attribution 3.0 License
http://creativecommons.org/licenses/by/3.0/
The post SD-WAN’s Musical Chairs, Tools, and the State of Support appeared first on Network Collective.
Introducing IP Lists
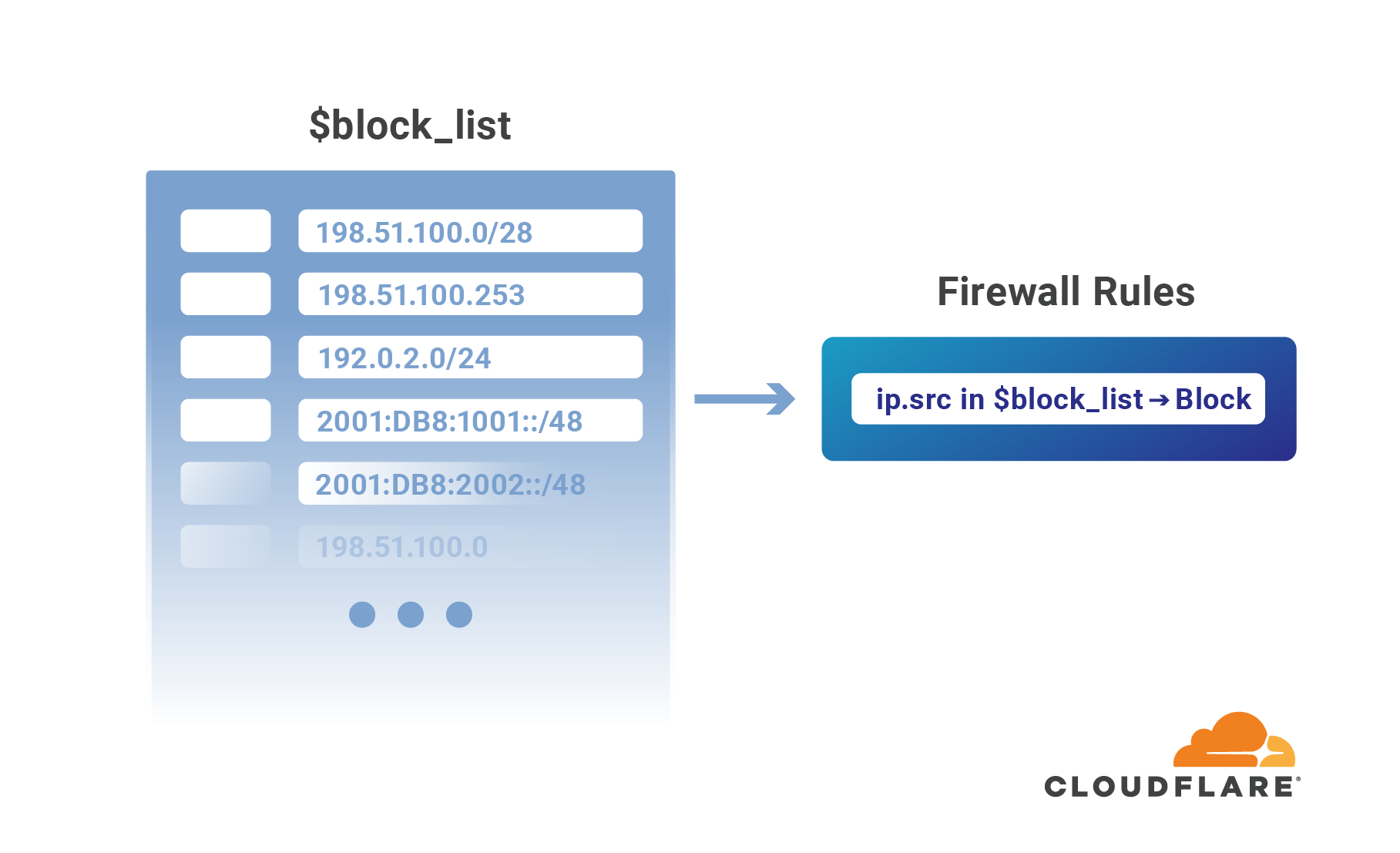
Authentication on the web has been steadily moving to the application layer using services such as Cloudflare Access to establish and enforce software-controlled, zero trust perimeters. However, there are still several important use cases for restricting access at the network-level by source IP address, autonomous system number (ASN), or country. For example, some businesses are prohibited from doing business with customers in certain countries, while others maintain a blocklist of problematic IPs that have previously attacked them.
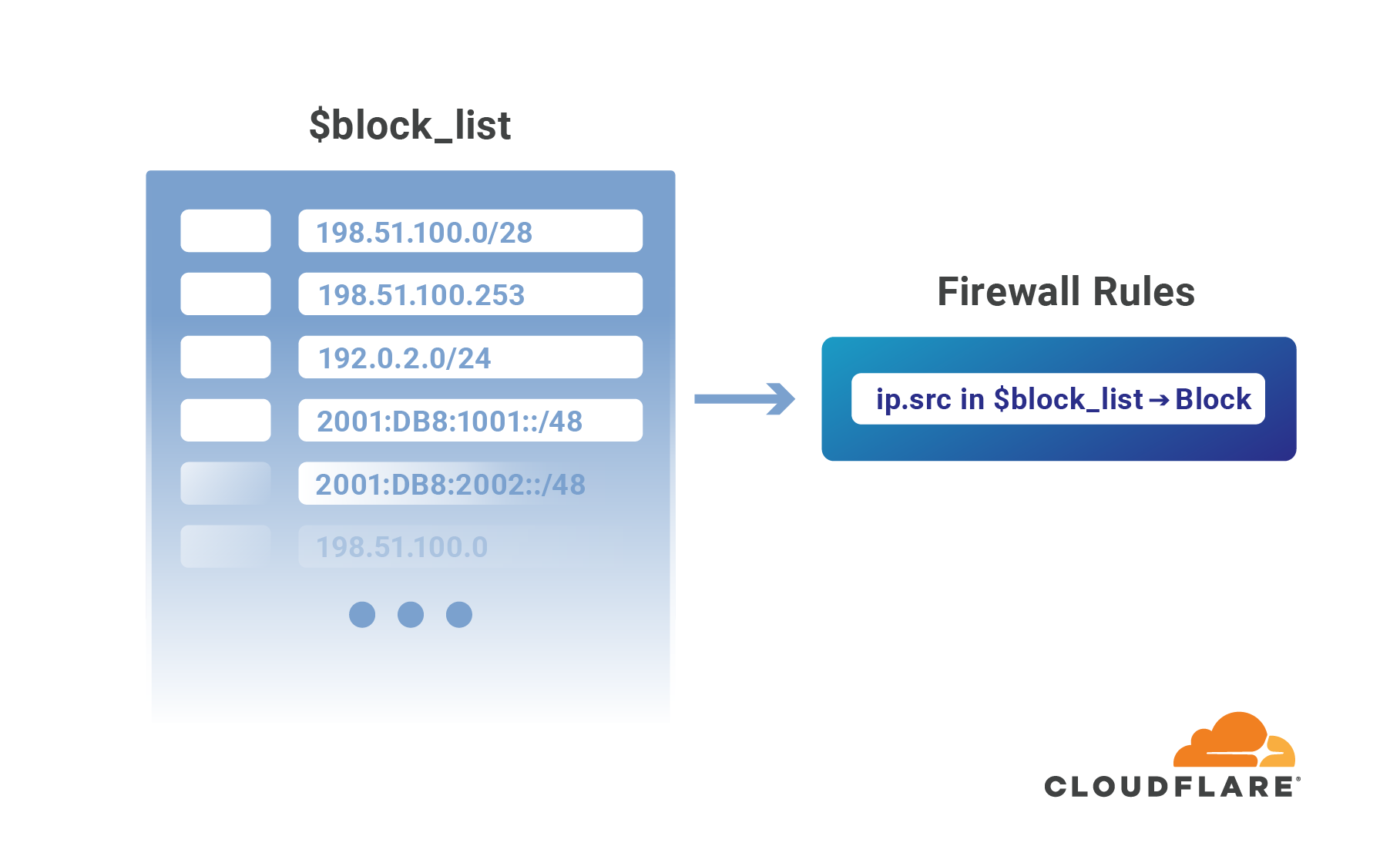
Enforcing these network restrictions at centralized chokepoints using appliances—hardware or virtualized—adds unacceptable latency and complexity, but doing so performantly for individual IPs at the Cloudflare edge is easy. Today we’re making it just as easy to manage tens of thousands of IPs across all of your zones by grouping them in data structures known as IP Lists. Lists can be stored with metadata at the Cloudflare edge, replicated within seconds to our data centers in 200+ cities, and used as part of our powerful, expressive Firewall Rules engine to take action on incoming requests.
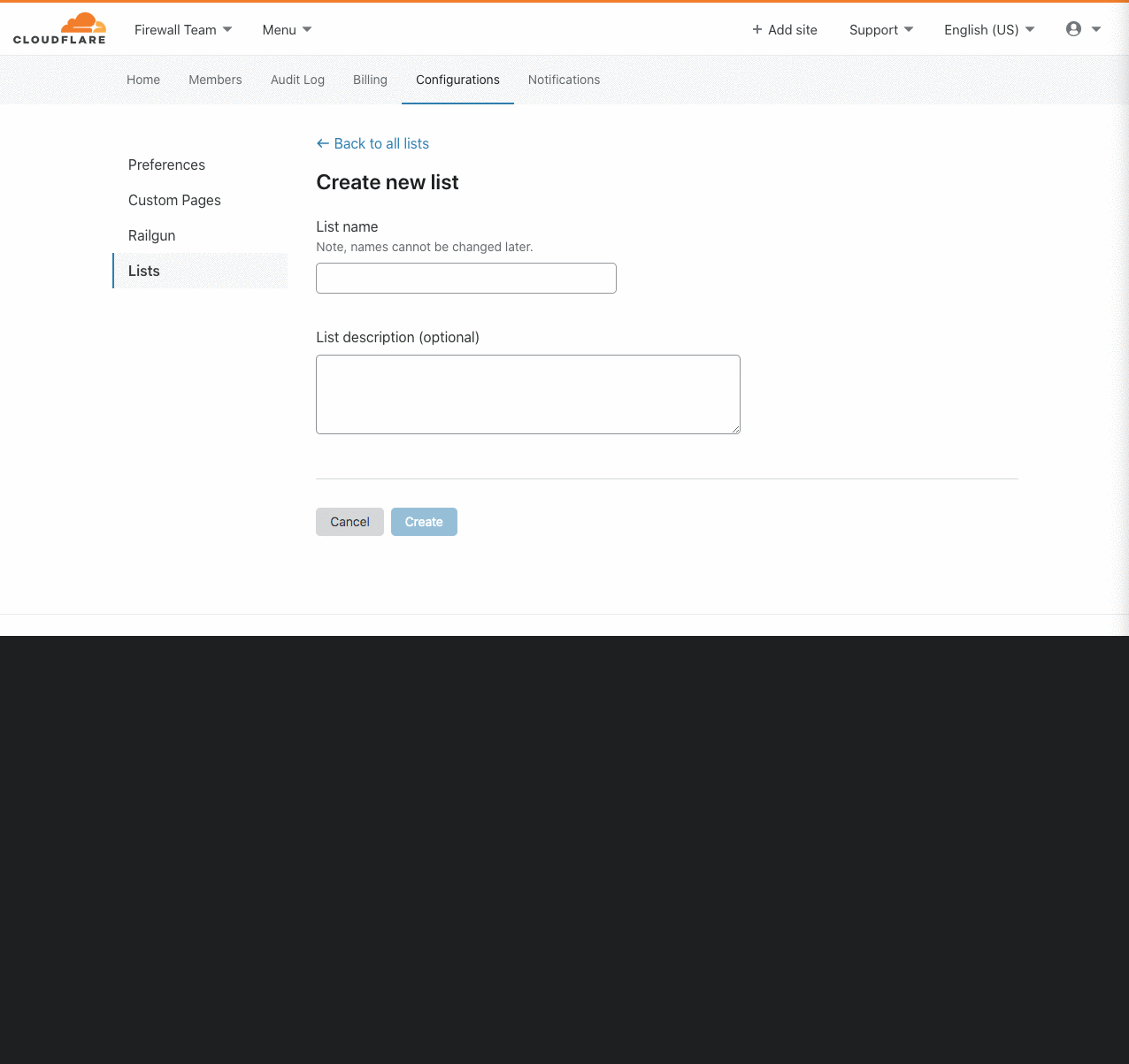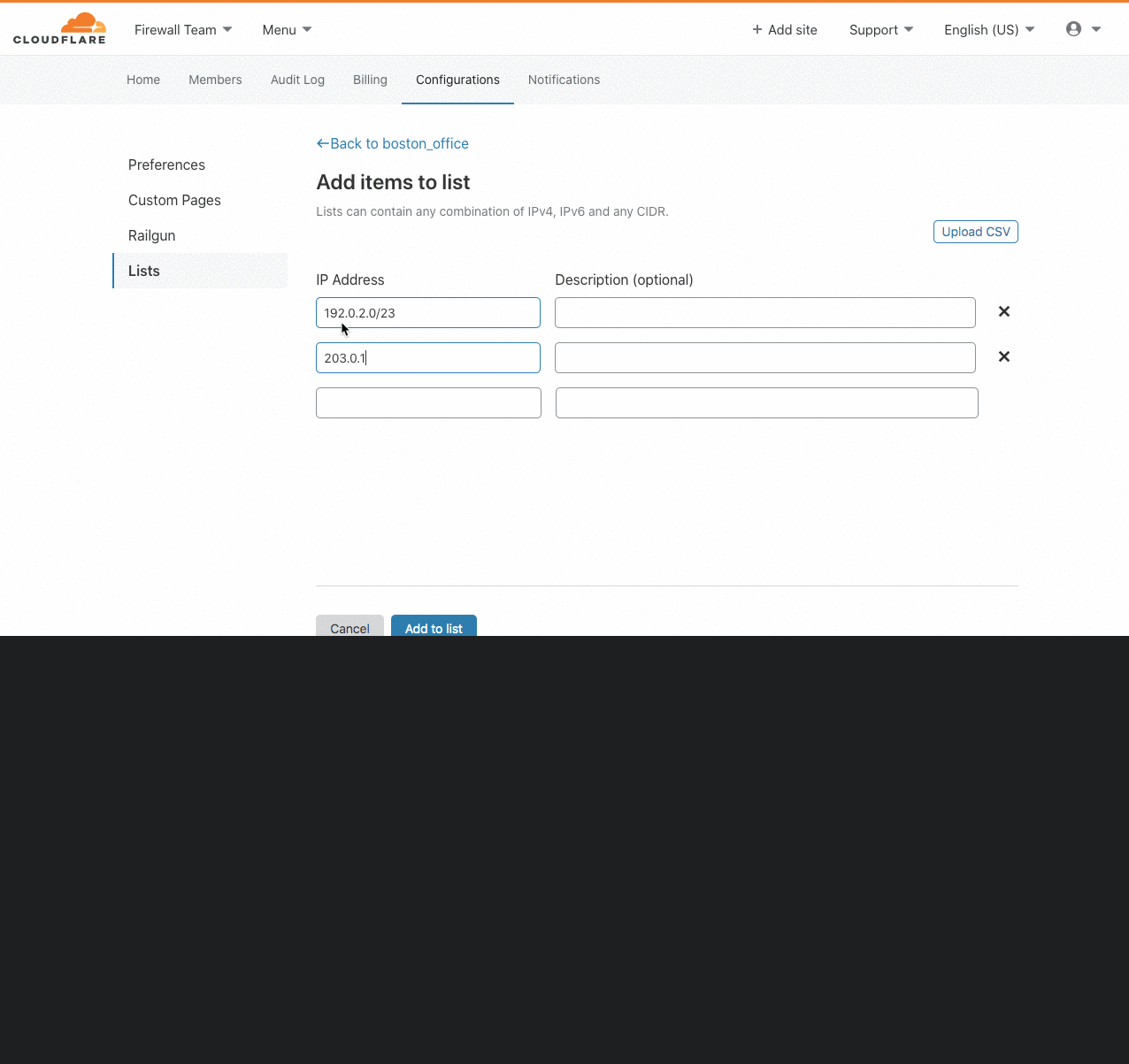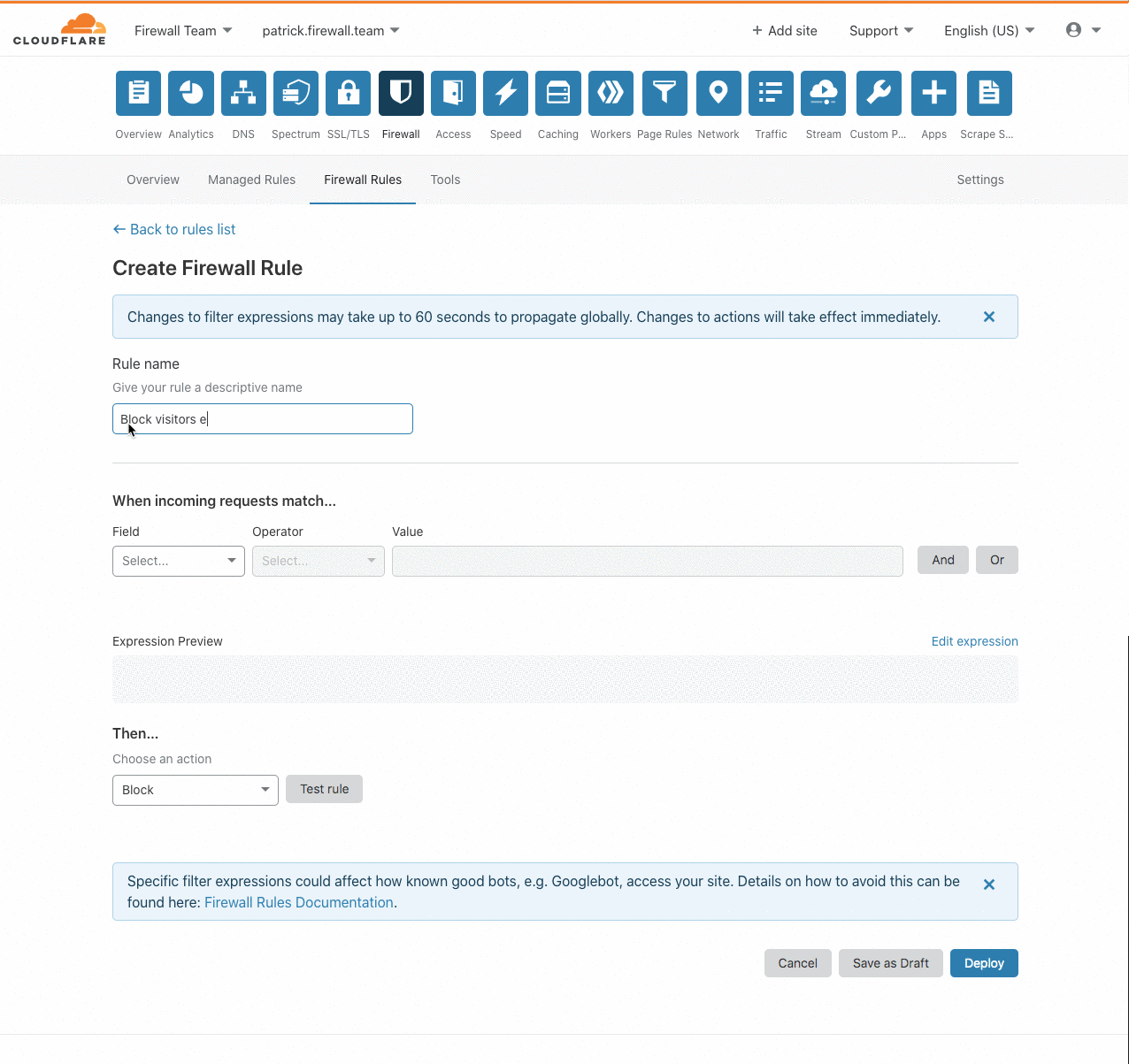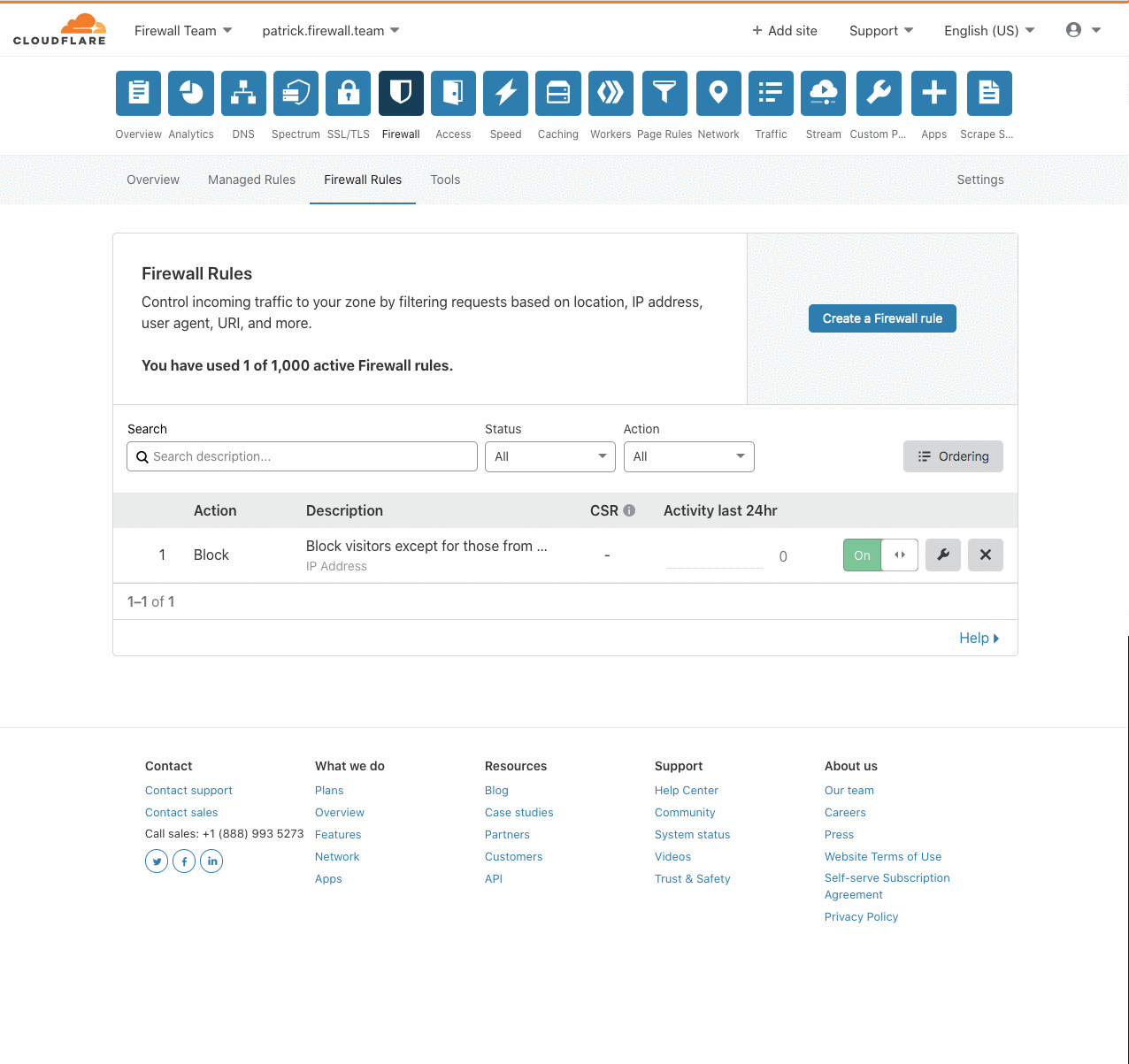
Previously, these sort of network-based security controls have been configured using IP Access or Zone Lockdown rules. Both tools have a number of Continue reading
Worth Reading: entr: Rerun Your Build when Files Change
Julia Evans recently described another awesome Linux tool: entr allows you to run a bash command every time a watched file changes (and it works on Linux and OSX).
I wish I found it years ago…
NVM Install and Usage Ubuntu 2004
Node version manager (NVM) allows you to run different version of Node on your system which is very helpful for testing and ensuring that the Node version you test on is the same as the Node version you run in production. This is just a quick post on how to install and use (NVM) on Ubuntu...Rust Traits: Defining Behavior
Before jumping into any programming language, you often hear about its “heavy hitters” - the features that usually make the highlight reel when someone “in the know” is trying to summarize the strong points of the language. In 2015, as I was learning Go, I would often hear things like concurrency support, channels, concurrency support, and Interfaces. Also concurrency support. With Rust, thus far the highlights have included things like strong support for generics, lower-level control, and an emphasis on memory safety manifested in the unavoidable ownership model.CEX (Code EXpress) 12. Using Python modules.
Hello my friend,
In the previous blogpost we have shared how some thoughts how you can parse the CSV file and how in general to work with external files. But the beauty of the programming languages including Python, is that there are always more than one way of doing things. And with learning it more, you are opening new ways.
Automate all the things
Raise of the 5G in the Service Provider world, micro services in Data Centres and mobility in Enterprise networks significantly changes the expectations about the way the network operate and the pace the changes are implemented. It is impossible to meet those expectation without automation.
At our network automation training, either self-paced or instructor lead, you will learn the leading technologies, protocols, and tools used to manage the networks in the busiest networks worldwide, such as Google data centres. However, once you master all the skills, you will be able to automate the network of any scale. You will see the opportunities and you will exploit them.
Secret words: NETCONF, REST API, gRPC, JSON , XML, Protocol buffers, SSH, OpenConfig, Python, Ansible, Linux, Docker; and many other wonderful tools and techniques are waiting for you Continue reading