Worth Reading: Written communication is remote work super power
Snir David wrote a great article explaining why you should focus on documenting stuff you do instead of solving other people’s challenges (or putting out fires) on Slack/Zoom/whatever. Enjoy ;)
U.S. Tribes Have until August 3rd to Apply to Help Bring Internet to Their Communities

See how the Makah Tribe launched an emergency network on EBS spectrum during COVID-19
The Makah Tribe has lived around Neah Bay at the northwest tip of what is now Washington State since time immemorial. It is a breathtaking landscape of dense rainforest and steep hills, far removed from any major urban center.
But for all its beauty, the hills, forests, and remoteness have made it difficult for the community to access quality high-speed Internet – and even cell and radio service.
In some areas, cell service was so poor that only certain spots worked: one community member had to go outside and stand beside a rhododendron bush to make a call or send a text. While Facebook is the main way people stay connected, many couldn’t access it. The local clinic struggled to use electronic records – it sometimes took upwards of 40 minutes just to get into the system. Even emergency responders, such as police and the fire department, couldn’t rely on the dispatch system that required Internet connectivity to operate.
And then the coronavirus began to sweep the world. The Makah closed the reservation to outsiders to protect the community. And its connectivity challenges became even more problematic. Continue reading
Virtual Open Office Hours – July 28 and 30

Come along, discuss and share.
The post Virtual Open Office Hours – July 28 and 30 appeared first on EtherealMind.
Jinja2 Tutorial – Part 4 – Template filters
This is part 4 of Jinja2 tutorial where we continue looking at the language features, specifically we'll be discussing template filters. We'll see what filters are and how we can use them in our templates. I'll also show you how you can write your own custom filters.
Jinja2 Tutorial series
- Jinja2 Tutorial - Part 1 - Introduction and variable substitution
- Jinja2 Tutorial - Part 2 - Loops and conditionals
- Jinja2 Tutorial - Part 3 - Whitespace control
- Jinja2 Tutorial - Part 4 - Template filters
- Jinja2 Tutorial - Part 5 - Macros
- Jinja2 Tutorial - Part 6 - Include and Import
- J2Live - Online Jinja2 Parser
Contents
- Overview of Jinja2 filters
- Multiple arguments
- Chaining filters
- Additional filters and custom filters
- Why use filters?
- When not to use filters?
- Writing your own filters
- Fixing "too clever" solution with Ansible custom filter
- Custom filters in Ansible
- Jinja2 Filters - Usage examples
- Conclusion
- References
- GitHub repository with resources for this post
Overview of Jinja2 filters
Let's jump straight in. Jinja2 filter is something we use to transform data held in variables. We apply filters by placing pipe symbol | Continue reading
Dictionary: Meat Crayon

Define 'Meat Crayon' - its PRINCE2 related.
The post Dictionary: Meat Crayon appeared first on EtherealMind.
Tradeoffs Come in Threes
This, in a nutshell, is what is often wrong with our design thinking in the networking world today. We want things to be efficient, wringing the last little dollar, and the last little bit of bandwidth, out of everything.
This is also, however, a perfect example of the problem of triads and tradeoffs. In the case of the street sweeper, we might thing, “well, we could replace those folks sitting around smoking a cigarette and cracking jokes with a robot, making things Continue reading
The Week in Internet News: Hackers Target COVID-19 Research

Hacking the research: Intelligence agencies from the U.S., U.K., and Canada have accused a Russian hacking group of targeting organizations conducting COVID-19 research, the Washington Post reports. The so-called Cozy Bear hacking group is trying to steal vaccine research specifically, the intelligence groups say.
Hacking the tweets: Meanwhile, 130 of Twitter’s most high-profile accounts were targeted by hackers recently, with a few of them compromised, in an apparent bitcoin scam, the New York Post writes. Among the accounts targeted were Kanye West, Elon Musk, Barack Obama, and Warren Buffett. The hackers reportedly paid a Twitter employee to help them with the attack.
No data collection, please: The government of China is cracking down on apps that collect what it considers too much personal data, the South China Morning Post says. The government has ordered several tech companies, including Alibaba Group and Tencent, to remove non-compliant apps as soon as possible.
Broadband is fundamental: Microsoft CEO Satya Nadella has called broadband a “fundamental right” in an interview with CNN. Many rural areas in the U.S. still lack broadband, and that needs to change, he said. “If you think about the rural community today, they are going to Continue reading
Network Break 293: HPE Acquires Silver Peak; Dell Teases VMware Sale
Today's Network Break scrutinizes HPE's big payout for Silver Peak and Dell's plans for a possible sale of VMware. We also discuss new capabilities in VMware Cloud on AWS, a new synthetic monitoring service from Kentik, how NIST thinks "giga" is pronounced, and more.
The post Network Break 293: HPE Acquires Silver Peak; Dell Teases VMware Sale appeared first on Packet Pushers.
Network Break 293: HPE Acquires Silver Peak; Dell Teases VMware Sale
Today's Network Break scrutinizes HPE's big payout for Silver Peak and Dell's plans for a possible sale of VMware. We also discuss new capabilities in VMware Cloud on AWS, a new synthetic monitoring service from Kentik, how NIST thinks "giga" is pronounced, and more.Phased Approach to Securing a Data Center
In the fight against relentless cyberattacks, organizations have long relied on traditional perimeter firewalls to protect sensitive workloads and information in the data center. But today, in the era of distributed applications and hybrid cloud environments, we know that perimeter defenses are not enough to stop cybercriminals.
To improve security postures inside corporate networks — which means protecting against both bad actors who penetrate perimeter defenses and malicious insiders — organizations must monitor, detect, and block hostile east-west (internal) traffic using internal firewalls.
To date, network and security professionals have generally viewed securing east-west traffic as too complex, expensive, and time-consuming for their brownfield, and even greenfield, data centers. At VMware, we agree with that perception: it’s certainly true for organizations trying to detect and prevent the lateral movement of attackers by employing traditional, appliance-based perimeter firewalls as internal firewalls.
There’s a Better Way to Secure the Data Center
Instead of awkwardly forcing appliance-based firewalls to serve as internal firewalls, organizations should employ a distributed, scale-out internal firewall specifically Continue reading
Why I’m Helping Cloudflare Grow in Japan

If you'd like to read this post in Japanese click here.
I’m excited to say that I’ve recently joined the Cloudflare team as Head of Japan. Cloudflare has had a presence in Japan for a while now, not only with its network spanning the country, but also with many Japanese customers and partners which I’m now looking forward to growing with. In this new role, I’m focused on expanding our capabilities in the Japanese market, building upon our current efforts, and helping more companies in the region address and put an end to the technical pain points they are facing. This is an exciting time for me and an important time for the company. Today, I’m particularly eager to share that we are opening Cloudflare’s first Japan office, in Tokyo! I can’t wait to grow the Cloudflare business and team here.

Why Cloudflare?
The web was built 25 years ago. This invention changed the way people connected—to anyone and anywhere—and the way we work, play, live, learn, and on. We have seen this become more and more complex. With complexities come difficulties, such as ensuring security, performance, and reliability while online. Cloudflare is helping to solve these challenges that businesses Continue reading
EIGRP Behavior with IP Unnumbered
Carl Zellers asked an excellent question on how EIGRP works when run over FlexVPN with IP unnumbered, considering that routers will not be on a common subnet. I thought this was a great question so I took some help from my great friend, the EIGRP guru, Peter Palúch.
First, let’s examine behavior when EIGRP is run on numbered interface. I have built a very simple lab consisting of three routers, R1, R2, and R3, where R1 and R3 are separated by R2. To demonstrate that EIGRP checks that incoming hellos are received on a common subnet, the following simple configurations were applied to R1 and R2:
R1:
interface GigabitEthernet1 ip address 10.0.0.1 255.255.255.0 ! router eigrp LAB ! address-family ipv4 unicast autonomous-system 64512 ! topology base exit-af-topology network 10.0.0.0 0.0.0.255 exit-address-family
R2:
interface GigabitEthernet1 ip address 10.0.1.1 255.255.255.0 ! router eigrp LAB ! address-family ipv4 unicast autonomous-system 64512 ! topology base exit-af-topology network 10.0.1.0 0.0.0.255 exit-address-family
This results in the well familiar messages on the console:
*Jul 15 08:53:20.966: %DUAL-6-NBRINFO: EIGRP-IPv4 64512: Neighbor 10.0.0.1 (GigabitEthernet1) is blocked: not Continue reading
Cloudflare outage on July 17, 2020
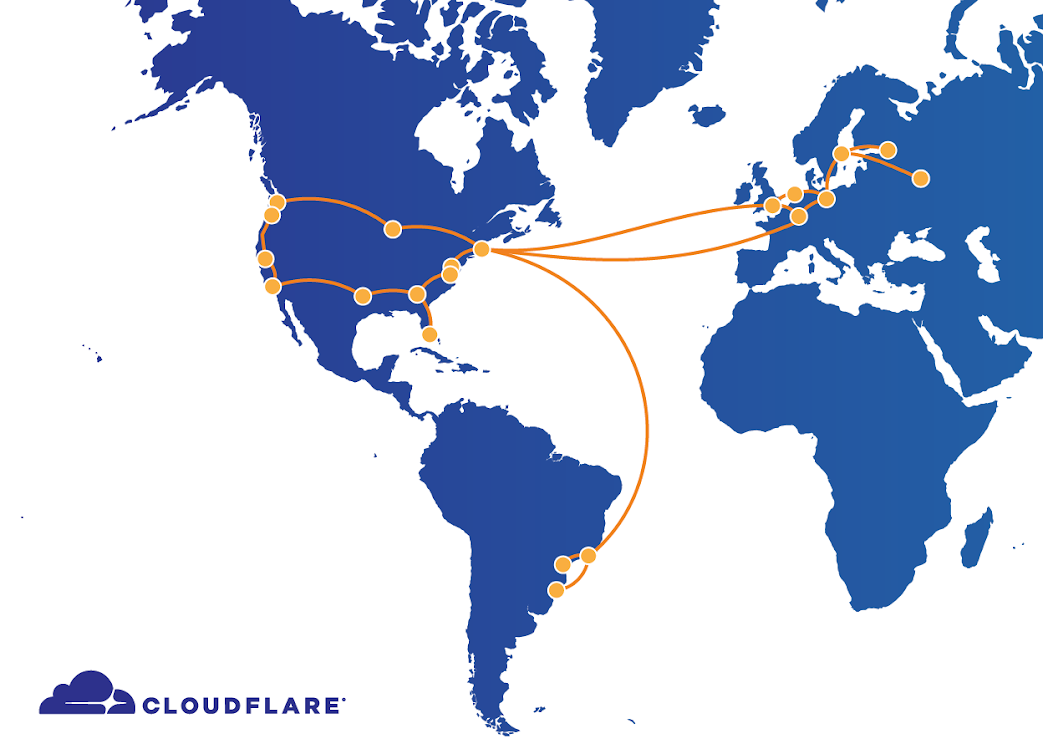
Today a configuration error in our backbone network caused an outage for Internet properties and Cloudflare services that lasted 27 minutes. We saw traffic drop by about 50% across our network. Because of the architecture of our backbone this outage didn’t affect the entire Cloudflare network and was localized to certain geographies.
The outage occurred because, while working on an unrelated issue with a segment of the backbone from Newark to Chicago, our network engineering team updated the configuration on a router in Atlanta to alleviate congestion. This configuration contained an error that caused all traffic across our backbone to be sent to Atlanta. This quickly overwhelmed the Atlanta router and caused Cloudflare network locations connected to the backbone to fail.
The affected locations were San Jose, Dallas, Seattle, Los Angeles, Chicago, Washington, DC, Richmond, Newark, Atlanta, London, Amsterdam, Frankfurt, Paris, Stockholm, Moscow, St. Petersburg, São Paulo, Curitiba, and Porto Alegre. Other locations continued to operate normally.
For the avoidance of doubt: this was not caused by an attack or breach of any kind.
We are sorry for this outage and have already made a global change to the backbone configuration that will prevent it from being able to occur Continue reading
Dictionary : simplicitarian

Using fancy words gives you credibility.
The post Dictionary : simplicitarian appeared first on EtherealMind.
Heavy Networking 530: Everything You Need To Know About Wireless ISPs
Today's Heavy Networking dives into wireless Internet Service Providers, or WISPs. WISPs typically serve rural areas that have limited access to fiber or copper, but they also serve metro and urban areas and industrial sectors such as energy. Our guests to inform and instruct us about WISPs are Kevin Myers, Senior Network Architect at IP ArchiTechs; and Cory Steele, Senior Consultant at STIGroup.
The post Heavy Networking 530: Everything You Need To Know About Wireless ISPs appeared first on Packet Pushers.
Heavy Networking 530: Everything You Need To Know About Wireless ISPs
Today's Heavy Networking dives into wireless Internet Service Providers, or WISPs. WISPs typically serve rural areas that have limited access to fiber or copper, but they also serve metro and urban areas and industrial sectors such as energy. Our guests to inform and instruct us about WISPs are Kevin Myers, Senior Network Architect at IP ArchiTechs; and Cory Steele, Senior Consultant at STIGroup.The Silver (Peak) Lining For HPE and Cloud

You no doubt saw the news this week that HPE announced that they’re buying Silver Peak for just shy of $1 billion dollars. It’s a good exit for Silver Peak and should provide some great benefits for both companies. There was a bit of interesting discussion around where this fits in the bigger picture for HPE, Aruba, and the cloud. I figured I’d throw my hat in the ring and take a turn discussing it.
Counting Your Chickens
First and foremost, let’s discuss where this acquisition is headed. HPE announced it and they’re the ones holding the purse strings. But the acquisition post was courtesy of Keerti Melkote, who runs the Aruba, a Hewlett Packard Enterprise Company (Aruba) side of the house. Why is that? It’s because HPE “reverse acquired” Aruba and sent all their networking expertise and hardware down to the Arubans to get things done.
I would venture to say that Aruba’s acquisition was the best decision HPE could have made. It gave them immediate expertise in an area they sorely needed help. It gave Aruba a platform to build on and innovate from. And it ultimately allowed HPE to shore up their campus networking story while trying Continue reading