Chapter Training Program 2020: The Power of Us!

“Vulnerability is the birthplace of innovation, creativity and change.”
—Brené Brown
Three months ago, the Internet Society decided to face a new challenge. We took ourselves out of our comfort zone to move our community to the next level: empowerment through education. We began the Chapter Training Program, born to satisfy the increasing need of our Chapter leaders to engage their members in an impactful and informed way. The purpose was to identify and help form new leaders to work together to create local awareness, as part of our 2020 Action Plan .
This journey was not easy. However, our community embraced vulnerability and we overcame many obstacles, like change and uncertainty. In the end, we succeeded – because together our strength is bigger than our challenges. It’s part of our community’s DNA: having the conviction to build an Internet that enriches people’s lives and enables opportunities to all.We demonstrated that when we work together, we accomplish great things. Challenge becomes just a word… To be brave, first we need to be vulnerable and once we are brave, the sky is the limit!
I want to share the results of our work – and I hope we can Continue reading
Now GA: Data-in-Transit Encryption in Calico v3.15
We’re excited to announce that the latest release of Calico includes encryption for data-in-transit. Calico is the open source networking and network security solution for containers, virtual machines, and host-based workloads, offering connectivity and security for container workloads.
One of Calico’s best-known security features is its implementation of Kubernetes Network Policy, providing a way to secure container workloads by restricting traffic to and from trusted sources. This enables the traffic to be controlled, however, the traffic itself had previously remained vulnerable to interception.
A common solution to this problem is to encrypt traffic at the application layer using protocols like Transport Layer Security (TLS). Traffic can also be encrypted at a lower infrastructure level using IPsec. However, these approaches introduce an additional layer of complexity. Calico avoids that complexity by utilizing WireGuard to implement data-in-transit encryption.
WireGuard is run as a module inside the Linux kernel and provides better performance and lower power consumption than IPsec and OpenVPN tunneling protocols. The Linux version of WireGuard reached a stable production release in March and was introduced as a tech preview in the 3.14 release of Project Calico. We are pleased to announce that WireGuard encryption is now generally available with Continue reading
How Does Technology Affect the Generation Gap?
One of the biggest divisions between the generations today is technology. And with a huge disparity in attitudes towards technology as well as competence levels, there is a danger that each generation is becoming even more separated, settling into their own niche areas regarding the way that we all socialize, receive news, and communicate with each other. When asking how technology affects the generation gap, there is a lot more to it than having the ability to download a movie or app or do online shopping.
First up the most digital savvy group of adults are the Millennials. These people born between 1981 and 1996 cannot remember a time without email and the internet. Millennials are technically competent, and this generation tends to want to share their lives online in a way that would appeal to older people. There is an attitude that if it isn’t posted on social media, it just didn’t happen!
By contrast, Generation X , the people born in the early 1960s through to the ’70s are often technically able to use the internet and use online banking , shopping and to occasionally post on social media, but in most cases, technology is not a major Continue reading
IPv6 Buzz 055: The Good, Bad, And Ugly Of IPv6 With Geoff Huston
We discuss the challenges and opportunities of IPv6 with Geoff Huston, APNIC's chief scientist and network analyst nonpareil. Topics include how dual-stack and Happy Eyeballs have papered over v6 deficiencies, why the address space may not be as vast as advertised, and why v6 is still the future.
The post IPv6 Buzz 055: The Good, Bad, And Ugly Of IPv6 With Geoff Huston appeared first on Packet Pushers.
IPv6 Buzz 055: The Good, Bad, And Ugly Of IPv6 With Geoff Huston
We discuss the challenges and opportunities of IPv6 with Geoff Huston, APNIC's chief scientist and network analyst nonpareil. Topics include how dual-stack and Happy Eyeballs have papered over v6 deficiencies, why the address space may not be as vast as advertised, and why v6 is still the future.HS. Part 6. First impression from Nokia SRLinux.
Hello my friend,
In this HS blog series we have covered so far the automated build of the network topology for hyper scale data centre using Microsoft Azure SONiC. Today Nokia has announced a new product for data centre, which is called SRLinux. In the next couple of articles we’ll review it from the architectural and automation standpoint.
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
Thanks
We want to thank Nokia team for providing us the details and assisting in creating these materials. It won’t be possible without your help, dear partners.
Network automation training – now as a self-paced course as well
Following your asks we open a new format for the network automation training – self-paced format:
- It doesn’t matter what your timezone is.
- It doesn’t matter how much hours weekly do you have to study.
- It doesn’t matter how solid is your current background in automation, scripting and software development.
Because you decide on your own when, how often and Continue reading
IXPs: Keeping Local Infrastructure Resilient during COVID-19

The COVID-19 pandemic has proven how important a strong Internet infrastructure is.
Internet exchange points are a vital part of that. They are key to bringing better, faster, and more affordable Internet to people.
Recently, the Asia Pacific Internet Exchange Association (APIX) and the Internet Society did a comprehensive survey to understand the impact of COVID-19 on IXP operations in the region.
IXPs from Japan, Hong Kong, Taiwan, Thailand, Myanmar, Philippines, Singapore, Vietnam, Indonesia, Malaysia, Nepal, and Australia provided data. Here are some of the key findings.
What is an Internet Exchange Point?
If you want to see your neighbor, taking a route that sends you across town and back again is not the quickest or most efficient way to get there. And yet, in many parts of the world, that is what happens with Internet traffic. IXPs help create shorter, more direct routes for Internet traffic.
Read the Explainer
Changes in Internet Traffic
There was a significant increase in Internet exchange traffic, between 7- 40%. Traffic patterns during the pandemic show that there is either no difference left between peak and off-peak time or the peak time has increased from a few to more hours.
The increase is highest Continue reading
draft-knodel-terminology-03 – Terminology, Power, and Inclusive Language in Internet-Drafts and RFCs

Add to your documentation style guide.
The post draft-knodel-terminology-03 – Terminology, Power, and Inclusive Language in Internet-Drafts and RFCs appeared first on EtherealMind.
No Humans Involved: Mitigating a 754 Million PPS DDoS Attack Automatically


On June 21, Cloudflare automatically mitigated a highly volumetric DDoS attack that peaked at 754 million packets per second. The attack was part of an organized four day campaign starting on June 18 and ending on June 21: attack traffic was sent from over 316,000 IP addresses towards a single Cloudflare IP address that was mostly used for websites on our Free plan. No downtime or service degradation was reported during the attack, and no charges accrued to customers due to our unmetered mitigation guarantee.
The attack was detected and handled automatically by Gatebot, our global DDoS detection and mitigation system without any manual intervention by our teams. Notably, because our automated systems were able to mitigate the attack without issue, no alerts or pages were sent to our on-call teams and no humans were involved at all.

During those four days, the attack utilized a combination of three attack vectors over the TCP protocol: SYN floods, ACK floods and SYN-ACK floods. The attack campaign sustained for multiple hours at rates exceeding 400-600 million packets per second Continue reading
The Hedge Pdocast Episode 43: Ivan Pepelnjak and Trusting Routing Protocols
Can you really trust what a routing protocol tells you about how to reach a given destination? Ivan Pepelnjak joins Nick Russo and Russ White to provide a longer version of the tempting one-word answer: no! Join us as we discuss a wide range of issues including third-party next-hops, BGP communities, and the RPKI.
Day Two Cloud 056: (Not) Streaming Telemetry
Streaming telemetry is all the rage, but today's show dives into an architecture that forgoes streaming telemetry in favor of other options. We talk about why our guests went in a different direction, the problems they're trying to solve, and how it's working out. Our guests are Kevin Landreth, Director, Service Reliability; and Carl Montanari, Network Reliability Engineer, both at Packet Fabric.
The post Day Two Cloud 056: (Not) Streaming Telemetry appeared first on Packet Pushers.
Day Two Cloud 056: (Not) Streaming Telemetry
Streaming telemetry is all the rage, but today's show dives into an architecture that forgoes streaming telemetry in favor of other options. We talk about why our guests went in a different direction, the problems they're trying to solve, and how it's working out. Our guests are Kevin Landreth, Director, Service Reliability; and Carl Montanari, Network Reliability Engineer, both at Packet Fabric.NTC – A Chat With Jason Edelman
In today’s episode we sit down with Network to Code’s founder, Jason Edelman, to discuss his personal networking journey, how Network to Code came to be, and how he views the networking industry through the lens of network automation and orchestration.
Outro Music:
Danger Storm Kevin MacLeod (incompetech.com)
Licensed under Creative Commons: By Attribution 3.0 License
http://creativecommons.org/licenses/by/3.0/
The post NTC – A Chat With Jason Edelman appeared first on Network Collective.
Member News: Chapters Focus on Encryption

Lock it down: Several Internet Society chapters across the globe have written about the importance of encryption in recent weeks. The Namibia Chapter wrote about the way encryption can improve privacy and fight against the big business of criminal hacking. “Cybercrime is a global business, often run by multinational outfits,” the Chapter wrote. The Hong Kong Chapter, meanwhile, wrote that “encryption matters to all of us.” Internet users need to work together to protect encryption, the Chapter added. “No party can stand alone to persuade governments to stop creating laws or policies that harm encryption and digital security.”
Freedom for all: The Hong Kong Chapter also called for Internet freedoms to continue in the region as the Chinese government pushes for new security laws there. “We are convinced that the freedoms of speech, press and publication guaranteed by the Basic Law are also applicable to the media industry on the Internet,” the chapter wrote. “Internet users have the freedom and right to obtain, share information and express their expressions, and are protected from being censored, blocked or criminalized.”
Expanding the community: The Nepal Chapter recently wrote about community networks in the country, by highlighting the Rural Continue reading
Sandboxing in Linux with zero lines of code
Modern Linux operating systems provide many tools to run code more securely. There are namespaces (the basic building blocks for containers), Linux Security Modules, Integrity Measurement Architecture etc.
In this post we will review Linux seccomp and learn how to sandbox any (even a proprietary) application without writing a single line of code.
Tux by Iwan Gabovitch, GPL
Sandbox, Simplified Pixabay License
Linux system calls
System calls (syscalls) is a well-defined interface between userspace applications and the operating system (OS) kernel. On modern operating systems most applications provide only application-specific logic as code. Applications do not, and most of the time cannot, directly access low-level hardware or networking, when they need to store data or send something over the wire. Instead they use system calls to ask the OS kernel to do specific hardware and networking tasks on their behalf:
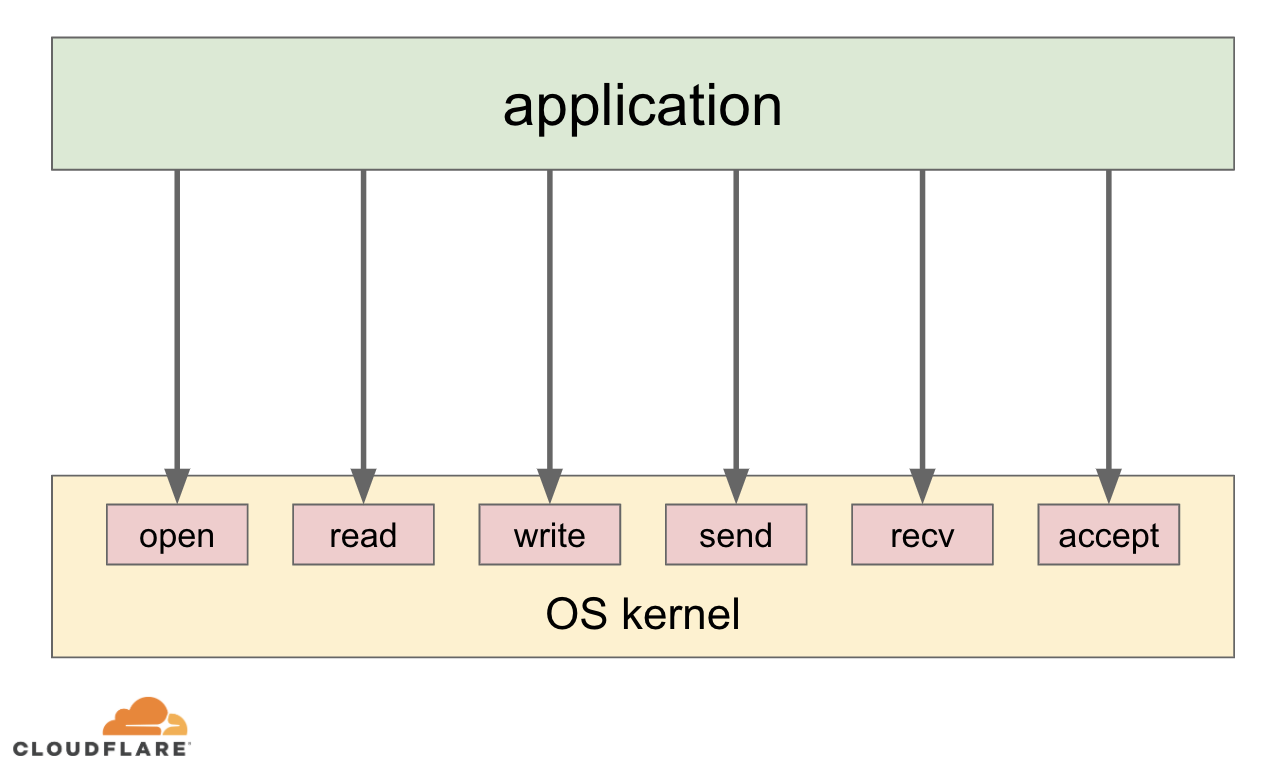
Apart from providing a generic high level way for applications to interact with the low level hardware, the system call architecture allows the OS kernel to manage available resources between applications as well as enforce policies, like application permissions, networking access control lists etc.
Linux seccomp
Linux seccomp is yet another syscall on Linux, but it is a bit Continue reading
Worth Reading: Lies, Damned Lies, and Keynotes
Got sick and tired of conference keynotes? You might love the Lies, Damned Lies, and Keynotes rant by Corey Quinn. Here are just two snippets:
They’re selling a fantasy, and you’ve been buying it all along.
We’re lying to ourselves. But it feels better than the unvarnished truth.
Enjoy!