Cloud-Native Security Remains a Complex Organism
“It’s natural that the security factors become critical because now they're suddenly very large...
Health Check Analytics and how you can use it
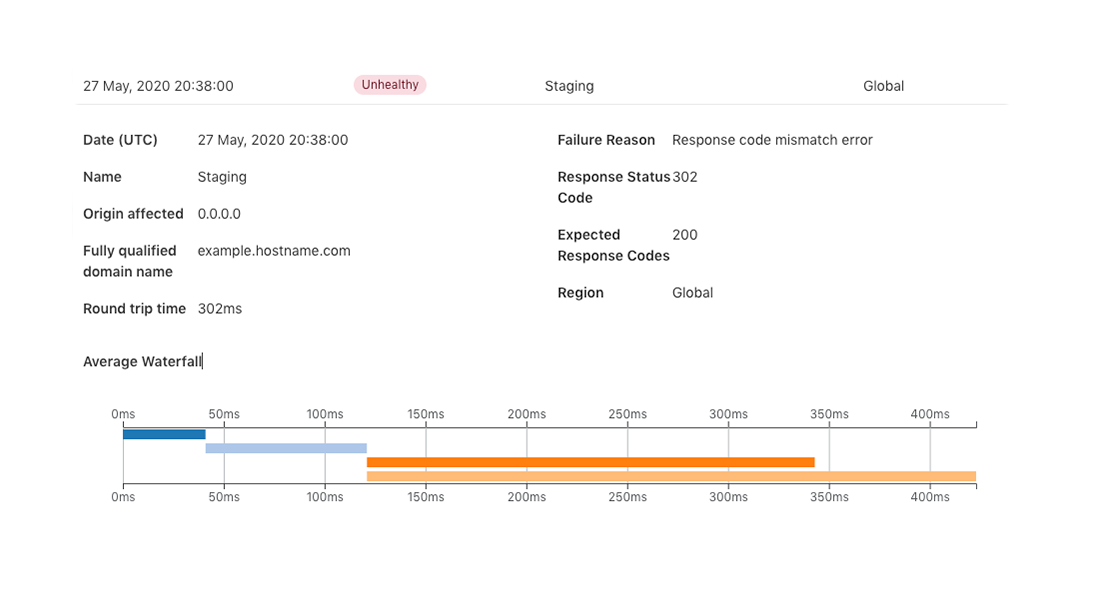
At the end of last year, we introduced Standalone Health Checks - a service that lets you monitor the health of your origin servers and avoid the need to purchase additional third party services. The more that can be controlled from Cloudflare decreases maintenance cost, vendor management, and infrastructure complexity. This is important as it ensures you are able to scale your infrastructure seamlessly as your company grows. Today, we are introducing Standalone Health Check Analytics to help decrease your time to resolution for any potential issues. You can find Health Check Analytics in the sub-menu under the Traffic tab in your Cloudflare Dashboard.
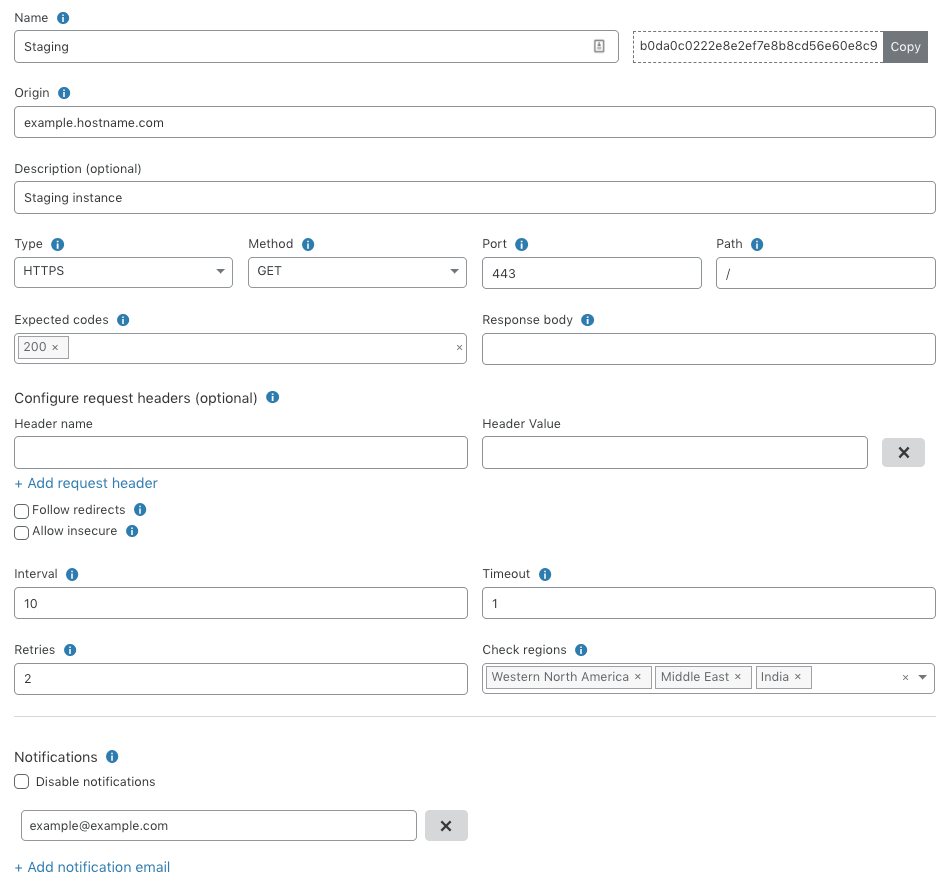
As a refresher, Standalone Health Checks is a service that monitors an IP address or hostname for your origin servers or application and notifies you in near real-time if there happens to be a problem. These Health Checks support fine-tuned configurations based on expected codes, interval, protocols, timeout and more. These configurations enable you to properly target your checks based on the unique setup of your infrastructure. An example of a Health Check can be seen below which is monitoring an origin server in a staging environment with a notification set via email.
Once you set Continue reading
Field Engineering and COVID19

First posted in Human Infrastructure Magazine in April 2020 – a free email newsletter from the Packet Pushers. Subscribe here. How does business operate when the pandemic lockdown ‘ends’ and how does it impact you ? COVID19 won’t be gone, its gonna be months before a new ‘normal’ emerges. Getting back to work means close […]
The post Field Engineering and COVID19 appeared first on EtherealMind.
SuzieQ with Dinesh Dutt and Justin Pietsch on Software Gone Wild
In early May 2020 I wrote a blog post introducing SuzieQ, a network observability platform Dinesh Dutt worked on for the last few years. If that blog post made you look for more details, you might like the Episode 111 of Software Gone Wild in which we went deeper and covered these topics:
- How does SuzieQ collect data
- What data is it collecting from network devices
- What can you do with that data
- How can you customize and extend SuzieQ
Kubernetes Security: Lateral Movement Detection and Defense
What is Lateral Movement?
Lateral movement refers to the techniques that a cyber-attacker uses, after gaining initial access, to move deeper into a network in search of sensitive data and other high-value assets. Lateral movement techniques are widely used in sophisticated cyber-attacks such as advanced persistent threats (APTs). An adversary uses these techniques to access other hosts from a compromised system and get access to sensitive resources, such as mail systems, shared folders, and legitimate credentials, ultimately gaining access to the identified target. Lateral movement techniques enable a threat actor to avoid detection and retain access over an extended dwell time of weeks, or even months, after the initial breach.
What are the Stages of Lateral Movement?
There are three primary stages of lateral movement: reconnaissance, credential/privilege gathering, and gaining access to other resources in the network.
How Does an Adversary Gain Unauthorized Access to a Kubernetes Cluster?
In a Kubernetes cluster, an attacker will gain initial access by compromising a pod. Once the pod is compromised, there are three main areas where the attacker can begin reconnaissance and move through the lateral movement stages to learn more about the cluster: the cloud provider metadata service, the pod networking and Continue reading
GitLab Acquires Peach Tech and Fuzzit to Expand its DevSecOps Offering
GitLab has acquired Peach Tech, a security software firm specializing in protocol fuzz testing and...
SD-WAN an Enterprise Favorite for Securing the Cloud
Of those surveyed, 74% reported had deployed or plan to deploy SD-WAN to secure cloud workloads.
Cradlepoint Partners With Rigado to Deliver a Safe Workplace Solution Using NetCloud Edge Containers and Built on Microsoft Azure
Cradlepoint announced that Rigado joined its Technology Alliance Partner program to build a Safe...
Daily Roundup: Amazon Won’t Sell Facial Recognition to Police
Amazon said it wouldn't sell facial recognition to police; Nokia mellowed its 5G outlook for 2020;...
Microsoft Joins Amazon, IBM With Facial Recognition Ban
Company President Brad Smith said it does not sell that technology today and is in favor of a...
Juniper CTO Dishes Edge Cloud Strategy
Open RAN and the rise of 5G presents an opportunity for Juniper to play in a market it hasn’t...
Google Taps Telefónica for Telco Cloud Edge Expansion
The deal includes Google opening a new cloud region in Spain and Telefónica using Google Cloud’s...
SonicWall Adds SD-Branch Functionality, Switches
The SD-branch capabilities will enable customers to remotely provision and manage branch...
Amazon Stops Selling Police Its Facial Recognition Tech
“We’ve advocated that governments should put in place stronger regulations to govern the...
IPv6 Buzz 053: Applications And IPv6
In this week's IPv6 Buzz episode, Scott and Tom discuss applications and IPv6 with Dan York. They also talk to Dan about his role at the Internet Society and pro-IPv6 ISOC programs such as Deploy360 and Open Standards Everywhere.IPv6 Buzz 053: Applications And IPv6
In this week's IPv6 Buzz episode, Scott and Tom discuss applications and IPv6 with Dan York. They also talk to Dan about his role at the Internet Society and pro-IPv6 ISOC programs such as Deploy360 and Open Standards Everywhere.
The post IPv6 Buzz 053: Applications And IPv6 appeared first on Packet Pushers.
Tech Bytes: Solving Common Network Issues With Apstra’s Intent-Based Networking (Sponsored)
Today's Tech Byte episode, sponsored by Apstra, delves into solving common network problems with Intent-Based Networking (IBN), including how a customer used Apstra AOS to troubleshoot an EVPN issue. Our Apstra guests are Sean Hafeez, VP of Product Management; and Jeff Tantsura, Head of Networking Strategy.
The post Tech Bytes: Solving Common Network Issues With Apstra’s Intent-Based Networking (Sponsored) appeared first on Packet Pushers.
Tech Bytes: Solving Common Network Issues With Apstra’s Intent-Based Networking (Sponsored)
Today's Tech Byte episode, sponsored by Apstra, delves into solving common network problems with Intent-Based Networking (IBN), including how a customer used Apstra AOS to troubleshoot an EVPN issue. Our Apstra guests are Sean Hafeez, VP of Product Management; and Jeff Tantsura, Head of Networking Strategy.Project Galileo’s 6th year Anniversary: The Impact of COVID-19 on the most vulnerable groups on the Internet


Consistent with our mission to “help build a better Internet,” Cloudflare believes that one of the most important roles for the Internet is to empower marginalized voices that may not be heard, or bring together oppressed groups of people that may otherwise find themselves isolated and alone. Six years ago, Cloudflare started Project Galileo to provide free services to vulnerable nonprofits, journalism and independent media voices online who might otherwise be in danger of being silenced by cyberattacks. Much has changed in the past couple of months as the COVID-19 pandemic has transformed the world while the United States faces a wave of protests addressing racial violence and inequality. These events have put further strain on vulnerable groups working in these spaces, and we have seen many organizations step up to ensure that those who are most affected by these circumstances are protected. At Cloudflare, we believe that protecting these groups from attack is essential to helping build a better Internet.
We are excited to mark the 6th anniversary of the project this month, and it is a good time for us to reflect, talk to participants, and see how the Project has grown and changed over the course of Continue reading