Cloud Foundry Foundation Adopts KubeCF Runtime
The adoption is another block in CFF's path-building toward Kubernetes.
Daily Roundup: AWS Pledges $20M to COVID-19 Testing
AWS pledged $20 million to COVID-19 testing; Microsoft topped cloud rankings; and Cisco donated...
Heavy Networking 507: Build And Run A Multi-Cloud Network Architecture With Aviatrix (Sponsored)
Cloud networking is a challenge, to say the least. And when you've got deployments running in different public clouds, your challenges multiply. On today's Heavy Networking, sponsor Aviatrix joins us to discuss their cloud networking architecture, which provides a consistent operational environment on top of cloud-native constructs. Our guests are Hammad Alam and Shahzad Ali, both Principal Cloud Solutions Architects at Aviatrix.Heavy Networking 507: Build And Run A Multi-Cloud Network Architecture With Aviatrix (Sponsored)
Cloud networking is a challenge, to say the least. And when you've got deployments running in different public clouds, your challenges multiply. On today's Heavy Networking, sponsor Aviatrix joins us to discuss their cloud networking architecture, which provides a consistent operational environment on top of cloud-native constructs. Our guests are Hammad Alam and Shahzad Ali, both Principal Cloud Solutions Architects at Aviatrix.
The post Heavy Networking 507: Build And Run A Multi-Cloud Network Architecture With Aviatrix (Sponsored) appeared first on Packet Pushers.
Fast Friday Thoughts on Where We Are
It’s been a crazy week. I know the curse is “May you live in interesting times,” but I’m more than ready for things to be less interesting for a while. It’s going to take some time to adjust to things. From a networking perspective, I have a few things that have sprung up.
- Video conferencing is now a big thing. Strangely, Cisco couldn’t make video the new phone. But when people are stuck at home now we need to do video again? I get that people have a need to see each other face-to-face. But having worked from home for almost seven years at this point I can tell you video isn’t a necessity. It’s a nice option, but you can get a lot accomplished with video calls and regular emails.
- Along side this is the fact that the push to put more video out there is causing applications to reach their breaking points. Zoom, which is fairing the best out of all of them so far, had some issues on Thursday morning. Tripling the amount of traffic that’s going out and making it very sensitive to delay and jitter is going expose a lot of flaws in the system.
- Continue reading
AWS Pledges $20M to COVID-19 Testing as Cloud Giants, Chipmakers Fight Virus With HPC
While the AWS initiative will initially focus on COVID-19, AWS says it “will also consider other...
Enea Taps Ampere for Arm-based Edge uCPE
The equipment provides an environment on which to run virtual network functions like those for...
Microsoft Skins AWS in Forrester Cloud Ranking
The report lauded those two giants for their extensive services and support, which continues to...
Cisco Donates OpenRoaming as WiFi Standard
OpenRoaming, which has been developed and managed by Cisco for two years, is built on standards and...
Invitation: Virtual Happy Hour The Second – TONIGHT 30 Mar 2020 2100BST/1600EST/1300PST

An open videoconference to be nice to each other, blow the Corona blues away.
The post Invitation: Virtual Happy Hour The Second – TONIGHT 30 Mar 2020 2100BST/1600EST/1300PST appeared first on EtherealMind.
The Serverlist: Workers Secrets, Serverless Supremacy, and more!

Check out our thirteenth edition of The Serverlist below. Get the latest scoop on the serverless space, get your hands dirty with new developer tutorials, engage in conversations with other serverless developers, and find upcoming meetups and conferences to attend.
Sign up below to have The Serverlist sent directly to your mailbox.
BGP – the right tool for so many jobs
The post BGP – the right tool for so many jobs appeared first on Noction.
Weekly Wrap: Coronavirus No Match for Oracle’s Larry Ellison
SDxCentral Weekly Wrap for March 30, 2020: Oracle posts strong results despite virus concerns;...
BGP+SPF for Hyperscale/Massively Scale Datacenter Deployment
BGP+SPF Imagine we replace BGP best path selection decision with SPF. BGP+SPF exactly does that. In this post, I will explain why we are looking for alternative protocols for Massively Scale Datacenter.
Although there is no exact answer how many devices should be in the datacenter so datacenter can be considered Massively Scale, but we know 10.000 Racks are not uncommon in these type of datacenter and each rack, when BGP is used as a transport, gets it’s own unique AS number.
Before I explain BGP+SPF, let’s understand why traditional , very well know, OSPF or IS-IS are not used in these type of datacenter.
Answer is scalability. OSPF and IS-IS are chatty protocols and flooding aspect of these protocols are just not suited to very densely meshed connectivities. Yes, these datacenter run on CLOS topology and CLOS is densely meshed topology.
Also, we want to have wide ECMP in these type of datacenter, meaning, between the TOR, Leaf and Spine devices, there are so many equal cost path and we want to utilize them all. OSPF and IS-IS will be limited to number of ways of ECMP.
BGP is very well suited protocol which provides very wide ECMP Continue reading
Remote Work Isn’t Just Video Conferencing: How We Built CloudflareTV
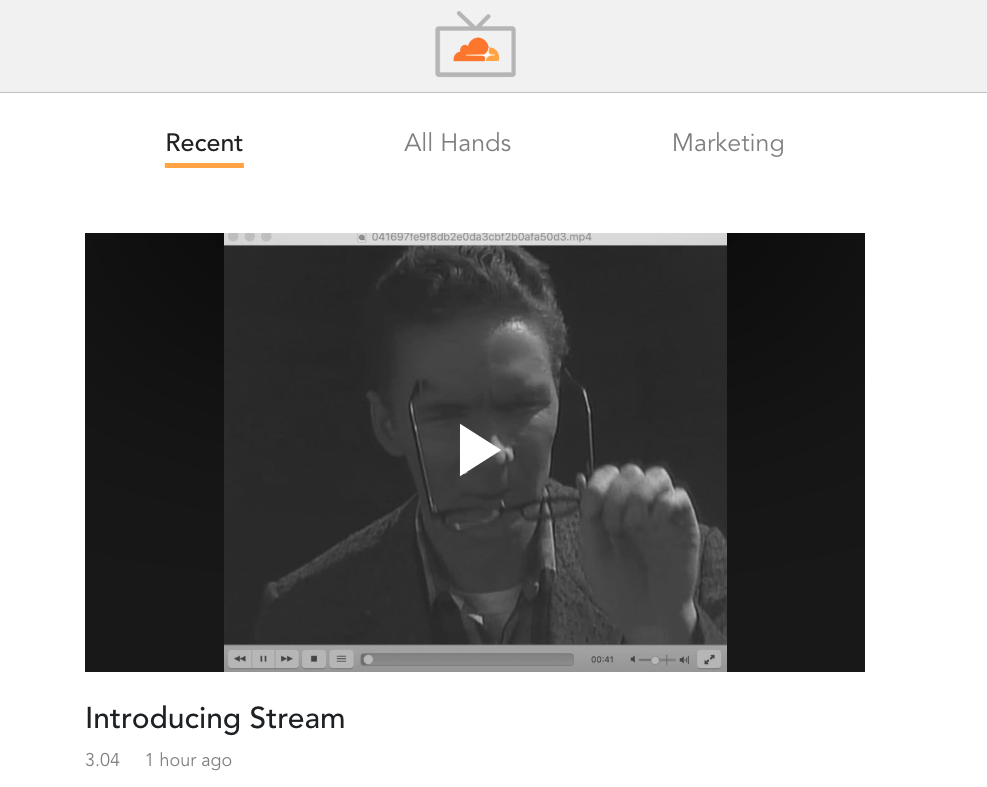
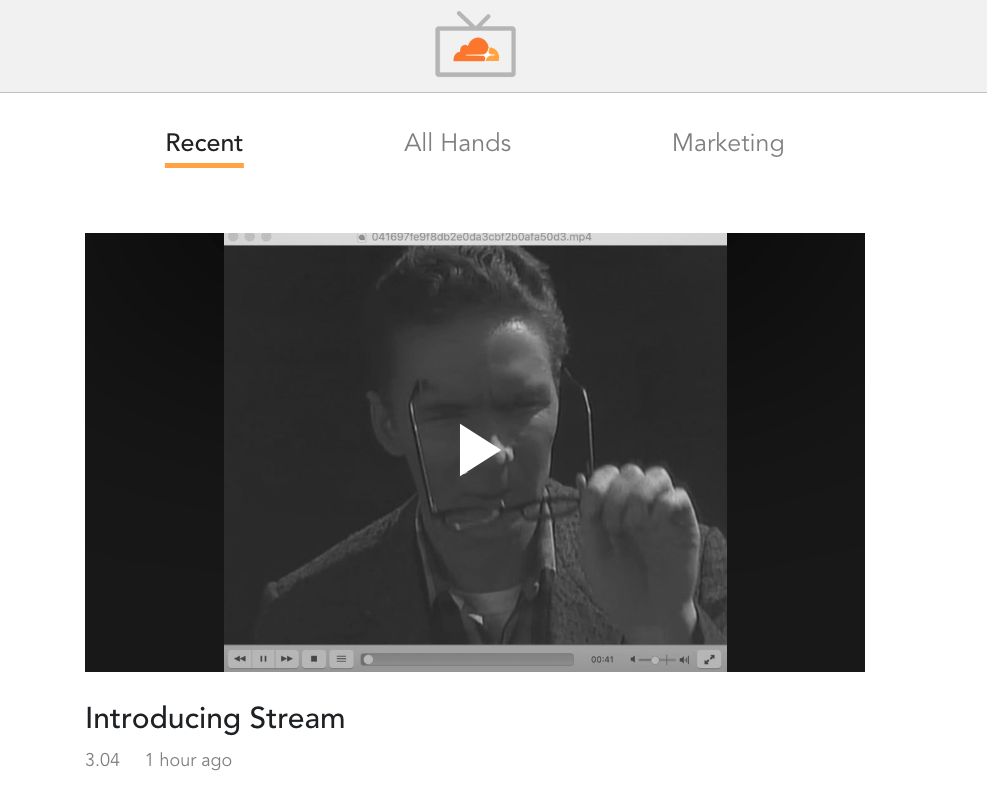
At Cloudflare, we produce all types of video content, ranging from recordings of our Weekly All-Hands to product demos. Being able to stream video on demand has two major advantages when compared to live video:
- It encourages asynchronous communication within the organization
- It extends the life time value of the shared knowledge
Historically, we haven’t had a central, secure repository of all video content that could be easily accessed from the browser. Various teams choose their own platform to share the content. If I wanted to find a recording of a product demo, for example, I’d need to search Google Drive, Gmail and Google Chat with creative keywords. Very often, I would need to reach out to individual teams to finally locate the content.
So we decided we wanted to build CloudflareTV, an internal Netflix-like application that can only be accessed by Cloudflare employees and has all of our videos neatly organized and immediately watchable from the browser.
We wanted to achieve the following when building CloudflareTV:
- Security: make sure the videos are access controlled and not publicly accessible
- Authentication: ensure the application can only be accessed by Cloudflare employees
- Tagging: allow the videos to be categorized so they can Continue reading
Opinion : Engineers, Solutions and Problems

The tension between iteration and guarantees.
The post Opinion : Engineers, Solutions and Problems appeared first on EtherealMind.
Video: FRRouting Deployment Guidelines
After describing the FRRouting architecture, as well as recent performance optimizations and usability enhancements, Donald Sharp concluded the FRRouting webinar with detailed deployment guidelines.
Video: FRRouting Deployment Guidelines
After describing the FRRouting architecture, as well as recent performance optimizations and usability enhancements, Donald Sharp concluded the FRRouting webinar with detailed deployment guidelines.
White Hat Hackers Fight COVID-19, Donate GPUs for a Cure
Security company Critical Start and its threat hunters are among the global contributors running...