Dremio CEO: Open Cloud Data Lake Levels on the Rise
Open cloud data warehouses are still data warehouses, and savvy enterprises are moving directly to...
JAMstack at the Edge: How we built Built with Workers… on Workers
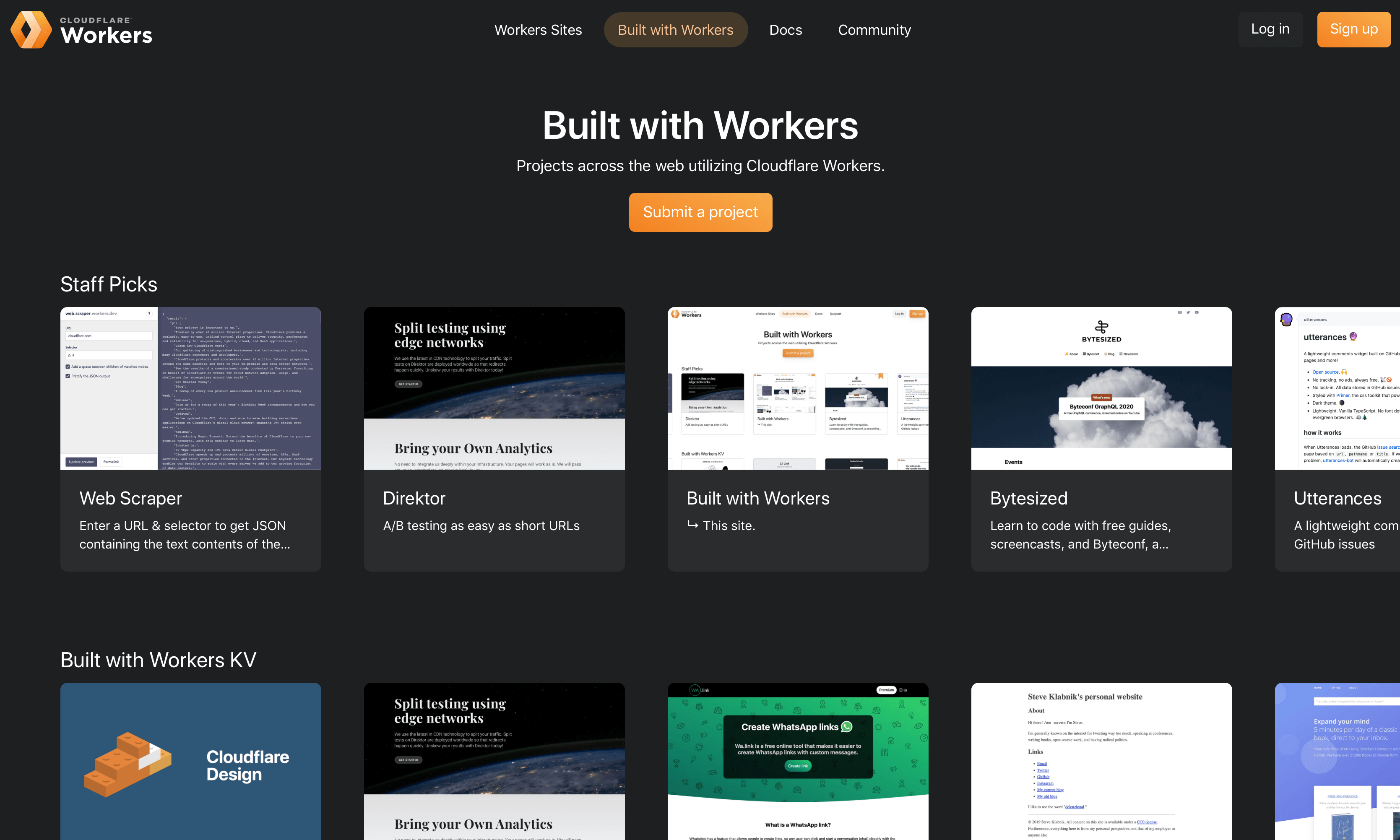
I'm extremely stoked to announce Built with Workers today – it's an awesome resource for exploring what you can build with Cloudflare Workers. As Adam explained in our launch post, showcasing developers building incredible projects with tools like Workers KV or our streaming HTML rewriter is a great way to celebrate users of our platform. It also helps encourage developers to try building their dream app on top of Workers. In this post, I’ll explore some of the architectural and implementation designs we made while building the site.
When we first started planning Built with Workers, we wanted to use the site as an opportunity to build a new greenfield application, showcasing the strength of the Workers platform. The Workers Developer Experience team is cross-functional: while we might spend most of our time improving our docs, or developing features for our command-line interface Wrangler, most of us have spent years developing on the web. The prospect of starting a new application is always fun, but in this instance, it was a prime chance to ask (and answer) the question, "If I could build this site on Workers with whatever tools I want, what would I choose?"
A guiding Continue reading
Announcing Built with Workers
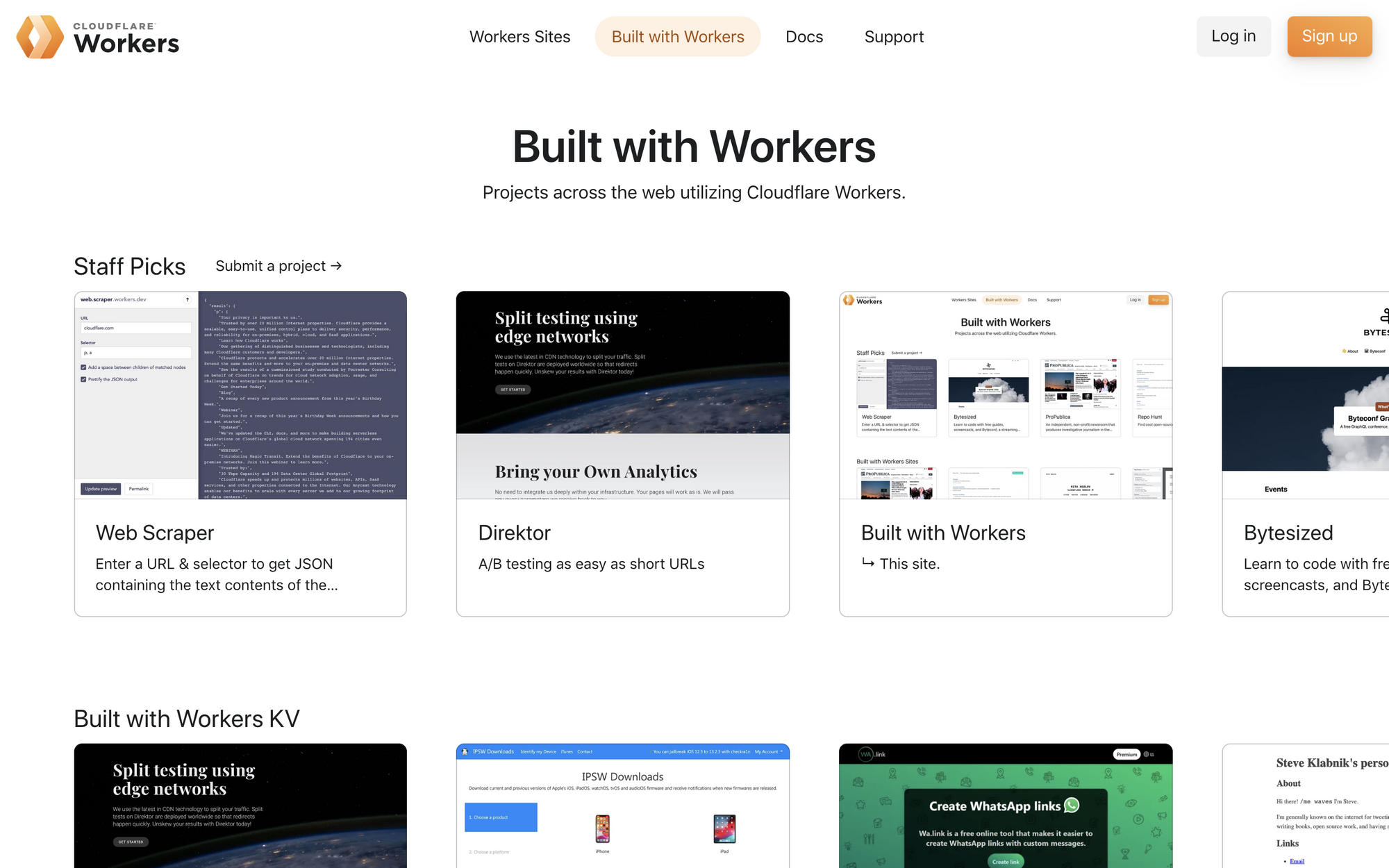
Ever since its initial release, Cloudflare Workers has given JavaScript developers a platform to enable building high-performance applications with automatic scaling.
As with any new technology, we know it can be a bit intimidating to get started. For one thing, running code on the edge is a paradigm shift—forcing us to rethink classic web architecture problems, or removing them altogether. For another, since you can build just about anything, it can be challenging to figure out what to build first.
Today we’re launching Built with Workers, a new site designed to help get those creative juices flowing and unblock you, by answering that simple but important question: What can I build with Cloudflare Workers?
Some time in 1999, at age 11, I received my first graphing calculator. It was a TI-82 that my older sister no longer needed. It was on this very calculator that I learned to write code. Looking back, I’m not sure how exactly I had the patience or sanity to figure it all out.
It was a mess. Among the many difficulties were that I had to type the code out on the calculator’s non-QWERTY keyboard, the language I was writing in didn’t have Continue reading
Transforming XML Data With Ansible
Some network devices return structured data in either text- or XML format (but cannot spell JSON). Ansible prefers getting JSON-formatted data, and has a number of filters to process text printouts… but what could you do if you want to work with XML documents within Ansible? I described a few solutions in Transforming XML Data in Ansible.
Daily Roundup: Cisco Joins On-Prem Kubernetes Party
Cisco joined the on-premises Kubernetes party; the U.K. banned Huawei from 5G core networks; and...
VMware Loses $237M Patent Infringement Lawsuit
Densify, a startup that makes cloud and container resource management software, accused VMware of...
Nutanix and HPE Team Up Together to Deliver Cloud Simplicity On-Premises
Though the customer takes delivery of the HPE systems with Nutanix software on-site or at the...
Cloud, Software Revenues Prop Up Juniper’s Q4 Earnings
Cloud revenues continued to be a sweet spot for the networking vendor. The vertical saw strong...
FCC Greenlights Shared Spectrum in CBRS Band
The effort, which eventually gathered buy-in from multiple federal agencies and 159 members of the...