BGP in 2019
It has become a tradition each January for me to report on the behaviour of the inter-domain routing system over the past year, looking in some detail at some metrics from the routing system that can show the essential shape and behaviour of the underlying interconnection fabric of the Internet.Daily Roundup: Citrix Bug Gets Uglier
The bug impacts Citrix's ACD platform; Samsung acquired TeleWorld to boost its U.S. RAN efforts;...
Vodafone UK Activates 5G Multi-Operator RAN
5G network sharing deals have gained momentum as carriers look to decrease the cost of deploying...
LogicMonitor Gobbles Up AIOps Provider Unomaly
Unomaly's technology will allow users to proactively take action before network disruptions impact...
SK Telecom Launches APAC-Focused MEC Task Force
The group will share its work on 5G and MEC including working toward international MEC standards to...
Samsung Taps TeleWorld Solutions to Elevate US 5G RAN
Samsung has earned 5G RAN contracts in the U.S. with Verizon, AT&T, and Sprint, but is behind...
Citrix ACD, Gateway Bug Gets Even Uglier
Over the weekend two groups released proof-of-concept (PoC) exploit codes for this vulnerability on...
Tech Bytes: Cushman & Wakefield Taps Silver Peak SD-WAN For Cloud-First Goals (Sponsored)
On today's Tech Bytes podcast, sponsored by Silver Peak, we talk with Cushman & Wakefield about how the global real estate company is using SD-WAN to enable its cloud-first goals. Our guest is Chris Butcher, Platform Architect, Global Networks, Cloud and Perimeter Security at Cushman & Wakefield.Tech Bytes: Cushman & Wakefield Taps Silver Peak SD-WAN For Cloud-First Goals (Sponsored)
On today's Tech Bytes podcast, sponsored by Silver Peak, we talk with Cushman & Wakefield about how the global real estate company is using SD-WAN to enable its cloud-first goals. Our guest is Chris Butcher, Platform Architect, Global Networks, Cloud and Perimeter Security at Cushman & Wakefield.
The post Tech Bytes: Cushman & Wakefield Taps Silver Peak SD-WAN For Cloud-First Goals (Sponsored) appeared first on Packet Pushers.
The Week in Internet News: Mexico, NYC Push for Internet Access for All

Everyone’s invited: Politicians in Mexico and New York City announced plans for universal Internet access in recent days. Mexican President Andres Manuel Lopez Obrador announced a plan to bring access to the large swaths of the country that don’t have it, including a government investment of more than $500,000, according to AA News. Meanwhile, New York City Major Bill de Blasio is pushing an “Internet master plan” to improve access. About 18 percent of the city’s residents have neither mobile nor home Internet connections, and about 40 percent have one or the other, but not both, the New York Daily News reports.
New pressure campaign: The U.S. FBI is asking Apple for help to access encrypted communications on an iPhone that belonged to the Saudi military student who killed three people last month at a naval base in Pensacola, Fla., the Washington Post reports. It’s unclear what information the FBI is looking for, given that the shooter is dead, but the request is a new step in the long-running fight between the U.S. government and large tech vendors over the use of encryption on smartphones and other devices.
Cyber retaliation: Many cybersecurity experts expect Iran to retaliate with cyberattacks Continue reading
Dictionary: Human Permafrost

What is Human Permafrost in IT Infrastructure ?
The post Dictionary: Human Permafrost appeared first on EtherealMind.
AWS Rarely Kills a Service. What About Your Vendor?
Here’s an interesting tidbit from “Last Week in AWS” blog:
From a philosophical point of view, AWS fundamentally considers an API to be a promise. Services that aren’t promoted anymore are still available […] Think about that for a second - a service launched 13 years ago is still actively supported to the point where you can use it today.
Compare that to Killed By Google graveyard, and you might understand why I’m a bit reluctant to cover GCP in my webinars.
Read more ...Helping mitigate the Citrix NetScaler CVE with Cloudflare Access
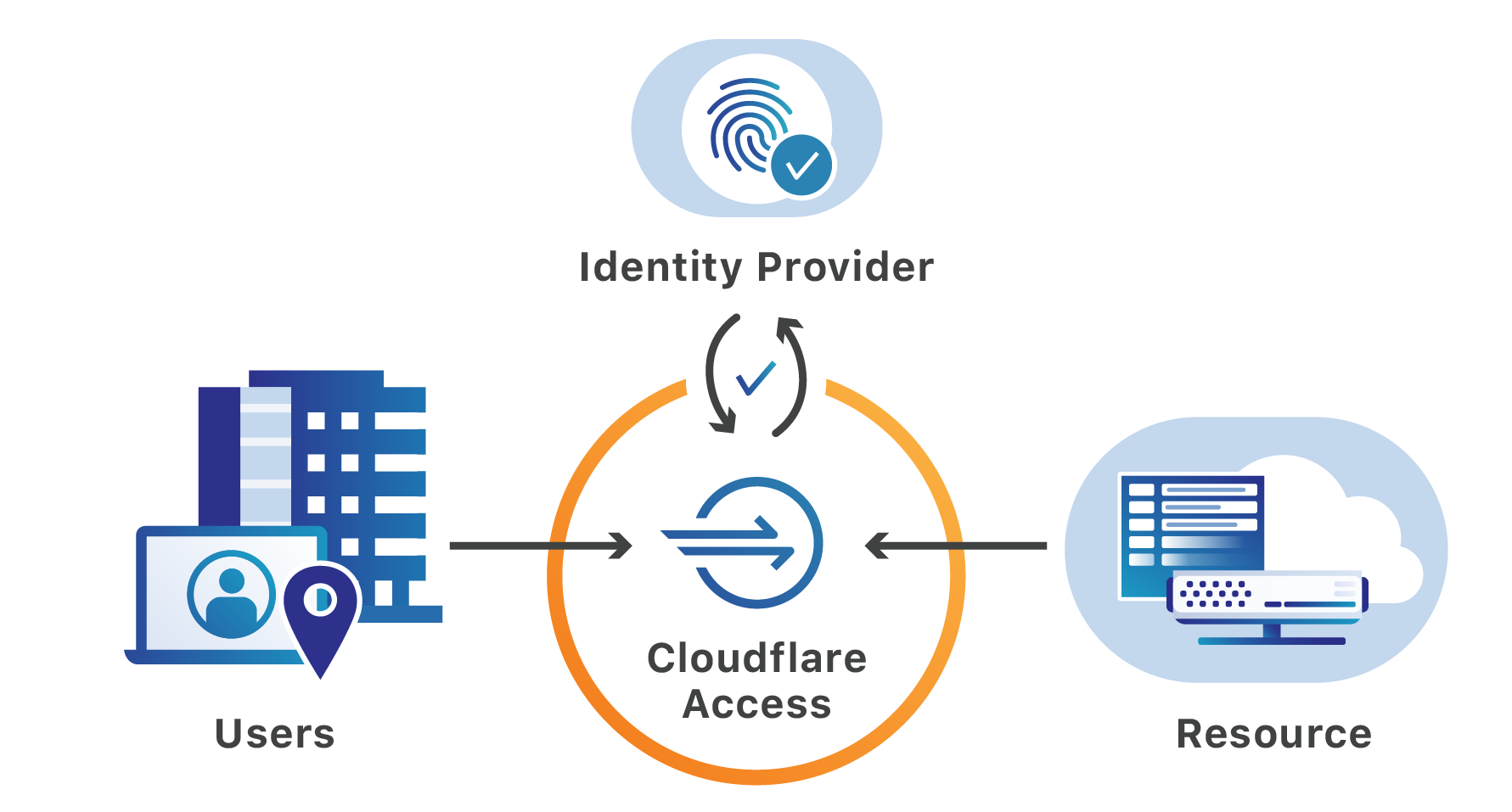
Yesterday, Citrix sent an updated notification to customers warning of a vulnerability in their Application Delivery Controller (ADC) product. If exploited, malicious attackers can bypass the login page of the administrator portal, without authentication, to perform arbitrary code execution.
No patch is available yet. Citrix expects to have a fix for certain versions on January 20 and others at the end of the month.
In the interim, Citrix has asked customers to attempt to mitigate the vulnerability. The recommended steps involve running a number of commands from an administrator command line interface.
The vulnerability relied on by attackers requires that they first be able to reach a login portal hosted by the ADC. Cloudflare can help teams secure that page and the resources protected by the ADC. Teams can place the login page, as well as the administration interface, behind Cloudflare Access’ identity proxy to prevent unauthenticated users from making requests to the portal.
Exploiting URL paths
Citrix ADC, also known as Citrix NetScaler, is an application delivery controller that provides Layer 3 through Layer 7 security for applications and APIs. Once deployed, administrators manage the installation of the ADC through a portal available at a dedicated URL on Continue reading
VXLAN Book Errata 12-January 2020
Continue reading
Must Read: Ironies of Automation
Stumbled upon a 35-year-old article describing the ironies of automation (HT: The Morning Paper). Here’s a teaser…
Unfortunately automatic control can ‘camouflage’ system failure by controlling against the variable changes, so that trends do not become apparent until they are beyond control.
In simpler words: when things fail, they fail really badly because the intermittent failures were kept hidden. Keep that in mind the next time someone tells you how wonderful software-defined AI-assisted networking is going to be.
Junos SNMP via Routing Instance
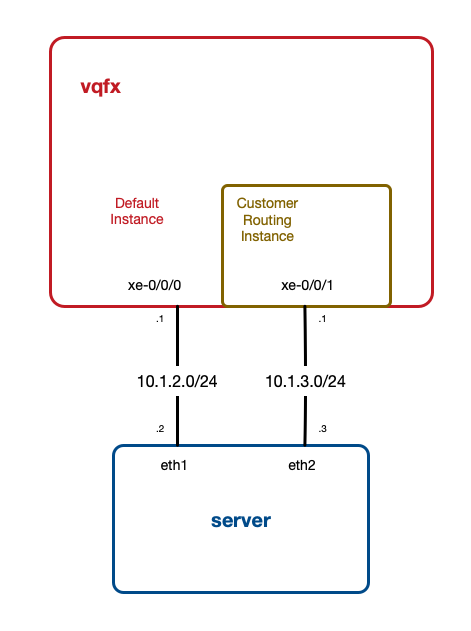
Juniper routing instances are very useful when you need separate routing tables on the one device, for example to separate customers. Junos lets you configure SNMP polling of routing instances, so customers can poll “their” interfaces using 'instance_name'@'community'. All very useful. But it wasn’t obvious to me how to poll the default table via an interface in a routing instance. The trick is to just use @'community'. Here’s an example.
Network Overview
To demo this I have a simple network. I’m using a Virtual QFX plus Vagrant setup, based on the Vagrantfiles in this repo. I’m running one vqfx10k, connected to one server. The key here is that the server has two connections to the vqfx. One interface is in the default instance, one is in a “Customer” routing instance:
Here’s the routing-instance config:
1
2
3
4
5
6
7
8
vagrant@vqfx> show configuration routing-instances
Customer {
instance-type virtual-router;
interface xe-0/0/1.0;
}
{master:0}
vagrant@vqfx>
And here’s my SNMP configuration:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
vagrant@vqfx> Continue reading