Unlock Your Full Network Monitoring Flow Potential
Traditionally, network monitoring software was designed to act in isolation, limited to features...
New tools to monitor your server and avoid downtime

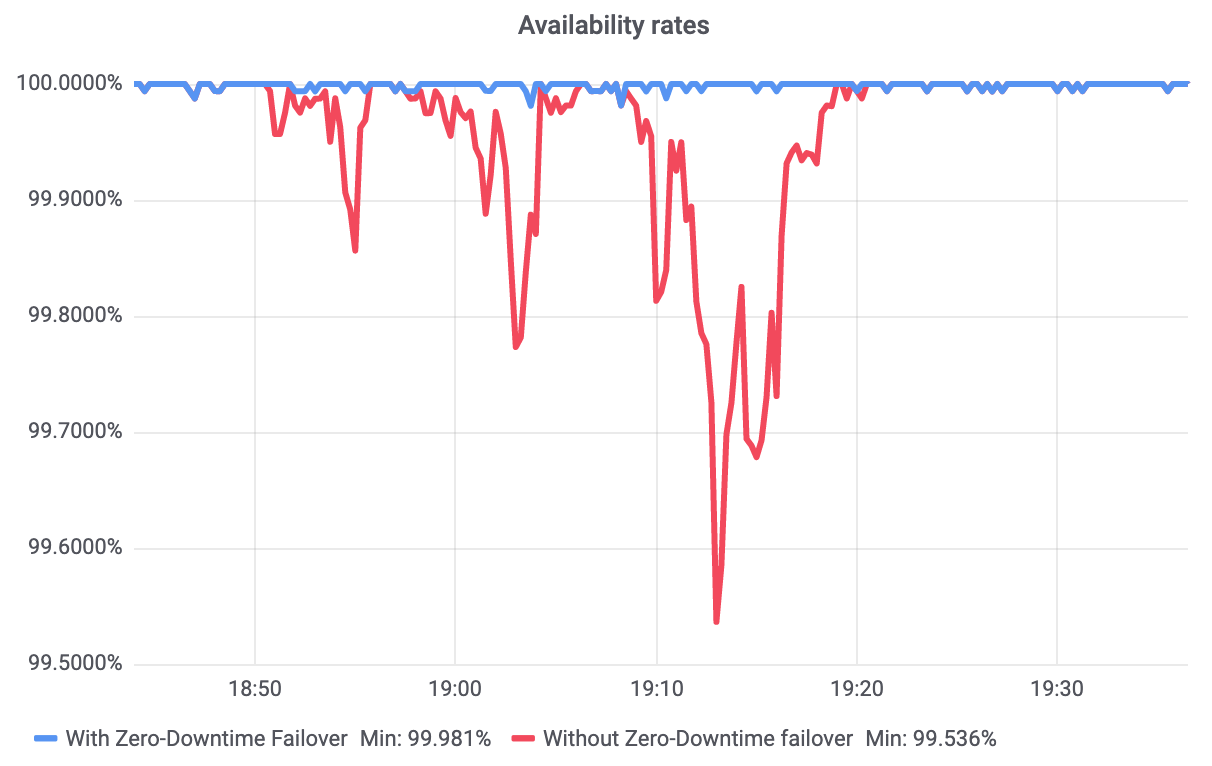
When your server goes down, it’s a big problem. Today, Cloudflare is introducing two new tools to help you understand and respond faster to origin downtime — plus, a new service to automatically avoid downtime.
The new features are:
- Standalone Health Checks, which notify you as soon as we detect problems at your origin server, without needing a Cloudflare Load Balancer.
- Passive Origin Monitoring, which lets you know when your origin cannot be reached, with no configuration required.
- Zero-Downtime Failover, which can automatically avert failures by retrying requests to origin.
Standalone Health Checks
Our first new tool is Standalone Health Checks, which will notify you as soon as we detect problems at your origin server -- without needing a Cloudflare Load Balancer.
A Health Check is a service that runs on our edge network to monitor whether your origin server is online. Health Checks are a key part of our load balancing service because they allow us to quickly and actively route traffic to origin servers that are live and ready to serve requests. Standalone Health Checks allow you to monitor the health of your origin even if you only have one origin or do not yet Continue reading
Practice Your Public Cloud Networking with Hands-On Exercises
Design assignments and hands-on exercises were always a big part of ipSpace.net online courses, and our new Networking in Public Cloud Deployments course is no different.
You’ll start with a simple scenario: deploy a virtual machine running a web server. Don’t worry about your Linux skills, you’ll get the necessary (CCIE-level) instructions and the source code for the web server. Building on that, you’ll create another subnet and deploy another virtual machine acting as a back-end application server.
And then we’ll get to the fun part:
Read more ...Open Source Flow Monitoring and Visualization
At the heart of any reasonably sized network, should be a solid strategy around flow collection, querying and visualization. Proper use of flow logs are crucial to SecOps/NetOps from triaging attacks to capacity planning and traffic trending. I remember some 20 years ago, the first time I saw flow logs being visualized in rrdtools it was pretty close to magic. ... The post Open Source Flow Monitoring and Visualization appeared first on NetworkStatic | Brent Salisbury's Blog....
Kubernetes Integrates Interoperability, Storage, Waits on Sidecars
A recent Datadog report found that 45% of its customers were running containers on Kubernetes and...
Aryaka SD-WAN Joins Azure App Gallery, Pens Energy Deal
The MyAryaka cloud portal is now available in the Microsoft Azure Active Directory Application...
Network inventory: what do you have, and should it be there?
How do you defend what you don’t know exists? In IT, this is more than just an existential question, or fuel for a philosophical debate. The existence of a complete network inventory—or the lack thereof—has a real-world impact on an organization’s ability to secure their network. Establishing and maintaining a network inventory is both a technological and a business process problem, and serves as an excellent example of the importance of open standards to a modern organization.
Consider for a moment NASA’s Jet Propulsion Laboratory (JPL). In April 2018 the JPL experienced a cybersecurity event. Upon investigation, it was determined that this was caused by someone smuggling an unauthorized Raspberry Pi onto the premises and connecting it to the network.
This incident triggered a security audit, and the results of that June 2019 report were, though not unexpected, still rather disappointing. The auditors’ biggest concern was that the JPL didn’t have a comprehensive, accurate picture of what devices were on its networks, nor did it know whether or not those devices were authorized to be there.
This lack of an up-to-date and automated network inventory led to a successful hack of the JPL via the unauthorized Raspberry Pi. Some Continue reading
Nutanix and HPE Deliver Integrated Hyperconverged Infrastructure Appliance
In April 2019, Nutanix and HPE announced a new global partnership to bring to market an...
Eclipse Foundation Warns Operators: Don’t Be a ‘Dumb Pipe’ for AWS
"This is the opportunity for the carriers to step away from just being data pipes and actually...
Microsoft, NTT Tap Azure, AI to Target Enterprises
The alliance also makes Microsoft’s Azure NTT’s preferred cloud platform for modernizing its...
IBM Security Gives Cloud Identity an AI Boost
IBM Cloud Identity now uses adaptive access capabilities to continually assess employee or consumer...