Enhance your website’s security with Cloudflare’s free security.txt generator
Meet Georgia, a diligent website administrator at a growing e-commerce company. Every day, Georgia juggles multiple tasks, from managing server uptime to ensuring customer data security. One morning, Georgia receives an email from a security researcher who discovered a potential vulnerability on the website. The researcher struggled to find the right contact information, leading to delays in reporting the issue. Georgia realizes the need for a standardized way to communicate with security researchers, ensuring that vulnerabilities are reported swiftly and efficiently. This is where security.txt comes in.
Security.txt is becoming a widely adopted standard among security-conscious organizations. By providing a common location and format for vulnerability disclosure information, it helps bridge the gap between security researchers and organizations. This initiative is supported by major companies and aligns with global security best practices. By offering an automated security.txt generator for free, we aim to empower all of our users to enhance their security measures without additional costs.
In 2020, Cloudflare published the Cloudflare Worker for the security.txt generator as an open-source project on GitHub, demonstrating our commitment to enhancing web security. This tool is actively used Continue reading
Auto Scaling Palo Alto VM-Series Firewalls in AWS

In this blog post, we're going to explore how to Auto-Scale Palo Alto VM-Series Firewalls in AWS. It's a known fact that running heavy instances in AWS can be costly, and it's not wise to have more firewalls running than necessary. But what happens when demand spikes unexpectedly? If we're not prepared, things can get messy quickly.
Auto-scaling these firewalls isn't as simple as pressing a button. There are several components to consider, but don't worry - once you grasp the basics, it's as straightforward as any other topic in the cloud and network world.
This blog post is based on the ideas from the Palo Alto Github repo - https://github.com/PaloAltoNetworks/terraform-aws-vmseries-modules/tree/main/examples/centralized_design_autoscale
Assumptions
As we get into the specifics of auto-scaling Palo Alto VM-Series firewalls in AWS, there are a few assumptions I'd like to lay out. This Continue reading
Adding Palo Alto PA-440 to My Home Lab

When I started my home lab, I used a Raspberry Pi 4 that functioned as a router/firewall, and I was pretty happy with it. Then, I needed something solid and cost-effective. There were multiple options like VyOS, PfSense, UniFi, etc, but MikroTik, specifically the hAP ax2, stood out for me. I've been using this for almost a year now, and I absolutely love it. It works as a switch, and firewall and runs my WireGuard VPN, and it has never let me down even once.
Why Palo Alto?
Fast forward to today, I started adding more and more devices to the lab, so I was looking for an upgrade. After debating between FortiGate and Palo Alto, I finally settled on buying a Palo Alto PA-440 firewall.

But I would say the main reason behind this decision is that I write a lot of content on Palo Alto, and not having a dedicated device was such a pain. Every time I wanted to write a post, I had to start the lab, and try things out, and not having licenses was preventing me from trying new features and sharing them via a post. Now, with a dedicated unit and Continue reading
HN752: How Digital Twins Enable Smarter Network Ops, Troubleshooting (Sponsored)
Our topic today is digital twins. Sponsor Forward Networks offers software that creates a “mathematically accurate” copy of your network, be it on prem or in the cloud. We talk about what “mathematically accurate” actually means, and how a digital twin can support network operations including change control, network automation, visibility, and troubleshooting. We also... Read more »TNO004: DevOps, NetOps, and Batman – Part 2
Guest Tom McGonagle, the creator of GitNops, is back with host Scott Robohn for part two of their GitNops discussion. They continue their conversation about the principles and applications of GitNops in network operations, including automated testing, the collaborative role of GitHub, and the challenges of ensuring accurate configurations before deployment. Finally, they explore the... Read more »BGP Labs: Improvements (September 2024)
I spent a few days in a beautiful place with suboptimal Internet connectivity. The only thing I could do whenever I got bored (without waiting for the Internet gnomes to hand-carry the packets across the mountain passes) was to fix the BGP labs on a Ubuntu VM running on my MacBook Air (hint: it all works).
Big things first. I added validation to these labs:
Managing Palo Alto App-ID Changes Using Threat Signature Indicators (TSID)

If you rely heavily on Palo Alto App-IDs, you know the challenge of managing new and modified App-IDs. Palo Alto regularly updates its App-ID database, introducing new App-IDs every month (typically on the third Tuesday) and modifying existing ones more often.
Each release can include hundreds of new and updated App-IDs. It's almost impossible to understand each of them and decide whether or not we are affected by the change. In this blog post, we will look at using Threat Signature Indicators (TSID) to help you get an advanced indication of any impact on your traffic as a result of upcoming App-ID changes.
The Problem with App-ID Changes
Let’s imagine for a moment that currently, Palo Alto doesn’t have a specific App-ID for ‘chatgpt’ (although they do, let’s assume they don’t for this example). If there isn’t an App-ID, the traffic would be identified as ‘ssl’. If Palo Alto decides to introduce a new App-ID for ‘chatgpt’, they will announce this in the new App-ID release notes. However, the challenge is that hundreds of other new App-IDs could be introduced at the same time that we might never have heard of.
So, when I go to Continue reading
IPB161: Compressing the IPv6 Deployment Timeline
In this episode we discuss the complexities of deploying IPv6 on a compressed timeline. We cover the need for careful planning, training, and understanding the protocol’s nuances. The conversation looks at the risks of delaying deployment, the benefits of incremental implementation, and the global momentum towards IPv6 adoption. Misconceptions about IPv6 are addressed, stressing that... Read more »Hedge 245: RADIUS and Authentication
RADIUS is one of those protocols we tend to forget about because it is ubiquitous–but authentication protocols are very large attack surfaces network engineers should pay more attention to. Alan DeKok joins Tom Ammon and Russ White to discuss the RADIUS protocol.
D2DO252: (Re)Building Cloudflare’s Millions-of-Logs-Per-Second Logging Pipeline
Cloudflare’s transition from SysLog-NG to OpenTelemetry is the topic of discussion on this episode of Day Two DevOps. Guests Colin Douch and Jayson Cena from Cloudflare explain the reasons behind the migration, including the need for better scalability, memory safety, and maintainability. They delve into challenges such as ensuring uninterrupted customer traffic and optimizing performance.... Read more »How Cloudflare auto-mitigated world record 3.8 Tbps DDoS attack
Since early September, Cloudflare's DDoS protection systems have been combating a month-long campaign of hyper-volumetric L3/4 DDoS attacks. Cloudflare’s defenses mitigated over one hundred hyper-volumetric L3/4 DDoS attacks throughout the month, with many exceeding 2 billion packets per second (Bpps) and 3 terabits per second (Tbps). The largest attack peaked 3.8 Tbps — the largest ever disclosed publicly by any organization. Detection and mitigation was fully autonomous. The graphs below represent two separate attack events that targeted the same Cloudflare customer and were mitigated autonomously.
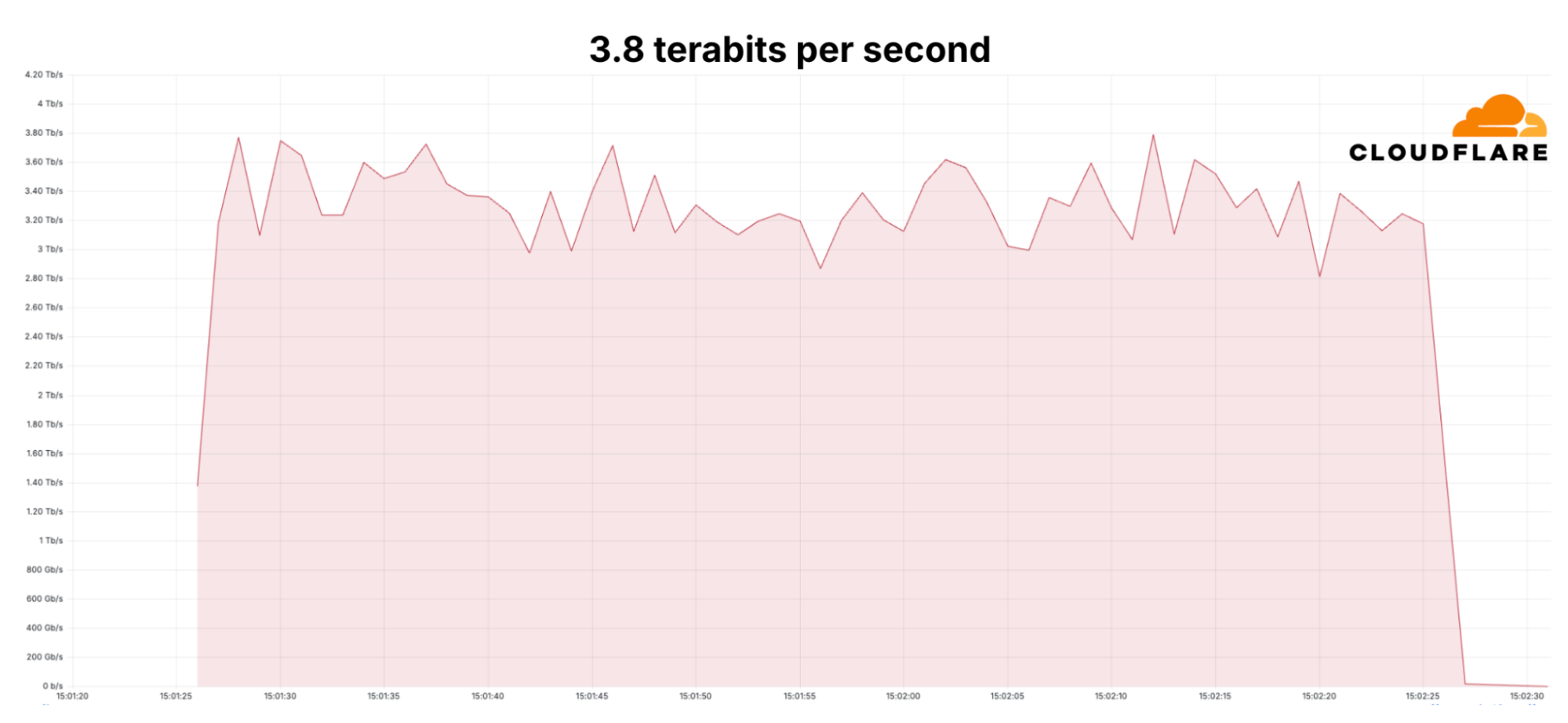
A mitigated 3.8 Terabits per second DDoS attack that lasted 65 seconds
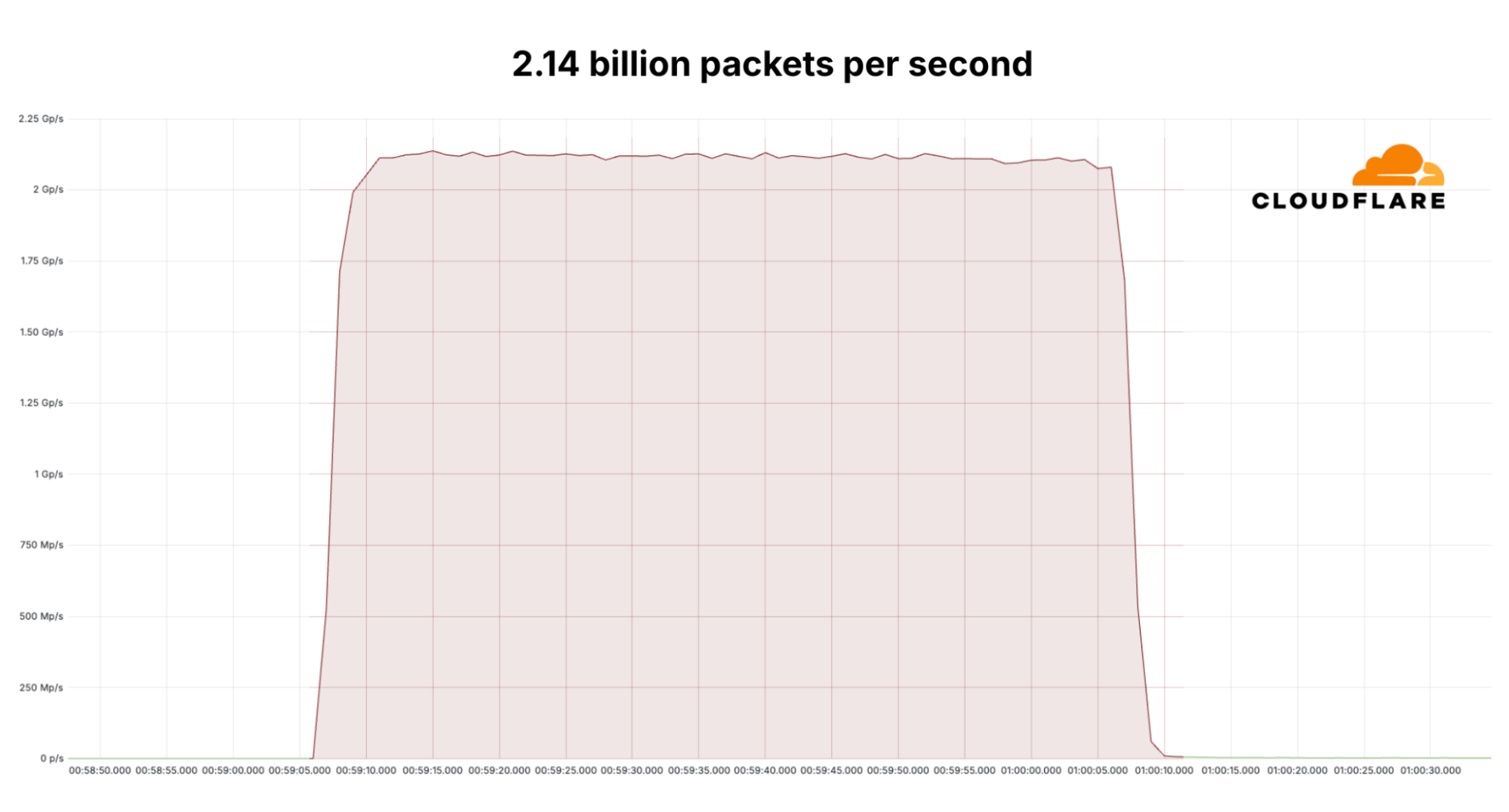
A mitigated 2.14 billion packet per second DDoS attack that lasted 60 seconds
Cloudflare customers are protected
Cloudflare customers using Cloudflare’s HTTP reverse proxy services (e.g. Cloudflare WAF and Cloudflare CDN) are automatically protected.
Cloudflare customers using Spectrum and Magic Transit are also automatically protected. Magic Transit customers can further optimize their protection by deploying Magic Firewall rules to enforce a strict positive and negative security model at the packet layer.
Other Internet properties may not be safe
The scale and frequency of these attacks are unprecedented. Due to their sheer size and bits/packets per second rates, these Continue reading
Patent troll Sable pays up, dedicates all its patents to the public!
Back in February, we celebrated our victory at trial in the U.S. District Court for the Western District of Texas against patent trolls Sable IP and Sable Networks. This was the culmination of nearly three years of litigation against Sable, but it wasn’t the end of the story.
Today we’re pleased to announce that the litigation against Sable has finally concluded on terms that we believe send a strong message to patent trolls everywhere — if you bring meritless patent claims against Cloudflare, we will fight back and we will win.
We’re also pleased to announce additional prizes in Project Jengo, and to make a final call for submissions before we determine the winners of the Final Awards. As a reminder, Project Jengo is Cloudflare’s effort to fight back against patent trolls by flipping the incentive structure that has encouraged the growth of patent trolls who extract settlements out of companies using frivolous lawsuits. We do this by asking the public to help identify prior art that can invalidate any of the patents that a troll holds, not just the ones that are asserted against Cloudflare. We’ve already given out over $125,000 to individuals since the launch Continue reading
How XtendISE Helps with 802.1X Management in ISE?

XtendISE is a simple web application connected to your Cisco ISE, which helps with everyday routine tasks and common challenges related to 802.1X without the need to train everyone in Cisco ISE. XtendISE can help you manage MAC addresses and troubleshoot 802.1X authentications. It also helps with managing the switch's 802.1x configuration or validating the configurations to make sure that they are configured as intended.
All the mentioned features save time for us Network Engineers and help us to do our job efficiently as we do not waste our time on routine tasks. It also increases network security because it makes sure that our network is configured correctly and thus is safe and secured.
What Company Is XtendISE Intended For?
XtendISE is suitable for a company of any size with Cisco ISE and Cisco network devices. However medium or large companies will better use XtendISE features because they are more likely affected by the mentioned problems.
XtendISE helps the Helpdesk or IT Support with
- Easy to use MAC address management and troubleshooting
- They save time and there is no need for extra knowledge on ISE
- They can manage switch port configurations
- They do not Continue reading
HW037: Is Wi-Fi 7 the Game Changer We’ve Been Waiting For?
Wi-Fi 7 brings new features and capabilities to the market, including Multi-Link Operation (MLO) and airtime optimization, which can enhance throughput and reduce latency. In today’s episode of Heavy Wireless, host Keith Parsons and guest Phil Morgan explore the advancements and practical implications of Wi-Fi 7. Phil shares his experiences testing Wi-Fi 7 with various... Read more »PP033: AI and Machine Learning 101 for Cybersecurity
The terms “AI” and “machine learning (ML)” get thrown around pretty regularly in IT and cybersecurity. On today’s Packet Protector we get an introduction to AI and ML to help you ask the right questions when vendors tout their latest AI-infused products. Our guest is Jeff Crume, a distinguished engineer and cybersecurity architect at IBM.... Read more »HS084: Straight Talk from Cisco’s CIO (Sponsored)
Cisco CIO Fletcher Previn visits Heavy Strategy to talk about how to create a technology culture, what it’s like being “customer zero”, and other challenges and tribulations of running IT from inside one of the world’s largest tech companies. Episode Guest: Fletcher Previn, SVP & Chief Information Officer, Cisco Fletcher Previn has over two decades... Read more »Dell Optiplex 7050 SFF Upgrade for Proxmox
The Dell OptiPlex 7050 SFF is a capable machine for virtualization thanks to its Intel […]
The post Dell Optiplex 7050 SFF Upgrade for Proxmox first appeared on Brezular's Blog.
NB497: Blocking AI Scraper Bots; HPE, Arista Reach for Bigger Slices of the Enterprise
Take a Network Break! This week we discuss significant vulnerabilities in HPE APs and Cisco Catalyst 9K switches, the benefits of bug bounties, how HPE is adding third-party device monitoring to Aruba Central, and whether Arista can succeed at positioning CloudVision as a management platform for enterprise data center, campus, and WAN environments. Alkira’s cloud... Read more »Repost: Layer-3-Only EVPN Behind the Scenes
After publishing the EVPN L3VPN lab-building instructions, I published a deep dive into EVPN and data-plane data structures. You might have missed it, as it was published in mid-August.
Impact of Verizon’s September 30 outage on Internet traffic
On Monday, September 30, customers on Verizon’s mobile network in multiple cities across the United States reported experiencing a loss of connectivity. Impacted phones showed “SOS” instead of the usual bar-based signal strength indicator, and customers complained of an inability to make or receive calls on their mobile devices.
AS6167 (CELLCO) is the autonomous system used by Verizon for its mobile network. To better understand how the outage impacted Internet traffic on Verizon’s network, we took a look at HTTP request volume from AS6167 independent of geography, as well as traffic from AS6167 in various cities that were reported to be the most significantly impacted.
Although initial reports of connectivity problems started around 09:00 ET (13:00 UTC), we didn’t see a noticeable change in request volume at an ASN level until about two hours later. Just before 12:00 ET (16:00 UTC), Verizon published a social media post acknowledging the problem, stating “We are aware of an issue impacting service for some customers. Our engineers are engaged and we are working quickly to identify and solve the issue.”
As the Cloudflare Radar graph below shows, a slight decline (-5%) in HTTP traffic as compared to traffic at the Continue reading
