HS083: Why Protocols Fail: Russ White’s Perspective on Effective Architecture
Network veteran Russ White joins the Heavy Strategy team for a rousing discussion on why protocols fail, how much complexity is too much, why “premature optimization is the root of all evil” (Donald Knuth) and why architects should always remember to think about state. Episode Guest: Russ White, Senior Architect, Akamai Technologies For the last... Read more »Semper Gumby

By now I’m sure you’re familiar with Murphy’s Law: “Anything that can go wrong will go wrong.” If you work in IT or events or even in a trade you’ve seen things go upside down on many occasions. Did you ever ask yourself why this happens? Or even what you can do to fix it? What about avoiding it completely?
I have done a lot in IT over the years. I’ve also been working hard as an event planner and coordinator with Tech Field Day. The best lessons that I’ve learned about anticipating disaster have come from my time in Scouting. I’m often asked by companies “how did you know that would happen?” I almost always answer the same way: “I didn’t know THAT would go wrong, but I knew something would. I just kept my eye out for it.” It almost sounds too simple, right? But if you are familiar with event planning you know it’s almost a law, just like Mr. Murphy’s famous version.
How can you anticipate problems and still manage to make things happen? You can’t always fix everything. However, you can make sure that people don’t notice the issues. You just have Continue reading
Cloudflare helps verify the security of end-to-end encrypted messages by auditing key transparency for WhatsApp
Chances are good that today you’ve sent a message through an end-to-end encrypted (E2EE) messaging app such as WhatsApp, Signal, or iMessage. While we often take the privacy of these conversations for granted, they in fact rely on decades of research, testing, and standardization efforts, the foundation of which is a public-private key exchange. There is, however, an oft-overlooked implicit trust inherent in this model: that the messaging app infrastructure is distributing the public keys of all of its users correctly.
Here’s an example: if Joe and Alice are messaging each other on WhatsApp, Joe uses Alice’s phone number to retrieve Alice’s public key from the WhatsApp database, and Alice receives Joe’s public key. Their messages are then encrypted using this key exchange, so that no one — even WhatsApp — can see the contents of their messages besides Alice and Joe themselves. However, in the unlikely situation where an attacker, Bob, manages to register a different public key in WhatsApp’s database, Joe would try to message Alice but unknowingly be messaging Bob instead. And while this threat is most salient for journalists, activists, and those most vulnerable to cyber attacks, we believe that protecting the privacy and integrity of Continue reading
Automatically generating Cloudflare’s Terraform provider
In November 2022, we announced the transition to OpenAPI Schemas for the Cloudflare API. Back then, we had an audacious goal to make the OpenAPI schemas the source of truth for our SDK ecosystem and reference documentation. During 2024’s Developer Week, we backed this up by announcing that our SDK libraries are now automatically generated from these OpenAPI schemas. Today, we’re excited to announce the latest pieces of the ecosystem to now be automatically generated — the Terraform provider and API reference documentation.
This means that the moment a new feature or attribute is added to our products and the team documents it, you’ll be able to see how it’s meant to be used across our SDK ecosystem and make use of it immediately. No more delays. No more lacking coverage of API endpoints.
You can find the new documentation site at https://developers.cloudflare.com/api-next/, and you can try the preview release candidate of the Terraform provider by installing 5.0.0-alpha1.
Why Terraform?
For anyone who is unfamiliar with Terraform, it is a tool for managing your infrastructure as code, much like you would with your application code. Many of our customers (big and small) rely Continue reading
Cloudflare partners with Internet Service Providers and network equipment providers to deliver a safer browsing experience to millions of homes
A committed journey of privacy and security
In 2018, Cloudflare announced 1.1.1.1, one of the fastest, privacy-first consumer DNS services. 1.1.1.1 was the first consumer product Cloudflare ever launched, focused on reaching a wider audience. This service was designed to be fast and private, and does not retain information that would identify who is making a request.
In 2020, Cloudflare announced 1.1.1.1 for Families, designed to add a layer of protection to our existing 1.1.1.1 public resolver. The intent behind this product was to provide consumers, namely families, the ability to add a security and adult content filter to block unsuspecting users from accessing specific sites when browsing the Internet.
Today, we are officially announcing that any ISP and equipment manufacturer can use our DNS resolvers for free. Internet service, network, and hardware equipment providers can sign up and join this program to partner with Cloudflare to deliver a safer browsing experience that is easy to use, industry leading, and at no cost to anyone.
Leading companies have already partnered with Cloudflare to deliver superior and customized offerings to protect their customers. By delivering this service Continue reading
A safer Internet with Cloudflare: free threat intelligence, analytics, and new threat detections
Anyone using the Internet likely touches Cloudflare’s network on a daily basis, either by accessing a site protected by Cloudflare, using our 1.1.1.1 resolver, or connecting via a network using our Cloudflare One products.
This puts Cloudflare in a position of great responsibility to make the Internet safer for billions of users worldwide. Today we are providing threat intelligence and more than 10 new security features for free to all of our customers. Whether you are using Cloudflare to protect your website, your home network, or your office, you will find something useful that you can start using with just a few clicks.
These features are focused around some of the largest growing concerns in cybersecurity, including account takeover attacks, supply chain attacks, attacks against API endpoints, network visibility, and data leaks from your network.
More security for everyone
You can read more about each one of these features in the sections below, but we wanted to provide a short summary upfront.
If you are a cyber security enthusiast: you can head over to our new Cloudforce One threat intelligence website to find out about threat actors, attack campaigns, and other Internet-wide Continue reading
CloudVision: The First Decade
As I think about the evolution of the CloudVisionⓇ platform over the last 10 years, and our latest announcement today, I’m reminded of three principles that have guided us along our journey: full network data without compromise, platform over point product, and a modern operating model. While the product and our plans have evolved over the years, each of these principles feels incredibly relevant to the problems facing enterprises today.
One-Arm Hub-and-Spoke VPN with MPLS/VPN
All our previous designs of the hub-and-spoke VPN (single PE, EVPN) used two VRFs for the hub device (ingress VRF and egress VRF). Is it possible to build a one-arm hub-and-spoke VPN where the hub device exchanges traffic with the PE router over a single link?
TL&DR: Yes, but only on some devices (for example, Cisco IOS or FRRouting) when using MPLS transport.
Here’s a high-level diagram of what we’d like to achieve:
Tech Bytes: Reduce GenAI App Risks Without Reducing Productivity (Sponsored)
Today on the Tech Bytes podcast we talk about GenAI apps. From search to software development to video creation, Generative AI tools are widely available as standalone apps and are being bundled into enterprise applications. Whether you want them or not, GenAI apps are out there and running wild. On today’s show, sponsored by Palo... Read more »NB496: Nokia’s Enterprise Data Center Intentions; Are AI ChatBots Worth the Nuclear Waste?
Take a Network Break! This week we discuss Microsoft’s proposed deal to buy power from the Three Mile Island nuclear plant, new APs and switches from Juniper Networks, and T-Mobile landing a customer driven by the network slicing capabilities of 5G. China disbands a botnet, Nokia takes on data center switch giants with a new... Read more »Making zone management more efficient with batch DNS record updates
Customers that use Cloudflare to manage their DNS often need to create a whole batch of records, enable proxying on many records, update many records to point to a new target at the same time, or even delete all of their records. Historically, customers had to resort to bespoke scripts to make these changes, which came with their own set of issues. In response to customer demand, we are excited to announce support for batched API calls to the DNS records API starting today. This lets customers make large changes to their zones much more efficiently than before. Whether sending a POST, PUT, PATCH or DELETE, users can now execute these four different HTTP methods, and multiple HTTP requests all at the same time.
Efficient zone management matters
DNS records are an essential part of most web applications and websites, and they serve many different purposes. The most common use case for a DNS record is to have a hostname point to an IPv4 address, this is called an A record:
example.com 59 IN A 198.51.100.0
blog.example.com 59 IN A 198.51.100.1
ask.example.com 59 IN A 198.51. Continue reading
Network performance update: Birthday Week 2024
When it comes to the Internet, everyone wants to be the fastest. At Cloudflare, we’re no different. We want to be the fastest network in the world, and are constantly working towards that goal. Since June 2021, we’ve been measuring and ranking our network performance against the top global networks. We use this data to improve our performance, and to share the results of those initiatives.
In this post, we’re going to share with you how our network performance has changed since our last post in March 2024, and discuss the tools and processes we are using to assess network performance.
Digging into the data
Cloudflare has been measuring network performance across these top networks from the top 1,000 ISPs by estimated population (according to the Asia Pacific Network Information Centre (APNIC)), and optimizing our network for ISPs and countries where we see opportunities to improve. For performance benchmarking, we look at TCP connection time. This is the time it takes an end user to connect to the website or endpoint they are trying to reach. We chose this metric to show how our network helps make your websites faster by serving your traffic where Continue reading
Introducing Ephemeral IDs: a new tool for fraud detection
In the early days of the Internet, a single IP address was a reliable indicator of a single user. However, today’s Internet is more complex. Shared IP addresses are now common, with users connecting via mobile IP address pools, VPNs, or behind CGNAT (Carrier Grade Network Address Translation). This makes relying on IP addresses alone a weak method to combat modern threats like automated attacks and fraudulent activity. Additionally, many Internet users have no option but to use an IP address which they don’t have sole control over, and as such, should not be penalized for that.
At Cloudflare, we are solving this complexity with Turnstile, our CAPTCHA alternative. And now, we’re taking the next step in advancing security with Ephemeral IDs, a new feature that generates a unique short-lived ID, without relying on any network-level information.
When a website visitor interacts with Turnstile, we now calculate an Ephemeral ID that can link behavior to a specific client instead of an IP address. This means that even when attackers rotate through large pools of IP addresses, we can still identify and block malicious actions. For example, in attacks like credential stuffing or account signups, where fraudsters attempt to disguise Continue reading
Start auditing and controlling the AI models accessing your content
Site owners have lacked the ability to determine how AI services use their content for training or other purposes. Today, Cloudflare is releasing a set of tools to make it easy for site owners, creators, and publishers to take back control over how their content is made available to AI-related bots and crawlers. All Cloudflare customers can now audit and control how AI models access the content on their site.
This launch starts with a detailed analytics view of the AI services that crawl your site and the specific content they access. Customers can review activity by AI provider, by type of bot, and which sections of their site are most popular. This data is available to every site on Cloudflare and does not require any configuration.
We expect that this new level of visibility will prompt teams to make a decision about their exposure to AI crawlers. To help give them time to make that decision, Cloudflare now provides a one-click option in our dashboard to immediately block any AI crawlers from accessing any site. Teams can then use this “pause” to decide if they want to allow specific AI providers or types of bots to proceed. Once that Continue reading
Egress Peer Engineering: basics
Egress Peer Engineering extends regular BGP policies to provide more flexibility.
Why use Egress Peer Engineering
When a network operator has multiple external connections, such as IP transit, private peerings or Internet Exchange (IXP), there is often a need to …
NAT Overload Towards Specific Host
This is a quick post on how to perform NAT overload (PAT) towards a specific host only. I have an inside network of 10.10.1.0/24. I need a host in this network to reach the host 192.168.0.1. They don’t have direct connectivity so I need to PAT it behind the router which has an IP of 192.168.128.103. I don’t want to PAT all the traffic from 10.10.1.0/24, though, only towards this specific host. There are hosts in 192.168.128.0/24 that the VM should access using its original source. The network is shown in the diagram below:
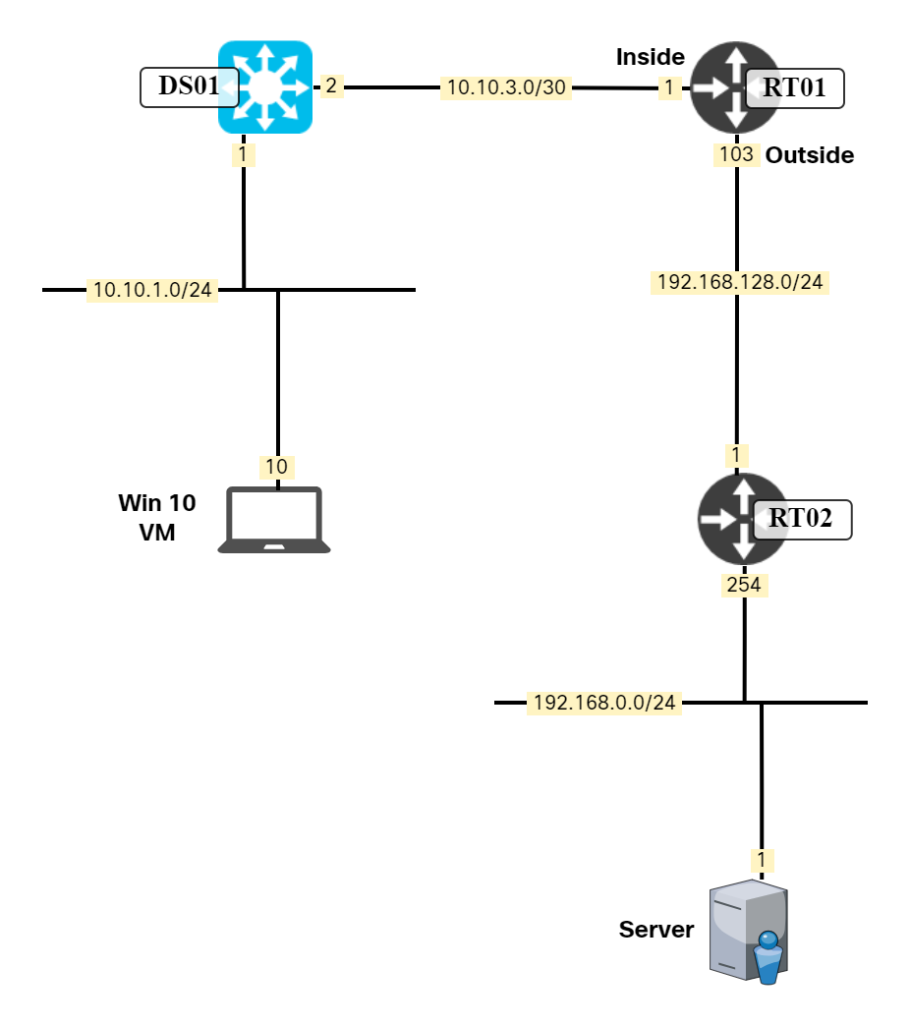
First, I’ll define my inside and outside interface:
RT01(config)#int gi0/0 RT01(config-if)#ip nat inside RT01(config-if)#int gi0/1 RT01(config-if)#ip nat outside
Then I’m going to create the ACL that matches on traffic from the 10.10.1.0/24 network to the host 192.168.0.1:
RT01(config)#ip access-list extended NAT-SRC-10.10.2.0/24 RT01(config-ext-nacl)#permit ip 10.10.2.0 0.0.255.255 host 192.168.0.1
Then, I’ll configure the NAT statement to match on the ACL and do an overload to interface Gi0/1:
RT01(config)#ip nat inside source list NAT-SRC-10.10.2. Continue reading
IBGP Load Balancing with BGP Link Bandwidth
In the previous BGP load balancing lab exercise, I described the BGP Link Bandwidth attribute and how you can use it on EBGP sessions. This lab moves the unequal-cost load balancing into your network; we’ll use the BGP Link Bandwidth attribute on IBGP sessions.
Cloudflare’s 2024 Annual Founders’ Letter
This week Cloudflare will celebrate the fourteenth anniversary of our launch. We think of it as our birthday. As is our tradition ever since our first anniversary, we use our Birthday Week each year to launch new products that we think of as gifts back to the Internet. For the last five years, we also take this time to write our annual Founders’ Letter reflecting on our business and the state of the Internet. This year is no different.
That said, one thing that is different is you may have noticed we've actually had fewer public innovation weeks over the last year than usual. That's been because a couple of incidents nearly a year ago caused us to focus on improving our internal systems over releasing new features. We're incredibly proud of our team's focus to make security, resilience, and reliability the top priorities for the last year. Today, Cloudflare's underlying platform, and the products that run on top of it, are significantly more robust than ever before.

With that work largely complete, and our platform in its strongest shape ever, we plan to pick back up the usual cadence of new product launches that we're known for. This Continue reading
Logging in Python

How many times have you found yourself staring at your screen, surrounded by a sea of hastily added print statements, thinking "There's got to be a better way"? If you're like me, the answer is probably "more times than I'd care to admit."
Sick of finding myself in this situation more often than I'd like, I decided to take action. Python's default logging module is powerful, but it just didn't cut it for my needs. I was looking for something more.
Why Logging Matters
Before we dive in, let's look at why logging is crucial:
- Debugging: Logs provide a trail of breadcrumbs to track down issues.
- Monitoring: They help you understand your application's behavior.
- Auditing: Logs can serve as a record of important events or actions.
- Performance Tracking: You can use logs to identify bottlenecks and optimize your code.
Introducing PyLogger
With these benefits in mind, I set out to build a custom logging class that would meet all my requirements. The result is PyLogger, a Python logging class that aims to make logging both powerful and user-friendly.
Key Features
Below are some of the key features that make pylogger appealing:
- Flexible Continue reading
