Networking in Public Clouds – New ipSpace.net Online Course
I have exciting news I’d love to share with you: we’re launching a new online course focused on networking in public clouds starting in February 2020 (I’ve been mulling over this idea and polishing the concept for almost 18 months, and finally it all came together ;)
With Go To The Cloud becoming the answer to all questions (regardless of what the question is), you can find tons of materials describing various aspects of public clouds, so you might wonder why I decided to enter the fray. The answer is simple: with everyone being focused on developers, there’s not much that an infrastructure engineer could use to help him survive when the developers move on and he’s left to manage whatever they put in place.
Read more ...Serverless Security Threats Loom as Enterprises Go Cloud Native
As enterprises increase their usage of serverless functions, companies must understand serverless...
Worth Reading: Koding Academies
Every few weeks I stumble upon an article (or twitter storm) in which someone claims you don’t need formal education to get started as a Software Engineer (or whatever else) - all you need is a coding academy/bootcamp and you're all set.
George V. Neville-Neil wrote a hilarious rebuttal of this idea followed by some pretty good advice. Hope you’ll enjoy it as much as I did ;)
Run a script on virtual machines when the host is shut down
I want to show you how to configure a host server so, when it is shut down, it executes a script that runs commands on any running virtual machines before the host tries to stop them. I will configure the host server to wait until the script completes configuring the virtual machines before continuing with the shutdown process, shutting down the virtual machines, and eventually powering off.
I had to learn how Systemd service unit configuration files work and some more details about how Libvirt is configured in different Linux distributions. Read on to see the solution, plus some details about how to test the solution in Ubuntu and CentOS.
Solution Summary
Create a new Systemd service named graceful-shutdown that runs a script when the host system shuts down, but before Libvirt shuts down any virtual machines. Ensure that the libvirt-guests service is already started and enabled, and is configured appropriately.
The graceful-shutdown.service unit configuration file
Create a new Systemd unit configuration file named graceful-shutdown.service and save it in the directory, /etc/systemd/system, where it is advised you put custom configuration files.
For example:
# vi /etc/systemd/system/graceful-shutdown.service
Enter the following text into the file, then save it:
Continue readingCloudflare’s protection against a new Remote Code Execution vulnerability (CVE-2019-16759) in vBulletin
Cloudflare has released a new rule as part of its Cloudflare Specials Rulesets, to protect our customers against a high-severity vulnerability in vBulletin.
A new zero-day vulnerability was discovered for vBulletin, a proprietary Internet forum software. By exploiting this vulnerability, bad actors could potentially gain privileged access and control to the host servers on which this software runs, through Remote Code Execution (RCE).
Implications of this vulnerability
At Cloudflare, we use three key indicators to understand the severity of a vulnerability 1) how many customers on Cloudflare are running the affected software 2) the Common Vulnerability Scoring System (CVSS) score, and 3) the OWASP Top 10, an open-source security framework.
We assess this vulnerability to be very significant as it has a CVSS score of 9.8/10 and affects 7 out of the 10 key risk areas of the OWASP 2017 Top 10.
Remote Code Execution is considered a type of injection, which provides the capability to potentially launch a catastrophic attack. Through RCE an attacker can gain privileged access to the host server that might be running the unpatched and vulnerable version of this software. With elevated privileges the attacker could perform malicious activities including discovery of additional Continue reading
Qualcomm Paints Strategic Contrasts in Cloud, AI, Edge
Qualcomm says there are key differences in its approach to cloud computing, artificial...
Worth Reading: SDN Ate My Hamster
A long while ago Daniel Dib wrote a nice blog post on “SDN will make the networking engineers obsolete” theme. While it sounds like beating a dead horse, the SDN craze isn’t subsiding, so another healthy dose of common sense might come handy.
Hint: if you’re not following Daniel’s blog, you should… even though he decided to make old farts’ life harder by publishing on LinkedIn.
Heavy Networking 474: Find Breaches With Continuous Monitoring From Open Systems (Sponsored)
On today's Heavy Networking, sponsor Open Systems joins us to talk about its continuous security monitoring capabilities that help customers find breaches quickly. Our guest is Dave Martin, Senior Director for Product Management of Threat Response at Open Systems.
The post Heavy Networking 474: Find Breaches With Continuous Monitoring From Open Systems (Sponsored) appeared first on Packet Pushers.
Cumulus Co-Founder JR Rivers Joins Amazon
Rivers left Cumulus three months ago and started “looking for [his] next challenge,” which...
Birthday Week 2019 Wrap-up


This week we celebrated Cloudflare’s 9th birthday by launching a variety of new offerings that support our mission: to help build a better Internet. Below is a summary recap of how we celebrated Birthday Week 2019.
Cleaning up bad bots
Every day Cloudflare protects over 20 million Internet properties from malicious bots, and this week you were invited to join in the fight! Now you can enable “bot fight mode” in the Firewall settings of the Cloudflare Dashboard and we’ll start deploying CPU intensive code to traffic originating from malicious bots. This wastes the bots’ CPU resources and makes it more difficult and costly for perpetrators to deploy malicious bots at scale. We’ll also share the IP addresses of malicious bot traffic with our Bandwidth Alliance partners, who can help kick malicious bots offline. Join us in the battle against bad bots – and, as you can read here – you can help the climate too!
Browser Insights
Speed matters, and if you manage a website or app, you want to make sure that you’re delivering a high performing website to all of your global end users. Now you can enable Browser Insights in the Speed section of the Continue reading
AT&T Lobs White Box Router Design at OCP
AT&T is aiming the new DDC design squarely at the provider edge and the core routers that...
5G: Easy Please for Enterprises Say Verizon, IBM, Qualcomm
5G will deliver the greatest impact for enterprises, but the technology that will drive that...
The Role of South Asia’s NOGs in Community Building

At the recently concluded 34th South Asia Network Operators Group (SANOG 34), it was interesting not only to hear about the evolution of digital infrastructure, technology, and the economy in South Asia, including the opportunities it presents to network operators, but also to hear how community-led national Network Operating Groups (NOGs) in South Asia are working to build technical community knowledge, capacity, and engagement in their respective economies.
SANOG, which was set up as a sub-regional, community-led initiative in 2003, has played a significant role in bringing operators from the region together for knowledge sharing and cooperation. It is a biannual event, rotated among economies for maximum reach and participation.
While the NOGs of developed economies in the Asia Pacific began forming in the late 1990s, the NOGs in South Asia are quite recent: Bangladesh (bdNOG) and Bhutan (btNOG) were set up in 2014; Nepal (npNOG) in 2016; Sri Lanka (LKNOG) in 2017; and India (INNOG) in 2017.
The objectives of these NOGs are to encourage knowledge sharing within their respective economies and discuss global and regional technical developments, while addressing local requirements and issues. This, in turn, helps members Continue reading
Weekly Wrap: Ericsson Bribery Scandal Cuts Deep, Surpassing $1B Penalty
Weekly Wrap for Sept. 27, 2019: Stateless launches Luxon platform; Kubernetes sinks Containership;...
The Certification Ladder

Are you climbing the certification ladder? If you’re in IT the odds are good that you are. Some people are just starting out and see certifications as a way to get the knowledge they need to do their job. Others see certs as a way to get out of a job they don’t like. Still others have plenty of certifications but want to get the ones at the top of their field. This last group are the ones that I want to spend some time talking about.
Pushing The Limit
Expert-level certifications aren’t easy on purpose. They’re supposed to represent the gap between being good at something and going above and beyond. For some that involves some kind of practical test of skills like the CCIE. For others it involves a board interview process like the VCDX. Or it could even involve a combination of things like the CWNE does with board review and documentation submissions.
Expert certifications aren’t designed to be powered through in a short amount of time. That’s because it’s difficult to become an expert at something without putting in the practice time. For some tests, that means meeting some minimum requirements. You can only attempt your Continue reading
Workers Sites: Extending the Workers platform with our own serverless building blocks
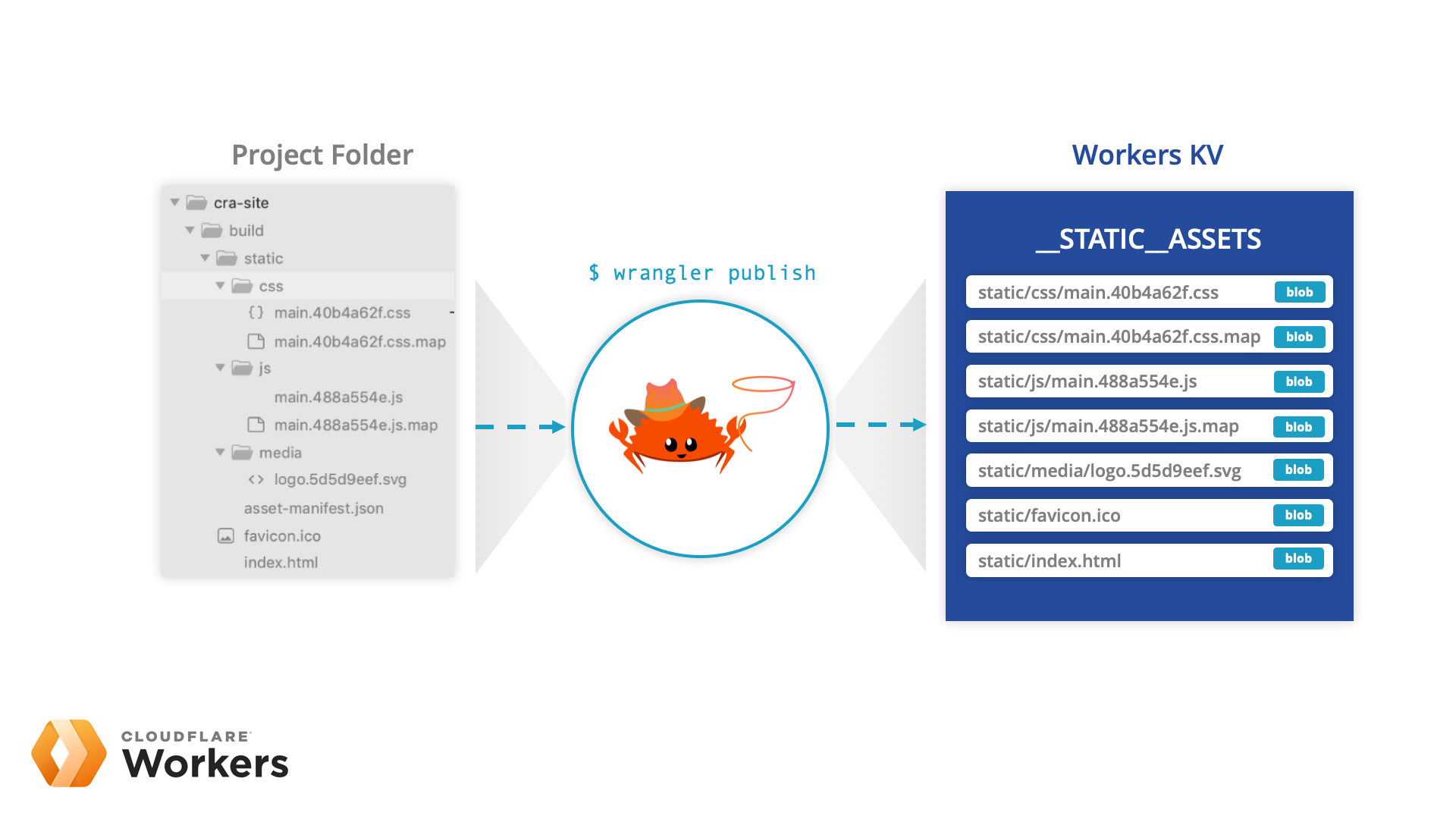
As of today, with the Wrangler CLI, you can now deploy entire websites directly to Cloudflare Workers and Workers KV. If you can statically generate the assets for your site, think create-react-app, Jekyll, or even the WP2Static plugin, you can deploy it to our entire global network, which spans 194 cities in more than 90 countries.
While you could deploy an entire site directly to Workers before, it wasn’t the easiest process. So, the Workers Developer Experience Team came up with a solution to make deploying static assets a significantly better experience.
Using our Workers command-line tool Wrangler, we've made it possible to deploy any static site to Workers in three easy steps: run wrangler init --site, configure the newly created wrangler.toml file with your account and project details, and then publish it to Cloudflare's edge with wrangler publish. If you want to explore how this works, check out our new Workers Sites tutorial for create-react-app, where we cover how this new functionality allows you to deploy without needing to write any additional code!
While in hindsight the path we took to get to this point might not seem the most straightforward, it really highlights the flexibility Continue reading
Workers Sites: Deploy Your Website Directly on our Network

Performance on the web has always been a battle against the speed of light — accessing a site from London that is served from Seattle, WA means every single asset request has to travel over seven thousand miles. The first breakthrough in the web performance battle was HTTP/1.1 connection keep-alive and browsers opening multiple connections. The next breakthrough was the CDN, bringing your static assets closer to your end users by caching them in data centers closer to them. Today, with Workers Sites, we’re excited to announce the next big breakthrough — entire sites distributed directly onto the edge of the Internet.
Deploying to the edge of the network
Why isn’t just caching assets sufficient? Yes, caching improves performance, but significant performance improvement comes with a series of headaches. The CDN can make a guess at which assets it should cache, but that is just a guess. Configuring your site for maximum performance has always been an error-prone process, requiring a wide collection of esoteric rules and headers. Even when perfectly configured, almost nothing is cached forever, precious requests still often need to travel all the way to your origin (wherever it may be). Cache invalidation is, after all, Continue reading
Net2Text: Natural-Language Interface to Network Operations
Sick-and-tired of intent-based GUIs that are barely better than CiscoWorks on steroids? How about asking Siri-like assistant queries about network state in somewhat-limited English and getting replies back in full-blown sentences?
Warning: you might be reentering the land of unicorns driving flying DeLoreans... but then keep in mind what Arthur Clarke had to say on this topic ;).
Welcome to Net2Text, another proof-of-concept tool created by the group led by Laurent Vanbever… who joined us for a short chat to discuss it, resulting in Episode 105 of Software Gone Wild.