EVPN Auto-RD and Duplicate MAC Addresses
Another EVPN reader question, this time focusing on auto-RD functionality and how it works with duplicate MAC addresses:
If set to Auto, RD generated will be different for the same VNI across the EVPN switches. If the same route (MAC and/or IP) is present under different leaves of the same L2VNI, since the RD is different there is no best path selection and both will be considered. It’s a misconfiguration and shouldn’t be allowed. How will the BGP deal with this?
Programmatically interpretable reinforcement learning
Programmatically interpretable reinforcement learning, Verma et al., ICML 2018
Being able to trust (interpret, verify) a controller learned through reinforcement learning (RL) is one of the key challenges for real-world deployments of RL that we looked at earlier this week. It’s also an essential requirement for agents in human-machine collaborations (i.e, all deployments at some level) as we saw last week. Since reading some of Cynthia Rudin’s work last year I’ve been fascinated with the notion of interpretable models. I believe there are a large set of use cases where an interpretable model should be the default choice. There are so many deployment benefits, even putting aside any ethical or safety concerns.
So how do you make an interpretable model? Today’s paper choice is the third paper we’ve looked at along these lines (following CORELS and RiskSlim), enough for a recognisable pattern to start to emerge. The first step is to define a language — grammar and associated semantics — in which the ultimate model to be deployed will be expressed. For CORRELS this consists of simple rule based expressions, and for RiskSlim it is scoring sheets. For Programmatically Interpretable Reinforcement Learning (PIRL) as we shall Continue reading
BGP in 2019 – Part 2
This second part of the report of BGP across 2019 will look at the profile of BGP updates across 2019 to assess whether the stability of the routing system, as measured by the level of BGP update activity, is changing.The Inevitability Of FPGAs In The Datacenter
You don’t have to be a chip designer to program an FPGA, just like you don’t have to be a C++ programmer to code in Java, but it probably helps in both cases if you want to do them well. …
The Inevitability Of FPGAs In The Datacenter was written by Timothy Prickett Morgan at The Next Platform.
Google Absorbs AppSheet to Automate Code
The deal will support enterprises in developing richer applications at scale that can leverage...
Daily Roundup: Nokia Slashes Jobs
Nokia cut 180 jobs, with more to come; Equinix pushed to the edge with Packet acquisition; and...
Microsoft Patches Critical Windows Security Flaw
“For the U.S. government to share its discovery of a critical vulnerability with a vendor is...
SDxCentral Adds Career Resources for IT Professionals
SDxCentral announces the additional of career resources for IT professions to SDxCentral.com. Check...
European Weather Center Breaks Tradition With Upcoming Supercomputer
Weather forecasting in Europe is going to get a big boost later this year when the European Centre for Medium-Range Weather Forecasts (ECMWF) installs its next-generation supercomputer. …
European Weather Center Breaks Tradition With Upcoming Supercomputer was written by Michael Feldman at The Next Platform.
AT&T Wins 5G Contract for Nellis Air Force Base
AT&T plans to equip the base with 5G infrastructure to support more than 40,000 Air Force...
Deep Dive: U.S. Federal Government’s Security and Privacy Practices

In April 2019, the Internet Society’s Online Trust Alliance released its 10th Annual Online Trust Audit & Honor Roll. The Audit looks at the security and privacy practices of over 1,000 of the top sites on the Internet, from retailers to government sites. In this post we will take a deeper dive into the U.S. Federal Government sector of the Audit. The Government sector is defined as the top 100 sites in the U.S. Federal Government by traffic (based on Alexa ranking). Given the nature of the U.S. Government compared to companies, this sample has some unique properties, namely site security.
The most obvious place the government excels is in the area of encryption. The reason for this is largely due to a mandate from the Homeland Security Department that all U.S. Government sites be encrypted, but the standard should still be the same for any site. Put another way, the other sectors in the Audit do not have an excuse for lagging in security.
In site security the Government sector fared the best with 100% adoption of “Always-On Secure Socket Layer” (AOSSL) and/or “HTTP Strict Transport Security” (HSTS), compared to 91% of sites overall. The Continue reading
Google Partners With CNCF, HackerOne on Kubernetes Bug Bounty
With more people looking for vulnerabilities, the safer and more secure Kubernetes will be,...
Embattled GTT Fortifies Its SD-WAN With Fortinet
The deal comes after a dismal second half of 2019 that saw the company's stock prices plunge from a...
A cost-effective and extensible testbed for transport protocol development
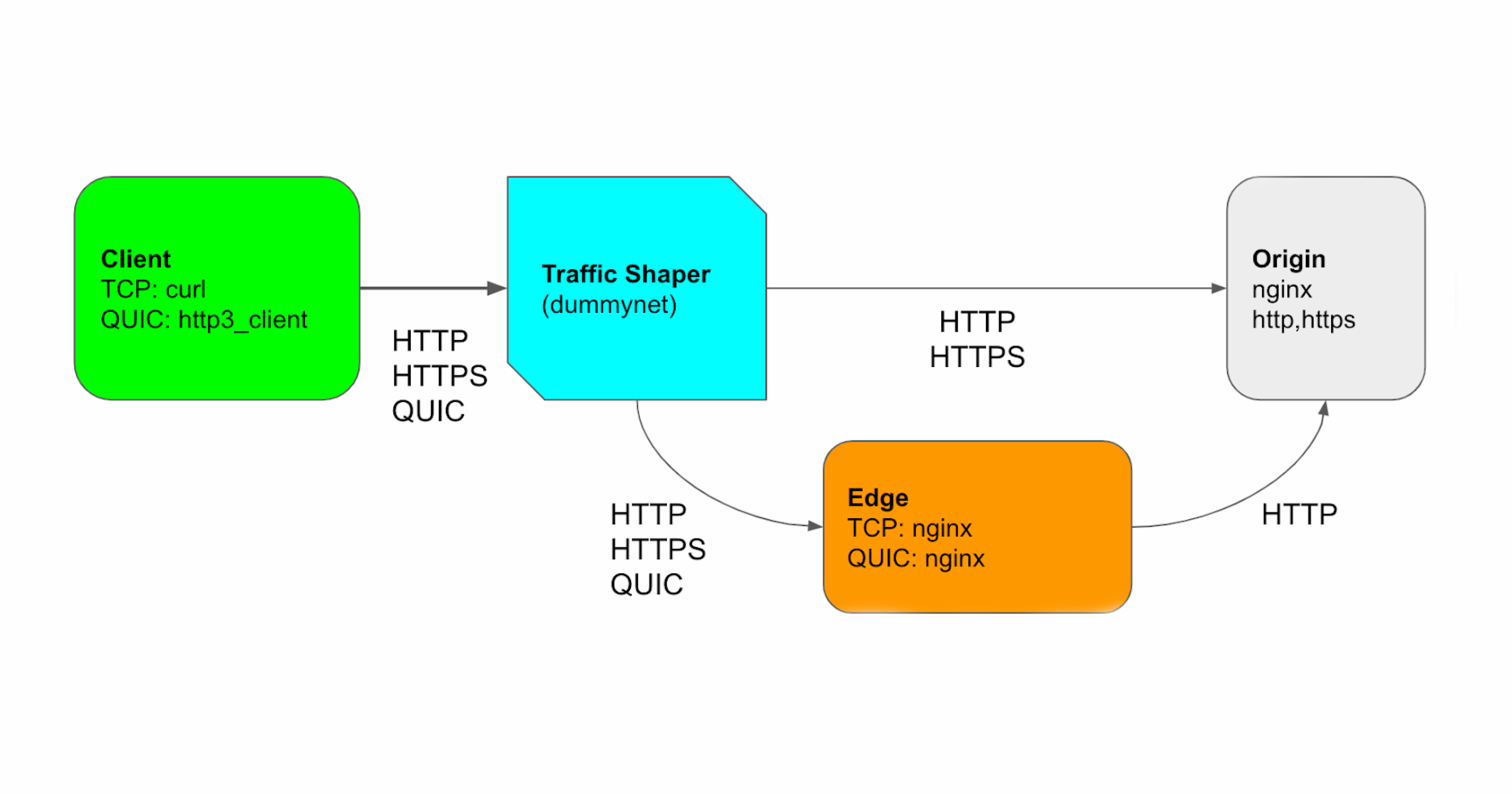
This was originally published on Perf Planet's 2019 Web Performance Calendar.
At Cloudflare, we develop protocols at multiple layers of the network stack. In the past, we focused on HTTP/1.1, HTTP/2, and TLS 1.3. Now, we are working on QUIC and HTTP/3, which are still in IETF draft, but gaining a lot of interest.
QUIC is a secure and multiplexed transport protocol that aims to perform better than TCP under some network conditions. It is specified in a family of documents: a transport layer which specifies packet format and basic state machine, recovery and congestion control, security based on TLS 1.3, and an HTTP application layer mapping, which is now called HTTP/3.
Let’s focus on the transport and recovery layer first. This layer provides a basis for what is sent on the wire (the packet binary format) and how we send it reliably. It includes how to open the connection, how to handshake a new secure session with the help of TLS, how to send data reliably and how to react when there is packet loss or reordering of packets. Also it includes flow control and congestion control to interact well with other transport protocols in Continue reading
Get Up To Speed on NSX Cloud with 5 Easy Resources
Over the last few years, as public and hybrid cloud adoption proliferated, organizations began looking for seamless and consistent manageability of their public cloud and private cloud workloads. This is one of the reasons why VMware brought NSX Cloud to the market.
Overview of NSX Cloud
In a nutshell, NSX Cloud provides consistent networking and security across hybrid and multi-cloud workloads. The key benefits and features of NSX Cloud include:
- Single-pane-of-glass visibility
- Essential networking capabilities
- Consistent security policy
- Granular micro-segmentation across on-premises and native public cloud environments such as AWS and Azure
NSX Cloud plays a key role in VMware’s Virtual Cloud Network vision of connecting and protecting workloads of all types (VMs, containers, bare metal) from data center to cloud to edge.
“With NSX Cloud, we got a very compact firewall policy—easy to review and easy to manage. The power, administratively, is that we go to one place to update our policy and when we publish it, it automatically deploys it to every cloud server instance. This was a big win for us.”
Brian Jemes, Network Manager, University of Idaho
VMworld US 2018, NET1516BU
Top 5 Resources on NSX Cloud
Here is a compilation of the Continue reading