Vitess Earns Vernerable CNCF’s Graduate Distinction
It was the second cloud-based storage project accepted by the CNCF in 2018 and the eighth project...
It was the second cloud-based storage project accepted by the CNCF in 2018 and the eighth project...
This is a guest post by Alex Iankoulski, Docker Captain and full stack software and infrastructure architect at Shell New Energies. The views expressed here are his own and are neither opposed or endorsed by Shell or Docker.
In this blog, I will show you how to use Docker Desktop for Mac or Windows to run Kubeflow. To make this easier, I used my Depend on Docker project, which you can find on Github.
Even though we are experiencing a tectonic shift of development workflows in the cloud era towards hosted and remote environments, a substantial amount of work and experimentation still happens on developer’s local machines. The ability to scale down allows us to mimic a cloud deployment locally and enables us to play, learn quickly, and make changes in a safe, isolated environment. A good example of this rationale is provided by Kubeflow and MiniKF.
Since Kubeflow was first released by Google in 2018, adoption has increased significantly, particularly in the data science world for orchestration of machine learning pipelines. There are various ways to deploy Kubeflow both on desktops and servers as described in Continue reading

In a bid to improve digital accessibility in Pakistan – a country with about 30 million persons with disability (PWDs), according to the World Health Organization – we recently partnered with the Ministry of IT (MoIT) and the National IT Board (NITB) so that more existing government websites could include accessibility features and future websites could incorporate such designs. We set out to make five websites more accessible – as a start – and are already seeing encouraging results.
According to local study and research paper, a majority of websites in Pakistan, including government, are not accessible for PWDs. PWDs face various challenges in using websites based on their impairment.
For example, persons with visual impairments can face compatibility challenges when screen reader software is used to access visual displays that are not labelled or hyperlinks that do not make sense when read out of context. Those with low vision are not able to access websites that cannot be adjusted for font type and size, contrast, and use of colors, and individuals who are deaf are not able to understand the narration in an online video if it is not properly captioned.
As part of this commitment given by Continue reading
The Day Two Cloud podcast is getting a new co-host, Ethan Banks; and becoming a weekly show! Now you can get deep dives on cloud and infrastructure topics including Kubernetes, cloud security, design and deployment, and more every week.
The post Day Two Cloud 022: Day Two Cloud Scales Out And Up! appeared first on Packet Pushers.
The deeper integration provide a consistent operational security model for customers running...
For much of the decade, a debate around Arm was whether it would fulfill its promise to become a silicon designer with suppliers of any significance to datacenter hardware. …
Attacking The Datacenter From The Edge Inward was written by Jeffrey Burt at The Next Platform.
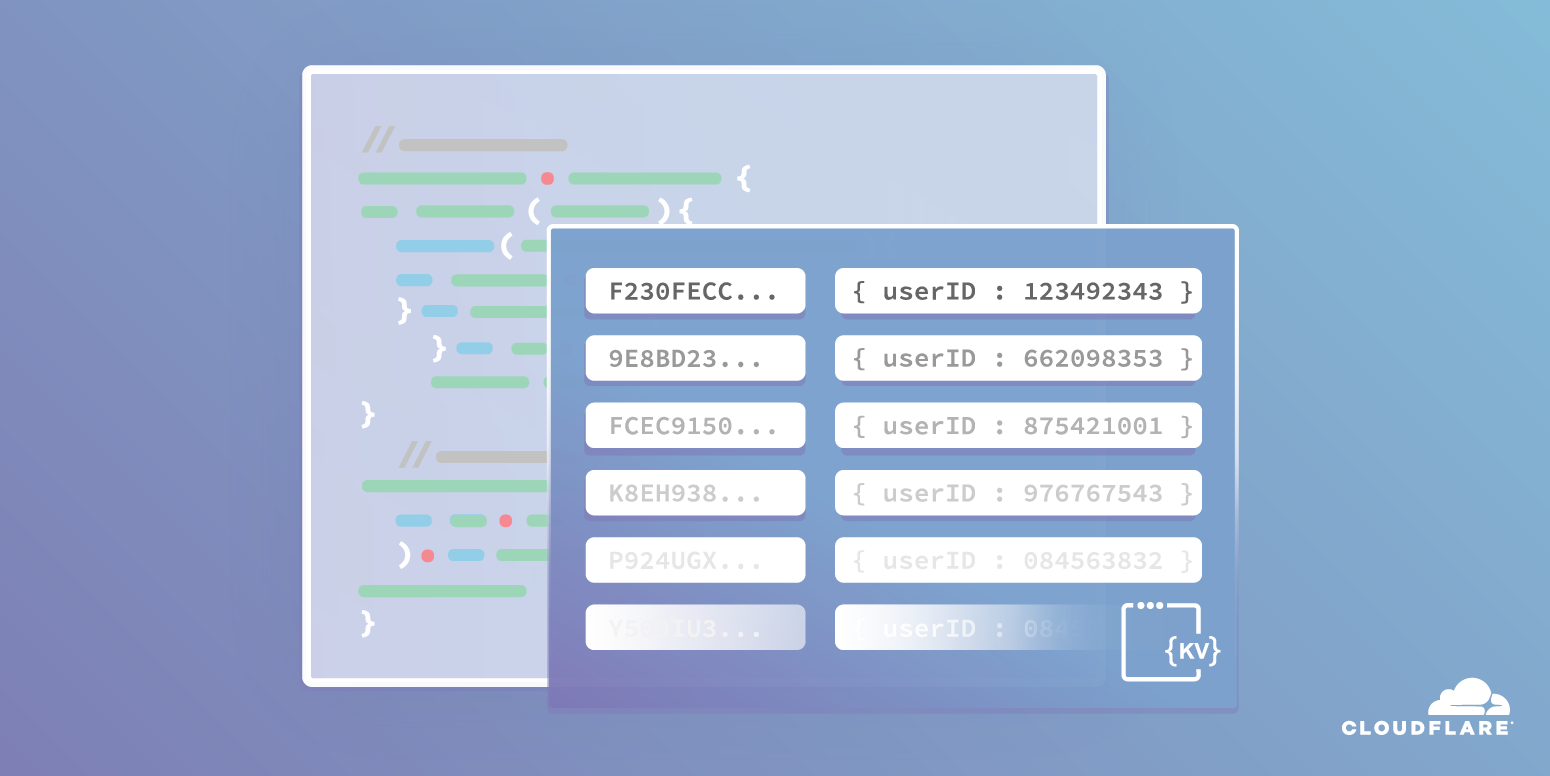

The Storage team here at Cloudflare shipped Workers KV, our global, low-latency, key-value store, earlier this year. As people have started using it, we’ve gotten some feature requests, and have shipped some new features in response! In this post, we’ll talk about some of these use cases and how these new features enable them.
We’ve shipped some new APIs, both via api.cloudflare.com, as well as inside of a Worker. The first one provides the ability to upload and delete more than one key/value pair at once. Given that Workers KV is great for read-heavy, write-light workloads, a common pattern when getting started with KV is to write a bunch of data via the API, and then read that data from within a Worker. You can now do these bulk uploads without needing a separate API call for every key/value pair. This feature is available via api.cloudflare.com, but is not yet available from within a Worker.
For example, say we’re using KV to redirect legacy URLs to their new homes. We have a list of URLs to redirect, and where they should redirect to. We can turn this list into JSON that Continue reading
A Network Artist left a lengthy comment on my Brief History of VMware NSX blog post. He raised a number of interesting topics, so I decided to write my replies as a separate blog post.
Using Geneve is an interesting choice to be made and while the approach has it’s own Pros and Cons, I would like to stick to VXLAN if I were to recommend to someone for few good reasons.
The main reason I see for NSX-T using Geneve instead of VXLAN is the need for additional header fields to carry metadata around, and to implement Network Services Header (NSH) for east-west service insertion.
Read more ...File systems unfit as distributed storage backends: lessons from 10 years of Ceph evolution Aghayev et al., SOSP’19
Ten years of hard-won lessons packed into just 17 pages (13 if you don’t count the references!) makes this paper extremely good value for your time. It’s also a fabulous example of recognising and challenging implicit assumptions. In this case, the assumption that a distributed storage backend should clearly be layered on top of a local file system. Breaking that assumption allowed Ceph to introduce a new storage backend called BlueStore with much better performance and predictability, and the ability to support the changing storage hardware landscape. In the two years since it’s release, 70% of all Ceph users had switched to running BlueStore in production.
Ceph is a widely-used, open-source distributed file system that followed this convention [of building on top of a local file system] for a decade. Hard lessons that the Ceph team learned using several popular file systems led them to question the fitness of file systems as storage backends. This is not surprising in hindsight.
Sometimes, things that aren’t surprising in hindsight can be the very hardest of things to spot!