AT&T Lobs White Box Router Design at OCP
AT&T is aiming the new DDC design squarely at the provider edge and the core routers that...
AT&T is aiming the new DDC design squarely at the provider edge and the core routers that...
5G will deliver the greatest impact for enterprises, but the technology that will drive that...
Wake up! It's HighScalability time:

Nifty diagram of what testing looks like in an era or progressive delivery. (@alexsotob, @samnewman)
Do you like this sort of Stuff? I'd greatly appreciate your support on Patreon. I wrote Explain the Cloud Like I'm 10 for all who want to understand the cloud. On Amazon it has 55 mostly 5 star reviews (131 on Goodreads). They'll thank you for changing their life forever.
Don't miss all that the Internet has to say on Scalability, click below and become eventually consistent with all scalability knowledge (which means this post has many more items to read so please keep on reading)...

At the recently concluded 34th South Asia Network Operators Group (SANOG 34), it was interesting not only to hear about the evolution of digital infrastructure, technology, and the economy in South Asia, including the opportunities it presents to network operators, but also to hear how community-led national Network Operating Groups (NOGs) in South Asia are working to build technical community knowledge, capacity, and engagement in their respective economies.
SANOG, which was set up as a sub-regional, community-led initiative in 2003, has played a significant role in bringing operators from the region together for knowledge sharing and cooperation. It is a biannual event, rotated among economies for maximum reach and participation.
While the NOGs of developed economies in the Asia Pacific began forming in the late 1990s, the NOGs in South Asia are quite recent: Bangladesh (bdNOG) and Bhutan (btNOG) were set up in 2014; Nepal (npNOG) in 2016; Sri Lanka (LKNOG) in 2017; and India (INNOG) in 2017.
The objectives of these NOGs are to encourage knowledge sharing within their respective economies and discuss global and regional technical developments, while addressing local requirements and issues. This, in turn, helps members Continue reading
In this blog series on Kubernetes, we’ve already covered:
In this series’ final installment, I’ll explain how to provision storage to a Kubernetes application.

The final component we want to think about when we build applications for Kubernetes is storage. Remember, a container’s filesystem is transient, and any data kept there is at risk of being deleted along with your container if that container ever exits or is rescheduled. If we want to guarantee that data lives beyond the short lifecycle of a container, we must write it out to external storage.
Any container that generates or collects valuable data should be pushing that data out to stable external storage. In our web app example, the database tier should be pushing its on-disk contents out to external storage so they can survive a catastrophic failure of our database pods.
Similarly, any container that requires the provisioning of a lot of data should be getting Continue reading
Weekly Wrap for Sept. 27, 2019: Stateless launches Luxon platform; Kubernetes sinks Containership;...

Are you climbing the certification ladder? If you’re in IT the odds are good that you are. Some people are just starting out and see certifications as a way to get the knowledge they need to do their job. Others see certs as a way to get out of a job they don’t like. Still others have plenty of certifications but want to get the ones at the top of their field. This last group are the ones that I want to spend some time talking about.
Expert-level certifications aren’t easy on purpose. They’re supposed to represent the gap between being good at something and going above and beyond. For some that involves some kind of practical test of skills like the CCIE. For others it involves a board interview process like the VCDX. Or it could even involve a combination of things like the CWNE does with board review and documentation submissions.
Expert certifications aren’t designed to be powered through in a short amount of time. That’s because it’s difficult to become an expert at something without putting in the practice time. For some tests, that means meeting some minimum requirements. You can only attempt your Continue reading
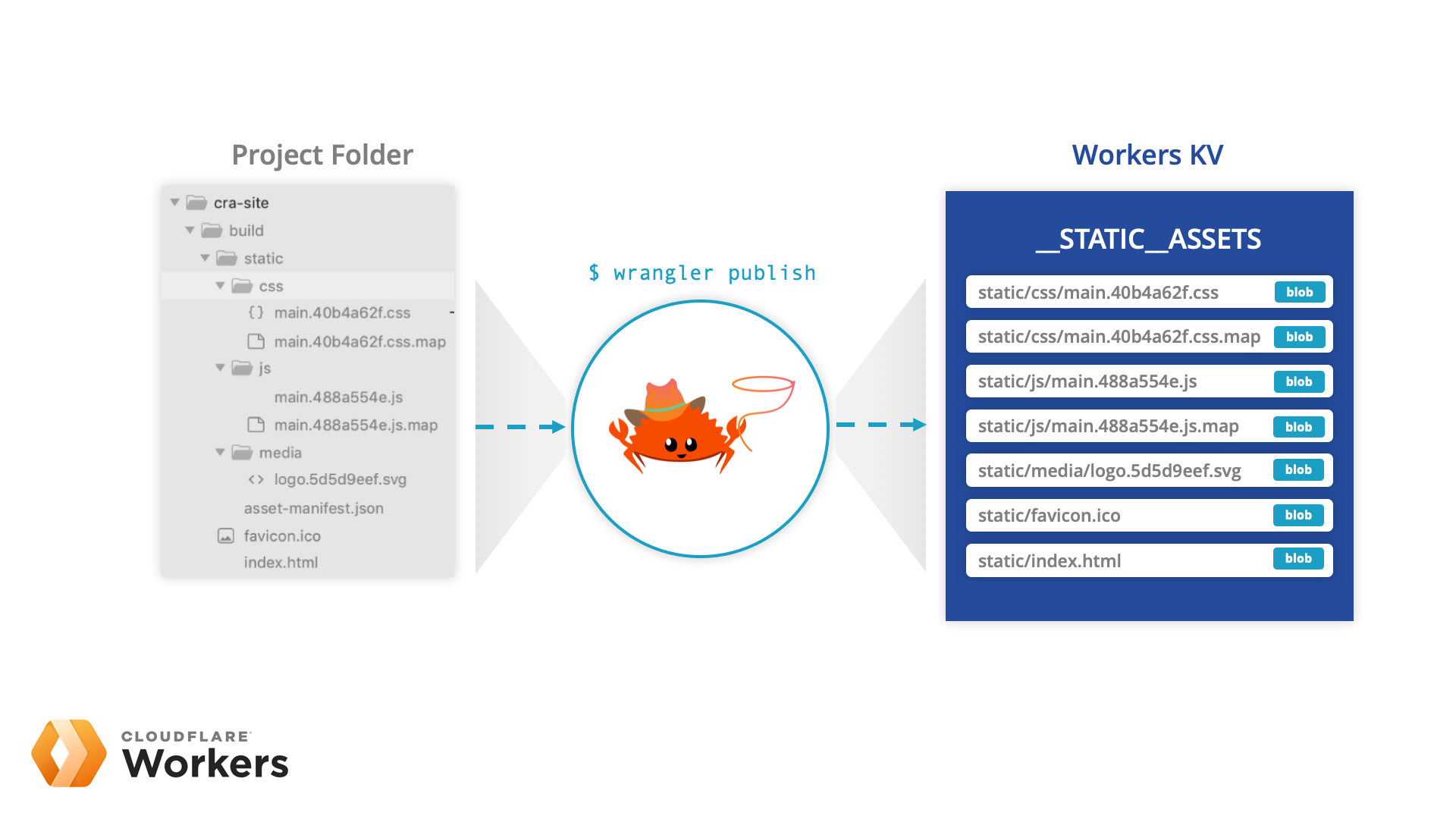
As of today, with the Wrangler CLI, you can now deploy entire websites directly to Cloudflare Workers and Workers KV. If you can statically generate the assets for your site, think create-react-app, Jekyll, or even the WP2Static plugin, you can deploy it to our entire global network, which spans 194 cities in more than 90 countries.
While you could deploy an entire site directly to Workers before, it wasn’t the easiest process. So, the Workers Developer Experience Team came up with a solution to make deploying static assets a significantly better experience.
Using our Workers command-line tool Wrangler, we've made it possible to deploy any static site to Workers in three easy steps: run wrangler init --site, configure the newly created wrangler.toml file with your account and project details, and then publish it to Cloudflare's edge with wrangler publish. If you want to explore how this works, check out our new Workers Sites tutorial for create-react-app, where we cover how this new functionality allows you to deploy without needing to write any additional code!
While in hindsight the path we took to get to this point might not seem the most straightforward, it really highlights the flexibility Continue reading

Performance on the web has always been a battle against the speed of light — accessing a site from London that is served from Seattle, WA means every single asset request has to travel over seven thousand miles. The first breakthrough in the web performance battle was HTTP/1.1 connection keep-alive and browsers opening multiple connections. The next breakthrough was the CDN, bringing your static assets closer to your end users by caching them in data centers closer to them. Today, with Workers Sites, we’re excited to announce the next big breakthrough — entire sites distributed directly onto the edge of the Internet.
Why isn’t just caching assets sufficient? Yes, caching improves performance, but significant performance improvement comes with a series of headaches. The CDN can make a guess at which assets it should cache, but that is just a guess. Configuring your site for maximum performance has always been an error-prone process, requiring a wide collection of esoteric rules and headers. Even when perfectly configured, almost nothing is cached forever, precious requests still often need to travel all the way to your origin (wherever it may be). Cache invalidation is, after all, Continue reading
Welcome to Technology Short Take #119! As usual, I’ve collected some articles and links from around the Internet pertaining to various data center- and cloud-related topics. This installation in the Tech Short Takes series is much shorter than usual, but hopefully I’ve managed to find something that proves to be helpful or informative! Now, on to the content!
iptables layer involved in most Kubernetes implementations to load balance traffic directly to Pods in the cluster. Unfortunately, this appears to be GKE-specific.Nothing this time around. I’ll stay tuned for content to include next time!
Sick-and-tired of intent-based GUIs that are barely better than CiscoWorks on steroids? How about asking Siri-like assistant queries about network state in somewhat-limited English and getting replies back in full-blown sentences?
Warning: you might be reentering the land of unicorns driving flying DeLoreans... but then keep in mind what Arthur Clarke had to say on this topic ;).
Welcome to Net2Text, another proof-of-concept tool created by the group led by Laurent Vanbever… who joined us for a short chat to discuss it, resulting in Episode 105 of Software Gone Wild.
Wireless attacks on aircraft instrument landing systems Sathaye et al., USENIX Security Symposium 2019
It’s been a while since we last looked at security attacks against connected real-world entities (e.g., industrial machinery, light-bulbs, and cars). Today’s paper is a good reminder of just how important it is becoming to consider cyber threat models in what are primary physical systems, especially if you happen to be flying on an aeroplane – which I am right now as I write this!
The first fully operational Instrument Landing System (ILS) for planes was deployed in 1932. But assumptions we’ve been making since then (and until the present day, it appears!) no longer hold:
Security was never considered by design as historically the ability to transmit and receive wireless signals required considerable resources and knowledge. However, the widespread availability of powerful and low-cost software-defined radio platforms has altered the threat landscape. In fact, today the majority of wireless systems employed in modern aviation have been shown to be vulnerable to some form of cyber-physical attacks.
Both sections 1 and 6 in the paper give some eye-opening details of known attacks against aviation systems, but to date no-one Continue reading
Lisa Dethmers-Pope and Amn Rahman at Docker also contributed to this blog post.

As a Technical Recruiter at Docker, I am excited to be a part of Grace Hopper Celebration. It is a marvelous opportunity to speak with many talented women in tech and to continue pursuing one of Docker’s most valued ambitions: further diversifying our team. The Docker team will be on the show floor at the Grace Hopper Celebration, the world’s largest gathering of women technologists the week of October 1st in Orlando, Florida.
Our Vice President of Human Resources, and our Senior Director of Product Management, along with representatives from our Talent Acquisition and Engineering teams will be there to connect with attendees. We will be showing how to easily build, run, and share an applications using the Docker platform, and talking about what it’s like to work in tech today.
While we’ve made strides in diversity within tech, the 2019 Stack Overflow Developer Survey shows we have work to do. According to the survey, only 7.5 percent of professional developers are women worldwide (it’s 11 percent of all developers in the U. Continue reading
“I would like you to find out what happened with this whole situation with Ukraine, they say Crowdstrike... I guess you have one of your wealthy people... The server, they say Ukraine has it.”Personally, I occasionally interrupt myself while speaking, so I'm not sure I'd criticize Trump here for his incoherence. But at the same time, we aren't quite sure what was meant. It's only meaningful in the greater context. Trump has talked before about CrowdStrike's investigation being wrong, a rich Ukrainian owning CrowdStrike, and a "server". He's talked a lot about these topics before.