Ericsson Expands US Manufacturing With New Factory in Texas
The 300,000-square-foot factory will begin commercial operations early next year in Lewisville,...
The 300,000-square-foot factory will begin commercial operations early next year in Lewisville,...
The group is working with service providers to define and create VNF reference architectures for...

Kubernetes’s gravity as the container orchestrator of choice continues to grow, and for good reason: It has the broadest capabilities of any container orchestrator available today. But all that power comes with a price; jumping into the cockpit of a state-of-the-art jet puts a lot of power under you, but how to actually fly the thing is not obvious.
Kubernetes’ complexity is overwhelming for a lot of people jumping in for the first time. In this blog series, I’m going to walk you through the basics of architecting an application for Kubernetes, with a tactical focus on the actual Kubernetes objects you’re going to need. I’m not, however, going to spend much time reviewing 12-factor design principles and microservice architecture; there are some excellent ideas in those sort of strategic discussions with which anyone designing an application should be familiar, but here on the Docker Training Team I like to keep the focus on concrete, hands-on-keyboard implementation as much as possible.
Furthermore, while my focus is on application architecture, I would strongly encourage devops engineers and developers building to Kubernetes to follow along, in addition to readers in application architecture Continue reading
Co-authored with Rajiv Prithvi, Product Manager Networking and Security Business Unit at VMware
During VMworld US 2019, we announced several new transformative capabilities in VMware NSX-T 2.5 release which is now shipping! The release strengthens the NSX platform’s intrinsic security, multi-cloud, container, and operational capabilities.
We also announced the successful FIPS 140-2 validation of NSX-T 2.5. FIPS compliance is mandatory for US federal agencies and has also been widely adopted in non-governmental sectors (e.g. financial services, utilities, healthcare). FIPS-140-2 establishes the integrity of cryptographic modules in use through validation testing done by NIST and CSE. With this validation, we further deliver on our confidentiality, integrity and availability objectives and provide our customers with a robust networking and security virtualization platform.
NSX-T 2.5 is configured to operate in FIPS mode by default. Any exceptions or deviations from established compliance norms are identified in a compliance report which can be used to review and configure your NSX-T Data Center environment to meet your IT policies and industry standards. Any exceptions to FIPS compliance including configuration errors can be retrieved from the compliance report using NSX Manager UI or APIs.
A sample FIPS Continue reading
Today's Network Break discusses upgrades to Arista's CloudVision management software, a new ACI partnership between Cisco and Microsoft Azure, a Google pledge to invest in new European data centers, Amazon's pledge to be carbon-neutral by 2040, and more tech news.
The post Network Break 253: Arista CloudVision Ingests Configs From Third-Party Gear; Cisco Adds Azure To Cloud ACI appeared first on Packet Pushers.

The Internet is changing. Consolidation in the Internet economy, the topic of the Global Internet Report 2019, might be the source of ongoing shifts in its underlying infrastructure and the way users engage, among many other things.
Clearly, the growing presence of big Internet platforms can benefit the user by offering seamless Internet experiences, but it could also harm innovation, competition, and the Internet’s broader architecture, says the report, which marks the start of the Internet Society’s efforts to examine this issue.
The Internet in Asia-Pacific is no exception. A few corporations – including Facebook and Tencent in social networking, Google and Baidu in search, and Amazon and Alibaba in online shopping – dominate large parts of the Internet, benefitting people while raising similar questions about what it means for the Internet’s fundamental properties.
This year’s Survey on Policy Issues in Asia-Pacific, released today, helps deepen our understanding of the role that corporations play in shaping Internet use and user experience in the region and how they may impact future innovation on the Internet.
More than 1,300 people from 39 economies in the region took our online survey when we opened it to the public in July.
The Continue reading
Over the past couple of years, Juniper has hosted a Hackathon at start of NXTWORK. This event is a great …
The post Juniper NXTWORK Hack-a-Thon appeared first on Fryguy's Blog.

From the very beginning Cloudflare has been stopping malicious bots from scraping websites, or misusing APIs. Over time we’ve improved our bot detection methods and deployed large machine learning models that are able to distinguish real traffic (be it from humans or apps) from malicious bots. We’ve also built a large catalog of good bots to detect things like helpful indexing by search engines.
But it’s not enough. Malicious bots continue to be a problem on the Internet and we’ve decided to fight back. From today customers have the option of enabling “bot fight mode” in their Cloudflare Dashboard.
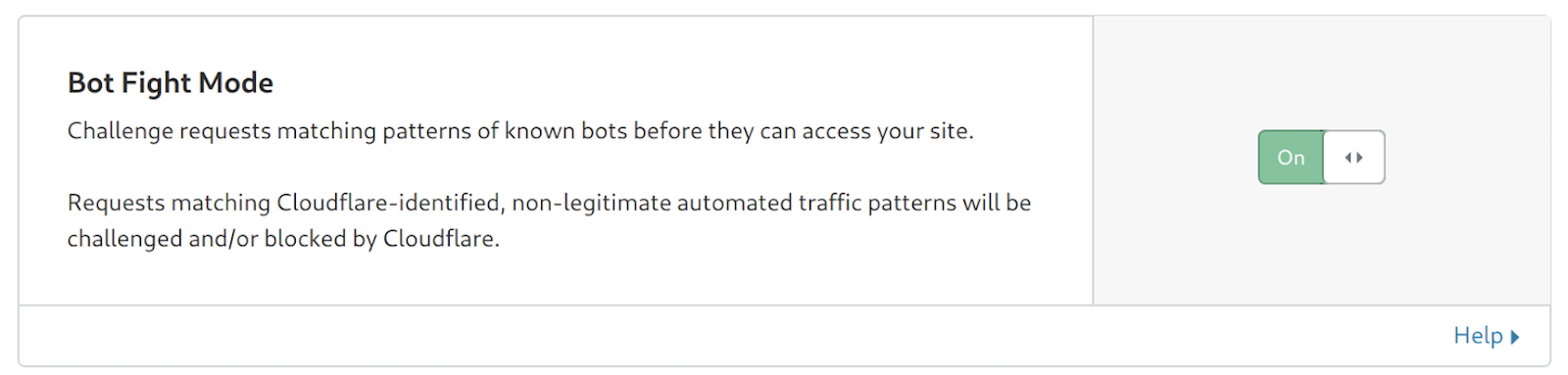
Once enabled, when we detect a bad bot, we will do three things: (1) we’re going to disincentivize the bot maker economically by tarpitting them, including requiring them to solve a computationally intensive challenge that will require more of their bot’s CPU; (2) for Bandwidth Alliance partners, we’re going to hand the IP of the bot to the partner and get the bot kicked offline; and (3) we’re going to plant trees to make up for the bot’s carbon cost.

Malicious bots harm legitimate web publishers and applications, hurt hosting providers by misusing resources, and they doubly hurt the planet Continue reading
If you are configuring Cisco ACI datacenter fabric it will sooner or later get to the point that you need to configure multiple objects inside the GUI which will, by using the click-n-click method, take a huge amount of time. While using POSTMAN to create multiple objects of the same type is the preferred method that everybody is speaking about (because you can generate REST API calls using Python or something similar), the quickest way to do it is using POST of JSON configuration file directly through the GUI. POSTing JSON config example As described above, the POST of JSON
The post Cisco ACI – Configuring by POSTing JSON appeared first on How Does Internet Work.
The transportation methodology aims to simplify metro networks, reduce capital expenditures, and...
In last week’s continuation of EVPN never-ending story Lukas Krattiger described how you could use EVPN constructs (VNIs, VRFs) to implement service insertion, and how you could combine then with policy-based routing.
TL&DW: It’s bridging and routing ;)
You’ll need Standard ipSpace Subscription to access the videos.
The secret sharer: evaluating and testing unintended memorization in neural networks Carlini et al., USENIX Security Symposium 2019
This is a really important paper for anyone working with language or generative models, and just in general for anyone interested in understanding some of the broader implications and possible unintended consequences of deep learning. There’s also a lovely sense of the human drama accompanying the discoveries that just creeps through around the edges.
Disclosure of secrets is of particular concern in neural network models that classify or predict sequences of natural language text… even if sensitive or private training data text is very rare, one should assume that well-trained models have paid attention to its precise details…. The users of such models may discover— either by accident or on purpose— that entering certain text prefixes causes the models to output surprisingly revealing text completions.
Take a system trained to make predictions on a language (word or character) model – an example you’re probably familiar with is Google Smart Compose. Now feed it a prefix such as “My social security number is “. Can you guess what happens next?
As a small scale demonstration, the authors trained a model on Continue reading


September has always been a special month for Cloudflare. Nine years ago — on September 27th — we launched Cloudflare. And, each year since, we’ve celebrated our birthday with a week full of new products and innovations that support our mission of helping to build a better Internet.
Our mission guides everything we do. One of the most intentional words in our mission is ‘helping’. Building an Internet that can meet the world’s needs cannot be done by any one company or individual; rather, it takes a global community — from nonprofit organizations and businesses to governments and individuals — collaborating to deliver new standards, technologies, and innovations. We believe Cloudflare should be an active participant in the community and help where we can and should.
Our customers and partners are an active part of the community. I often say that customers are one of my favorite parts of my job (our team is my other favorite part). Our customers give us feedback all the time about what they'd like to see to make their Internet properties more secure, more performant and more reliable. Our partners bring forward standards to help make the Internet run more smoothly. For Birthday Week Continue reading
People who can explain complex topics in simple terms, or focus on the essentials of a particular topic are exceedingly rare… and two of the best are Randall Munroe of the XKCD fame and Julia Evans, the mastermind behind WizardZines. I loved her recent curl and git exercises, and I’m guessing a lot of people in this industry would benefit from her latest HTTP zine.
Similarly to what I did a long time ago with ipSpace.net, Julia recently decided to go all-in, leaving her job and focusing on explaining things. I hope it will work out and we’ll keep enjoying her tidbits of wisdom for years to come.
Communications leaders from around the world will gather at MEF19 to focus on accelerating the...