Another Benefit of Open-Source Networking Software
You probably know my opinion on nerd knobs and the resulting complexity, but sometimes you desperately need something to get the job done.
In traditional vendor-driven networking world, you might be able to persuade your vendor to implement the knob (you think) you need in 3 years by making it a mandatory requirement for a $10M purchase order. In open-source world you implement the knob, write the unit tests, and submit a pull request.
Read more ...HHVM JIT: A profile-guided, region-based compiler for PHP and Hack
HHVM JIT: A profile-guided, region-based compiler for PHP and Hack Ottoni, PLDI’18
HHVM is a virtual machine for PHP and Hack (a PHP extension) which is used to power Facebook’s website among others. Today’s paper choice describes the second generation HHVM implementation, which delivered a 21.7% performance boost when running the Facebook website compared to the previous HHVM implementation.
…the PHP code base that runs the Facebook website includes tens of millions of lines of source code, which are translated to hundreds of megabytes of machine code during execution.
I’m clearly suffering from an over-simplified understanding of what the Facebook web application actually does, but at the same time if I asked you to write a Facebook clone for just the website (not the backing services, not the mobile apps, etc.), would your initial estimate be on the order of tens of millions of lines of code???!
HHVM high-level overview
The starting point for HHVM is source code in PHP or Hack. Hack is a PHP dialect used by Facebook and includes support for a richer set of type hints. From the perspective of HHVM though the two languages are fundamentally equivalent. In particular, Hack’s type hints are Continue reading
What the Caesars (@DefCon) WiFi situation looks like
So I took a survey of WiFi at Caesar's Palace and thought I'd write up some results.When we go to DEF CON in Vegas, hundreds of us bring our WiFi tools to look at the world. Actually, no special hardware is necessary, as modern laptops/phones have WiFi built-in, while the operating system (Windows, macOS, Linux) enables “monitor mode”. Software is widely available and free. We still love our specialized WiFi dongles and directional antennas, but they aren’t really needed anymore.
It’s also legal, as long as you are just grabbing header information and broadcasts. Which is about all that’s useful anymore as encryption has become the norm -- we can pretty much only see what we are allowed to see. The days of grabbing somebody’s session-cookie and hijacking their web email are long gone (though the was a fun period). There are still a few targets around if you want to WiFi hack, but most are gone.
So naturally I wanted to do a survey of what Caesar’s Palace has for WiFi during the DEF CON hacker conference located there.
Here is a list of access-points (on channel 1 only) sorted by popularity, the number of stations using Continue reading
Vagrant Libvirt Install openSUSE
I have recently started using openSUSE as my server platform of choice. This post will go over installing qemu-kvm and libvirt for use with Vagrant and the vagrant-libirt provider on openSUSE. For reference the following software will be used in this post. openSUSE - 15 Vagrant - 2.1.2 ...Vagrant Libvirt Install openSUSE
Install Vagrant and the libvirt provider on OpenSUSE.MikroTik ISP Design: Building an 802.1q trunk between sites using VPLS and S-tag
Use Case
ISPs that use MikroTik are always looking for new ways to deliver services to customers and expand their offerings. Delivering Layer 2 at scale for customers is a design challenge that comes up frequently.
While it’s easy enough to build a VLAN nested inside of another VLAN (see below), this requires you to build all of the VLANs a customer wants to use into the PE router or handoff switch.
However, if you have a client that needs a layer 2 service delivered to two or more points and wants to be able to treat it just like an 802.1q trunk and add VLANs in an ad-hoc way, then using the S-Tag feature in RouterOS along with VPLS transport is a great option.
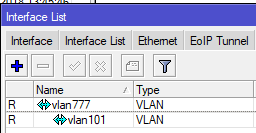
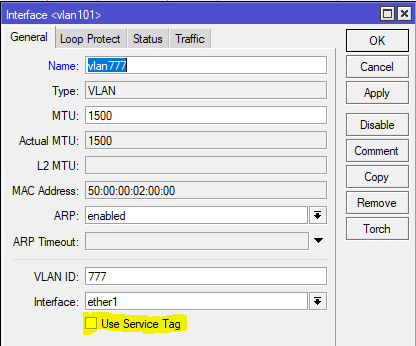
What’s the S-tag do???
Clients will often ask me “what’s the S-Tag check box for?”
So a little background on this, there is a protocol for using outer and inner VLAN tags specified in IEEE 802.1ad that uses Service Tag (or S-Tag) to denote the outer VLAN tag used to transport Customer Tags (or C-Tags).
What makes the S-Tag/C-Tag a little bit different is that it actually changes the ethertype of the Frame.
| Continue reading |
|---|
MikroTik ISP Design: Building an 802.1q trunk between sites using VPLS and S-tag
Use Case
ISPs that use MikroTik are always looking for new ways to deliver services to customers and expand their offerings. Delivering Layer 2 at scale for customers is a design challenge that comes up frequently.
While it’s easy enough to build a VLAN nested inside of another VLAN (see below), this requires you to build all of the VLANs a customer wants to use into the PE router or handoff switch.
However, if you have a client that needs a layer 2 service delivered to two or more points and wants to be able to treat it just like an 802.1q trunk and add VLANs in an ad-hoc way, then using the S-Tag feature in RouterOS along with VPLS transport is a great option.
What’s the S-tag do???
Clients will often ask me “what’s the S-Tag check box for?”
So a little background on this, there is a protocol for using outer and inner VLAN tags specified in IEEE 802.1ad that uses Service Tag (or S-Tag) to denote the outer VLAN tag used to transport Customer Tags (or C-Tags).
What makes the S-Tag/C-Tag a little bit different is that it actually changes the ethertype of the Frame.
| Continue reading |
|---|
Juniper Announces New Acceleration Cards For SRX5000 Security Appliances
Juniper Networks has announced that it will soon begin shipping new SPC3 (Services Process Card) Advanced Security Acceleration cards for its SRX5000 line of security gateways, which includes the 5400, 5600, and 5800 appliances. These security appliances target large enterprises, service providers, and cloud providers. Customers can mix and match security features including firewalling, IPS, […]Iran State-Sponsored Hackers Pose Growing Threat, Accenture Says
 "It’s somebody’s day job to make sure they exploit you and remain a presence on your network,” said Josh Ray, global cyber defense lead for Accenture Security.
"It’s somebody’s day job to make sure they exploit you and remain a presence on your network,” said Josh Ray, global cyber defense lead for Accenture Security.
How many labels for VPN in MPLS
How many labels for VPN in MPLS ? For those who has good amount of knowledge in MPLS already may know the answer. Or if you have taken my CCDE course before, this question is basic for you. But understanding this fundamental piece of knowledge is key to understand MPLS Applications. MPLS …
Continue reading "How many labels for VPN in MPLS"
The post How many labels for VPN in MPLS appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
How many labels for VPN in MPLS
How many labels for VPN in MPLS ? For those who has good amount of knowledge in MPLS already may know the answer. Or if you have taken my CCDE course before, this question is basic for you. But understanding this fundamental piece of knowledge is key to understand MPLS Applications. MPLS …
Continue reading "How many labels for VPN in MPLS"
The post How many labels for VPN in MPLS appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
How many labels for VPN in MPLS
How many labels for VPN in MPLS ? For those who has good amount of knowledge in MPLS already may know the answer. Or if you have taken my CCDE course before, this question is basic for you. But understanding this fundamental piece of knowledge is key to understand MPLS Applications. MPLS […]
The post How many labels for VPN in MPLS appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
SDN, NFV, 5G Part of AT&T’s 2018 Capex Splurge
 “But once you get there those investments you are making to achieve that goal ebb out. They either come down or effectively stabilize,” said CFO John Stephens.
“But once you get there those investments you are making to achieve that goal ebb out. They either come down or effectively stabilize,” said CFO John Stephens.
VMware and Mist Collaborate for Wireless LAN, WAN Visibility and Troubleshooting
 The joint offering boasts interoperability between Mist’s Learning Wireless LAN and VMware VeloCloud-based NSX SD-WAN to bring AI and open programmability to WLAN and WAN.
The joint offering boasts interoperability between Mist’s Learning Wireless LAN and VMware VeloCloud-based NSX SD-WAN to bring AI and open programmability to WLAN and WAN.
Cisco Is Ready To Upgrade a Million Routers With SD-WAN Software
 The Viptela software can run on all Cisco ISR and ASR routers, as well as ENCS 5000 routers, that are four years old or younger.
The Viptela software can run on all Cisco ISR and ASR routers, as well as ENCS 5000 routers, that are four years old or younger.