Ericsson, Qualcomm Achieve 5G Interoperability Using New Standard
 The demo used Ericsson pre-commercial base stations and Qualcomm prototype devices.
The demo used Ericsson pre-commercial base stations and Qualcomm prototype devices.
 The demo used Ericsson pre-commercial base stations and Qualcomm prototype devices.
The demo used Ericsson pre-commercial base stations and Qualcomm prototype devices.

2017 was such a great year for the Ansible team at Red Hat. From launching Ansible Engine to open sourcing Ansible Tower, we’ve had a year to remember. And just in case you missed them, here are our 10 most viewed blog posts of the year to showcase all the fun we’ve had.
Did you know a large portion of Ansible’s functionality comes from the Ansible plugin system? These important pieces of code augment Ansible’s core functionality such as parsing and loading inventory and Playbooks, running Playbooks and reading the results. In this blog, we review each of these plugins and offer a high-level overview on how to write your own plugin to extend Ansible functionality. Read more.
In 2016, we added the first networking modules to Ansible, since then we’ve added hundreds of modules and many networking vendor platforms have been enabled. This year, our focus on networking enablement turned to increasing performance and adding connection methods that provide compatibility and flexibility. You were eager to learn all about it and made this our second most read blog of the year! Read more.
The past year has proven to be one of rapid customer growth and traction in the enterprise. The channel is a fundamental part of our achievements to date and we are grateful for all of the dedicated partners involved in taking container technology mainstream. We now have hundreds of the largest enterprises as customers and we look forward to driving even greater adoption in the coming year alongside our partners.
With 2017 coming to an end, here’s a quick look back at channel achievements from this past year:
At the end of 2016, I wrote a blog post with seven predictions for 2017. Let’s start by reviewing how I did.

Public Domain image by Michael Sharpe
I’ll score myself with two points for being correct, one point for mostly right and zero for wrong. That’ll give me a maximum possible score of fourteen. Here goes...
2017-1: 1Tbps DDoS attacks will become the baseline for ‘massive attacks’
This turned out to be true but mostly because massive attacks went away as Layer 3 and Layer 4 DDoS mitigation services got good at filtering out high bandwidth and high packet rates. Over the year we saw many DDoS attacks in the 100s of Gbps (up to 0.5Tbps) and then in September announced Unmetered Mitigation. Almost immediately we saw attackers stop bothering to attack Cloudflare-protected sites with large DDoS.
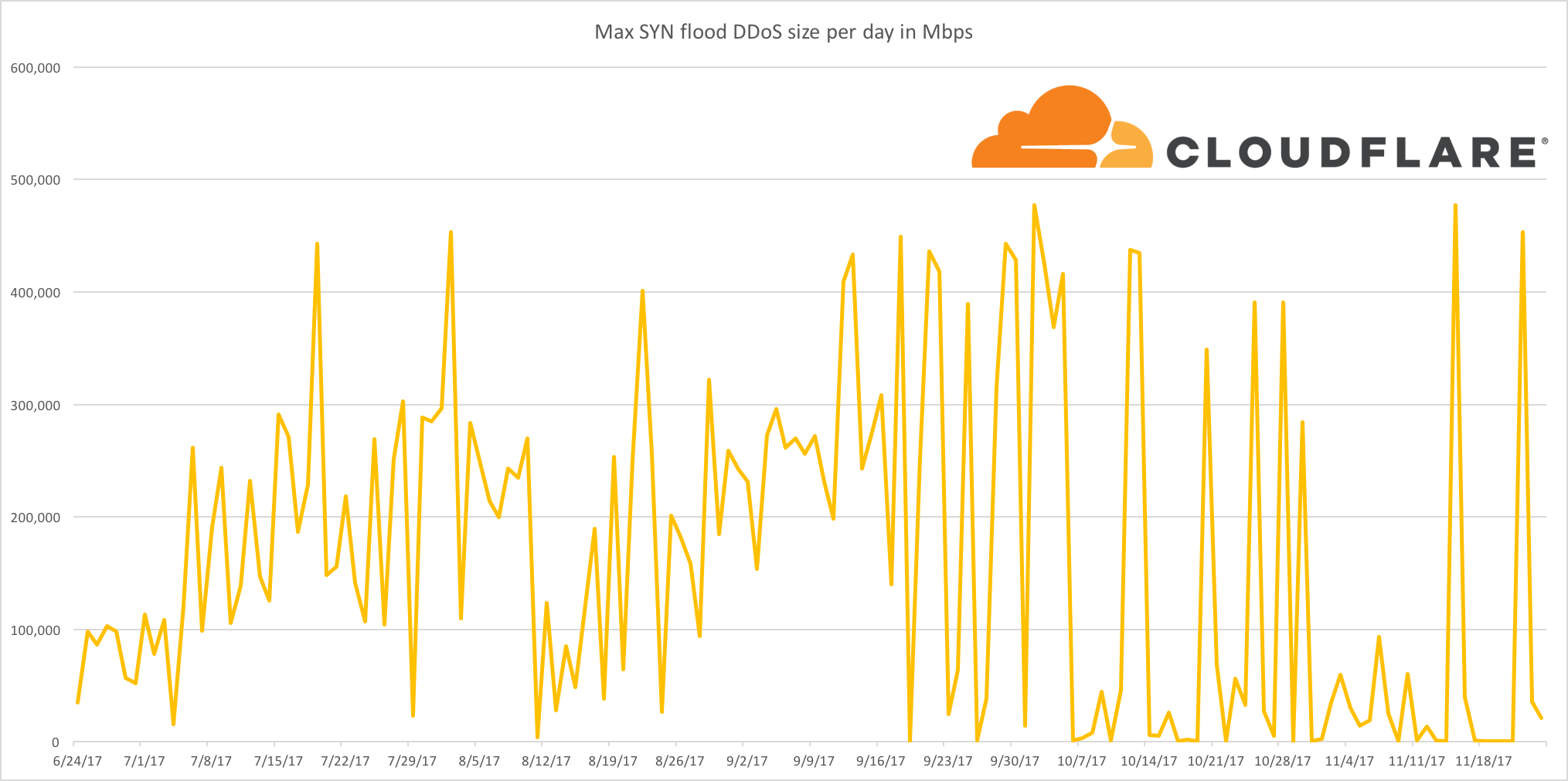
So, I’ll be generous and give myself one point.
2017-2: The Internet will get faster yet again as protocols like QUIC become more prevalent
Well, yes and no. QUIC has become more prevalent as Google has widely deployed it in the Chrome browser and it accounts for about 7% of Internet traffic. At the same time the protocol is working its Continue reading
At the end of 2016, I wrote a blog post with seven predictions for 2017. Let’s start by reviewing how I did.
 Public Domain image by Michael Sharpe
Public Domain image by Michael Sharpe
I’ll score myself with two points for being correct, one point for mostly right and zero for wrong. That’ll give me a maximum possible score of fourteen. Here goes...
2017-1: 1Tbps DDoS attacks will become the baseline for ‘massive attacks’
This turned out to be true but mostly because massive attacks went away as Layer 3 and Layer 4 DDoS mitigation services got good at filtering out high bandwidth and high packet rates. Over the year we saw many DDoS attacks in the 100s of Gbps (up to 0.5Tbps) and then in September announced Unmetered Mitigation. Almost immediately we saw attackers stop bothering to attack Cloudflare-protected sites with large DDoS.

So, I’ll be generous and give myself one point.
2017-2: The Internet will get faster yet again as protocols like QUIC become more prevalent
Well, yes and no. QUIC has become more prevalent as Google has widely deployed it in the Chrome browser and it accounts for about 7% of Internet traffic. At the same time the protocol is working its Continue reading
CloudPassage talked with the Packet Pushers about Container Secure, a product announcement they made at AWS re:Invent earlier this year. Ethan Banks shares his impressions.
The post BiB 022: CloudPassage Adds Container Security To Halo Platform appeared first on Packet Pushers.
All companies can learn something from the EU data protection regulation.
Could you believe it? Another year swooshed by… and it’s high time to stop being snarky and cynical, disconnect from the Internet, and spend a few days with people who really matter – our families.
For me, there’s another large group of people that matter: my users.
Read more ... The 5G NR specification is a stepping stone on the path to a global 5G standard.
The 5G NR specification is a stepping stone on the path to a global 5G standard.
The holidays are a time of joy, gratitude and reflection. As we look back on the year, we’re celebrating you, our amazing customers! You are the ones that make the Docker community special and inspire us to innovate. We appreciate the business and are grateful for the opportunity! With that we’d like to put the spotlight on the top 5 Docker Enterprise Edition (Docker EE) customer stories of 2017.
MetLife, the global provider of insurance, annuities, and employee benefit programs, will be celebrating it’s 150th birthday next year. To stay ahead of the competition, MetLife realizes it must be agile to more rapidly respond to changing market requirements. During the Day 2 General Session at DockerCon 2017, MetLife shared how they’re inspiring new innovation in their organization with Docker EE. MetLife also took part in the Docker MTA program designed to help customers bring portability, security, and efficiency to their traditional applications while saving on their total cost of ownership (TCO). Learn more about the Docker MTA program at Metlife in this video.

In the keynote on Day Continue reading
In my previous post, I focused on the concepts of what is called off box routing and centralized routing. They were two different yet similar solutions. The first one being the simplest solution leveraging an external gateway to route between VXLANs. The second solution integrated the edge device to be both an external gateway and VXLAN end point (VTEP).
To expand on my previous post, the next logical place to put a gateway in VXLAN designs is to distribute them all on the top of rack (TOR), also known as the leaf. This TOR acts as a VTEP in the VXLAN solution. Its primary purpose is to encapsulate and decapsulate traffic. This solution is also colloquially known as Anycast Gateway VXLAN Routing. Anycast Gateway VXLAN Routing can only be performed on ASICs that support routing in and out of tunnels (RIOT), as discussed in the previous post. For the rest of this post, when I refer to VXLAN Routing, I specifically mean Anycast Gateway VXLAN Routing unless otherwise noted.
In the simplest form, VXLAN Routing allows the TOR to perform a route lookup on the inbound packet before encapsulating the traffic into a VXLAN tunnel. There are two ways that Continue reading
 Some organizations are taking the forklift approach too literally.
Some organizations are taking the forklift approach too literally.
 Google encrypts all data at rest and in transit by default.
Google encrypts all data at rest and in transit by default.
 The RAN is the most expensive part of the network.
The RAN is the most expensive part of the network.