Workers AI Update: Stable Diffusion, Code Llama + Workers AI in 100 cities

Thanksgiving might be a US holiday (and one of our favorites — we have many things to be thankful for!). Many people get excited about the food or deals, but for me as a developer, it’s also always been a nice quiet holiday to hack around and play with new tech. So in that spirit, we're thrilled to announce that Stable Diffusion and Code Llama are now available as part of Workers AI, running in over 100 cities across Cloudflare’s global network.
As many AI fans are aware, Stable Diffusion is the groundbreaking image-generation model that can conjure images based on text input. Code Llama is a powerful language model optimized for generating programming code.
For more of the fun details, read on, or head over to the developer docs to get started!

Generating images with Stable Diffusion
Stability AI launched Stable Diffusion XL 1.0 (SDXL) this past summer. You can read more about it here, but we’ll briefly mention some really cool aspects.
First off, “Distinct images can be prompted without having any particular ‘feel’ imparted by the model, ensuring absolute freedom of Continue reading
BGP Labs: AS-Path Prepending
In the previous lab, you learned how to use BGP Multi-Exit Discriminator (MED) to influence incoming traffic flow. Unfortunately, MED works only with parallel links to the same network. In a typical Redundant Internet Connectivity scenario, you want to have links to two ISPs, so you need a bigger hammer: AS Path Prepending.
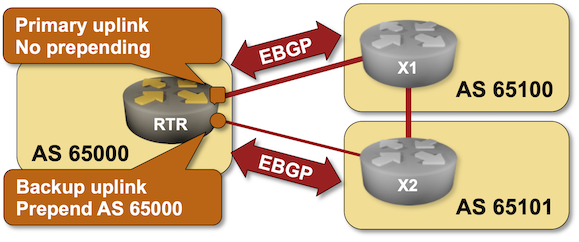
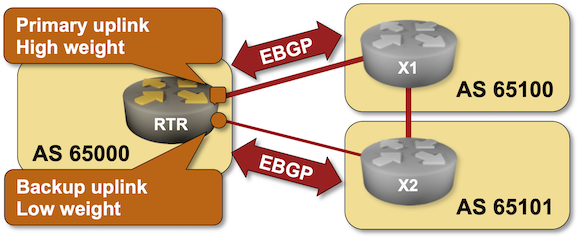
BGP Labs: AS-Path Prepending
In the previous lab, you learned how to use BGP Multi-Exit Discriminator (MED) to influence incoming traffic flow. Unfortunately, MED works only with parallel links to the same network. In a typical Redundant Internet Connectivity scenario, you want to have links to two ISPs, so you need a bigger hammer: AS Path Prepending.
LFNE – Linux For Network Engineers
Formerly known as PFNE – Python For Network Engineer, the images developed to be more than just for Python learning. My choice was to call the new one more generic and pick the Linux For Network Engineers (LFNE) Linux images build with all tools need by network engineers to perform various tasks ranging from simple […]
<p>The post LFNE – Linux For Network Engineers first appeared on IPNET.</p>
A Bright Forecast for Single-Vendor SASE Solutions. What’s Fueling Their Emergence?
The continued rise of single-vendor SASE offerings promises benefits to businesses. What are the pros and cons of the security architecture option?Nvidia Proves The Enormous Potential For Generative AI
The exorbitant cost of GPU-accelerated systems for training and inference and latest to rush to find gold in mountains of corporate data are combining to exert tectonic forces on the datacenter landscape and push up a new Himalaya range – with Nvidia as its steepest and highest peak. …
The post Nvidia Proves The Enormous Potential For Generative AI first appeared on The Next Platform.
Nvidia Proves The Enormous Potential For Generative AI was written by Timothy Prickett Morgan at The Next Platform.
Cisco Intent-Based Networking: Part II – Cisco ISE and Catalyst Center Migration
Cisco Identity Service Engine (ISE) and Catalyst Center Integration
Before you can add Cisco ISE to Catalyst Center’s global network settings as an Authentication, Authorization, and Accounting server (AAA) for clients and manage the Group-Based access policy implemented in Cisco ISE, you must integrate them.
This post starts by explaining how to activate the pxGrid service on ISE, which it uses for pushing policy changes to Catalyst Center (steps 1a-f). Next, it illustrates the procedure to enable External RESTful API (ERS) read/write on Cisco ISE to allow external clients to Create, Read, Update, and Delete (CRUD) processes on ISE. Catalyst Center uses ERS for pushing configuration to ISE. After starting the pxGrid service and enabling ERS, this post discusses how to initiate the connection between ISE and Catalyst Center (steps 2a-h and 3a-b). The last part depicts the Group-Based Access Control migration processes (4a-b).
Step-1: Start pxGrid Service and Enabling ERS on ISE
Open the Administrator tab on the main view of Cisco ISE. Then, under the System tab, select the Deployment option. The Deployment Nodes section displays the Cisco ISE Node along with its personas. In Figure 1-3, a standalone ISE Node is comprised of three personas: Policy Continue reading
D2C221: KubeConversations Part 2 – Building Cloud Platforms
Welcome to part 2 of my KubeConversations. I spent two days in the Windy City attending KubeCon Cloud Native Con Chicago. I had the opportunity to speak to a wide array of vendors and open source maintainers about what’s going on in the cloud native ecosystem. From those conversations, I picked up on some major... Read more »D2C221: KubeConversations Part 2 – Building Cloud Platforms
Ned Bellavance continues his KubeCon conversations with Akamai about cloud-native design and its impact on cloud architecture, Acorn Labs about building a cloud platform, F5 about the networking side of platform engineering, and the startup Chkk about platform engineering and managing Kubernetes.
The post D2C221: KubeConversations Part 2 – Building Cloud Platforms appeared first on Packet Pushers.
Why Do We Need BGP Identifiers?
A friend of mine sent me an interesting question along these lines:
We all know that in OSPF, the router ID is any 32-bit number, not necessarily an IP address of an interface. The only requirement is that it must be unique throughout the OSPF domain. However, I’ve always wondered what the role of BGP router ID is. RFC 4271 says it should be set to an IP address assigned to that BGP speaker, but where do we use it?
Also, he observed somewhat confusing behavior in the wild:
Take two routers and configure the same BGP identifier on both. Cisco IOS will not establish a session, while IOS XR and Junos will.
I decided to take the challenge and dug deep into the bowels of RFC 4271 and RFC 6286. Here’s what I brought back from that rabbit hole:
Why Do We Need BGP Identifiers?
A friend of mine sent me an interesting question along these lines:
We all know that in OSPF, the router ID is any 32-bit number, not necessarily an IP address of an interface. The only requirement is that it must be unique throughout the OSPF domain. However, I’ve always wondered what the role of BGP router ID is. RFC 4271 says it should be set to an IP address assigned to that BGP speaker, but where do we use it?
Also, he observed somewhat confusing behavior in the wild:
Take two routers and configure the same BGP identifier on both. Cisco IOS will not establish a session, while IOS XR and Junos will.
I decided to take the challenge and dug deep into the bowels of RFC 4271 and RFC 6286. Here’s what I brought back from that rabbit hole:
Call the Routing Police!
There is a continual strewam of routing anomalies that are seen in today's Internet. Some are the result of operational mishaps, some are malicious and deliberate, but all of them have some impact. The latest routing mishap in Australia affected some 10 million customers when all their services, including telephony, IP, mobiles and fixed services all stopped. How can we enforce a set of requirements for service operators to do a better job? Where's the Routing Police to chase down these incidents and find out where poor operational practices are compromising the stability of the public Internet?Is Your Infrastructure Ready? What You Need to Know Ahead of an AI Investment
Modernizing the enterprise architecture is a critical path on the journey to becoming a digital, AI, and data-driven business.Workers AI Update: Hello Mistral 7B
This post is also available in Deutsch.

Today we’re excited to announce that we’ve added the Mistral-7B-v0.1-instruct to Workers AI. Mistral 7B is a 7.3 billion parameter language model with a number of unique advantages. With some help from the founders of Mistral AI, we’ll look at some of the highlights of the Mistral 7B model, and use the opportunity to dive deeper into “attention” and its variations such as multi-query attention and grouped-query attention.
Mistral 7B tl;dr:
Mistral 7B is a 7.3 billion parameter model that puts up impressive numbers on benchmarks. The model:
- Outperforms Llama 2 13B on all benchmarks
- Outperforms Llama 1 34B on many benchmarks,
- Approaches CodeLlama 7B performance on code, while remaining good at English tasks, and
- The chat fine-tuned version we’ve deployed outperforms Llama 2 13B chat in the benchmarks provided by Mistral.
Here’s an example of using streaming with the REST API:
curl -X POST \
“https://api.cloudflare.com/client/v4/accounts/{account-id}/ai/run/@cf/mistral/mistral-7b-instruct-v0.1” \
-H “Authorization: Bearer {api-token}” \
-H “Content-Type:application/json” \
-d '{ “prompt”: “What is grouped query attention”, “stream”: true }'
API Response: { response: “Grouped query attention is a technique used in natural language processing (NLP) and machine learning Continue readingIs BGP TTL Security Any Good?
After checking what routers do when they receive a TCP SYN packet from an unknown source, I couldn’t resist checking how they cope with TCP SYN packets with too-low TTL when using TTL security, formally known as The Generalized TTL Security Mechanism (GTSM) defined in RFC 5082.
TL&DR: Not bad: most devices I managed to test did a decent job.
Is BGP TTL Security Any Good?
After checking what routers do when they receive a TCP SYN packet from an unknown source, I couldn’t resist checking how they cope with TCP SYN packets with too-low TTL when using TTL security, formally known as The Generalized TTL Security Mechanism (GTSM) defined in RFC 5082.
TL&DR: Not bad: most devices I managed to test did a decent job.
Trying To Do More Real HPC In An Increasingly AI World
If you are in the traditional HPC community, it is not hard to be of two minds about the rise of AI and the mainstreaming of generative AI. …
The post Trying To Do More Real HPC In An Increasingly AI World first appeared on The Next Platform.
Trying To Do More Real HPC In An Increasingly AI World was written by Timothy Prickett Morgan at The Next Platform.
NB456: China Flexes Tech Muscles With 1.2Tb Backbone; Will CISOs Mitigate Risk Or Liability?
China demonstrates the strength of its home-grown technology industry by announcing a 1.2Tbit Internet backbone that stretches 3,000 kilometers, Fortinet warns of a 9.8 severity bug in its SIEM product, and Nvidia and Dell roll out ready-made models and infrastructure for enterprises to build their own generative AI apps. HPE Aruba Networking releases a new... Read more »NB456: China Flexes Tech Muscles With 1.2Tb Backbone; Will CISOs Mitigate Risk Or Liability?
China demonstrates the strength of its home-grown technology industry by announcing a 1.2Tbit Internet backbone that stretches 3,000 kilometers, Fortinet warns of a 9.8 severity bug in its SIEM product, and we continue our ongoing discussion about the precarious role of the CISO, plus more tech news, in this episode of the Network Break podcast.
The post NB456: China Flexes Tech Muscles With 1.2Tb Backbone; Will CISOs Mitigate Risk Or Liability? appeared first on Packet Pushers.