Commitment to Customer Security


Cloudflare has been hooked on securing customers globally since its inception. Our services protect customer traffic and data as well as our own, and we are continuously improving and expanding those services to respond to the changing threat landscape of the Internet. Proving that commitment is a multi-faceted venture, the Security Team focuses on people, proof, and transparency to ensure every touchpoint with our products and company feels dependable.
People
The breadth of knowledge of the Security Team is wide and bleeding edge. Working as a security team at a security company means being highly technical, diverse, willing to test any and all products on ourselves, and sharing our knowledge with our local and global communities through industry groups and presenting at conferences worldwide. Connecting with our customers and counterparts through meetups and conferences lets us share problems, learn about upcoming industry trends, and share feedback to make improvements to the customer experience. In addition to running a formally documented, risk-based security program for Cloudflare, team members drive continuous improvement efforts across our Product and Infrastructure teams by reviewing and advising on changes, identifying and treating vulnerabilities, controlling authorization and access to systems and data, encrypting data in Continue reading
VMware Widens Its Road To The Cloud With Google Partnership
Google and VMware have announced a new element to their partnership that the two companies said will simplify cloud migrations, provide more flexibility, and help companies modernize their enterprise applications with a minimum amount of pain. …
VMware Widens Its Road To The Cloud With Google Partnership was written by Brandon Vigliarolo at The Next Platform.
Edge. Smart Cities. Retail AI. Oh My!
Regular readers of The Next Platform know there are few more attention-grabbing tech events than Nvidia’s GPU Technology Conference (GTC). …
Edge. Smart Cities. Retail AI. Oh My! was written by David Gordon at The Next Platform.
Zero Trust client sessions
Starting today, you can build Zero Trust rules that require periodic authentication to control network access. We’ve made this feature available for years for web-based applications, but we’re excited to bring this level of granular enforcement to TCP connections and UDP flows.
We’re excited to announce that Zero Trust client-based sessions are now generally available. During CIO Week in 2021, we announced the beta program for this feature. We incorporated feedback from early users into the generally available version. In this post, I will revisit why Zero Trust client-based sessions are important, how the feature works and what we learned during the beta.
Securing traffic with Sessions
We built Zero Trust client-based sessions to enhance the security of Cloudflare’s Zero Trust Network Access (ZTNA). The Zero Trust client is software that runs on a user machine and forwards all traffic from the machine to Cloudflare before it is sent over the Internet. This includes traffic bound for internal IPs and hostnames that typically house sensitive business applications. These sensitive applications were traditionally accessed using a VPN. Unlike VPNs, Cloudflare’s ZTNA allows administrators to set granular policies about who can access a specific resource. The only piece missing was that once Continue reading
Introducing SSH command logging
SSH (Secure Shell Protocol) is an important protocol for managing remote machines. It provides a way for infrastructure teams to remotely and securely manage their fleet of machines. SSH was a step-up in security from other protocols like telnet. It ensures encrypted traffic and enforces per user controls over access to a particular machine. However, it can still introduce a significant security risk. SSH, especially root access, is destructive in the wrong hands (think rm -r *) and can be difficult to track. Logging and securing user actions via SSH typically requires custom development or restrictive software deployments. We’re excited to announce SSH command logging as part of Cloudflare Zero Trust.
Securing SSH access
Security teams put significant effort into securing SSH across their organization because of the negative impact it can have in the wrong hands. Traditional SSH security consists of strong authentication, like certificate based authentication, and tight controls on who has “root” access. Additionally, VPNs and IP allow lists are used to further protect a machine from being publicly accessible to the Internet. The security challenges that remain are visibility and potential for lateral movement.
SSH commands to a remote machine are end-to-end encrypted, which means Continue reading
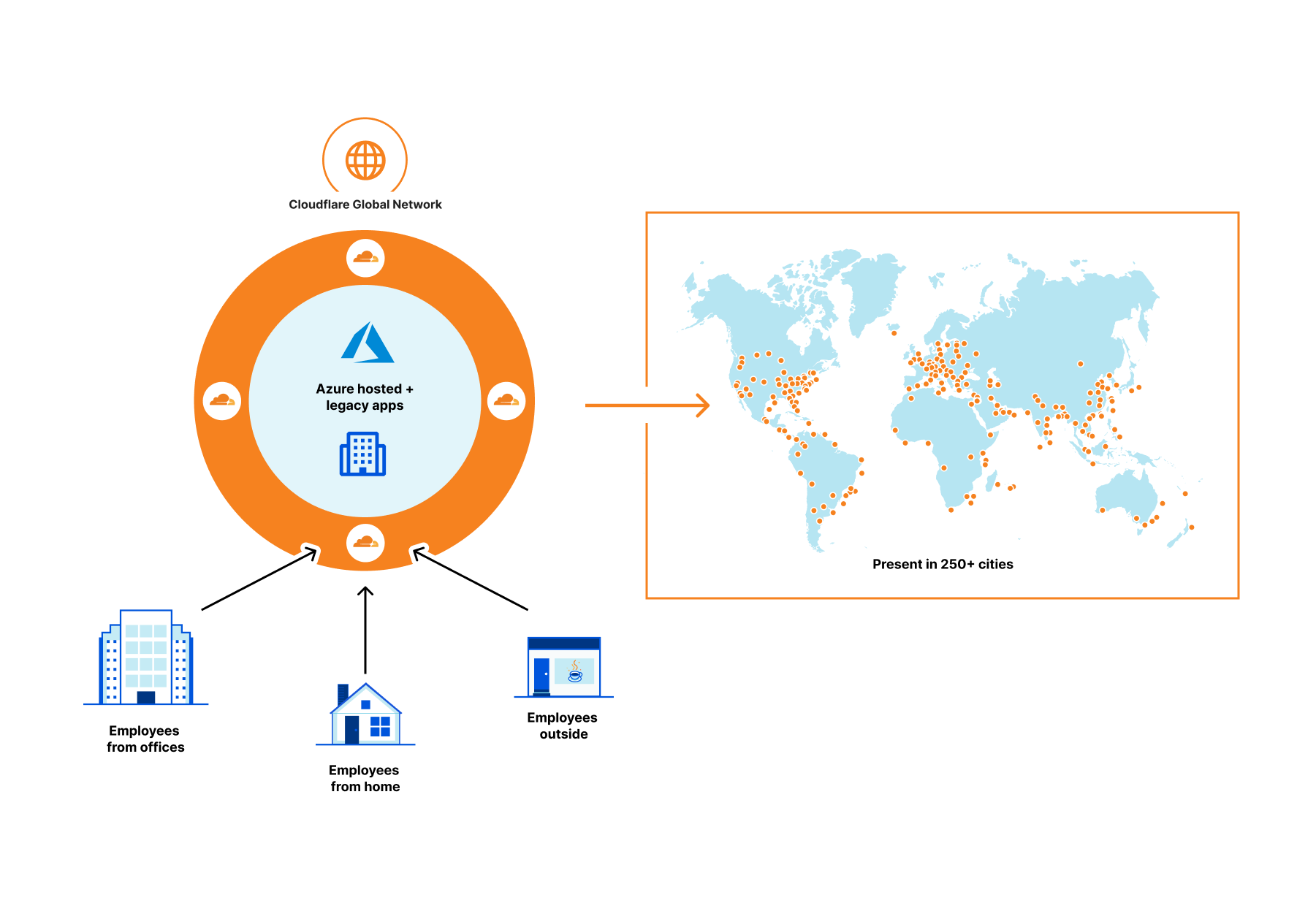
Cloudflare partners with Microsoft to protect joint customers with a Global Zero Trust Network


As a company, we are constantly asking ourselves what we can do to provide more value to our customers, including integrated solutions with our partners. Joint customers benefit from our integrations below with Azure Active Directory by:
First, centralized identity and access management via Azure Active Directory which provides single sign-on, multifactor authentication, and access via conditional authentication.
Second, policy oriented access to specific applications using Cloudflare Access—a VPN replacement service.
Third, an additional layer of security for internal applications by connecting them to Cloudflare global network and not having to open them up to the whole Internet.
Let’s step back a bit.
Why Zero Trust?
Companies of all sizes are faced with an accelerating digital transformation of their IT stack and an increasingly distributed workforce, changing the definition of the security perimeter. We are moving away from the castle and moat model to the whole Internet, requiring security checks for every user accessing every resource. As a result, all companies, especially those whose use of Azure’s broad cloud portfolio is increasing, are adopting Zero Trust architectures as an essential part of their cloud and SaaS journey.
Cloudflare Access provides secure access to Azure hosted applications and Continue reading
A bridge to Zero Trust


Cloudflare One enables customers to build their corporate networks on a faster, more secure Internet by connecting any source or destination and configuring routing, security, and performance policies from a single control plane. Today, we’re excited to announce another piece of the puzzle to help organizations on their journey from traditional network architecture to Zero Trust: the ability to route traffic from user devices with our lightweight roaming agent (WARP) installed to any network connected with our Magic IP-layer tunnels (Anycast GRE, IPsec, or CNI). From there, users can upgrade to Zero Trust over time, providing an easy path from traditional castle and moat to next-generation architecture.
The future of corporate networks
Customers we talk to describe three distinct phases of architecture for their corporate networks that mirror the shifts we’ve seen with storage and compute, just with a 10 to 20 year delay. Traditional networks (“Generation 1”) existed within the walls of a datacenter or headquarters, with business applications hosted on company-owned servers and access granted via private LAN or WAN through perimeter security appliances. As applications shifted to the cloud and users left the office, companies have adopted “Generation 2” technologies like SD-WAN Continue reading
Managing Clouds – Cloudflare CASB and our not so secret plan for what’s next


Last month we introduced Cloudflare’s new API–driven Cloud Access Security Broker (CASB) via the acquisition of Vectrix. As a quick recap, Cloudflare’s CASB helps IT and security teams detect security issues in and across their SaaS applications. We look at both data and users in SaaS apps to alert teams to issues ranging from unauthorized user access and file exposure to misconfigurations and shadow IT.
I’m excited to share two updates since we announced the introduction of CASB functionality to Cloudflare Zero Trust. First, we’ve heard from Cloudflare customers who cannot wait to deploy the CASB and want to use it in more depth. Today, we’re outlining what we’re building next, based on that feedback, to give you a preview of what you can expect. Second, we’re opening the sign-up for our beta, and I’m going to walk through what will be available to new users as they are invited from the waitlist.
What’s next in Cloudflare CASB?
The vision for Cloudflare’s API–driven CASB is to provide IT and security owners an easy-to-use, one-stop shop to protect the security of their data and users across their fleet of SaaS tools. Our goal is to make sure any IT or security Continue reading
Video: Kubernetes Networking Model
After describing the Kubernetes architecture in the introductory part of the excellent Kubernetes Networking Deep Dive webinar, Stuart Charlton focused on what matters most to networking engineers: Kubernetes networking model.
Video: Kubernetes Networking Model
After describing the Kubernetes architecture in the introductory part of the excellent Kubernetes Networking Deep Dive webinar, Stuart Charlton focused on what matters most to networking engineers: Kubernetes networking model.
Capturing Bird Photos
Continuing from the previous post which I have set up to install a bird feeder, I have mentioned that I would install a camera based on the https://mynaturewatch.net/daylight-camera-instructions project and I did install it, this took some really good photos and would like to share some of them.
Few points:
- The battery that I used is a 10000mAh power-bank and it lasted for 2-3 days
- The box that I used is a baby food box and I nailed them to the boundary wooden poles from inside.
- This Bird Feeder is not the one I 3d Printed, this is an old bird feeder that someone gave it to me



Glad to see these pics, many more to come with Idea to install and make it sustain through solar power
-Rakesh
Defense in depth with Calico Cloud
Last month, we announced the launch of our active cloud-native application runtime security. Calico Cloud’s active runtime security helps security teams secure their containerized workloads with a holistic approach to threat detection, prevention, and mitigation.
As security teams look to secure these workloads, it’s also critical that they employ a defense-in-depth strategy. Calico Cloud’s active runtime security can detect, prevent, and mitigate threats across the entire cyber kill chain for containerized workloads.
What is the cyber kill chain?
The cyber kill chain is a framework used to track the steps a threat actor might take as they attempt to execute a cyber attack on your organization. The cyber kill chain was originally developed by Lockheed Martin to adapt the military concept that details the structure of an attack for cybersecurity threats. Today, this framework is used by security teams from a wide range of organizations to understand and respond to cybersecurity threats.
The Lockheed Martin cyber kill chain consists of seven stages:
- Reconnaissance: An attacker assesses potential targets and tactics for an attack
- Weaponization: An attacker prepares the attack by obtaining or setting up the appropriate infrastructure
- Delivery: An attacker launches their attack
- Exploitation: An attacker gains access to their Continue reading
Liqid Launches Its Own Systems, Chases AI And HPC
To hardware or not to hardware, that is a real question for vendors peddling all kinds of software in the datacenter. …
Liqid Launches Its Own Systems, Chases AI And HPC was written by Timothy Prickett Morgan at The Next Platform.