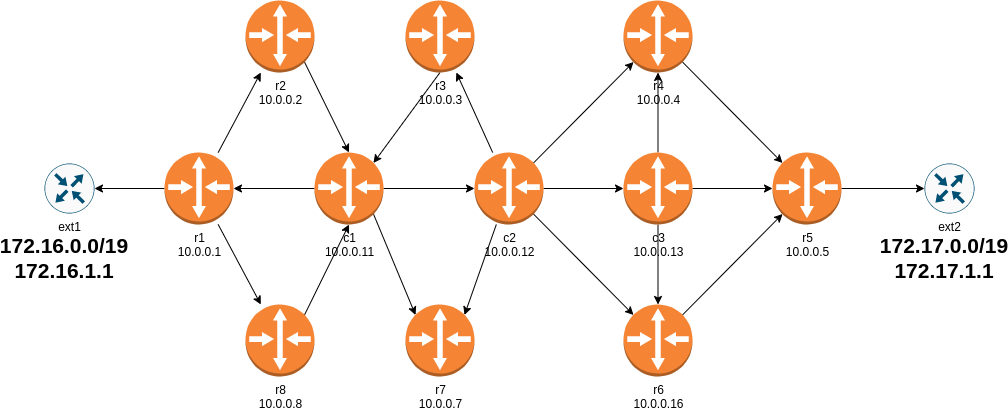
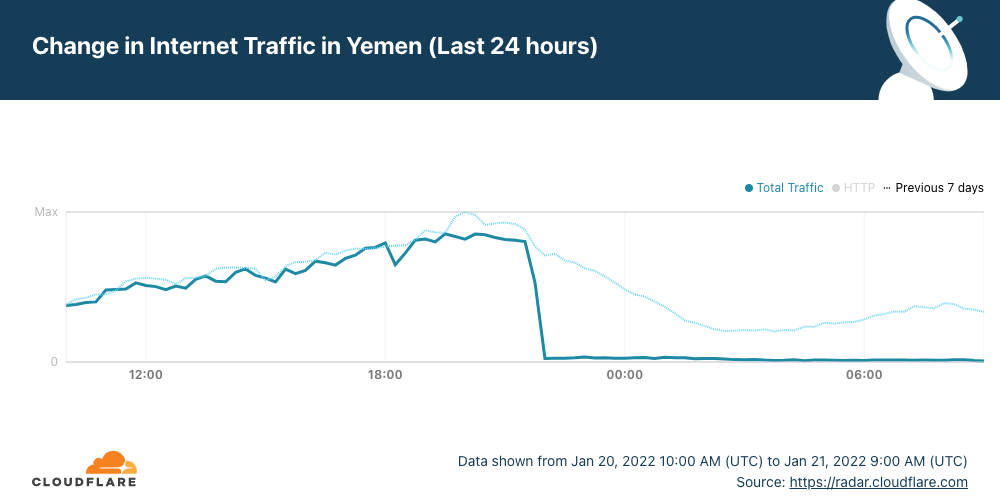
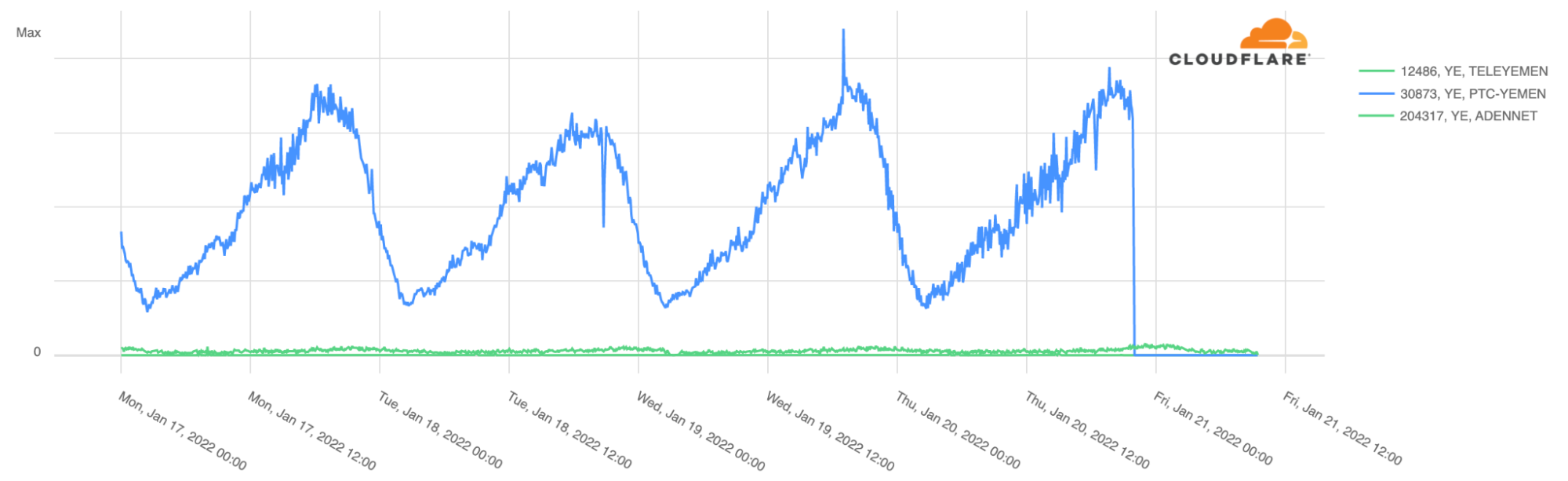
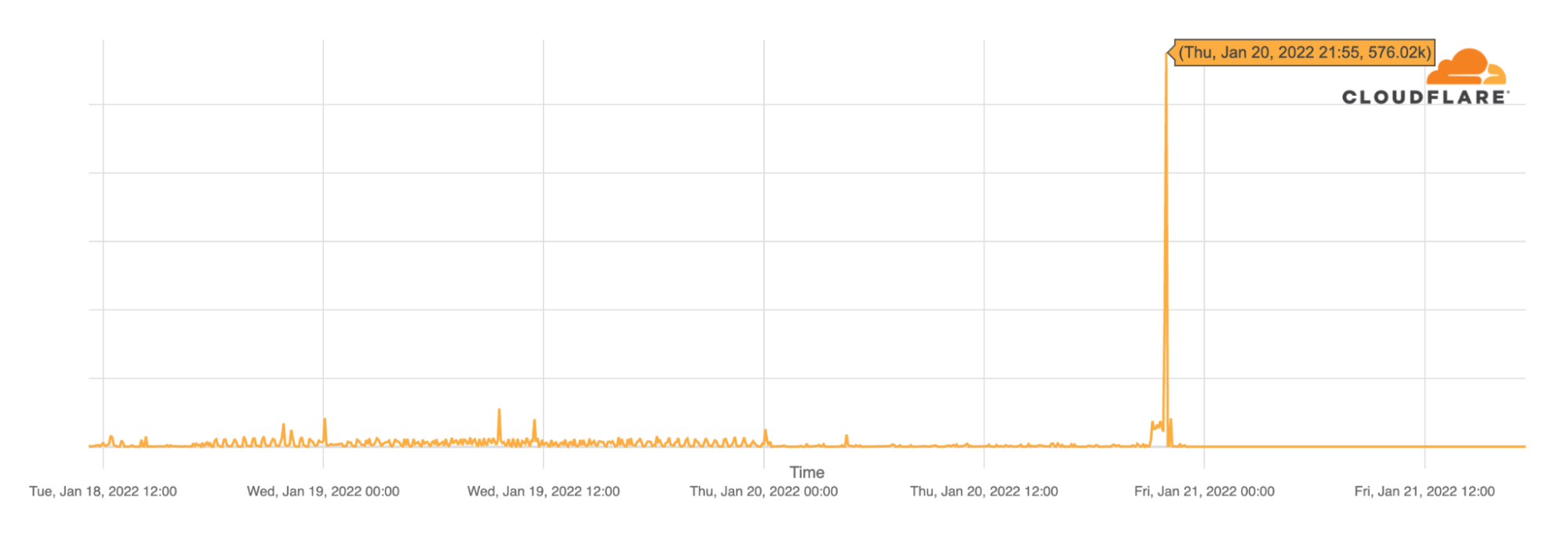
0
Dell expands Apex cloud and on-prem storage options
Dell Technologies is charging ahead with its Apex consumption-based sales portfolio with a total of seven new launches, while also expanding its public cloud integration for a broader multi-cloud experience for its customers.Dell sees the writing on the wall and that the future is hybrid and multicloud. Today, 92% of organizations have a multi-cloud strategy in place or underway, and 82% of large enterprises have adopted a hybrid cloud infrastructure. And a new Forrester study commissioned by Dell Technologies found that 83% of organizations have adopted a multi-cloud approach or plan to within the next 12 months.To read this article in full, please click here