Day Two Cloud 114: Successfully Transitioning From A Tech Role To Management
Today's Day Two Cloud podcast topic is about moving from a tech role into management. Is it a good idea? Why might you want to make the change? How can you do it successfully? We speak with two guests who've made the leap.
The post Day Two Cloud 114: Successfully Transitioning From A Tech Role To Management appeared first on Packet Pushers.
Lenovo Bundles VMware Stack At The Edge
Enterprises and tech vendors alike for the past few years have been talking about the growing importance of the edge in the increasingly distributed IT environment. …
Lenovo Bundles VMware Stack At The Edge was written by Jeffrey Burt at The Next Platform.
Introducing: Custom Hostname Analytics


In our last blog, we talked about how Cloudflare can help SaaS providers extend the benefits of our network to their customers. Today, we’re excited to announce that SaaS providers will now be able to give their customers visibility into what happens to their traffic when the customer onboards onto the SaaS provider, and inherently, onto the Cloudflare network.
As a SaaS provider, you want to see the analytics about the traffic bound for your service. Use it to see the global distribution of your customers, or to measure the success of your business. In addition to that, you want to provide the same insights to your individual customers. That’s exactly what Custom Hostname Analytics allows you to do!
The SaaS Setup
Imagine you run a SaaS service for burrito shops, called The Burrito Bot. You have your burrito service set up on shop.theburritobot.com and your customers can use your service either through a subdomain of your zone, i.e. dina.theburritobot.com, or through their own website e.g. burrito.example.com.
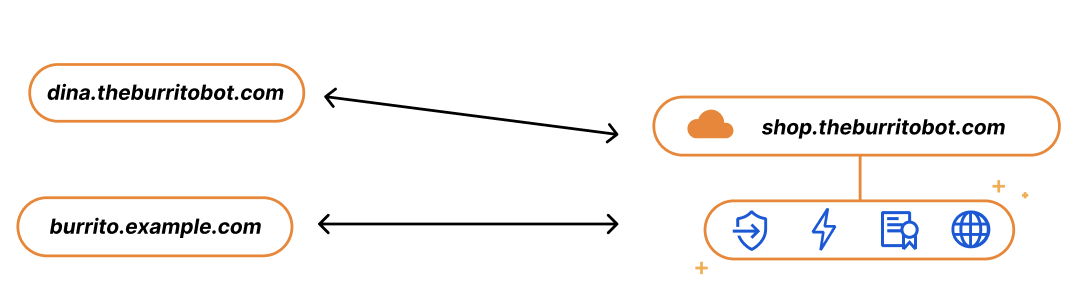
When customers onboard to your burrito service, they become fully reliant on you to provide their website with the fastest load time, the Continue reading
How Cloudflare helped mitigate the Atlassian Confluence OGNL vulnerability before the PoC was released
On August 25, 2021, Atlassian released a security advisory for their Confluence Server and Data Center. The advisory highlighted an Object-Graph Navigation Language (OGNL) injection that would result in an unauthenticated attacker being able to execute arbitrary code.
A full proof of concept (PoC) of the attack was made available by a security researcher on August 31, 2021. Cloudflare immediately reviewed the PoC and prepared a mitigation rule via an emergency release. The rule, once tested, was deployed on September 1, 2021, at 15:32 UTC with a default action of BLOCK and the following IDs:
100400(for our legacy WAF)e8c550810618437c953cf3a969e0b97a(for our new WAF)
All customers using the Cloudflare WAF to protect their self-hosted Confluence applications have automatically been protected since the new rule was deployed last week. Additionally, the Cloudflare WAF started blocking a high number of potentially malicious requests to Confluence applications even before the rule was deployed.
And customers who had deployed Cloudflare Access in front of their Confluence applications were already protected even before the emergency release. Access checks every request made to a protected hostname for a JSON Web Token (JWT) containing a user’s identity. Any unauthenticated users attempting this exploit Continue reading
Open-Source DMVPN Alternatives
When I started collecting topics for the September 2021 ipSpace.net Design Clinic one of the subscribers sent me an interesting challenge: are there any open-source alternatives to Cisco’s DMVPN?
I had no idea and posted the question on Twitter, resulting in numerous responses pointing to a half-dozen alternatives. Thanks a million to @MarcelWiget, @FlorianHeigl1, @PacketGeekNet, @DubbelDelta, @Tomm3h, @Joy, @RoganDawes, @Yassers_za, @MeNotYouSharp, @Arko95, @DavidThurm, Brian Faulkner, and several others who chimed in with additional information.
Here’s what I learned:
Open-Source DMVPN Alternatives
When I started collecting topics for the September 2021 ipSpace.net Design Clinic one of the subscribers sent me an interesting challenge: are there any open-source alternatives to Cisco’s DMVPN?
I had no idea and posted the question on Twitter, resulting in numerous responses pointing to a half-dozen alternatives. Thanks a million to @MarcelWiget, @FlorianHeigl1, @PacketGeekNet, @DubbelDelta, @Tomm3h, @Joy, @RoganDawes, @Yassers_za, @MeNotYouSharp, @Arko95, @DavidThurm, Brian Faulkner, and several others who chimed in with additional information.
Here’s what I learned:
What’s new in Calico Enterprise 3.9: Live troubleshooting and resource-efficient application-level observability
We are excited to announce Calico Enterprise 3.9, which provides faster and simpler live troubleshooting using Dynamic Packet Capture for organizations while meeting regulatory and compliance requirements to access the underlying data. The release makes application-level observability resource-efficient, less security intrusive, and easier to manage. It also includes pod-to-pod encryption with Microsoft AKS and AWS EKS with AWS CNI.
Live troubleshooting
Enterprises that want to carry out live troubleshooting in their production environments face the following challenges when doing packet capture at an organizational scale:
- Difficult to limit access to packet capture by organizational roles
- Takes hours to days to setting up packet capture instead of making part of the code
- Extremely difficult to capture the right amount of data to lessen storage and compute cost
- Spend days and weeks to correlate the data collected from different Kubernetes components such as namespaces, workloads, pods, microservices
With Dynamic Packet Capture, organizations can enable DevOps, SREs, service owners to collect the data that they need when they need it. They can filter the data based on protocol and port to fine-tune their capture for faster debugging and subsequent analysis for shorter time-to-resolution. With just-in-time data collection and built-in smart correlation, Continue reading
Tier 1 Carriers Performance Report: August, 2021
The post Tier 1 Carriers Performance Report: August, 2021 appeared first on Noction.
The CXL Roadmap Opens Up The Memory Hierarchy
The system world would have been a simpler place if InfiniBand had fulfilled its original promise as a universal fabric interconnect for linking all manner of devices together within a system and across systems. …
The CXL Roadmap Opens Up The Memory Hierarchy was written by Timothy Prickett Morgan at The Next Platform.
AWS EC2 Pioneer on Early Days, Next Wave
Dave Brown remembers when Amazon executives would pop into their small office in Cape Town, populated by the entire EC2 team of fourteen, and tell them they would be working for a billion-dollar business one day. …
AWS EC2 Pioneer on Early Days, Next Wave was written by Nicole Hemsoth at The Next Platform.
Network Break 349: T-Mobile Fails To Protect Millions Of Customer Records; Ciena Buys Vyatta Router
Today's Network Break podcast opines on why Ciena acquired the Vyatta router from AT&T (and why AT&T wanted to sell), how T-Mobile failed current and former customers via a breach that exposed sensitive details on millions of people, financial results from HPE and Dell Technologies, and more.Network Break 349: T-Mobile Fails To Protect Millions Of Customer Records; Ciena Buys Vyatta Router
Today's Network Break podcast opines on why Ciena acquired the Vyatta router from AT&T (and why AT&T wanted to sell), how T-Mobile failed current and former customers via a breach that exposed sensitive details on millions of people, financial results from HPE and Dell Technologies, and more.
The post Network Break 349: T-Mobile Fails To Protect Millions Of Customer Records; Ciena Buys Vyatta Router appeared first on Packet Pushers.
Container Security Best Practices
A specialist responsible for container security should have an understanding of the infrastructure and proficiency in Linux and Kubernetes.What’s new with Cloudflare for SaaS?
This past April, we announced the Cloudflare for SaaS Beta which makes our SSL for SaaS product available to everyone. This allows any customer — from first-time developers to large enterprises — to use Cloudflare for SaaS to extend our full product suite to their own customers. SSL for SaaS is the subset of Cloudflare for SaaS features that focus on a customer’s Public Key Infrastructure (PKI) needs.
Today, we’re excited to announce all the customizations that our team has been working on for our Enterprise customers — for both Cloudflare for SaaS and SSL for SaaS.
Let’s start with the basics — the common SaaS setup
If you’re running a SaaS company, your solution might exist as a subdomain of your SaaS website, e.g. template.<mysaas>.com, but ideally, your solution would allow the customer to use their own vanity hostname for it, such as example.com.
The most common way to begin using a SaaS company’s service is to point a CNAME DNS record to the subdomain that the SaaS provider has created for your application. This ensures traffic gets to the right place, and it allows the SaaS provider to make infrastructure changes without Continue reading
BGP with Link State (LS) and the reasons for BGP-LS use
The post BGP with Link State (LS) and the reasons for BGP-LS use appeared first on Noction.
Non-Stop Forwarding (NSF) 101
Non-Stop Forwarding (NSF) is one of those ideas that look great in a slide deck and marketing collaterals, but might turn into a giant can of worms once you try to implement them properly (see also: stackable switches or VMware Fault Tolerance).