Tech Bytes: Wi-Fi 6E – New Spectrum, New Opportunities (Sponsored)
Today’s Tech Bytes podcast dives into Wi-Fi 6E, the extended version of the Wi-Fi 6 standard that takes advantage of newly available spectrum in the 6 GHz band. We’re sponsored today by Aruba, a Hewlett Packard Enterprise company, and we’ll explore highlights of the standard and discuss Aruba’s forthcoming 6E AP.
The post Tech Bytes: Wi-Fi 6E – New Spectrum, New Opportunities (Sponsored) appeared first on Packet Pushers.
Broadband Options: Fiber, Satellite, and Wi-Fi, Oh My!
Infrastructure investments for broadband service delivery can flow in many directions, but making wise decisions will maximize the value.Network Break 336: Cisco Announces Cloud ACI And More; Amazon Borrows Wi-Fi Without Asking
Cisco debuts Cloud ACI to unify segmentation policies on prem and in the public cloud, Amazon will activate an opt-out mesh network using your Ring and Echo devices, Microsoft buys an IoT security company, and more tech news in this week's Network Break podcast.Network Break 336: Cisco Announces Cloud ACI And More; Amazon Borrows Wi-Fi Without Asking
Cisco debuts Cloud ACI to unify segmentation policies on prem and in the public cloud, Amazon will activate an opt-out mesh network using your Ring and Echo devices, Microsoft buys an IoT security company, and more tech news in this week's Network Break podcast.
The post Network Break 336: Cisco Announces Cloud ACI And More; Amazon Borrows Wi-Fi Without Asking appeared first on Packet Pushers.
The Week in Internet News: Yet Another Ransomware Attack

Where’s the beef? Cybercriminals, likely from Russia, shut down a Brazilian meatpacker’s operation for a couple of days using ransomware, Reuters reports. The attack on JBS, the world’s largest meatpacker, came just weeks after ransomware, also likely from Russia, shut down the Colonial Pipeline in the U.S. for several days. The U.S. FBI blamed the […]
The post The Week in Internet News: Yet Another Ransomware Attack appeared first on Internet Society.
Changes to Docker Hub Autobuilds
As many of you are aware, it has been a difficult period for companies offering free cloud compute [1]. Unfortunately, Docker’s Autobuild service has been targeted by the same bad actors, so today we are disappointed to announce that we will be discontinuing Autobuilds on the free tier starting from June 18, 2021.
In the last few months we have seen a massive growth in the number of bad actors who are taking advantage of this service with the goal of abusing it for crypto mining. For the last 7 years we have been proud to offer our Autobuild service to all our users as the simplest way to set up CI for containerized projects. As well as the increased cost of running the service, this type of abuse periodically impacts performance for paying Autobuild users and induces many sleepless nights for our team 
In April we saw the number of build hours spike 2X our usual load and by the end of the month we had already deactivated ~10,000 accounts due to mining abuse The following week we had another ~2200 miners spin up.

As a result of this we have made the hard choice to remove Autobuilds Continue reading
Feedback: Azure Networking
When I started developing AWS- and Azure Networking webinars, I wondered whether they would make sense – after all, you can easily find tons of training offerings focused on public cloud services.
However, it looks like most of those materials focus on developers (no wonder – they are the most significant audience), with little thought being given to the needs of network engineers… at least according to the feedback left by one of ipSpace.net subscribers.
Feedback: Azure Networking
When I started developing AWS- and Azure Networking webinars, I wondered whether they would make sense – after all, you can easily find tons of training offerings focused on public cloud services.
However, it looks like most of those materials focus on developers (no wonder – they are the most significant audience), with little thought being given to the needs of network engineers… at least according to the feedback left by one of ipSpace.net subscribers.
Worth Reading: The Neuroscience of Busyness
In the Neuroscience of Busyness article, Cal Newport describes an interesting phenomenon: when solving problems, we tend to add components instead of removing them.
If that doesn’t describe a typical network (or protocol) design, I don’t know what does. At least now we have a scientific basis to justify our behavior ;)
Worth Reading: The Neuroscience of Busyness
In the Neuroscience of Busyness article, Cal Newport describes an interesting phenomenon: when solving problems, we tend to add components instead of removing them.
If that doesn’t describe a typical network (or protocol) design, I don’t know what does. At least now we have a scientific basis to justify our behavior ;)
EVE-NG Cloud NAT
This post explains how to configure EVE-NG as a DHCP server (isc-dhcp-server) assigning IPs to lab devices that are then dynamically NATed behind the primary EVE management IP address (iptables masquerade) to provide Internet breakout.
Worth Reading: Switching to IP fabrics
Namex, an Italian IXP, decided to replace their existing peering fabric with a fully automated leaf-and-spine fabric using VXLAN and EVPN running on Cumulus Linux.
They documented the design, deployment process, and automation scripts they developed in an extensive blog post that’s well worth reading. Enjoy ;)
Worth Reading: Switching to IP fabrics
Namex, an Italian IXP, decided to replace their existing peering fabric with a fully automated leaf-and-spine fabric using VXLAN and EVPN running on Cumulus Linux.
They documented the design, deployment process, and automation scripts they developed in an extensive blog post that’s well worth reading. Enjoy ;)
MikroTik – RouterOSv7 first look – MLAG on CRS 3xx switches
What is MLAG?
Multi-Chassis Link Aggregation Group or MLAG is an idea that’s been around for a while.
It allows for the ability to form LACP channels across multiple physical switches.
Wikipedia shows a few different topology examples here
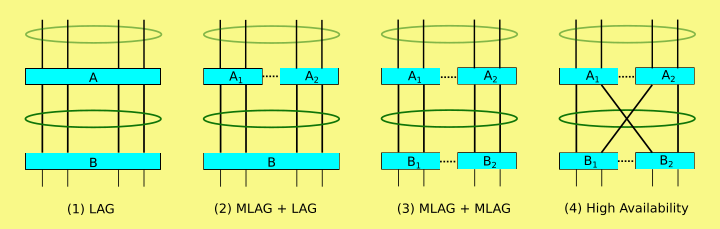
Vendor implementations are proprietary but the idea of MLAG was first mentioned in 802.1AX-2008 in 2008.
It first started to become popular in data center networking in the late 2000s
What makes the addition of MLAG to MikroTik’s RouterOS feature set notable is that it lowers the barrier to entry for this particular feature.
CRS 3xx switches are very inexpensive (starting at $149 USD) and may very well be the lowest cost MLAG capable hardware available on the market.

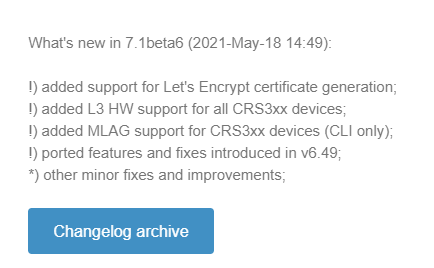
Introduced in 7.1beta6
MLAG has been asked for by the MikroTik community a number of times and the most active feature request thread started here in 2020:
new feature request MLAG!!! – MikroTik
MikroTik added several version 7 beta releases in 2021 and included MLAG for all CRS 3xx series switches in 7.1beta6 on May 18th, 2021.
Overview of protocol requirements
MLAG is fairly consistent across vendors with the need Continue reading