Domain Name System Security Extensions Now Deployed in all Generic Top-Level Domains – ICANN
 Well huh, it wasn't done already ?
Well huh, it wasn't done already ?
Considerations for Host-based Firewalls (Part 2)
This is a guest blog post by Matthias Luft, Principal Platform Security Engineer @ Salesforce, and a regular ipSpace.net guest speaker.
A couple of months ago I had the pleasure to publish my first guest post here and, as to be expected from ipspace.net, it triggered some great discussion.
With this input and some open thoughts from the last post, I want to dive into a few more topics.
Considerations for Host-based Firewalls (Part 2)
This is a guest blog post by Matthias Luft, Principal Platform Security Engineer @ Salesforce, and a regular ipSpace.net guest speaker.
A couple of months ago I had the pleasure to publish my first guest post here and, as to be expected from ipspace.net, it triggered some great discussion.
With this input and some open thoughts from the last post, I want to dive into a few more topics.
Application Engineering vs. (?) Network Engineering
One trigger for the initial post was the question whether host-based firewalls (HBFs), potentially combined with solutions to learn rulesets based on flows, are intrinsically better than central firewalls. While we discussed the mileage around that already, comments and questions emphasized how often we have to handle a “software engineering vs. network engineering” mentality – which should not involve any blame in either direction as this mindset is usually enforced by organizational structures.
For whatever it is worth, I can only stress the point that a strong collaboration between software and network engineering will resolve way more issues than any technology. I award myself a “Thanks, Captain Obvious” here, but I still want to make the point to try Continue reading
BizOps: Powering Data-Driven Decision Making
Business and IT alignment is more vital than ever. What's needed is BizOps, a framework for data-driven decision making.The Hedge Podcast #65: Jacquelyn Adams and the Future of Work

Everyone in networking—and beyond networking, in fact—thinks about what the future of work might look like. Jacquelyn Adams joins Eyvonne Sharp, Tom Ammon, and Russ White on this episode of the Hedge to discuss what work might look like based on this era of rapid change, and how you can prepare for that future.
Internet traffic disruption caused by the Christmas Day bombing in Nashville
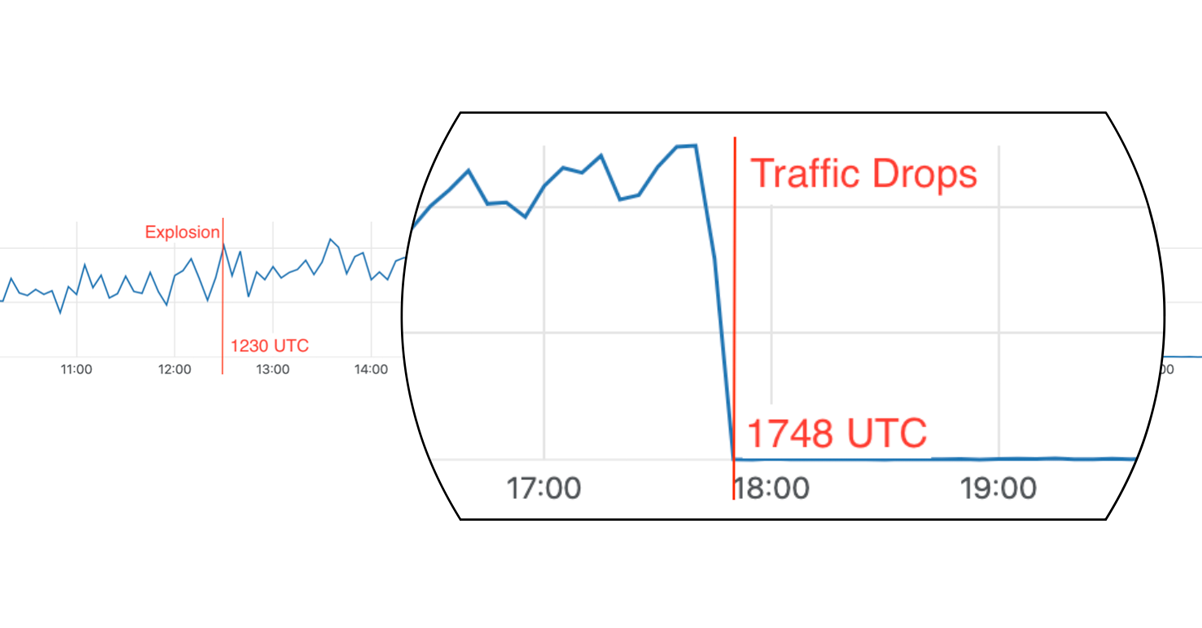
On Christmas Day 2020, an apparent suicide bomb exploded in Nashville, TN. The explosion happened outside an AT&T network building on Second Avenue in Nashville at 1230 UTC. Damage to the AT&T building and its power supply and generators quickly caused an outage for telephone and Internet service for local people. These outages continued for two days.
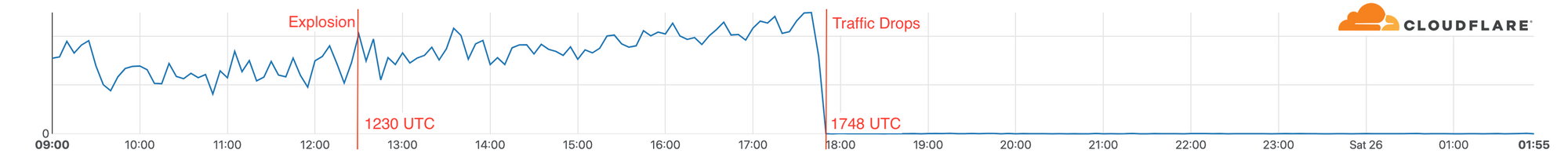
Looking at traffic flow data for AT&T in the Nashville area to Cloudflare we can see that services continued operating (on battery power according to reports) for over five hours after the explosion, but at 1748 UTC we saw a dramatic drop in traffic. 1748 UTC is close to noon in Nashville when reports indicate that people lost phone and Internet service.
We saw traffic from Nashville via AT&T start to recover over a 45 minute period on December 27 at 1822 UTC making the total outage 2 days and 34 minutes.
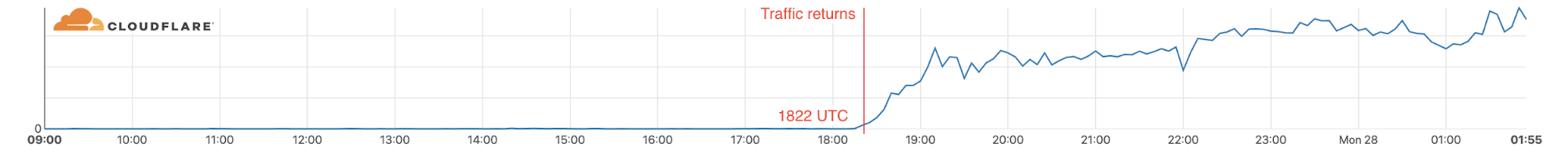
Traffic flows continue to be normal and no further disruption has been seen.
How Change Review Boards Really Work to Fail
 Its supposed to enable change but reality is about preventing change.
Its supposed to enable change but reality is about preventing change.
IBGP, IGP Metrics, and Administrative Distances
TL&DR: If you run multiple IGP protocols in your network, and add BGP on top of that, you might get the results you deserve. Even better, the results are platform-dependent.
One of my readers sent me a link to an interesting scenario described by Jeremy Filliben that results in totally unexpected behavior when using too many routing protocols in your network (no surprise there).
Imagine a network in which two edge routers advertise the same (external) BGP prefix. All other things being equal, it would make sense that other routers in the same autonomous system should use the better path out of the autonomous system. Welcome to the final tie-breaker in BGP route selection process: IGP metric.
IBGP, IGP Metrics, and Administrative Distances
TL&DR: If you run multiple IGP protocols in your network, and add BGP on top of that, you might get the results you deserve. Even better, the results are platform-dependent.
One of my readers sent me a link to an interesting scenario described by Jeremy Filliben that results in totally unexpected behavior when using too many routing protocols in your network (no surprise there).
Imagine a network in which two edge routers advertise the same (external) BGP prefix. All other things being equal, it would make sense that other routers in the same autonomous system should use the better path out of the autonomous system. Welcome to the final tie-breaker in BGP route selection process: IGP metric.
From AI to 5G, How Global Trends Will Transform Data Centers in 2021
Data centers are poised to undergo rapid change as businesses adjust to accelerated digitization of information.Add Friendly ID to a Rails 6 App
How to add nice URLs to your Rails 6 app using Friendly ID.George Sadowsky on the History of Networking
George Sadowsky was a pioneer in recognizing the importance of networking technology for economic development, particularly in developing economies. He has worked in over 50 countries to bring training and networking infrastructure to the local population. In this episode of the History of Networking, George recounts some of the early, pre-Internet, work in computer networking, and the development of many of the organizations that make the Internet work today. His web site can be found here.
Reimagining Accelerators with Sparsity at the Core
There could be a new era of codesign dawning for machine learning, one that moves away from the training and inference separations and toward far less dense networks with highly sparse weights and activations. …
Reimagining Accelerators with Sparsity at the Core was written by Nicole Hemsoth at The Next Platform.
Tools 3. Checking your connectivity bandwidth with Speedtest
Hello my friend,
Continuing our discussion about the network troubleshooting tools we can’t pass by one of the most popular and widely used, which is named SpeedTest.
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
Can automation help with performance troubleshooting?
Doing the collection and initial analysis of the information during the troubleshooting could be quite a time-consuming task. On the other hand, the troubleshooting of the live outages should be as quick as possible to minimise the downtime of the affected services. That’s where the automation can help you.

In our network automation training we explain how to use existing open-source tools and create your own with Ansible, Bash and Python. Leveraging them and all possible interfaces (CLI, NETCONF, RESTCONF, gNMI) we teach you how to effectively build, operate and troubleshoot your network.
Brief description
From the name of the tool, SpeedTest, it is obvious that the main goal is to measure the “speed”. In fact, it measures Continue reading