Counting The Cost Of Under-Utilized GPUs – And Doing Something About It
The compute engines keep changing as the decades pass, but the same old problems keep cropping up in slightly different form. …
Counting The Cost Of Under-Utilized GPUs – And Doing Something About It was written by Timothy Prickett Morgan at The Next Platform.
OpenShift At The Center Of The Hybrid Cloud Storm
For several years, IBM has been eyeing the hybrid cloud, remaking itself into a provider with the platform that can enable enterprises to more easily move their workloads and data between their on-premises datacenters and the public cloud, and the multiple public clouds they are using. …
OpenShift At The Center Of The Hybrid Cloud Storm was written by Jeffrey Burt at The Next Platform.
Anchoring Trust: A Hardware Secure Boot Story
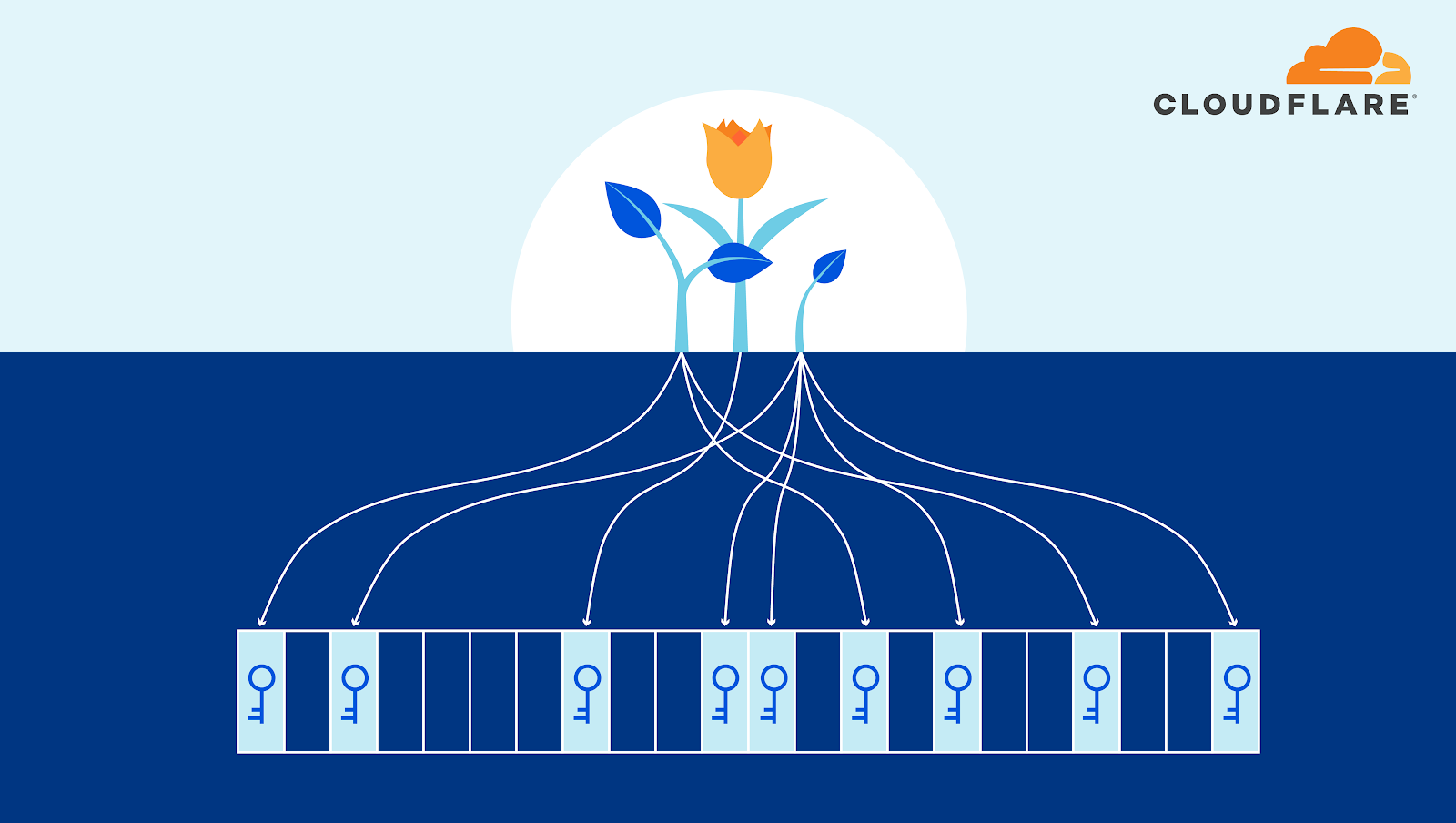
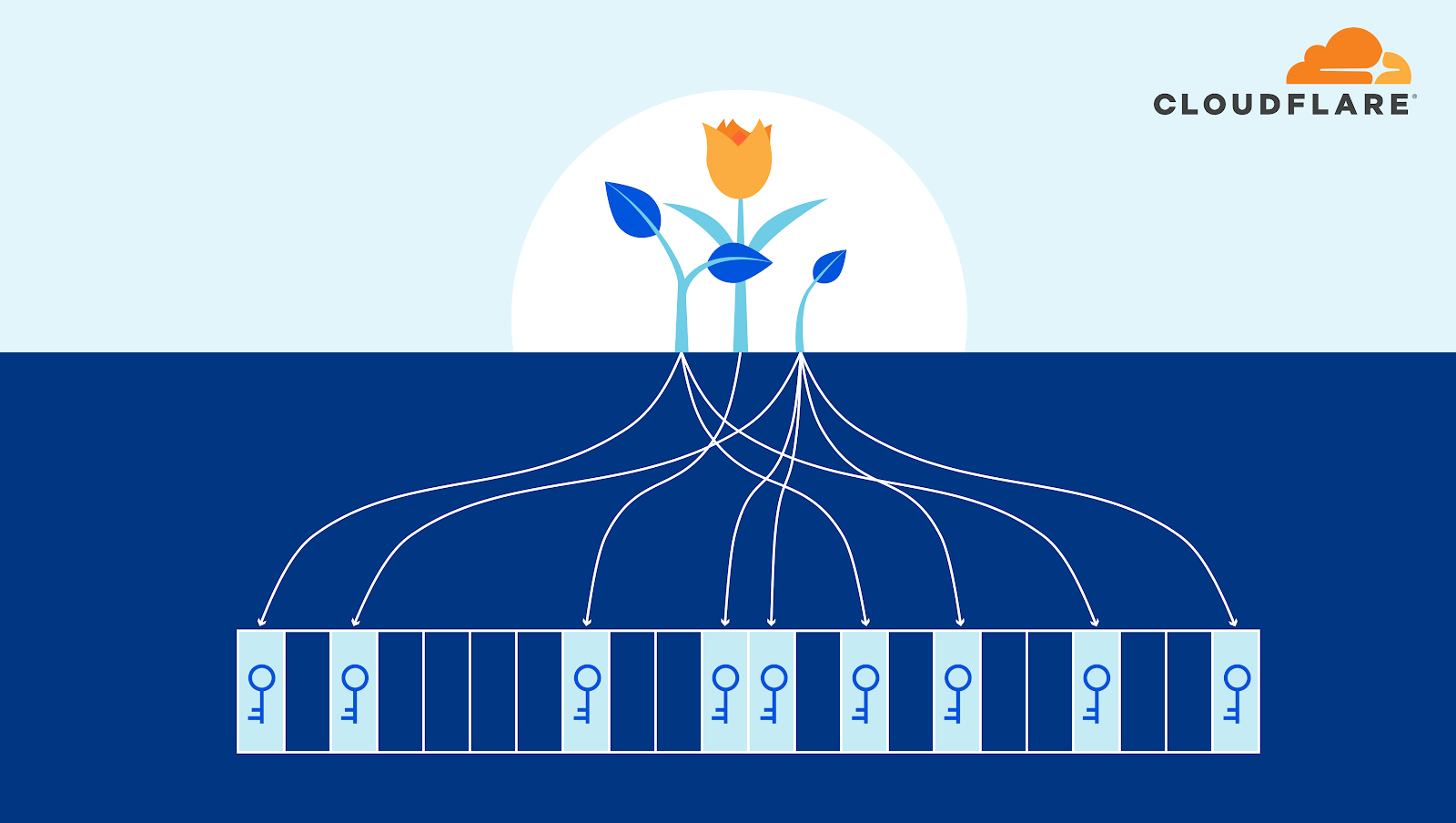
As a security company, we pride ourselves on finding innovative ways to protect our platform to, in turn, protect the data of our customers. Part of this approach is implementing progressive methods in protecting our hardware at scale. While we have blogged about how we address security threats from application to memory, the attacks on hardware, as well as firmware, have increased substantially. The data cataloged in the National Vulnerability Database (NVD) has shown the frequency of hardware and firmware-level vulnerabilities rising year after year.
Technologies like secure boot, common in desktops and laptops, have been ported over to the server industry as a method to combat firmware-level attacks and protect a device’s boot integrity. These technologies require that you create a trust ‘anchor’, an authoritative entity for which trust is assumed and not derived. A common trust anchor is the system Basic Input/Output System (BIOS) or the Unified Extensible Firmware Interface (UEFI) firmware.
While this ensures that the device boots only signed firmware and operating system bootloaders, does it protect the entire boot process? What protects the BIOS/UEFI firmware from attacks?
The Boot Process
Before we discuss how we secure our boot process, we will first Continue reading
How Fast Can We Detect a Network Failure?
In the introductory fast failover blog post I mentioned the challenge of fast link- and node failure detection, and how it makes little sense to waste your efforts on fast failover tricks if the routing protocol convergence time has the same order of magnitude as failure detection time.
Now let’s focus on realistic failure detection mechanisms and detection times. Imagine a system connecting a hardware switching platform (example: data center switch or a high-end router) with a software switching platform (midrange router):
How Fast Can We Detect a Network Failure?
In the introductory fast failover blog post I mentioned the challenge of fast link- and node failure detection, and how it makes little sense to waste your efforts on fast failover tricks if the routing protocol convergence time has the same order of magnitude as failure detection time.
Now let’s focus on realistic failure detection mechanisms and detection times. Imagine a system connecting a hardware switching platform (example: data center switch or a high-end router) with a software switching platform (midrange router):
Take Back Control of IT with Cloud-Native IGA
Identity governance and administration (IGA) is all about security automation, delivering the needed efficiency, speed, accuracy, and consistent output.The Many Facets Of Hybrid Supercomputing As Exascale Dawns
There may not be a lot of new systems on the November 2020 edition of the Top500 rankings of supercomputers, but there has been a bunch of upgrades and system tunings of machines that have been recently added, expanding their performance, as well as a handful of new machines that are interesting in their own right. …
The Many Facets Of Hybrid Supercomputing As Exascale Dawns was written by Timothy Prickett Morgan at The Next Platform.
Workers KV – free to try, with increased limits!


In May 2019, we launched Workers KV, letting developers store key-value data and make that data globally accessible from Workers running in Cloudflare’s over 200 data centers.
Today, we’re announcing a Free Tier for Workers KV that opens up global, low-latency data storage to every developer on the Workers platform. Additionally, to expand Workers KV’s use cases even further, we’re also raising the maximum value size from 10 MB to 25 MB. You can now write an application that serves larger static files directly or JSON blobs directly from KV.
Together with our announcement of the Durable Objects limited beta last month, the Workers platform continues to move toward providing storage solutions for applications that are globally deployed as easily as an application running in a single data center today.
What are the new free tier limits?
The free tier includes 100,000 read operations and 1,000 each of write, list and delete operations per day, resetting daily at UTC 00:00, with a maximum total storage size of 1 GB. Operations that exceed these limits will fail with an error.
Additional KV usage costs $0.50 per million read operations, $5.00 per million list, write and delete operations Continue reading
Tech Bytes: Protecting Remote Workers From VPN Risks With Zscaler (Sponsored)
Many companies use VPNs to protect their distributed workforce. But VPNs present their own security challenges, from compromised clients to insecure VPN servers. Sponsor Zscaler explains how its cloud-based security service can provide safe, high-performance remote access. Our guest is Lisa Lorenzin, Director, Transformation Strategy at Zscaler.Tech Bytes: Protecting Remote Workers From VPN Risks With Zscaler (Sponsored)
Many companies use VPNs to protect their distributed workforce. But VPNs present their own security challenges, from compromised clients to insecure VPN servers. Sponsor Zscaler explains how its cloud-based security service can provide safe, high-performance remote access. Our guest is Lisa Lorenzin, Director, Transformation Strategy at Zscaler.
The post Tech Bytes: Protecting Remote Workers From VPN Risks With Zscaler (Sponsored) appeared first on Packet Pushers.
Upcoming Webinar: Network Troubleshooting

I’m teaching a webinar on troubleshooting theory on the 20th; register here. From the course description:
This training focuses on the half-split system of troubleshooting, which is widely used in the electronic and civil engineering domains. The importance of tracing the path of the signal, using models to put the system in context, and the use of a simple troubleshooting “loop” to focus on asking how, what, and why are added to the half-split method to create a complete theory of troubleshooting. Other concepts covered in this course are the difference between permanent and temporary fixes and a review of measuring reliability. The final third of the course contains several practical examples of working through problems to help in applying the theory covered in the first two sections to the real world.