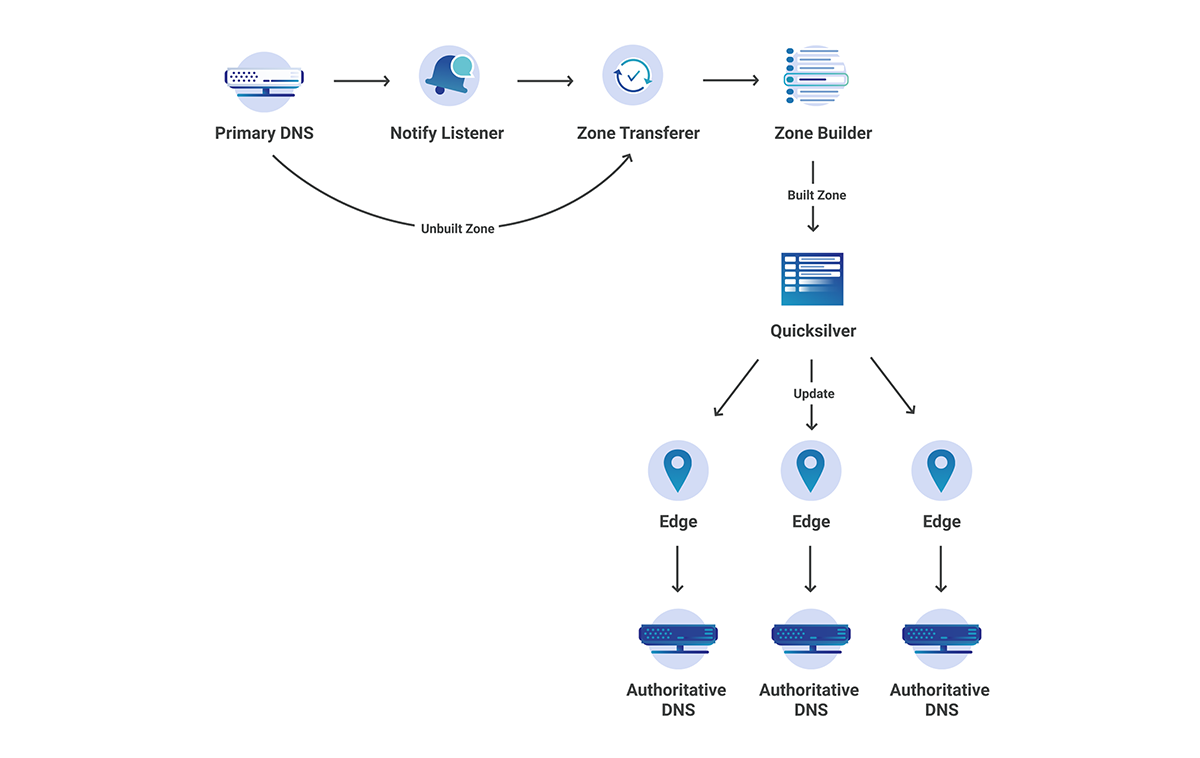
0
By Kevin Lees and Devyani Pisolkar, authors of the ‘Operationalizing VMware NSX’ guide
Virtualized networking and security may appear to be a standard feature of today’s modern data center, but it wasn’t so long ago — what, seven years? — that network virtualization was a new concept, largely introduced and propelled by VMware. How time flies. Today, across industries, network virtualization, in the form of VMware NSX, is the go-to choice for delivery of software-based network and security services. Nowadays we spend less time discussing the novelty of the architecture and more time talking about how to maximize the value of NSX by fully operationalizing the platform to make it a critical driver in your digital transformation.
VMware NSX is utterly unlike legacy networking
VMware NSX delivers networking and security services entirely in software. That enables organizations to move myriad operational tasks into the software layer, but to leverage it fully requires a top-to-bottom rethink of network operation itself. Under NSX, the old paradigm of the network as a hardware silo is gone; instead, the virtualized NSX network is an integral component in the software-defined data center.
Which brings us to the key point: in order to fully realize Continue reading