Dictionary: Human Permafrost

What is Human Permafrost in IT Infrastructure ?
The post Dictionary: Human Permafrost appeared first on EtherealMind.

What is Human Permafrost in IT Infrastructure ?
The post Dictionary: Human Permafrost appeared first on EtherealMind.
Here’s an interesting tidbit from “Last Week in AWS” blog:
From a philosophical point of view, AWS fundamentally considers an API to be a promise. Services that aren’t promoted anymore are still available […] Think about that for a second - a service launched 13 years ago is still actively supported to the point where you can use it today.
Compare that to Killed By Google graveyard, and you might understand why I’m a bit reluctant to cover GCP in my webinars.
Read more ...Challenges of real-world reinforcement learning, Dulac-Arnold et al., ICML’19
Last week we looked at some of the challenges inherent in automation and in building systems where humans and software agents collaborate. When we start talking about agents, policies, and modelling the environment, my thoughts naturally turn to reinforcement learning (RL). Today’s paper choice sets out some of the current (additional) challenges we face getting reinforcement learning to work well in many real-world systems.
We consider control systems grounded in the physical world, optimization of software systems, and systems that interact with users such as recommender systems and smart phones. … RL methods have been shown to be effective on a large set of simulated environments, but uptake in real-world problems has been much slower.
Why is this? The authors posit that there’s a meaningful gap between the tightly-controlled and amenable to simulation research settings where many RL systems do well, and the messy realities and constraints of real-world systems. For example, there may be no good simulator available, exploration may be curtailed by strong safety constraints, and feedback cycles for learning may be slow.
This lack of available simulators means learning must be done using Continue reading
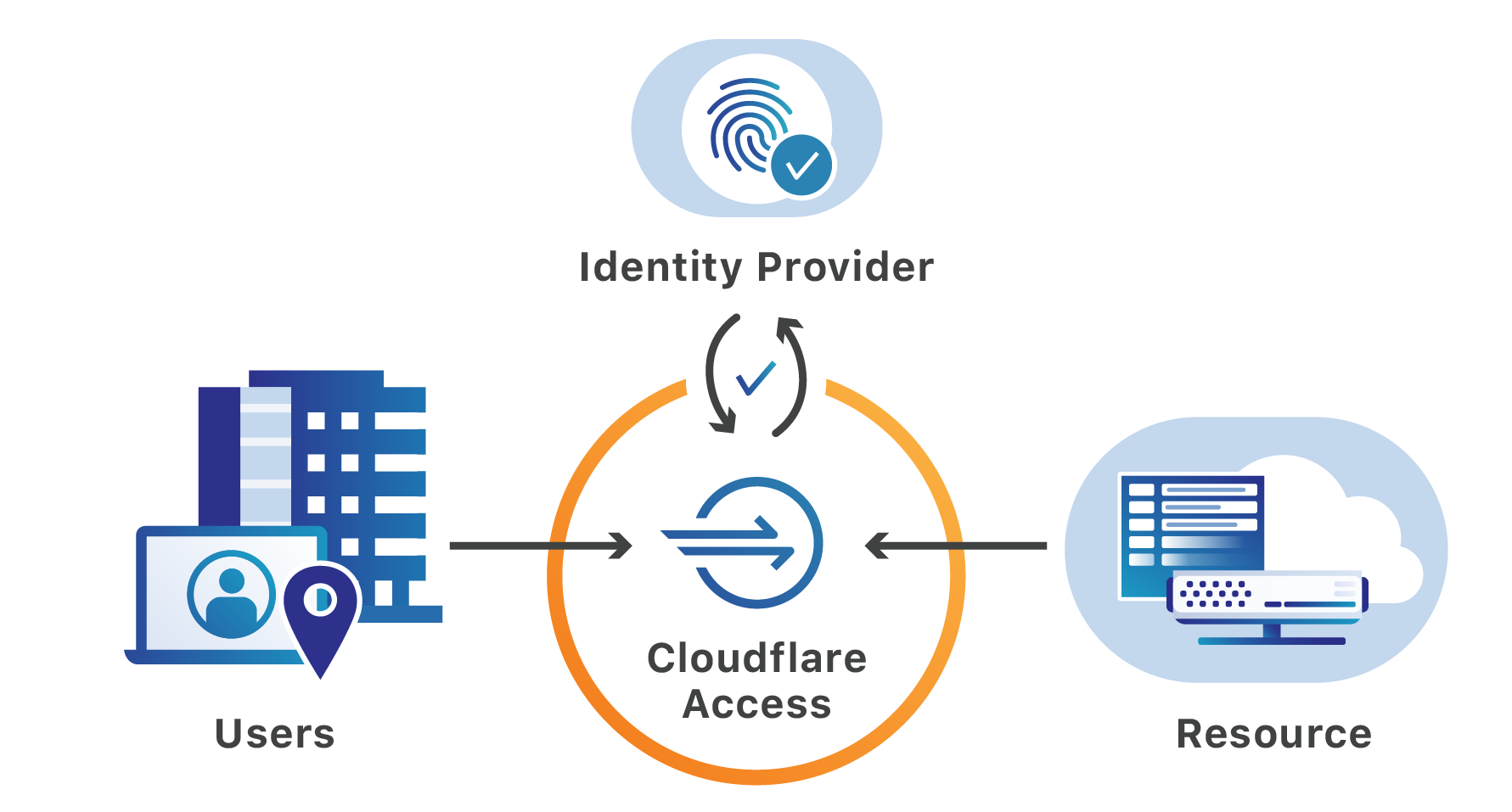
Yesterday, Citrix sent an updated notification to customers warning of a vulnerability in their Application Delivery Controller (ADC) product. If exploited, malicious attackers can bypass the login page of the administrator portal, without authentication, to perform arbitrary code execution.
No patch is available yet. Citrix expects to have a fix for certain versions on January 20 and others at the end of the month.
In the interim, Citrix has asked customers to attempt to mitigate the vulnerability. The recommended steps involve running a number of commands from an administrator command line interface.
The vulnerability relied on by attackers requires that they first be able to reach a login portal hosted by the ADC. Cloudflare can help teams secure that page and the resources protected by the ADC. Teams can place the login page, as well as the administration interface, behind Cloudflare Access’ identity proxy to prevent unauthenticated users from making requests to the portal.
Citrix ADC, also known as Citrix NetScaler, is an application delivery controller that provides Layer 3 through Layer 7 security for applications and APIs. Once deployed, administrators manage the installation of the ADC through a portal available at a dedicated URL on Continue reading
Stumbled upon a 35-year-old article describing the ironies of automation (HT: The Morning Paper). Here’s a teaser…
Unfortunately automatic control can ‘camouflage’ system failure by controlling against the variable changes, so that trends do not become apparent until they are beyond control.
In simpler words: when things fail, they fail really badly because the intermittent failures were kept hidden. Keep that in mind the next time someone tells you how wonderful software-defined AI-assisted networking is going to be.
Juniper routing instances are very useful when you need separate routing tables on the one device, for example to separate customers. Junos lets you configure SNMP polling of routing instances, so customers can poll “their” interfaces using 'instance_name'@'community'. All very useful. But it wasn’t obvious to me how to poll the default table via an interface in a routing instance. The trick is to just use @'community'. Here’s an example.
To demo this I have a simple network. I’m using a Virtual QFX plus Vagrant setup, based on the Vagrantfiles in this repo. I’m running one vqfx10k, connected to one server. The key here is that the server has two connections to the vqfx. One interface is in the default instance, one is in a “Customer” routing instance:
Here’s the routing-instance config:
1
2
3
4
5
6
7
8
vagrant@vqfx> show configuration routing-instances
Customer {
instance-type virtual-router;
interface xe-0/0/1.0;
}
{master:0}
vagrant@vqfx>
And here’s my SNMP configuration:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
vagrant@vqfx> show Continue reading
Juniper routing instances are very useful when you need separate routing tables on the one device, for example to separate customers. Junos lets you configure SNMP polling of routing instances, so customers can poll “their” interfaces using 'instance_name'@'community'. All very useful. But it wasn’t obvious to me how to poll the default table via an interface in a routing instance. The trick is to just use @'community'. Here’s an example.
To demo this I have a simple network. I’m using a Virtual QFX plus Vagrant setup, based on the Vagrantfiles in this repo. I’m running one vqfx10k, connected to one server. The key here is that the server has two connections to the vqfx. One interface is in the default instance, one is in a “Customer” routing instance:
Here’s the routing-instance config:
1
2
3
4
5
6
7
8
vagrant@vqfx> show configuration routing-instances
Customer {
instance-type virtual-router;
interface xe-0/0/1.0;
}
{master:0}
vagrant@vqfx>
And here’s my SNMP configuration:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
vagrant@vqfx> Continue reading
Found a nice article about Margaret Hamilton, the lady who coined the term "software engineering".
Engineering—back in 1969 as well as here in 2020—carries a whole set of associated values with it, and one of the most important is the necessity of proofing for disaster before human usage. You don’t “fail fast” when building a bridge: You ensure the bridge works first.
Now be a good "networking engineer" and go and stretch another VLAN around the globe... ;)
Things get a little wonky at exascale and hyperscale. Things that don’t matter quite as much at enterprise scale, such as the cost or the performance per watt or the performance per dollar per watt for a system or a cluster, end up dominating the buying decisions. …
The Supercomputing Efficiency Curve Bends In The Right Direction was written by Timothy Prickett Morgan at The Next Platform.
If one of your New Year's resolutions is to blog more, or start a blog, this episode is for you. We discuss the benefits of technical blogging including raising your profile, improving your own understanding, contributing to the community, and creating new opportunities in your professional life. Our guests are John Mark Troyer and Stephen Foskett.
The post Heavy Networking 497: Good Reasons To Start Your Tech Blog appeared first on Packet Pushers.
How do we work toward a more secure Internet?
In the Cyber Security discussions that take place in the various policy fora around the world, there is often little appreciation that the security of the Internet is a distributed responsibility, where many stakeholders take action.
By design, the Internet is a distributed system with no central core or point of control. Instead, Internet security is achieved by collaboration where multiple companies, organizations, governments, and individuals take action to improve the security and trustworthiness of the Internet – so that it is open, secure, and available to all.
Today we’ve published Major Initiatives in Cybersecurity: Public & Private Contributions Towards Increasing Internet Security to illustrate, via a handful of examples regarding Internet Infrastructure, there are a great number initiatives working, sometimes together and sometimes independently, in improving the Internet’s security. An approach we call collaborative security.
Major Initiatives in Cybersecurity describes Internet security as the part of cybersecurity that, broadly speaking, relates to the security of Internet infrastructure, the devices connected to it, and the technical building blocks from which applications and platforms are built.
We make no claim to completeness, but we do hope that the paper illustrates the complexity, breath, Continue reading
Wake up! It's HighScalability time:

Forrest Brazeal warns you not to spend your limited innovation credits building bespoke, complex systems that provide no direct value to your business, instead position yourself at the top of what heI calls the Wisdom/Cleverness Curve
Do you like this sort of Stuff? Your support on Patreon is appreciated more than you can know. I also wrote Explain the Cloud Like I'm 10 for everyone who needs to understand the cloud (which is everyone). On Amazon it has 84 mostly 5 star reviews (147 on Goodreads). Please recommend it. You'll be a real cloud hero.
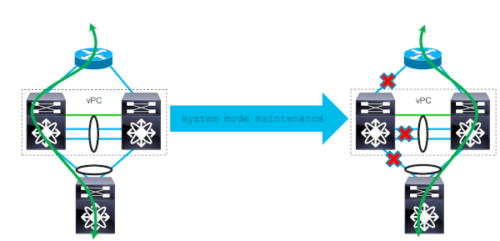
If you operate a data-center network with Cisco Nexus, you’ve probably already faced the problem of how to perform a maintenance on one of the two switches of a vPC pair, with minimum impact and risks for the production network. Cisco NX-OS contains a feature called “Graceful Insertion and Removal” or GIR to help you for that. Here is how it works. Scenario Let’s take the example below: (click on the image to see a larger version) We have two Nexus (in nx-os mode) in vPC. Doing layer-2 aggregation and …
The post Cisco NX-OS Graceful Insertion and Removal (GIR) appeared first on AboutNetworks.net.