Join Cloudflare & PicsArt at our meetup in Yerevan!

Cloudflare is partnering with PiscArt to create a meetup this month at PicsArt office in Yerevan. We would love to invite you to join us to learn about the newest in the Internet industry. You'll join Cloudflare's users, stakeholders from the tech community, and Engineers from both Cloudflare and PicsArt.
Tuesday, 4 June, 18:30-21:00
PicsArt office, Yerevan

Agenda:
- 18:30-19:00 Doors open, food and drinks
- 19:00 - 19:30 Areg Harutyunyan, Engineering Lead of Argo Tunnel at Cloudflare, "Cloudflare Overview / Cloudflare Security: How Argo Tunnel and Cloudflare Access enable effortless security for your team"
- 19:30-20:00 Gerasim Hovhannisyan, Director IT Infrastructure Operations at PicsArt, "Scaling to 10PB Content Delivery with Cloudflare's Global Network"
- 20:00-20:30 Olga Skobeleva, Solutions Engineer at Cloudflare, "Security: the Serverless Future"
- 20:30-21:00 Networking, food and drinks
View Event Details & Register Here »
We'll hope to meet you soon. Here are some photos from the meetup at PicsArt last year:




Create lab lessons for the NRE Labs Antidote network emulator
The Antidote network emulator, part of the Network Reliability Engineering project, offers a web interface that presents network emulation scenarios to users as documented lessons. Each lesson is presented in a window running Jupyter Notebooks and contains commands that the user can click on to run them on the virtual nodes in the network emulation scenario.

The NRE Labs developers intend for Antidote to be used as an educational tool. Its lesson-focused user interface supports students’ learning progress. This post is a tutorial showing how to create and test two simple, but different, Antidote lessons.
Lab documentation
At the time I wrote this post, the Antidote documentation does not provide enough practical information about how to create new Antidote labs. However, useful information is spread around in a few different locations, which I list below:
- Read the documentation about Lesson Endpoints
- The NRE Labs blog and videos on the NRE Labs Community Resources page provide some useful information about building labs for Antidote
- The Tips and FAQs Page that includes useful information about building lessons
- Read the post on the NRE Labs blog about how NRE Labs implements curriculum as code
- You can also reverse-engineer existing lab lessons
- Look Continue reading
Stopping SharePoint’s CVE-2019-0604
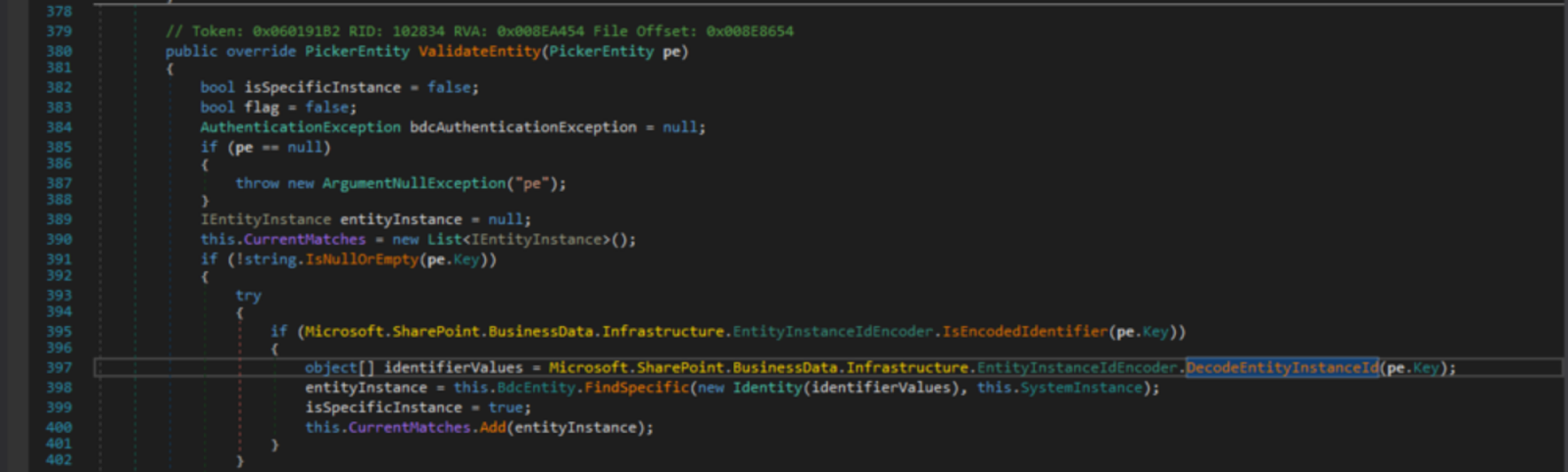
On Saturday, 11th May 2019, we got the news of a critical web vulnerability being actively exploited in the wild by advanced persistent threats (APTs), affecting Microsoft’s SharePoint server (versions 2010 through 2019).
This was CVE-2019-0604, a Remote Code Execution vulnerability in Microsoft SharePoint Servers which was not previously known to be exploitable via the web.
Several cyber security centres including the Canadian Centre for Cyber Security and Saudi Arabia’s National Center put out alerts for this threat, indicating it was being exploited to download and execute malicious code which would in turn take complete control of servers.
The affected software versions:
- Microsoft SharePoint Foundation 2010 Service Pack 2
- Microsoft SharePoint Foundation 2013 Service Pack 1
- Microsoft SharePoint Server 2010 Service Pack 2
- Microsoft SharePoint Server 2013 Service Pack 1
- Microsoft SharePoint Enterprise Server 2016
- Microsoft SharePoint Server 2019
Introduction
The vulnerability was initially given a critical CVSS v3 rating of 8.8 on the Zero Day Initiative advisory (however the advisory states authentication is required). This would imply only an insider threat, someone who has authorisation within SharePoint, such as an employee, on the local network could exploit the vulnerability.
We discovered that was not always Continue reading
Virtual Design Clinic 5 – Continues

Open, free and ready for you to join.
The post Virtual Design Clinic 5 – Continues appeared first on EtherealMind.
Wiwynn Launches Telco Edge Platform Based On OCP OpenEdge
 The server manufacturer also said it will contribute an open firmware development kit to the...
The server manufacturer also said it will contribute an open firmware development kit to the...
Who Wins and Loses if Sprint and T-Mobile Merge?
 If Sprint and T-Mobile gain approval from regulators to merge, it will impact infrastructure...
If Sprint and T-Mobile gain approval from regulators to merge, it will impact infrastructure...
Orange and Nokia Play 5G Doubles at French Open
 The French carrier has deployed two Nokia 5G base stations to support 8K broadcasts and a mixed...
The French carrier has deployed two Nokia 5G base stations to support 8K broadcasts and a mixed...
Orange Matter: Automating the Automators

I’ve been blogging for Solarwinds recently, posting on Orange Matter, with a cross-post to the Thwack Geek Speak forum. APIs are critical to operating infrastructure programmatically, but ultimately we need to add one or more layers of API-based middleware to make the solution usable and flexible.
This post appeared on Orange Matter as “Automating The Automators“, but I’m also linking to the version posted on Thwack, mainly because that format allows me to use more images and be slightly more irreverent; you don’t want to miss the great artwork on this one.
I’d love it if you were to take a moment to visit and read, and maybe even comment!
If you liked this post, please do click through to the source at Orange Matter: Automating the Automators and give me a share/like. Thank you!
MEF Inches One Step Closer Toward SD-WAN Standard
 The group released the draft of its SD-WAN service definition standard, with the official...
The group released the draft of its SD-WAN service definition standard, with the official...
Your Voice Matters: The World Can Learn from Canada’s Inclusive Solutions to Make Citizens Safer Online

Canada has shown great leadership in its innovative approach to secure our connected future by drawing on the diverse strengths, backgrounds, and perspectives our country has to offer.
While the wrap up of a collaborative effort to produce policy recommendations to keep us safe online is definitely worth celebrating, the real work for Canadians has just begun.
The Internet has profoundly changed the way we do things, expanding opportunity as it shrinks distances between people, cultures, and ideas. With connected devices hitting the shelves of major Canadian retailers like never before, the Internet of Things (IoT) is adding countless facets to a new era of human potential.
It has also brought new and complex challenges in areas such as privacy and security.
Many of us worry about our security when we log on. Despite recent calls by governments around the world to create regulation to keep citizens and information safe online, it is critical to consider that not one person or government can solve these issues alone.
If there’s anything the world of Internet governance has shown us, it’s that we get better answers to tough questions when a range of experts and interests can meaningfully take part in the Continue reading
Model Your Network as a Graph not a Set of Boxes
Last week I explained how you could take a typical first attempt at a network automation data model and reduce the amount of duplicate data… but the data model we used was still describing a set of seemingly disconnected boxes.
How about restructuring the whole thing and describing what networks really are - graphs made of nodes (network devices) and links?
The Week in Internet News: Broadband Goes to Space

The final countdown: After two delays, SpaceX has launched a rocket containing 60 satellites designed to deliver broadband to Earth-bound people, Marketwatch reports. SpaceX plans to eventually deploy up to 12,000 satellites in an effort to provide broadband service across the globe. SpaceX sees the satellite network as a way to fund future Mars missions.
Banning rural broadband: Moves by U.S. President Donald Trump’s administration to ban products from Chinese telecom hardware company Huawei may hurt rural broadband access, Phys.org says. Many small broadband and mobile providers serving rural areas use inexpensive telecom equipment from Huawei and other Chinese companies.
The (un)connected tractor: Meanwhile, the U.S. is far from the only country facing challenges with rural broadband. Farmers in Brazil often lack access, Reuters reports. Even as many pieces of new farm equipment require Internet access, less than 10 percent of Brazilian farms are connected, according to one estimate.
Dividing line: The Internet is dividing between a Chinese and a Western view of how it should operate, says ABC.net.au. And Chinese companies, aided by their government, are spreading their technologies and philosophies across the globe, the story suggests.
Expensive bugs: An 11-year-old laptop loaded with Continue reading
Pragmatic Debian packaging (2019)
Notice
This guide is an updated version of a previous edition. If you need to target distributions older than Debian Stretch and Ubuntu Bionic, please have a look at the older version instead.
While the creation of Debian packages is abundantly documented, most tutorials are targeted to packages implementing the Debian policy. Moreover, Debian packaging has a reputation of being unnecessarily difficult1 and many people prefer to use less constrained tools2 like fpm or CheckInstall.
However, building Debian packages with the official tools can become straightforward if you bend some rules:
-
No source package will be generated. Packages will be built directly from a checkout of a VCS repository.
-
Additional dependencies can be downloaded during build. Packaging individually each dependency is a painstaking work, notably when you have to deal with some fast-paced ecosystems like Java, Javascript and Go.
-
The produced packages may bundle dependencies. This is likely to raise some concerns about security and long-term maintenance, but this is a common trade-off in many ecosystems, notably Java, Javascript and Go.
The BGP Monitoring Protocol (BMP)
If you run connections to the ‘net at any scale, even if you are an “enterprise” (still a jinxed term, IMHO), you will quickly find it would be very useful to have a time series record of the changes in BGP at your edge. Even if you are an “enterprise,” knowing what changes have taken place in the routes your providers have advertised to you can make a big difference in tracking down an application performance issue, or knowing just when a particular service went off line. Getting this kind of information, however, can be difficult.
BGP is often overloaded for use in data center fabrics, as well (though I look forward to the day when the link state alternatives to this are available, so we can stop using BGP this way). Getting a time series view of BGP updates in a fabric is often crucial to understanding how the fabric converges, and how routing convergence events correlate to application issues.
One solution is to set up the BGP Monitoring Protocol (BMP—an abbreviation within an abbreviation, in the finest engineering tradition).
BMP is described in RFC7854 as a protocol intended to “provide a convenient interface for obtaining route views.” Continue reading