Configuring Voice VLANs
 |
| Fig 1.1- Sample Topology- Switch and IP Phone |
The Languages Which Almost Became CSS
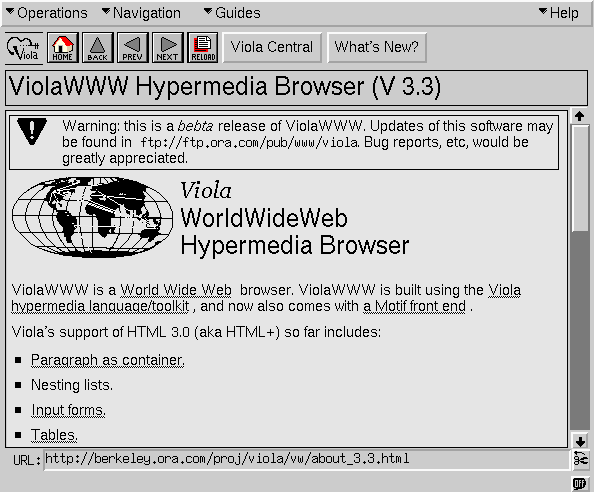
This was adapted from a post which originally appeared on the Eager blog. Eager has now become the new Cloudflare Apps.
In fact, it has been a constant source of delight for me over the past year to get to continually tell hordes (literally) of people who want to – strap yourselves in, here it comes – control what their documents look like in ways that would be trivial in TeX, Microsoft Word, and every other common text processing environment: “Sorry, you’re screwed.”
— Marc Andreessen
1994
When Tim Berners-Lee announced HTML in 1991 there was no method of styling pages. How a given HTML tag was rendered was determined by the browser, often with significant input from the user’s preferences. To Continue reading
Troubleshooting Cisco Network Elements with the USE Method
I want to draw some attention to a new document I've written titled “Troubleshooting Cisco Network Elements with the USE Method". In it, I explain how I've taken a model for troubleshooting a complex system-the USE Method, by Brendan Gregg-and applied it to Cisco network devices. By applying the USE Method, a network engineer can perform methodical troubleshooting of a network element in order to determine why the NE is not performing/acting/functioning as it should.Troubleshooting Cisco Network Elements with the USE Method
The USE Method is a model for troubleshooting a system that is in distress when you don't know exactly what the nature of the problem is. For example, if users within a specific part of your network are complaining of slowness, disconnects and poor application performance, you can probably isolate your troubleshooting to 2-3 switches or routers. However, since the problem description is so vague (we all love the “it's slow!EVPN-VXLAN lab – basic L2 switching
My EVPN-VXLAN lab topology:

There is IP Fabric in DC1 (2 vMX and 2 vQFX), and 2 vMX_v14 to emulate CE devices. Each CE device connected to EVPN via LACP LAG ae0 (EVPN Active-Active ethernet segment on service side). vMX_old-1 also has sigle-homed interface ge-0/0/4 (just to show you the difference).
Each CE device split into two logical systems for more convenient testing of routing functionality (global device context for Vlan100 and logical-system second for Vlan200). You could also use virtual-router routing instances for that, if you prefer this way. The rest of CE config is pretty self-explanatory:
ge-0/0/0 {
description vMX1;
gigether-options {
802.3ad ae0;
}
}
ge-0/0/1 {
description vMX2;
gigether-options {
802.3ad ae0;
}
}
ge-0/0/4 {
description vMX1_second;
flexible-vlan-tagging;
encapsulation flexible-ethernet-services;
mac 00:46:d3:04:fe:06;
}
ae0 {
description to_MC-LAG_vMX;
Continue reading
Worth Reading: LinkedIn passes an IPv6 milestone
The post Worth Reading: LinkedIn passes an IPv6 milestone appeared first on rule 11 reader.
Data Center Physical Realities in a Software-Defined World
A company's ability to leverage software depends on efficient infrastructure.
Cisco Completes $610M Viptela SD-WAN Deal
 SVP David Goeckeler will oversee the Viptela business.
SVP David Goeckeler will oversee the Viptela business.
Bitnami to Open Source its Mobile Kubernetes Dashboard
 Bitnami hopes to add more functionality and provide a unifying experience.
Bitnami hopes to add more functionality and provide a unifying experience.
Talari Adds WAN Opt and Bolsters SD-WAN Security
 Talari inherited its WAN optimization technology by acquiring an unknown vendor.
Talari inherited its WAN optimization technology by acquiring an unknown vendor.