Cloudflare Zaraz steps up: general availability and new pricing

This post is also available in Deutsch, Français.
Cloudflare Zaraz has transitioned out of beta and is now generally available to all customers. It is included under the free, paid, and enterprise plans of the Cloudflare Developer Platform. Visit our docs to learn more on our different plans.

Zaraz is part of the Cloudflare Developer Platform
Cloudflare Zaraz is a solution that developers and marketers use to load third-party tools like Google Analytics 4, Facebook CAPI, TikTok, and others. With Zaraz, Cloudflare customers can easily transition to server-side data collection with just a few clicks, without the need to set up and maintain their own cloud environment or make additional changes to their website for installation. Server-side data collection, as facilitated by Zaraz, simplifies analytics reporting from the server rather than loading numerous JavaScript files on the user's browser. It's a rapidly growing trend due to browser limitations on using third-party solutions and cookies. The result is significantly faster websites, plus enhanced security and privacy on the web.
We've had Zaraz in beta mode for a year and a half now. Throughout this time, we've dedicated our efforts to meeting as many customers as we could, gathering feedback, and Continue reading
Day Two Cloud 203: Becoming An SRE – It’s More Than Just Software Skills
If you want to be a Site Reliability Engineer (SRE) you need strong software skills. You also have to be versed in observability, incident response, capacity planning, change management, performance, even security. But wait, there's more! Our guest on today's Day Two Cloud argues you need strong communication skills, emotional intelligence, personal resilience, and the ability to work with a team. Our guest is Amin Astaneh.
The post Day Two Cloud 203: Becoming An SRE – It’s More Than Just Software Skills appeared first on Packet Pushers.
Day Two Cloud 203: Becoming An SRE – It’s More Than Just Software Skills
If you want to be a Site Reliability Engineer (SRE) you need strong software skills. You also have to be versed in observability, incident response, capacity planning, change management, performance, even security. But wait, there's more! Our guest on today's Day Two Cloud argues you need strong communication skills, emotional intelligence, personal resilience, and the ability to work with a team. Our guest is Amin Astaneh.Is Neutral Host the Killer App for Private Wireless?
A more modern approach to lowering the cost and complexity of extending cellular signals indoors is driving a new generation of private cellular wireless within the enterprise.The Arrival of Open AI Networking
Recently I attended the 50th golden anniversary of Ethernet at the Computer History Museum. It was a reminder of how familiar and widely deployed Ethernet is and how it has evolved by orders of magnitude. Since the 1970s, it has progressed from a shared collision network at 2.95 megabits in the file/print/share era to the promise of Terabit Ethernet switching in the AI/ML era. Legacy Ethernot* alternatives such as Token Ring, FDDI, and ATM generally get subsumed by Ethernet. I believe history is going to repeat itself for AI networks.
AWS Advanced Networking Speciality 1.3:Considerations for encryption and authentication with load balancers (for example, TLStermination, TLS passthrough)
< MEDIUM :https://towardsaws.com/aws-advanced-networking-speciality-1-3-considerations-402e0d057dfb >
List of blogs on AWS Advanced Networking Speciality Exam — https://medium.com/@raaki-88/list/aws-advanced-network-speciality-24009c3d8474
Data Protection in ELB
AWS Shared-Responsibility Model defines how data protection applies in ELBs. It boils down to AWS protecting global infrastructure while the service consumer is more responsible for preserving the content and control over the hosted content.
Few important suggestions for accessing/Securing
- MFA for accounts
- TLS 1.2 or TLS 1.3 for AWS resource communication
- Logging with AWS CloudTrail
- Amazon Macie — Discovering and securing sensitive data in S3
- FIP140–2 — Fips Endpoint
Encryption
Encryption at rest: Server-side encryption for S3 (SSE-S3) is used for ELB access logs. ELB automatically encrypts each log file before storing it in the S3 bucket and decrypts the access log files when you access them. Each log file is encrypted with a unique key, which is encrypted with a master key that is regularly rotated.
Encryption in Transit:
HTTPS/TLS traffic can be terminated at the ELB. ELB can encrypt and decrypt the traffic instead of additional EC2 instances or current EC2 backend instances doing this TLS termination. Using ACM (AWS Certificate Continue reading
AWS Advanced Networking Speciality 1.3: AWS Load Balancer Controller for Kubernetes clusters
List of blogs on AWS Advanced Networking Speciality Exam — https://medium.com/@raaki-88/list/aws-advanced-network-speciality-24009c3d8474
Before understanding LoadBalancer Service, it’s worth understanding a few things about NodePort service.
NodePort Service :
NodePort service opens a port on each node. External agents can connect directly to the node on the NodePort. If not mentioned, a randomly chosen service is picked up for NodePort. LoadBalancing here is managed by front-end service, which listens to a port and load balances across the Pods, which responds to service requests.
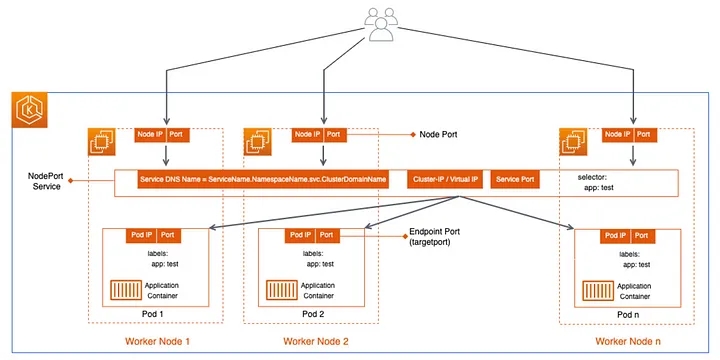
LoadBalancer Service:

Like NodePort Service, the LoadBalancer service extends the functionality by adding a load balancer in front of all the nodes. Kubernetes requests ELB and registers all the nodes. It’s worth noting that Load Balancer will not detect where the pods are running. Worker nodes are added as backend instances in the load balancer. The classic-load balancer is the default LB the service chooses and can be changed to NLB(Network Load Balancer). CLB routes the requests to Front-end, then to internal service ports Continue reading
The Packet Pushers Welcome CEO Jennifer Tribe
We’re excited to announce Jennifer Tribe has joined Packet Pushers Interactive as our first-ever CEO! Jennifer’s mission is to help grow the Packet Pushers podcast network, increase our visibility and reach in the tech community, and bring in new listeners and clients. Jennifer’s skill set and experience are ideal for this position. She’s been a […]
The post The Packet Pushers Welcome CEO Jennifer Tribe appeared first on Packet Pushers.
Implementing workload-centric Web Application Firewall (WAF) using Calico
Microservices security is a growing concern for businesses in the face of increasing cyber threats. With application layer attacks being a leading cause of breaches, it’s more important than ever to safeguard the HTTP-based communication between microservices within a Kubernetes cluster. Traditional web application firewalls (WAFs) are not designed to address this specific challenge, but Calico WAF offers a unique solution.
What is a workload-centric WAF?
Calico WAF, a workload-centric web application firewall, brings a fresh, cloud-native approach to securing microservices communication. Unlike traditional WAFs deployed at the edge of a Kubernetes cluster, Calico WAF focuses on protecting the intra-cluster traffic and applies zero-trust rules specifically designed for microservices within your cluster.
This innovative solution defends against common HTTP-layer attacks, such as server-side request forgery (SSRF), improper HTTP header type, occurring within the cluster. It seamlessly integrates with Calico Cloud network policies, enabling the enforcement of security controls at the host level for selected pods.
Calico WAF ensures the secure communication between microservices within your Kubernetes cluster, reducing the risk of vulnerabilities and threats. By adopting Calico WAF, businesses can confidently fortify the HTTP-based communication channels within their microservices architecture. This comprehensive approach enhances the overall security posture of Continue reading
Full Stack Journey 080: Career Transitions Via Cloud, Infrastructure, And Content Creation With Rishab Kumar
Today's Full Stack Journey talks with Rishab Kumar, developer advocate at Twilio. He and Scott Lowe discuss three key things Rishab learned in public cloud, Infrastructure as Code, and creating content that helped his career transitions.
The post Full Stack Journey 080: Career Transitions Via Cloud, Infrastructure, And Content Creation With Rishab Kumar appeared first on Packet Pushers.
Full Stack Journey 080: Career Transitions Via Cloud, Infrastructure, And Content Creation With Rishab Kumar
Today's Full Stack Journey talks with Rishab Kumar, developer advocate at Twilio. He and Scott Lowe discuss three key things Rishab learned in public cloud, Infrastructure as Code, and creating content that helped his career transitions.The Era of Multi-Cloud is Here: Here’s How to Get the Most Out of It
Enterprises need to optimize their multi-cloud investments to enjoy the benefits of things like lower cost and better performance.DDoS threat report for 2023 Q2


Welcome to the second DDoS threat report of 2023. DDoS attacks, or distributed denial-of-service attacks, are a type of cyber attack that aims to disrupt websites (and other types of Internet properties) to make them unavailable for legitimate users by overwhelming them with more traffic than they can handle — similar to a driver stuck in a traffic jam on the way to the grocery store.
We see a lot of DDoS attacks of all types and sizes and our network is one of the largest in the world spanning more than 300 cities in over 100 countries. Through this network we serve over 63 million HTTP requests per second at peak and over 2 billion DNS queries every day. This colossal amount of data gives us a unique vantage point to provide the community access to insightful DDoS trends.
For our regular readers, you might notice a change in the layout of this report. We used to follow a set pattern to share our insights and trends about DDoS attacks. But with the landscape of DDoS threats changing as DDoS attacks have become more powerful and sophisticated, we felt it's time for a change in how we present Continue reading
Informe sobre las amenazas DDoS en el 2º trimestre de 2023


Te damos la bienvenida al segundo informe sobre amenazas DDoS de 2023. Los ataques DDoS, o ataques de denegación de servicio distribuido, son un tipo de ciberataque cuyo objetivo es sobrecargar de tráfico sitios web (y otros tipos de propiedades de Internet) para interrumpir el funcionamiento normal y que los usuarios legítimos no puedan acceder a ellos, lo mismo que cuando un conductor está atrapado en un atasco de camino al supermercado.
Observamos muchos ataques DDoS de diferentes tipos y tamaños, y nuestra red es una de las mayores del mundo, ya que abarca más de 300 ciudades en más de 100 países. A través de esta red atendemos más de 63 millones de solicitudes HTTP por segundo durante picos de tráfico y más de 2 billones de consultas de DNS cada día. Esta ingente cantidad de datos nos ofrece una perspectiva privilegiada para dar a conocer a la comunidad tendencias reveladoras sobre los ataques DDoS.
Nuestros lectores habituales quizá noten un cambio en el diseño de este informe. Solíamos seguir un patrón fijo para compartir nuestras percepciones y tendencias sobre los ataques DDoS. Sin embargo, creemos que ha llegado el momento de cambiar la forma de presentar nuestras Continue reading
HS052 Professional Liability and Qualified Design
As technology becomes more critical and vital to companies business leaders are beginning to question the reliability and liability. Insurers now require audits and demand complienace with set practices before issuing a policy. Corporate boards are realising that so-called tech professionals have zero training or professional requirement, consultants have even less and the analysts are […]
The post HS052 Professional Liability and Qualified Design appeared first on Packet Pushers.


