Configuring OSPF between Logical and Edge routers on VMware NSX
On previous posts the following topology has been deployed: The next step is adding an Edge router which can manage external traffic. On a next post the Edge router will be bridged to a physical network. The expected topology will be the following: Open the Web Client and go to “Networking & Security ->Logical Switches” […]Should I Go For CCDE or VCIX-NV?
I got a lengthy email from one of my readers a while ago, essentially asking a simple question: assuming I want to go return to my studies and move further than CCIE I currently hold, should I go for CCDE or the new VMware’s VCIX-NV?
Well, it’s almost like “do you believe in scale-up or scale-out?” ;) Both approaches have their merits.
Read more ...VMware NSX Loves Hardware
One of the core value propositions of VMware NSX is ability to take advantage of any underlying hardware infrastructure and deliver a fully decoupled virtualized network in software. VMware NSX loves a  good hardware fabric,.
good hardware fabric,.
But that’s not the only hardware VMware NSX loves.
The votes have been cast and counted, and we are pleased to announce that VMware NSX was selected as the winner in the “Best Software Defined Infrastructure” category in the 2015 Modern Infrastructure Impact Awards. The awards were judged by the Modern Infrastructure e-zine editorial staff, in conjunction with users, readers, and industry experts.
The Modern Infrastructure Impact Awards recognize the top products, technologies and services in the essential areas of technology that Modern Infrastructure covers. The award-winning tools are those helping to run enterprise businesses with efficiency and insight — whether they’re used inside the data center or out.
VMware NSX delivers secure network services to applications running in the data center, resulting in instant and programmatic provisioning, fast and highly available infrastructure, and increased security and micro segmentation capabilities.
Read about the award here and to learn more about the business value of VMware NSX visit vmware.com/products/nsx.
Roger
SDN and Gartner’s Hype Cycle
Many years ago Gartner introduced their technology Hype Cycle, which maps visibility against maturity for new technology. The Hype Cycle in essence states that many new technologies get a large amount of visibility early in their maturity cycle. The visibility and enthusiasm drops significantly when reality sets in: technologies early in their maturity cycle will have low adoption rates. The vast majority of customers of technology are conservative in their choices, especially if this new technology is not (yet) fundamental to this customer’s business.
I call it common sense reality, Garter calls it the Trough of Disillusionment, fine. It is that realization that the technology may have lots of promises, but isn’t ready to be consumed.
That is where the real work starts, maturing the technology, driving solutions and use cases, creating the economic viability of the technology and tons of other stuff that needs to be done to get a customer base to actually buy into this technology. Not with words and attention, but with the only thing that matters ultimately, money. Gartner calls delivering these absolutely necessary components the Slope of Enlightenment.
Not every technology follows this cycle, not every technology survives the downward turn after the inflated Continue reading
Distributed routing on VMware NSX
On the previous post a NSX environment has been configured with three isolated logical switches. In this post a distributed router will be added to route packets between logical switches inside tenant 1. Open the Web client and go to “Networking & Security -> NES Edges” and add a new logical (distributed) router: Configure username, […]Scaling Overlay Virtual Networks: The Problem
Every major hypervisor and networking vendor has an overlay virtual networking solution. Obviously they’re not identical, and some of them work better than others in large-scale environments – an interesting challenge we tried to address in the Scaling Overlay Virtual Networks webinar. As always, we started by identifying the potential problems.
CCDE Study Guide – CCDE Preparation Resources for written exam
I am glad to announce that we prepared a streamlined CCDE written exam preparation resources. Today it has been placed on Cisco’s official learning site, Cisco Learning network.
The post CCDE Study Guide – CCDE Preparation Resources for written exam appeared first on Network Design and Architecture.
Routers vs Switches, When to position which?
Everyone knows the difference between a router and switch right? Good.. (for those that need a good refresher) this post is not going is not going to dive into that topic. What I want to talk about is Router vs Switching from a positioning standpoint. One question I often get asked working with customers is: “Can I […]
Author information
The post Routers vs Switches, When to position which? appeared first on Packet Pushers Podcast and was written by Derek Pocoroba.
The SDN Ecosystem
As I mentioned last week, I am kicking off a three part series on Software Defined Networking (SDN)…. I will post them over the nextOVN, Bringing Native Virtual Networking to OVS
By Justin Pettit, Ben Pfaff, Chris Wright, and Madhu Venugopal
Today we are excited to announce Open Virtual Network (OVN), a new project that brings virtual networking to the OVS user community. OVN complements the existing capabilities of OVS to add native support for virtual network abstractions, such as virtual L2 and L3 overlays and security groups. Just like OVS, our design goal is to have a production quality implementation that can operate at significant scale.
Why are we doing this? The primary goal in developing Open vSwitch has always been to provide a production-ready low-level networking component for hypervisors that could support a diverse range of network environments. As one example of the success of this approach, Open vSwitch is the most popular choice of virtual switch in OpenStack deployments. To make OVS more effective in these environments, we believe the logical next step is to augment the low-level switching capabilities with a lightweight control plane that provides native support for common virtual networking abstractions.
To achieve these goals, OVN’s design is narrowly focused on providing L2/L3 virtual networking. This distinguishes OVN from general-purpose SDN controllers or platforms.
OVN is a new project from the Open vSwitch team to Continue reading
AT&T Personifies Slow Crawl to SDN Ubiquity
AT&T Personifies Slow Crawl to SDN Ubiquity
by Brian Boyko, Contributor - January 13, 2015
The Wall Street Journal reported in a “CIO Journal” blog post that AT&T intends to virtualize 75% of its network by 2020, with “very specific operational planning,” according to SEVP of Technology and Operations, John Donovan.
Why would AT&T push off SDN so far into the distant future? Then again, 2020 is only five years away. Five years is a relative timeframe in IT, and I think the length of AT&T’s transition not only underscores the size and scope of AT&T’s networks but also the caution to which they’re giving the task. This is understandable considering the complexity of managing SDN.
Donovan says the motivation for AT&T is to reduce capital expenditures while increasing capacity in the network. In our recent survey of service providers, more than 40% said reducing costs is their number one driver for deploying SDN, compared to only 17% in 2013. The biggest drivers cited however – which corroborates AT&T’s desire to increase capacity – are improved agility and supporting new services such as cloud, big data applications, and mobility.
According to the article, it Continue reading
Rules Shouldn’t Have Exceptions

On my way to Virtualization Field Day 4, I ran into a bit of a snafu at the airport that made me think about policy and application. When I put my carry-on luggage through the X-ray, the officer took it to the back and gave it a thorough screening. During that process, I was informed that my double-edged safety razor would not be able to make the trip (or the blade at least). I was vexed, as this razor had flown with me for at least a whole year with nary a peep from security. When I related as much to the officer, the response was “I’m sorry no one caught it before.”
Everyone Is The Same, Except For Me
This incident made me start thinking about polices in networking and security and how often they are arbitrarily enforced. We see it every day. The IT staff comes up with a new plan to reduce mailbox sizes or reduce congestion by enforcing quality of service (QoS). Everyone is all for the plan during the discussion stages. When the time comes to implement the idea, the exceptions start happening. Upper management won’t have mailbox limitations. The accounting department is Continue reading
Internet for the Next 3 Billion

Last month, I traveled to Doha, Qatar to participate in the ITU’s Telecom World conference. While there I got to understand how a satellite provider brings Internet access to South Sudan using medium-earth orbit satellites and, amazingly, achieves terrestrial latencies to a region where reliable terrestrial connections simply don’t exist! The mission of this company is to help close the digital divide by extending Internet access to the estimated three billion people on the planet who are currently not served. Our measurements show the that performance improvement over traditional satellite can be dramatic.
ITU Telecom World
First, let me say a few words about the conference itself and then I’ll review this intriguing new satellite service. In Doha, I was on a panel entitled Affordable International Backhaul and chaired by Abu Saaed Kahn of LIRNEAsia, a telecommunications policy institute primarily focused on the Asia-Pacific region.

Load Balancing Elephant Storage Flows
Olivier Hault sent me an interesting challenge:
I cannot find any simple network-layer solution that would allow me to use total available bandwidth between a Hypervisor with multiple uplinks and a Network Attached Storage (NAS) box.
TL&DR summary: you cannot find it because there’s none.
Read more ...Announcing: Pieces of Human Infrastructure Magazine
TL-DR: This week I'm started a magazine style newsletter called "Pieces of Human Infrastructure". You can sign up at http://etherealmind.com/pieces-human-infrastructure-newsletter/
The post Announcing: Pieces of Human Infrastructure Magazine appeared first on EtherealMind.
Zero Touch Provisioning in a Bare Metal World
Who doesn’t like automation? If you’re speaking to somebody in IT, then the short answer is “nobody”.
While the term Zero Touch Provisioning (ZTP) might be increasingly more common to networking, the concept of automation has existed for years in IT. At its core, ZTP is an automation solution that’s designed to reduce errors and save time when an IT administrator needs to bring new infrastructure online.
This is particularly useful for data center servers, where scale and configuration similarities across systems make automation a necessity. In the server world, the Linux-based operating system has revolutionized on boarding and provisioning. Rather than using command-line interfaces (CLI) to configure these systems one at a time, administrators can use automation tools to roll out the operating system software, patches, and packages on new servers with a single command, or the click of a mouse.
Advanced scripting capabilities also allow administrators to tailor the boot configuration of these systems with profiles for specific applications. So for example, if you need ten servers for a new Hadoop cluster, you can load this with one profile, but if you need six new servers for a new web application, you can Continue reading
phpipam MySQL database optimizations
Having large amount of subnets (and other tables) on unoptimised MySQL database server can significantly increase page loads. To see which parameters need to be change I usually use mysqltuner perl script, which connects to database, analyses data and proposes which parameters need to be changed that are not optimally set based on current load.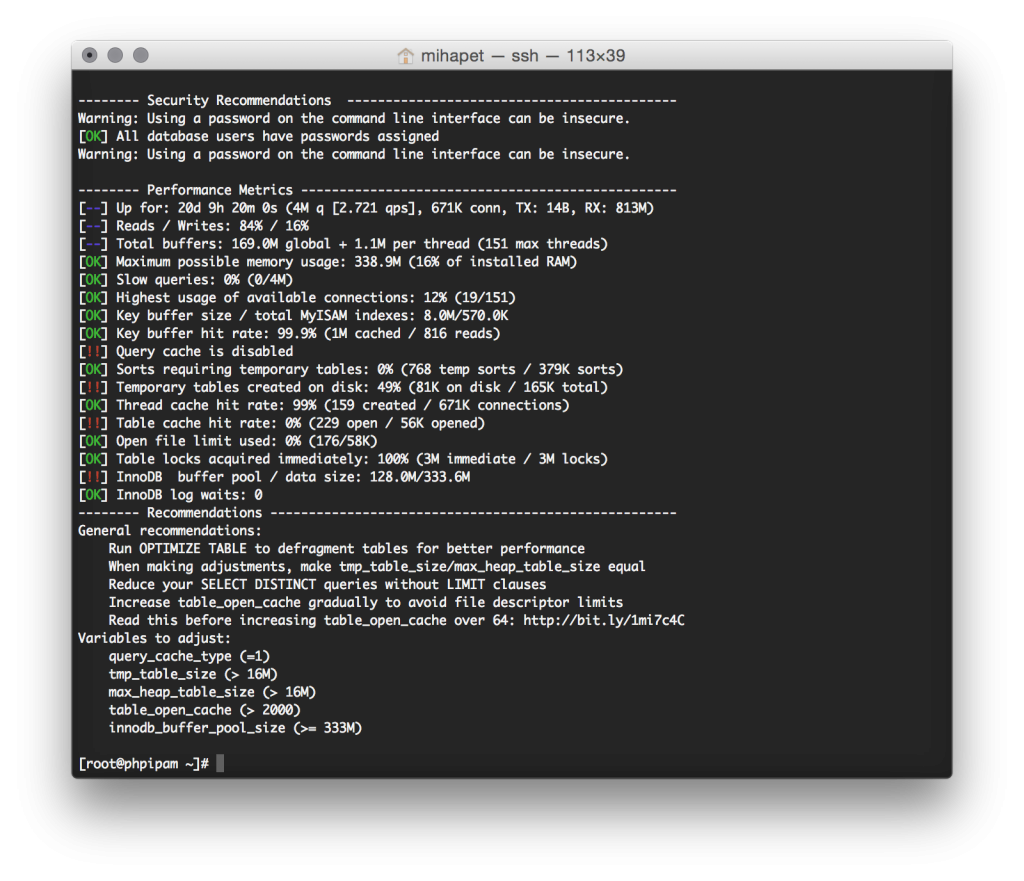
Installation is simple:
1.) Fetch mysqltuner on FreeBSD:
cd ~ fetch http://mysqltuner.pl
or wget on linux:
wget http://mysqltuner.com
2.) Make it executable:
chmod +x mysqltuner.pl
3.) And run it to analyse database, you have to provide administrative credentials.
./mysqltuner.pl
Any other similar scripts out there you would recommend?
brm
