Introduction to Cloud Development Kit for Terraform
Cloud Development Kit for Terrafrom or CDKTF as it is commonly referred to is a tool kit that allows you to leverage the advantages of Terrafrom from within a high-level programming language such as TypeScript, Python, Java, C#, or Go. CDKTF automatically extracts the schema from Terraform providers and modules to generate the necessary classes for your application. We can use CDKTF with every provider that is avaiable on the Terrafrom registry.
In this post, we will look at an example of using CDKTF with Python to provision resources on a Palo Alto Networks Panorama. I chose a Palo Alto Networks Panorama as the target here because I am from a network engineering background.
Installation
Hashicorp have well documented steps on how you can install CDKTF and can be found here.
Getting Started
Initialise a new Project
Once we have successfully installed CDKTF and verified our installation, we begin by initialising a cdktf project with an appropriate template. Here, we are using Python as our template.
cdktf init --template=python --local --project-name cdktf-post --project-description A-simple-projectInitialise a new CDKTF project
Once the initialiation has been completed, you will notice that several new files and folders are created. The main.py file Continue reading
netlab VXLAN Router-on-a-Stick Example
In October 2022 I described how you could build a VLAN router-on-a-stick topology with netlab. With the new features added in netlab release 1.41 we can do the same for VXLAN-enabled VLANs – we’ll build a lab where a router-on-a-stick will do VXLAN-to-VXLAN routing.
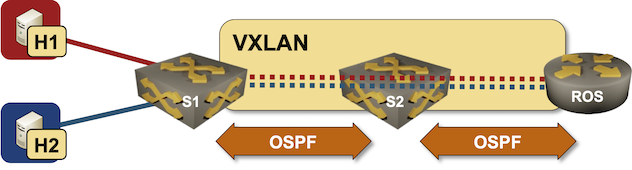
Lab topology
netlab VXLAN Router-on-a-Stick Example
In October 2022 I described how you could build a VLAN router-on-a-stick topology with netlab. With the new features added in netlab release 1.41 we can do the same for VXLAN-enabled VLANs – we’ll build a lab where a router-on-a-stick will do VXLAN-to-VXLAN routing.

Lab topology
Worth Reading: History of Fiber Optics Cables
Geoff Huston published a fantastic history of fiber optics cables, from the first (copper) transatlantic cable to 2.2Tbps coherent optics. Have fun!
Worth Reading: History of Fiber Optics Cables
Geoff Huston published a fantastic history of fiber optics cables, from the first (copper) transatlantic cable to 2.2Tbps coherent optics. Have fun!
The Fibre Optic Path
The story of the evolution of fibre optic cable is a fascinating one, with a rich scientific history, including more than a few Nobel prizes.Weekend Reads 111122
https://www.darkreading.com/risk/build-security-around-users-a-human-first-approach-to-cyber-resilience
User-first security must begin with an understanding of how people use computing technology. We have to ask: What is it that makes users vulnerable to hacking via email, messaging, social media, browsing, file sharing?
Responding to a recent surge in AI-generated bot accounts, LinkedIn is rolling out new features that it hopes will help users make Continue reading
Fast zero copy static web server with KTLS
I’m writing a webserver optimized for serving a static site with as high performance as possible. Counting every syscall, and every copy between userspace and kernel space.
It’s called “tarweb”, because it serves a website entirely from a tar file.
I’m optimizing for latency of requests, throughput of the server, and scalability over number of active connections.
I won’t go so far as to implement a user space network driver to bypass the kernel, because I want to be able to just run it in normal setups, even as non-root.
I’m not even close to done, and the code is a mess, but here are some thoughts for now.
First optimize syscall count
Every syscall costs performance, so we want to minimize those.
The minimum set of syscalls for a webserver handling a request is:
accept()to acquire the new connection.epoll_ctl()to add the fd.epoll_wait()&read()or similar. (ideally getting the whole request in oneread()call)epoll_wait()&write()or similar. (again ideally in one call)close()the connection.
There’s not much to do about accept() and read(), as far as I can
see. You need to accept the connection, and you need to Continue reading
2022 US midterm elections attack analysis


Through Cloudflare’s Impact programs, we provide cyber security products to help protect access to authoritative voting information and the security of sensitive voter data. Two core programs in this space are the Athenian Project, dedicated to protecting state and local governments that run elections, and Cloudflare for Campaigns, a project with a suite of Cloudflare products to secure political campaigns’ and state parties’ websites and internal teams.
However, the weeks ahead of the elections, and Election Day itself, were not entirely devoid of attacks. Using data from Cloudflare Radar, which showcases global Internet traffic, attack, and technology trends and insights, we can explore traffic patterns, attack types, and top attack sources associated with both Athenian Project and Cloudflare for Campaigns participants.
For both programs, overall traffic volume unsurprisingly ramped up as Election Day approached. SQL Injection (SQLi) and HTTP Anomaly attacks were the two largest categories of attacks mitigated by Cloudflare’s Web Application Firewall (WAF), and the United States was the largest source of observed attacks — see more on this last point below.
Below, we explore the trends seen across both customer sets from October 1, 2022, through Election Day on November 8.
Athenian Project
Throughout Continue reading
Heavy Networking 655: On-Prem VPC Networking With Netris (Sponsored)
Heavy Networking welcomes sponsor Netris to the show with a special episode for you network nerds who are really getting into automation, infrastructure as code, pipelines, and so on. Netris is all about bringing that public cloud VPC experience to the network you’ve already got. Imagine being able to consume your existing network with APIs and being able to stand up VLANs, VXLANs, elastic load balancers, firewalls, Internet gateways, and more the same way you do in the cloud, but on premises.
The post Heavy Networking 655: On-Prem VPC Networking With Netris (Sponsored) appeared first on Packet Pushers.
Heavy Networking 655: On-Prem VPC Networking With Netris (Sponsored)
Heavy Networking welcomes sponsor Netris to the show with a special episode for you network nerds who are really getting into automation, infrastructure as code, pipelines, and so on. Netris is all about bringing that public cloud VPC experience to the network you’ve already got. Imagine being able to consume your existing network with APIs and being able to stand up VLANs, VXLANs, elastic load balancers, firewalls, Internet gateways, and more the same way you do in the cloud, but on premises.Video: Routing Protocols Overview
After discussing network addressing and switching, routing, and bridging in the How Networks Really Work webinar, it was high time for a deep dive into routing protocols, starting (as always) with an overview.
Video: Routing Protocols Overview
After discussing network addressing and switching, routing, and bridging in the How Networks Really Work webinar, it was high time for a deep dive into routing protocols, starting (as always) with an overview.
Network Automation with CUE – Augmenting Ansible workflows
Hardly any conversation about network automation that happens these days can avoid the topic of automation frameworks. Amongst the few that are still actively developed, Ansible is by far the most popular choice. Ansible ecosystem has been growing rapidly over the last few years, with modules being contributed by both internal (Redhat) and external (community) developers. Having the backing of one of the largest open-source first companies has allowed Ansible to spread into all areas of infrastructure – from server automation to cloud provisioning. By following the principle of eating your own dog food, Redhat used Ansible in a lot of its own open-source projects, which made it even more popular in the masses. Another important factor in Ansible’s success is the ease of understanding. When it comes to network automation, Ansible’s stateless and agentless architecture very closely follows a standard network operation experience – SSH in, enter commands line-by-line, catch any errors, save and disconnect. But like many complex software projects, Ansible is not without its own challenges, and in this post, I’ll take a look at what they are and how CUE can help overcome them.
Ansible Automation Workflow
Let’s start with an overview of the intermediate Ansible Continue reading
Kubernetes Unpacked 013: Azure Kubernetes Service (AKS) In Production
In this episode, Michael Levan catches up Richard Hooper, Microsoft Azure MVP and Azure Architect, to chat about Azure Kubernetes Service (AKS) in production. Richard spends the majority of his time working with organizations that are either using AKS, or are migrating to AKS, so he has a ton of experience in how to actually use AKS in the real-world.
The post Kubernetes Unpacked 013: Azure Kubernetes Service (AKS) In Production appeared first on Packet Pushers.