Network Break 404: Episode Not Found
This week the Network Break covers new SASE capabilities from Fortinet, new 800G hardware from Cisco that uses its homegrown ASIC, and an app from RSA for smart phones that can disable authentication if the app detects malicious behavior. Plus we cover new initiatives from the Open Compute Project, disaggregated Wi-Fi, and more tech news.On the ‘net: Privacy and Networking
The final three posts in my series on privacy for infrastructure engineers is up over at Packet Pushers. While privacy might not seem like a big deal to infrastructure folks, it really is an issue we should all be considering and addressing—if for no other reason than privacy and security are closely related topics. The primary “thing” you’re trying to secure when you think about networking is data—or rather, various forms of privacy.
Tech Bytes: Using Opengear Every Day–For Disruptions And More (Sponsored)
Today on the Tech Bytes podcast we talk about how to use out-of-band management for daily networking tasks, not just when there’s a problem or crisis. Our sponsor is Opengear and we’re joined by Ramtin Rampour, Solutions Architect, to talk about use cases including zero touch provisioning, configuration, and more.
The post Tech Bytes: Using Opengear Every Day–For Disruptions And More (Sponsored) appeared first on Packet Pushers.
Tech Bytes: Using Opengear Every Day–For Disruptions And More (Sponsored)
Today on the Tech Bytes podcast we talk about how to use out-of-band management for daily networking tasks, not just when there’s a problem or crisis. Our sponsor is Opengear and we’re joined by Ramtin Rampour, Solutions Architect, to talk about use cases including zero touch provisioning, configuration, and more.Deploy Ceph on K8s Worker Nodes Using ROOK
please visit following Git wiki
https://github.com/kashif-nawaz/Deploy-Ceph-on-K8s-Worker-Node-Using-ROOK
And here’s another one: the Next.js Edge Runtime becomes the fourth full-stack framework supported by Cloudflare Pages


You can now deploy Next.js applications which opt in to the Edge Runtime on Cloudflare Pages. Next.js is the fourth full-stack web framework that the Pages platform officially supports, and it is one of the most popular in the 'Jamstack-y' space.
Cloudflare Pages started its journey as a platform for static websites, but with last year's addition of Pages Functions powered by Cloudflare Workers, the platform has progressed to support an even more diverse range of use cases. Pages Functions allows developers to sprinkle in small pieces of server-side code with its simple file-based routing, or, as we've seen with the adoption from other frameworks (namely SvelteKit, Remix and Qwik), Pages Functions can be used to power your entire full-stack app. The folks behind Remix previously talked about the advantages of adopting open standards, and we've seen this again with Next.js' Edge Runtime.
Next.js' Edge Runtime
Next.js' Edge Runtime is an experimental mode that developers can opt into which results in a different type of application being built. Previously, Next.js applications which relied on server-side rendering (SSR) functionality had to be deployed on a Node.js server. Running a Node.js Continue reading
Use VRFs for VXLAN-Enabled VLANs
I started one of my VXLAN tests with a simple setup – two switches connecting two hosts over a VXLAN-enabled (gray tunnel) red VLAN. The switches are connected with a single blue link.
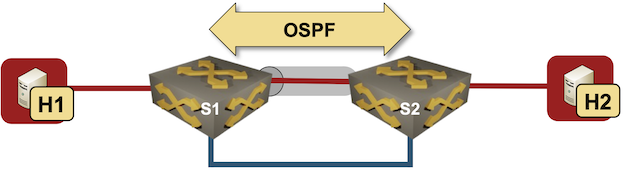
Test lab
I configured VLANs and VXLANs, and started OSPF on S1 and S2 to get connectivity between their loopback interfaces. Here’s the configuration of one of the Arista cEOS switches:
Use VRFs for VXLAN-Enabled VLANs
I started one of my VXLAN tests with a simple setup – two switches connecting two hosts over a VXLAN-enabled (gray tunnel) red VLAN. The switches are connected with a single blue link.

Test lab
I configured VLANs and VXLANs, and started OSPF on S1 and S2 to get connectivity between their loopback interfaces. Here’s the configuration of one of the Arista cEOS switches:
Controversial Reads 102222
This month, LinkedIn researchers revealed in Science that the company spent five years quietly researching more than 20 million users. By tweaking the professional networking platform’s algorithm, researchers were trying to determine through A/B testing whether users end up Continue reading
Heavy Networking 652: Why Networkers Should Want Routing Protocols Written In Rustlang
On today’s Heavy Networking episode, I talk with Nick Carter about Flock Networks, his routing protocol stack startup, as well as Nick’s love of the Rust programming language. As a network engineer, maybe you don’t think you care about Rust. Nick’s here to explain why the discerning network engineer might prefer their routing daemons to have been written in Rust. We also talk about the pleasures and travails of startup life.
The post Heavy Networking 652: Why Networkers Should Want Routing Protocols Written In Rustlang appeared first on Packet Pushers.
Heavy Networking 652: Why Networkers Should Want Routing Protocols Written In Rustlang
On today’s Heavy Networking episode, I talk with Nick Carter about Flock Networks, his routing protocol stack startup, as well as Nick’s love of the Rust programming language. As a network engineer, maybe you don’t think you care about Rust. Nick’s here to explain why the discerning network engineer might prefer their routing daemons to have been written in Rust. We also talk about the pleasures and travails of startup life.Page Shield can now watch for malicious outbound connections made by third-party JavaScript code


Page Shield can now watch for malicious outbound connections made by third-party JavaScript code
Many websites use third party JavaScript libraries to cut development time by using pre-built features. Common examples include checkout services, analytics tools, or live chat integrations. Any one of these JavaScript libraries may be sending site visitors’ data to unknown locations.
If you manage a website, and you have ever wondered where end user data might be going and who has access to it, starting today, you can find out using Page Shield’s Connection Monitor.
Page Shield is our client side security solution that aims to detect malicious behavior and compromises that affect the browser environment directly, such as those that exploit vulnerabilities in third party JavaScript libraries.
Connection Monitor, available from today, is the latest addition to Page Shield and allows you to see outbound connections being made by your users’ browsers initiated by third party JavaScript added to your site. You can then review this information to ensure only appropriate third parties are receiving sensitive data.
Customers on our business and enterprise plans receive visibility in outbound connections provided by Connection Monitor. If you are using our Page Shield enterprise add-on, you also Continue reading
Integration Platform as a Service (iPaaS) in 2023: Top Trends to Know
Since integration is complex, Integration PaaS (iPaaS) has gained widespread adoption of late, and the trend is expected to continue next year.EVPN Multihoming: Taxonomy and Overview
I promised you a blog post explaining the intricacies of implementing MLAG with EVPN, but (as is often the case) it’s taking longer than expected. In the meantime, enjoy the EVPN Multihoming Taxonomy and Overview video from Lukas Krattiger’s EVPN Multihoming versus MLAG presentation (part of EVPN Deep Dive webinar).
Video: EVPN Multihoming Taxonomy and Overview
I promised you a blog post explaining the intricacies of implementing MLAG with EVPN, but (as is often the case) it’s taking longer than expected. In the meantime, enjoy the EVPN Multihoming Taxonomy and Overview video from Lukas Krattiger’s EVPN Multihoming versus MLAG presentation (part of EVPN Deep Dive webinar).